2021-02-14 02:21:00 Author: www.hackingarticles.in(查看原文) 阅读量:278 收藏
This is the second instalment of our series comprehensive guide on dirsearch. In the first part of this series, we have discussed some basic command on dirsearch. If you haven’t checked the first part yet you can learn these features from here. In this part, we will try to explore some more option of this command-line tool dirsearch.
Table of Content
- URL Attack
- Full URL
- Exclude Status Codes
- Minimal Size
- Maximal Size
- Random Agent
- Include Status Code
- Suffixes
- Prefixes
- Threads
- Only Selected
- Remove Extensions
- Upper Case Directories
- Lower Case Directories
- Capital Letter Directories
- Exclude Text
- Exclude Sizes
URL Attack
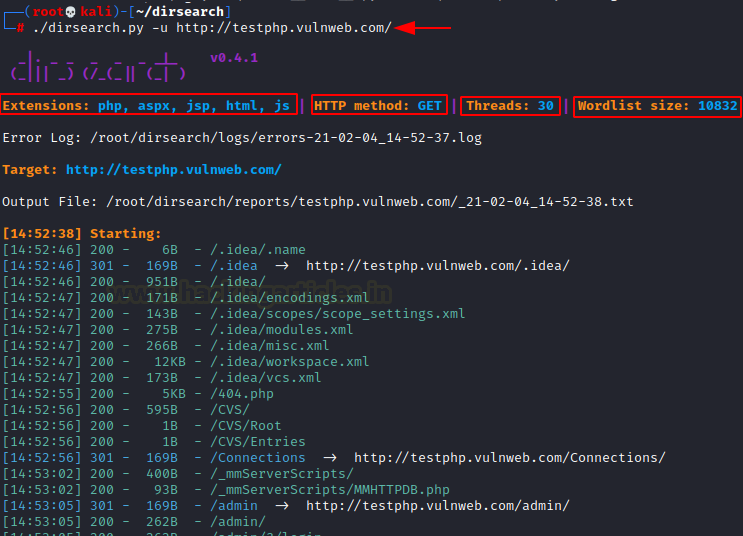
Firstly, we are taking the reference for simple URL attack. With the help of the [-u] parameter, we can use our web content scanner on a particular targeted URL. To get the required results, we need to ensure that this command is accompanied by an authenticated URL to get the desired results.
./dirsearch.py -u http://testphp.vulnweb.com/ |
As we can see we got some web directories and web pages. In this screenshot, we have highlighted a few things. Like default extensions [php, aspx, jsp, html, js], default HTTP method [GET], default Threads [30] and default wordlist size [10832]. These things act very crucially in our directories attack and we are tacking these as a reference from time to time in our attack.

Full URL
Sometimes these directories attack results can be confusing. To solve these confusions, we have a separated parameter called [–full-url]. This parameter helps us to gone through these results with ease.
./dirsearch.py -u http://testphp.vulnweb.com/ --full-url |
As we can see from these results, we have got full url details now.

Exclude Status Code
We know that, in five groups or divisions, all HTTP response status codes are segregated. The first digit of the status code determines the answer class, while there is no classifying or categorizing function for the last two digits.
There are five classes defined by their standards.

We can exclude this status code with our parameter called [-x]. Through this feature, we can remove the unwanted codes and get our desired results, get only those status which we wanted in our attack schedule.
./dirsearch.py -u http://testphp.vulnweb.com/ -x 301 |
We can also exclude more than one status code by separating them with comma [,].
./dirsearch.py -u http://testphp.vulnweb.com/ -x 301,302,403 |
As we can see in our results for this attack, we only get a successful one due to our parameter.

Minimal Size
Sometime some web pages have lots of small size files. These files have no use for us in offensive purposes so this tool provides us the power to eliminate them with [–minimal] parameter. We just need to specify the size in bytes, which we don’t want in our results.
./dirsearch.py -u http://testphp.vulnweb.com/ -x 301,302,403 --minimal=2048 |
As we can see in results it is showing only the successful results [due to -x parameter] with minimal size set by us which is 2kb or 2048 bytes.

Maximal Size
Wise versa of minimal size, maximal size is used to set the upper limit of the results. The parameter we use to achieve this is [–maximal]. We just need to specify the size in bytes, which we don’t want in our results.
./dirsearch.py -u http://testphp.vulnweb.com/ -x 301,302,403 --maximal=5120 |
We can also provide both minimal and maximal size together, this provides us with a proper range through which we can get a proper scope finding a particular size file.
./dirsearch.py -u http://testphp.vulnweb.com/ -x 301,302,403 --minimal=2048 --maximal=5120 |

Random Agent
We all recognize that a user agent in computing is a program (a software agent) that operates on behalf of a user, such as a web browser that “retrieves, renders, and facilitates interaction with web content by end-users.”
We can use the random user agent to break the default schedules and get our data results in the brand new order.
./dirsearch.py -u http://testphp.vulnweb.com/ -x 301,302,403 --random-agent |

Include Status Code
As we earlier performed exclude status code which would remove the unwanted status code. Include code is just likewise versa in this parameter we include any status code, which we want in our results.
./dirsearch.py -u http://testphp.vulnweb.com/ -i 200 |
We can include more than one status code, by just following this command.
./dirsearch.py -u http://testphp.vulnweb.com/ -i 200,301,302 |
As we can observe these results, it only shows these codes [200, 301, 302].

Suffixes
The grammatically meaning of a suffix. It is a letter or group of letters inserted at the end of a word that creates a new word. This parameter helps us to search only those specific result, which matches our provided suffix to the attack. To get these results in our attack.
./dirsearch.py -u http://testphp.vulnweb.com/ --suffixes=.php |
As we can see these results, we successfully got all those results related through our provided suffix.

Prefixes
The grammatically meaning of a prefix. It is a letter or group of letters inserted at the start of a word that creates a new word. This parameter helps us to search only those specific result, which matches our provided prefix to the attack. To get these results in our attack.
./dirsearch.py -u http://testphp.vulnweb.com/ --prefixes=index |
As we can see these results, it is only showing those results which have our prefixes.

Threads
We can increase or decrease the number of threads. This will increase or decrease the speed of our attack depending upon the number of threads provided by us. As we see earlier in URL attack the by default number threads are set on 30.
As we want to increase the speed of attack so we change it to 100 with the help of [-t] parameter.
./dirsearch.py -u http://testphp.vulnweb.com/ -i 200 -t 100 |

Only selected
In this parameter called [–only-selected], we got a focused directories wordlist through which only got selected web pages and directories. This can be very useful to find out some great results through the attack.
./dirsearch.py -u http://testphp.vulnweb.com/ -i 200 --only-selected |
As we can see in the banner of this tool our wordlist got shorter size 10832 to 7608.

Remove Extension
We all know the definition of the extension, a file extension (or simply “extension”) is the suffix at the end of a file name that specifies what sort of file it is. We can remove extension files from our results. To get this kind of results we can use our parameter called [–remove-extensions].
./dirsearch.py -u http://testphp.vulnweb.com/ -i 200 --remove-extensions |
As we can see it removes all the extensions.

Upper Case Directories
It just acts like a filter, which only let’s go to the upper-case directories with the help of parameter [-U]. we can apply this filter by using this command.
./dirsearch.py -u http://testphp.vulnweb.com/ -U |

Lower Case Directories
Similarly, as above it is just like a filter. Which only let’s go to the lower-case directories with the help of parameter [-L]. we can apply this filter by using this command.
./dirsearch.py -u http://testphp.vulnweb.com/ -i 200 -L |

Capital Letter Directories
It acts as a filter, which only let’s go the first letter capital directories with the help of parameter [-C]. we can apply this filter by using this command.
./dirsearch.py -u http://testphp.vulnweb.com/ -i 200 -C |

Exclude Text
As earlier we have removed or excluded the unwanted status codes, we can also exclude some text from our results as per our need. By using this parameter called [–exclude-texts].
./dirsearch.py -u http://testphp.vulnweb.com/ -i 200 --exclude-texts=index |
As we can see this result and compare it without filtered results, we can observe that it has excluded index text from its results.

Exclude sizes
As earlier we have removed or excluded the unwanted text, we can also exclude some file sizes from our results as per our need. By using this parameter called [–exclude-sizes].
./dirsearch.py -u http://testphp.vulnweb.com/ -i 200 --exclude-sizes=5KB |
As we can see this result and compare it without filtered results, we can observe that it has excluded files sizes have 5KB from its results.

Author: Shubham Sharma is a passionate Cybersecurity Researcher, contact LinkedIn and Twitter.
如有侵权请联系:admin#unsafe.sh