BestCrypt, developed by the Finnish company Jetico, is a cross-platform commercial disk encryption tool. Available for Windows, Linux, macOS and Android platforms, BestCrypt is delivered in two editions, one offering full-disk encryption and the other encrypting virtual disk volumes stored in containers, the latter being supported with our tools.
BestCrypt Encryption Algorithms
Similar to open-source encryption tools such as TrueCrypt/VeraCrypt, BestCrypt supports multiple encryption algorithms including AES, Blowfish, CAST, GOST 28147-89, RC6, Serpent, Twofish, and Camellia. As you may already know, the choice of the encryption algorithm other than AES has an effect of drastically reduces the speed of accessing data without a tangible increase in security.
PBKDF: Hash Functions and Number of Hash Iterations
What does affect security (and the speed of the password recovery attack) is the choice of the hash algorithm and the number of hash rounds (iterations) used in the corresponding Password-Based Key Derivation Function.
BestCrypt supports the following hash functions: SHA-3 (512-bit), Whirlpool (512-bit), SHA-256 and SHA-512, and Skein.
BestCrypt supports several different encryption modes; by default, Password Based Encryption is used. The default hash algorithm is SHA-512, and the number of hash rounds is 16384 (the user can alter that number).
Breaking BestCrypt Passwords
Our tools can only break BestCrypt disks (physical and virtual volumes) that are protected with Password Based Encryption. Follow these steps to set up an attack.
Step 1: Extract encryption metadata
During the first step, you must extract encryption metadata from the encrypted disk or virtual volume. Unlike TrueCrypt/VeraCrypt, BestCrypt stores information about the encryption algorithm, hash function and the number of rounds in the disk header. This encryption metadata helps set up an attack by automatically applying the correct settings. The encryption metadata can be extracted with Elcomsoft Forensic Disk Decryptor, which is included with Elcomsoft Distributed Password Recovery and available separately.
Elcomsoft Forensic Disk Decryptor is a small tool included with Elcomsoft Distributed Password Recovery. You can use Elcomsoft Forensic Disk Decryptor users to set up attacks on a tiny file instead of the original encrypted container. Since no raw or encrypted data is included in encryption metadata, the hash files produced with Elcomsoft Forensic Disk Decryptor offer significantly higher level of privacy, allowing remote and cloud processing without the risk of a data leak.
To extract encryption metadata, do the following.
- Launch Elcomsoft Forensic Disk Decryptor.
- Specify the BestCrypt container to extract encryption metadata from.
- Save the encryption metadata.
Once you are done, collect the extracted hash files and open them in Elcomsoft Distributed Password Recovery to set up the attack.
Step 3: Use Distributed Password Recovery to break the password
Launching an attack against a BestCrypt disk is as simple as opening the encryption metadata you obtained in Step 1 with Elcomsoft Distributed Password Recovery. However, you may want to modify the attack as opposed to using the brute force.
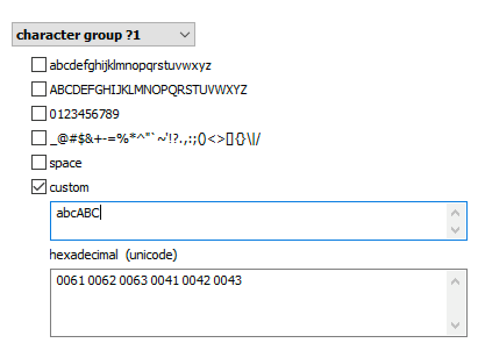
While BestCrypt does its best to protect encrypted disks against brute force attacks, we have significant advances in password recovery attacks. Breaking a password today involves the use of targeted dictionaries and smart attacks supported by Elcomsoft Distributed Password Recovery. The user’s existing passwords are an excellent starting point. These passwords can be pulled from the user’s Google Account, macOS, iOS or iCloud keychain, Microsoft Account, or simply extracted from the user’s computer. The user’s existing passwords give a hint at what character groups are likely used:
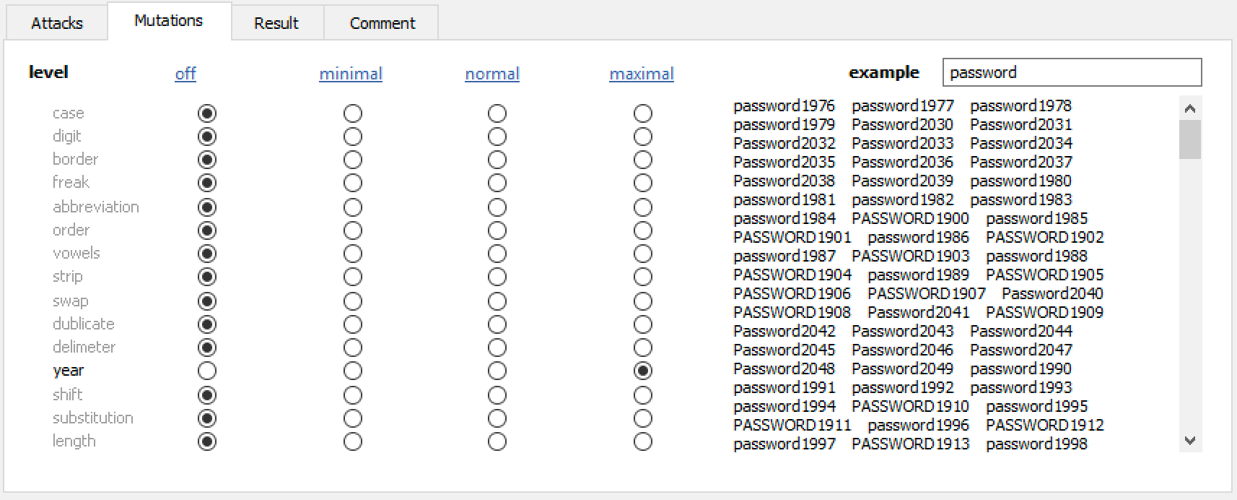
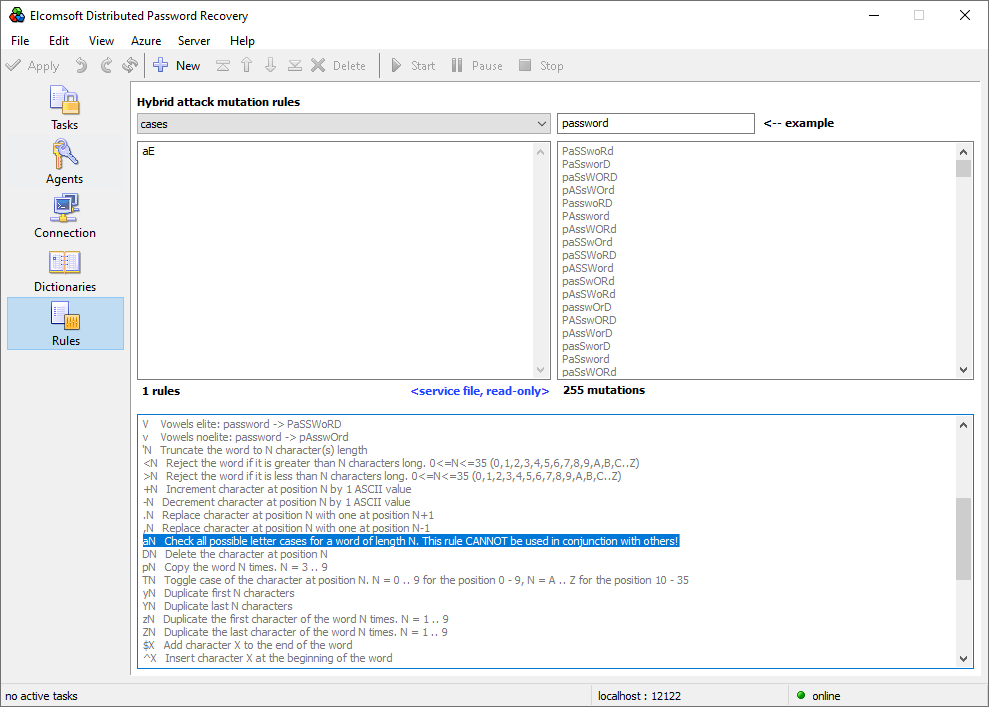
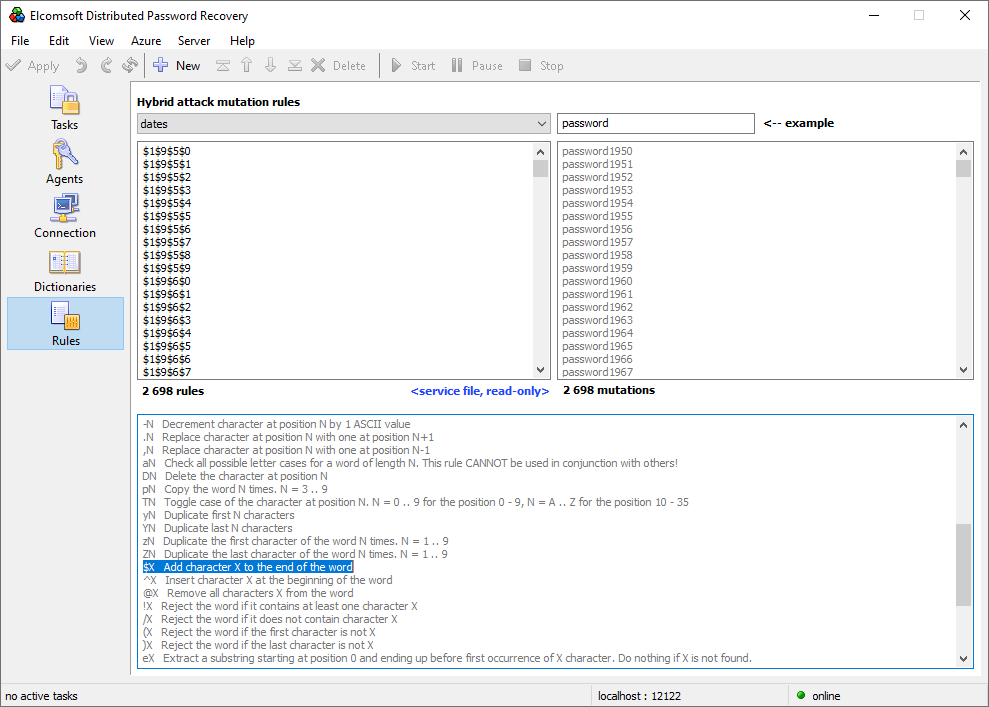
Elcomsoft Distributed Password Recovery offers a number of options to automatically try the most common variations of your password (such as the Password1, password1967 or pa$$w0rd):
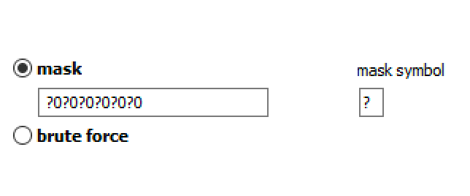
Masks can be used to try passwords matching established common patterns:
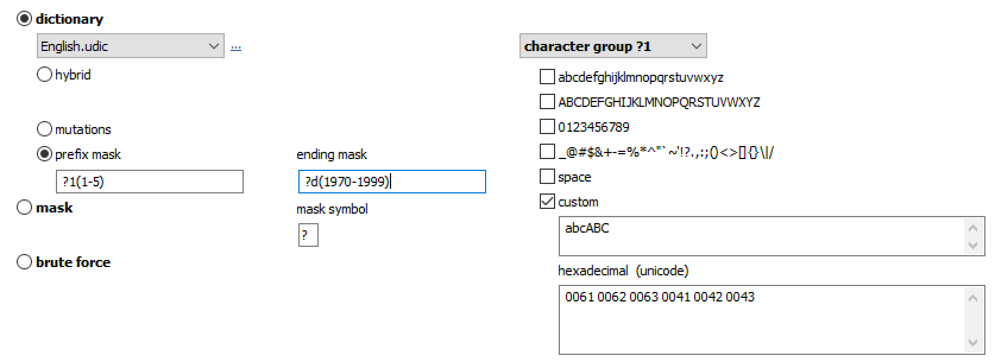
Advanced techniques allow composing passwords with up to two dictionaries and scriptable rules:
REFERENCES:
![]()
Elcomsoft Distributed Password Recovery
Build high-performance clusters for breaking passwords faster. Elcomsoft Distributed Password Recovery offers zero-overhead scalability and supports GPU acceleration for faster recovery. Serving forensic experts and government agencies, data recovery services and corporations, Elcomsoft Distributed Password Recovery is here to break the most complex passwords and strong encryption keys within realistic timeframes.
Elcomsoft Distributed Password Recovery official web page & downloads »
如有侵权请联系:admin#unsafe.sh