2021-02-01 21:25:19 Author: blog.elcomsoft.com(查看原文) 阅读量:335 收藏
More than a year ago, we started researching the available encryption options in off the shelf network attached storage devices. We started with Synology devices, followed by Asustor, TerraMaster, Thecus, and finally Qnap. The manufacturers exhibit vastly different approaches to data protection, with different limitations, security implications and vulnerabilities. Today we are publishing the aggregate results of our analysis.
The Types of Encryption
Before we begin the comparison, let’s review the available encryption methods as well as the options the different manufacturers use to store the encryption keys.
While all manufacturers advertise AES-256 encryption, the details can differ greatly. There are three different types of encryption commonly used by major NAS manufacturers. These are:
- Self-encrypting drive (SED). SED encryption support is only available in select models by select manufacturers, providing hardware-based encryption for hard drives with encryption support. SED encryption can be used on individual drives as well as on multiple drive storage pools, enabling the creation of fully encrypted storage pools. SED encryption is the lowest encryption layer. Typically, SED works per disk or on the Storage Pool level. The use of SED encryption does not affect performance, yet its scope of protection is limited, especially if the encryption keys are stored on the NAS itself.
- Full-disk or volume encryption. This type of encryption is available in most Qnap and Thecus models, as well as in Asustor My Archive disks. Disk encryption is software based; it works on the level of individual volumes. Disk encryption can protect single-disk and static volumes (Asustor My Archive) as well as volumes located on multi-disk storage pools (Qnap). Volume encryption does affect the performance, albeit the effect is relatively minor compared to folder-based encryption.
- Folder-based encryption. This is the kind of encryption we’ve first researched in Synology (Forensic Analysis of Synology NAS Devices), which is also used in Asustor, TerraMaster and select Qnap devices. The implementation of folder-based encryption is always based on eCryptFS; however, the location of the stored encryption key varies between manufacturers.
Encryption Keys
Most NAS manufacturers allow storing encryption keys on the device in order to facilitate automatic, non-interactive unlock of encrypted data at boot (or on a certain event, such as inserting or removing a USB flash drive). There are several options for managing the encryption keys:
- Interactive. This is the simplest and most secure method. The encryption keys are not stored anywhere on the device, and must be entered manually by the user every time they want to mount the encrypted disk or volume. All manufacturers except Thecus support this mode.
- Binary key (also referred as “escrow key” or “recovery key”). Most manufacturers allow producing and exporting a file that contains a binary encryption key. That file can be used to manually unlock encrypted data by uploading the file.
- On device. This method stores the encryption keys on the device itself (specifically not on the hard drives or any removable media). Typically, the built-in DOM (a SATA flash chip mounted on the mainboard) is used to store the encryption key. Qnap is one manufacturer using this approach; we are unsure about Asustor. If this method is used, then moving the disks to another device (even similar model) will require the password or encryption key to unlock the disks.
- On hard drives. Synology can store the encryption keys on the hard drives (using system partition that is mirrored across all disks); we are unsure about Asustor. If this is the case, hard drives can be moved to a different NAS (even a different model), and the data can still be unlocked without providing the password or recovery key.
- On USB device. The encryption keys can be also stored on an external USB device such as flash drive. Synology DSM uses an additional password to protect keys stored on the USB device; the wrapped password may be optionally stored on the hard drives to facilitate the automatic mounting of encrypted data. If this is the case, both the hard drives and the USB device will be required to gain access to the data without the password. Thecus uses this option exclusively, while Asustor can bind My Archive volumes to the flash drive’s serial number (without storing anything on the flash drive itself).
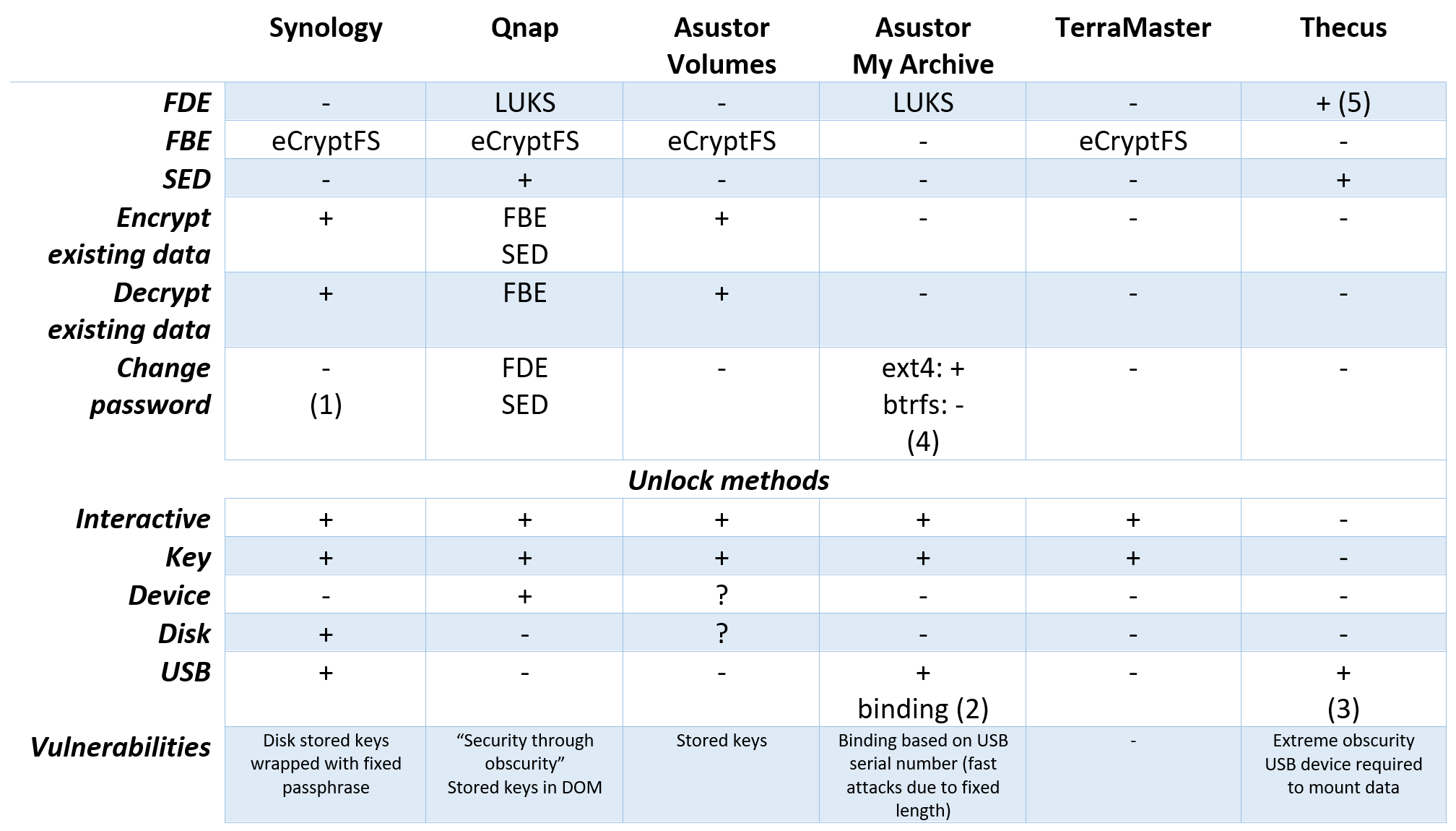
Comparison Table
Time for the actual comparison! Abbreviations:
- FDE – Full-disk or volume encryption
- FBE – Folder-based encryption
- SED – Self-Encrypting Disk
Notes:
- DSM Key Manager password (for machine keys stored on USB device) can be changed.
- Asustor can “bind” My Archive volumes to USB devices. Once the USB device is inserted, the NAS automatically unlocks the corresponding My Archive volumes. The volumes remain unlocked only while the USB device is inserted. Once the USB device is removed from the USB port, the volumes are instantly locked.
- Thecus implements an extremely non-transparent encryption scheme based on a binary key stored on a USB device. Once the USB device is inserted, the NAS automatically unlocks encrypted volumes. The volumes remain unlocked only while the USB device is inserted. Once the USB device is removed from the USB port, the volumes are instantly locked.
- Asustor only allows changing the password on My Archive volumes formatted in ext4. For btrfs volumes password changes are not allowed.
- Thecus uses volume encryption of unknown type. It’s not that the documentation lacks this information; rather, there’s no documentation at all.
Conclusion
We have tested network storage appliances made by five different manufacturers, and discovered five very different approaches to data protection.
Qnap has the most comprehensive protection options by far. In select models (which includes even some mid-range consumer units), it offers the unrestricted choice of SED, volume encryption (LUKS) and shared folder encryption (eCryptFS) in all possible combinations, including the stacking of the three layers on top of one another. However, the company’s reliance on security-through-obscurity when it comes to storing the encryption keys for auto-mounting the encrypted data, the lack of proper documentation, and the extremely slow speed of managing encrypted volumes (up to 5 minutes to mount or unmount the volume, about 10 minutes to change the password) make us wish for more. Still, taking the three-layer approach and never storing the encryption keys on the device can deliver sufficient security for the encrypted data.
Asustor offers the choice of full-disk encryption (LUKS) on My Archive volumes and folder-based encryption (eCryptFS) for regular volumes. The documentation is poor, especially when it comes to the two methods of auto-mounting encrypted data: storing encryption keys for regular volumes, or ‘binding’ My Archive volumes to USB flash drives. We discovered a weakness in the second method, which we will describe in detail at a later time; however, we did not look for the place on the NAS where the keys for auto-mounted encrypted shares are stored when it comes to regular volumes. The company’s reliance on eCryptFS for encrypting shares stored on regular volumes does not look sufficient to protect sensitive information, while the lack of ability to change passwords or revoke compromised encryption keys makes encryption on regular volumes dubious. My Archive volumes, on the other hand, are encrypted with LUKS, which is a proven and secure standard. However, the ‘USB binding’ feature that can be used to automatically unlock My Archive volumes on Asustor NAS when a flash drive with a given serial number is present does present a significant weakness, effectively breaking security provided by LUKS encryption.
Synology deserved a lot of attention from our side. The company has the most comprehensive (but still lacking) documentation. Just like everyone else, Synology relies on “security through obscurity”, hiding the location of the encryption keys if these are stored on the disk volume, and using a fixed wrapping passphrase “$1$5YN01o9y”. Things like that, should they be properly documented, should have never made it to production. The company’s sole reliance on eCryptFS does not look sufficient to protect sensitive information, while the lack of ability to change passwords or revoke compromised encryption keys makes Synology’s encryption a rather vague attempt.
TerraMaster is a fresh contender. Traditionally for NAS vendors, the company lacks any sort of technical documentation on its encryption method of choice. TerraMaster uses eCryptFS, a shared folder based encryption scheme, with all caveats of such encryption. The implementation is rudimentary, and looks more of an afterthought than a serious attempt to secure data. The lack of possibility to automatically mount encrypted data at least removes the associated security weakness.
Thecus is a classic manufacturer of NAS devices. It excels in not making the encryption understandable with or without documentation. What type of encryption is used? What is the user provided password used for? (Mind you, it’s not needed for mounting encrypted volumes.) What is the encryption key that’s stored on the USB drive? Lots of unknowns, with only one thing on the bright side: Thecus, in addition to its proprietary encryption, supports SED encryption in some of their units.
Detailed information about each manufacturer’s encryption methods is available in our research articles:
- Synology NAS Encryption: Forensic Analysis of Synology NAS Devices
- NAS Forensics: QNAP Encryption Analysis
- Attached Storage Forensics: Security Analysis of ASUSTOR NAS
- Attached Storage Forensics: Security Analysis of TerraMaster NAS
- Attached Storage Forensics: Security Analysis of Thecus NAS
- Breaking LUKS Encryption
如有侵权请联系:admin#unsafe.sh