
2021-01-28 09:00:15 Author: blog.didierstevens.com(查看原文) 阅读量:268 收藏
I released an update to my 010 Editor script XORSelection.1sc.
010 is a binary editor with a scripting engine. XORSelection.1sc is a script I wrote years ago, that will XOR-encode a (partial) file open in the editor.
The first version just accepted a printable, arbitrary-length string as XOR-key. Later versions accepted an hexadecimal key too, and introduced various options.
With version 6.0, I add support for a dynamic XOR-key. That is a key that changes while it is being used. It can change, one byte at-a-time, before or after each XOR operation at byte-level is executed.
Hence option cb means change before, and ca means change after. Watch this video to understand exactly how the key changes (if you want to skip the part explaining my script XORSelection, you can jump directly to the dynamic XOR-key explanation).
I made this update to my XORSelection script, because I had to “manually” decode a Cobalt Strike beacon that was XOR-encoded with a changing XOR key (it is part of a WebLogic server attack). Later I included this decoding in my Cobalt Strike beacon analysis tool 1768.py.
The decoding shellcode is in the first 62 bytes (0x3E) of the file:

After the shellcode comes the XOR-key, the size and the beacon:

We can decode the beacon size, that is XOR-encoded with key 0x3F0882FB, as follows. First we select the bytes to be decoded:

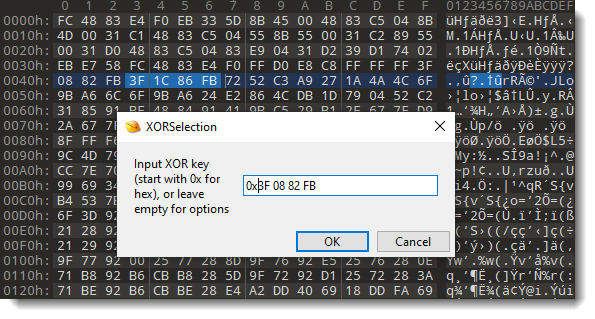
Then we launch 010 Editor script XORSelection.1sc:

Provide the XOR key (prefix 0x is to indicate that the key is provide as hexadecimal byte values):
And then, after pressing OK, the bytes that contain the beacon size are decoded by XOR-ing them with the provided key:
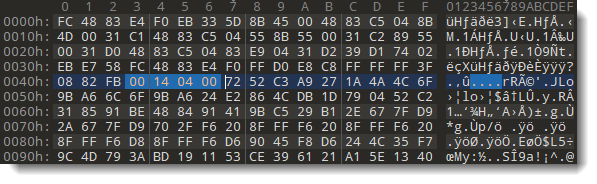
This beacon size (bytes 00 14 04 00) is a little-endian, 32-bit integer: 0x041400.
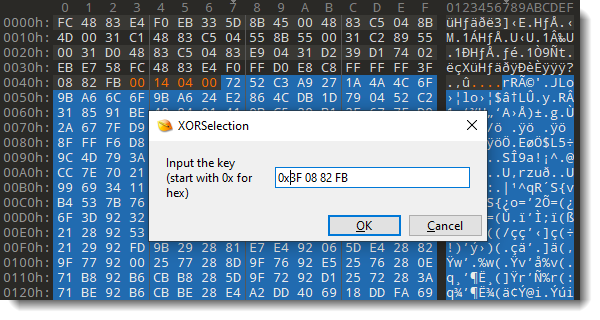
To decode the beacon, we select the encoded beacon and launch script XORSelection.1sc again:
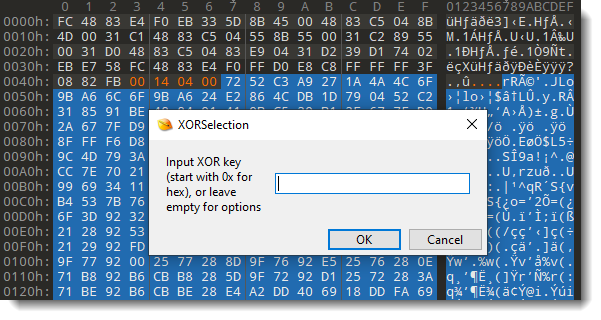
This time, we need to provide an option to change the XOR-decoding process. We press OK without entering a value, this will make the next prompt appear, where we can provide options:
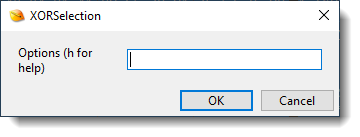
The option we need to use to decode this Cobalt Strike beacon, is cb: change before.
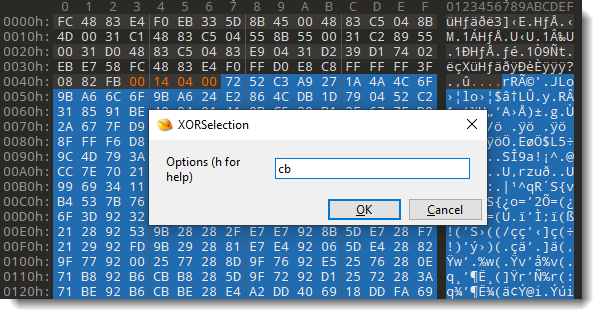
In the next prompt, we can provide the XOR-key:
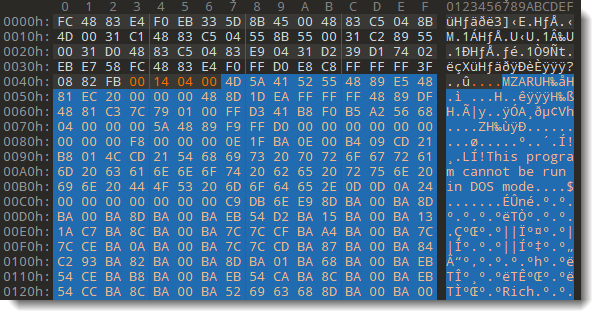
And we end up with the decoded beacon (you can see parts of the PE file that is the beacon):
Remark that you can enter “h” at the option prompt, to get a help screen:

I made this video explaining how to use this new option, and also explaining how the XOR key is changed exactly when using option change before (cb) or change after (ca).
If you want to skip the part explaining my script XORSelection, you can jump directly to the dynamic XOR-key explanation.
XORSelection_V6_0.zip (https)
MD5: C1872C275B59E236906D38B2302F3F4B
SHA256: 1970A506299878FAC2DDD193F9CE230FD717854AC1C85554610DDD95E04DE9E9
如有侵权请联系:admin#unsafe.sh