It’s common knowledge that attackers often use email as a delivery mechanism for their malicious activity — which can range from enticing victims to click a phishing URL or download a malicious attachment.
To support these activities, attackers seek out tools that assist in the mass sending of malspam (malicious spam) emails from a compromised website. PHP scripts like Leaf PHPMailer are well suited for this task.
Hacktool Analysis: Leaf PHPMailer
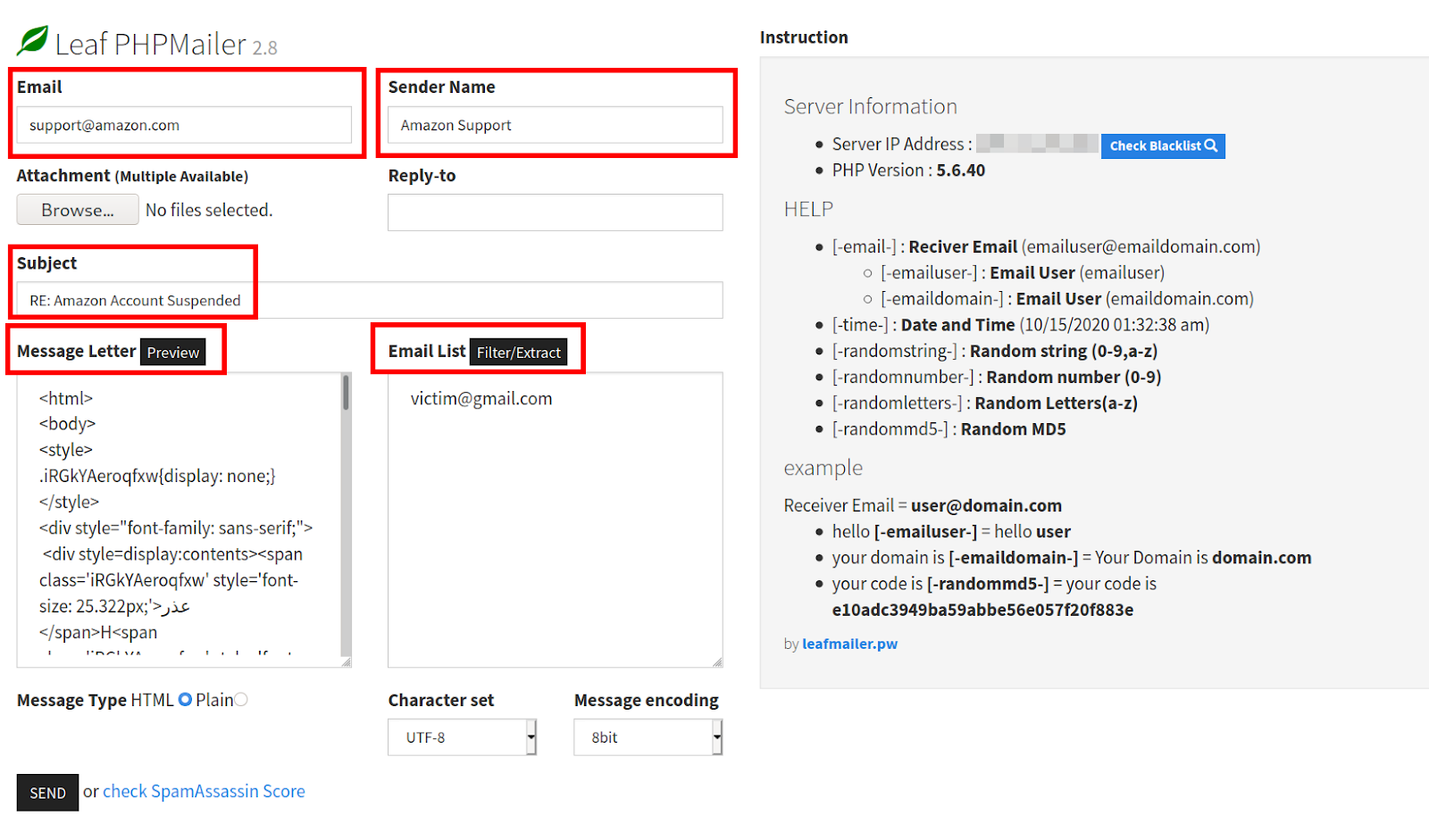
Leaf PHPMailer is a PHP mailer hacktool that lets an attacker send out large amounts of malspam emails from a compromised website’s web server.
When the tool is loaded, it leverages the LeafPHP mailer library to distribute the spam. It contains various text fields that allow the attacker to input custom data for important email fields:
Email = The email address that will be forged as the “From:” address
Sender Name = The name of the forged sender Email address – for example, this fake Amazon Support name in this screenshot:
Reply-to = The email address that will receive any replies to the sent email, may be left blank if no reply expected
Subject = String of text used to capture attention
Message Letter = Body content of the email
Email List = A list of recipient email addresses
These fields make it easy for the attacker to forge email headers to manipulate the appearance of the sender and deceive recipients, masking the true source of the email.
Malspam Transmission
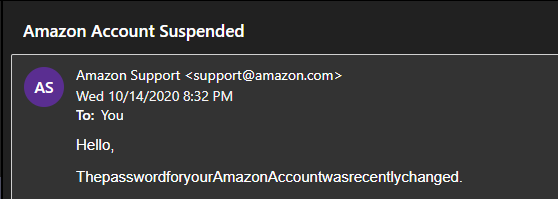
After inputting the desired values for the text fields, the attacker hits Send to dispatch the emails to the recipients. If the email successfully reaches their inbox, the email contents look similar to the following:
Leaf PHPMailer also has a Blacklist Checker feature that is used to query common blacklists for the hosting server’s IP address, allowing an attacker to determine whether it is listed or not:
This feature makes it easy for a bad actor to identify the viability of their campaign and pinpoint issues with mail deliverability.
Conclusion & Mitigation Steps
Email phishing and malspam campaigns are commonly used by bad actors because they make it incredibly easy to harvest personal data, banking, and other sensitive account information.
Attackers simply need to invest a bit of time into designing or emulating a convincing message from a known brand before sending to a stolen or purchased list of email addresses — if even only 1% of users actually fall for the campaign, the results can still be rewarding.
What’s more, an infection of this variety can have serious repercussions for website owners. If your site is compromised and begins to send out email spam, your hosting provider may suspend your account for spam. Any legitimate emails that are sent from your web server may be redirected to spam folders. Your domain may also be blacklisted by Google or other notable authorities.
In general, the best solutions to mitigate risk is to harden your website’s environment, keep your software and plugins updated with the latest security patches, and use a web application firewall to protect your site from bad actors.
If you think your website has already been compromised is sending malspam, we can help clean up the malware infection and remove your site from blacklists.