2021-03-18 15:55:12 Author: blog.elcomsoft.com(查看原文) 阅读量:255 收藏
iOS Forensic Toolkit 7.0 brings low-level extraction support for the latest generation of Apple devices. This includes the entire range of iPhone 12 models as well as all other devices capable of running iOS 14.0 to 14.3. Learn how to image the latest iPhone models without a jailbreak.
The latest update of iOS Forensic Toolkit enabled jailbreak-free, low-level extraction of A14 Bionic devices, which includes the entire iPhone 12 model range, running the iOS versions 14.0 through 14.3. In addition, the toolkit can image other iPhone and iPad models running the same versions of iOS (iPhone 6s/SE models and newer). In the end, the tool delivers the complete, zero-gap coverage for iPhone devices without a jailbreak from iOS 9 onwards, up to and including iOS 14.3 on supported devices. With this exclusive jailbreak-free coverage experts will be able to image all iPhone models based on 64-bit SoC (iPhone 5s through iPhone 12).
Benefits of jailbreak-free extraction
Speaking of iOS devices, there are several extraction methods of varying quality and applicability. These include:
Logical acquisition. This is the most universal and the most compatible extraction method based on Apple’s APIs and protocols. With logical acquisition, experts can make the phone create the full local backup of its data, pull pictures and videos, and obtain certain logs and shared files. This method is one of the most limited, too: both Apple and developers can restrict which parts of data are backed up, and the user can protect local backups with a password, which must be broken or removed in order to access the data. Breaking the password might be time-consuming or not even possible depending on the length and complexity of the password, while resetting the password involves removing the screen lock passcode on the iPhone, which, in turn, has important consequences. On the other hand, media files (including metadata) can be extracted regardless of the backup password, while log files may help recover some of the device usage timeline.
Physical acquisition (legacy devices). When analyzing an old, 32-bit device such as the iPhone 4, 5 or 5c, one can make a bit-precise image of the data partition, decrypting everything down to the last bit. While this is the deepest and most comprehensive acquisition method, it is not applicable to modern devices. Starting with the iPhone 5s, the encryption keys protecting the data are safeguarded with Secure Enclave, a hardware security subsystem, and there is no known way to extract these keys from the chip.
File system imaging and keychain decryption (with a jailbreak). When extracting an iOS device, one needs low-level access to the device. We developed a workflow to allow experts imaging the device’s file system and decrypting the keychain based on publicly available jailbreaks. While decidedly not forensically sound, this process was the only chance of accessing the full content of the device including all keychain records, private chats and application data not included in backups. Jailbreaks are both hardware-specific and iOS-specific. This method was superseded with agent-based extraction.
File system imaging and keychain decryption (with bootrom exploit). On some models (iPhone 5s through iPhone X), a bootrom exploit can be used to image the device regardless of the installed iOS version. For general use, this method was superseded with agent-based extraction. On the plus side, bootrom extractions are more forensically sound compared to jailbreaking, and support those versions of iOS for which no kernel-level exploits are available. In addition, limited BFU (Before First Unlock) extraction is available for all iPhone 5s – iPhone 7 devices, as well as for iPhone 8/8 Plus/iPhone X devices running iOS 13.x.
File system imaging and keychain decryption (without a jailbreak). When extracting an iOS device, we still need low-level access to the device. Instead of relying on public jailbreaks and exploits, which are not designed to be forensically sound, we developed our own solution based on the extraction agent. The extraction agent establishes a communication channel between the device and the computer, escalates privileges, and gains access to the file and the encryption keys required to decrypt the content of the keychain. Agent-based extraction provides numerous benefits over jailbreak-based acquisition, being a lot safer, a lot faster, and a lot more robust. The extraction agent collects all of the same information obtained with jailbreak-based methods without the risks associated with jailbreaks, while leaving drastically smaller footprint.
For models newer than the iPhone X (which includes the iPhone Xr/Xs, 11, SE 2020, and the iPhone 12 range), the bootrom exploit is no longer applicable. Using the extraction agent is the only way to extract the full file system and decrypt the keychain from iPhone Xr/Xs and newer models.
Agent-based vs. checkm8 extraction
Checkm8 is a bootrom-level exploit that is coded in hardware and cannot be fully patched by Apple. However, Apple were able to partially patch the exploit on iPhone 8/8 Plus/iPhone X devices running in iOS 14, thus fixing BFU extraction. In addition, checkm8 is not available on some versions of iOS. The extraction agent, when used with iPhone 5s – iPhone 12 devices, is the only extraction method in the following cases:
- The iOS version is not supported by checkm8 (iOS 9.0 through 12.x)
- For iPhone Xr/Xs devices and newer (up to and including the iPhone 12 range)
Extraction agent compatibility
You’ll need a supported iPhone or iPad device running a compatible version of iOS. Currently supported devices include all iPhone models ranging from the iPhone 5s all the way to the iPhone 12 range, with no gaps. iPad models based on the same chipsets are also supported. Compatible versions of iOS range from iOS 9.0 through 14.3, again with full coverage and no exclusions.
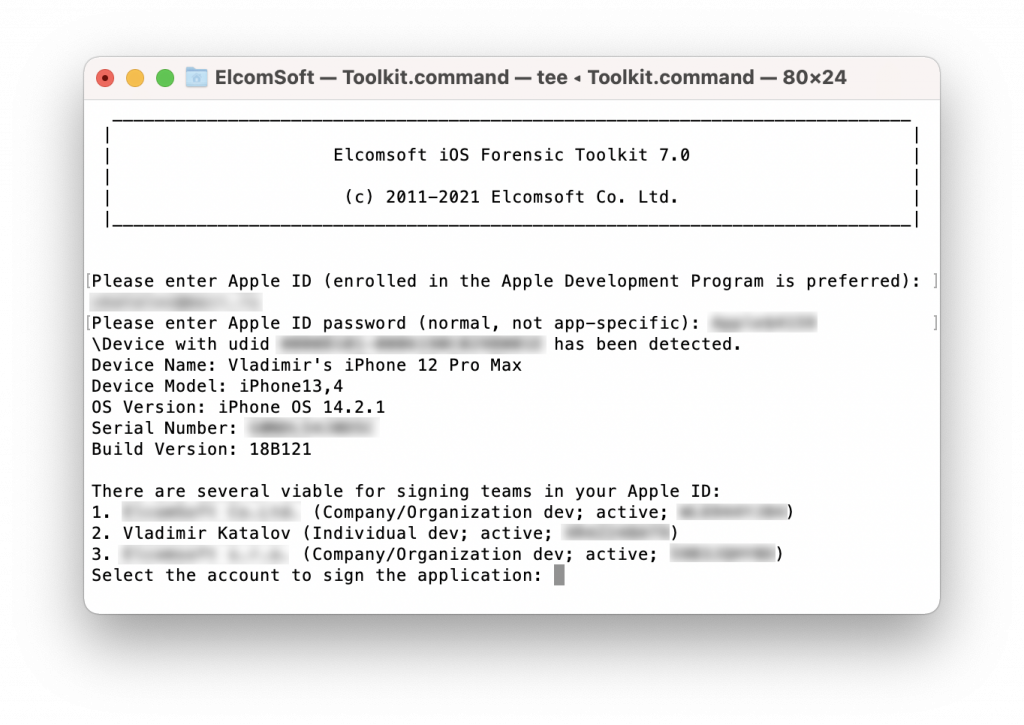
Using an Apple ID registered in Apple’s Developer Program is strongly recommended for installing the agent as it alleviates the need to open Internet access on the device. More about that in Why Mobile Forensic Specialists Need a Developer Account with Apple [article]. A workaround is available to Mac users.
Elcomsoft iOS Forensic Toolkit installation
There are important differences when using EIFT on Windows and macOS.
When installing iOS Forensic Toolkit on macOS Catalina and Big Sur, you’ll need to remove the quarantine flag from the installation DMG file you downloaded. Once you mount the DMG file, do not run EIFT directly from the mounted image. Instead, create a new local folder on your computer and copy the entire content of the installation DMG to that folder. Once you do that, you can safely unmount and remove the DMG. You’ll be able to launch EIFT from the local folder.
Installing the extraction agent
If you have a previous version of the extraction agent installed on the iPhone, make sure to uninstall it before using the newer version. You can uninstall the agent via the icon on the iPhone or by using the “5 UNINSTALL” command from the main menu.
When installing the agent with the “1 INSTALL” command, you will be prompted for Apple ID credentials. On Windows systems, you must use an Apple ID registered in Apple Developer Program. On macOS, regular and developer Apple ID’s are accepted, yet using a developer Apple ID is strongly recommended. If you use a regular, non-developer Apple ID, you will have to approve (“trust”) the certificate from the iPhone Settings, which in turn requires an Internet connection. Using a developer Apple ID does not require approving the certificate, and no Internet connection on the iPhone will be required.
If you are processing multiple devices, you may want to automate the authentication procedure instead of entering the login and password manually.
Quick tip: if you do not want to enter Apple ID, password and Team ID when installing the Agent on every new device, you can set them up right in the EIFT script (Windows: Toolkit.cmd; macOS: macOS/Toolkit.sh):
[email protected] AGENT_PASSWORD=abcd-efgh-ijkl-mnop AGENT_TEAMID=XXXXXXXXXX
The AGENT_ID is the Apple ID enrolled into Apple Developer Program; AGENT_PASSWORD is the password (see below), and AGENT_TEAMID is the Team ID (you can easily find it by logging in to Apple’s Developer Center, under Membership Information in Account | Membership).
Note that the password will be different depending on whether you use Windows or macOS. If you are using Windows, use an app-specific password to install the extraction agent. If you are using macOS, use the regular login and password to an Apple ID, then pass two-factor authentication using a trusted device or text message delivered to a trusted phone number. Note that we recommend using a USB 3.0 port to connect the iPhone, especially on newer devices.
Agent-based keychain and file system extraction
Using the extraction agent with Elcomsoft iOS Forensic Toolkit is generally as easy as using steps [1] through [5] from the main menu:
From the several blocks of commands, you’ll be using the following one:
1 INSTALL Install acquisition agent on device 2 KEYCHAIN Acquire device keychain 3 FILE SYSTEM Acquire device file system (as TAR archive) 4 FILE SYSTEM (USER) Acquire user files only (as TAR archive) 5 UNINSTALL Uninstall acquisition agent on device
Before you begin, connect the iPhone to the computer and establish trust between the PC and the iPhone. You will need to enter the screen lock passcode on the iPhone to confirm trust settings.
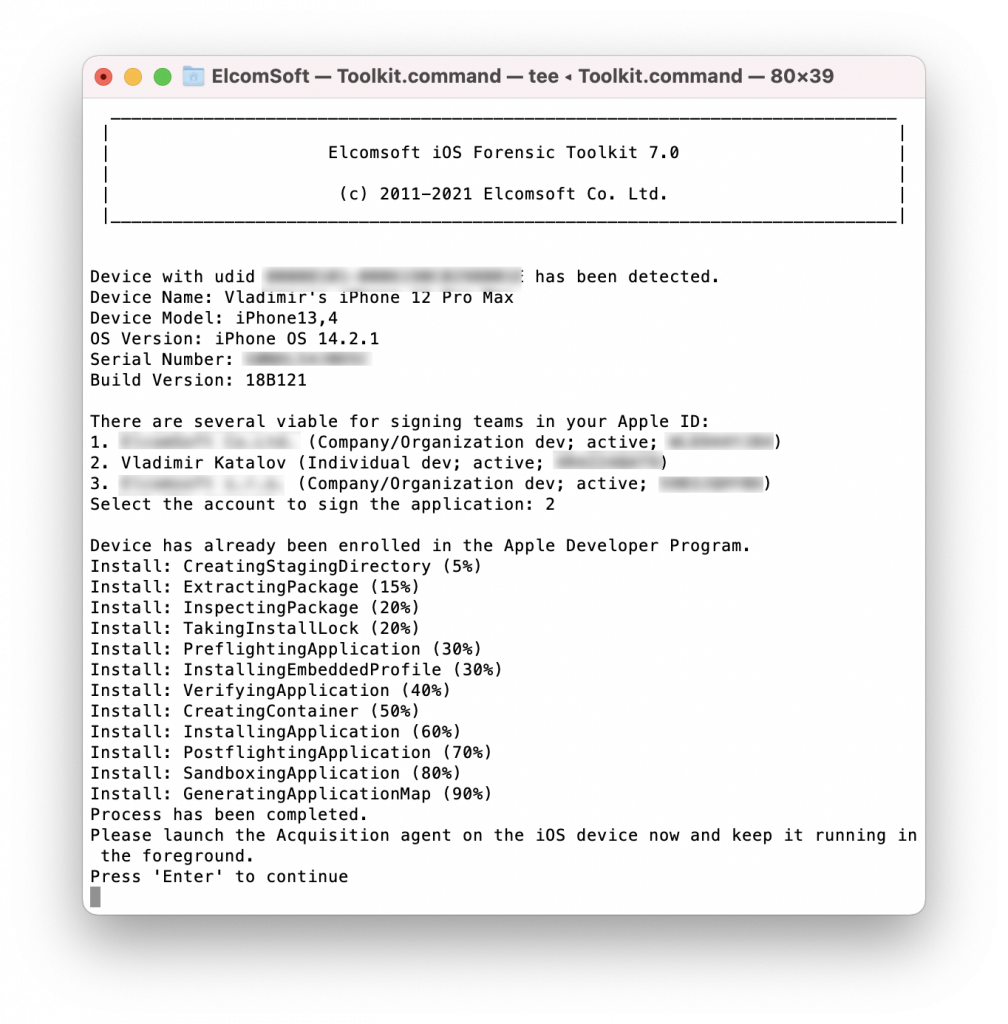
Enter “1” to install the extraction agent on the iPhone.
Launch the extraction agent on the iPhone by tapping its icon. Keep the agent working in foreground at all times during the extraction!
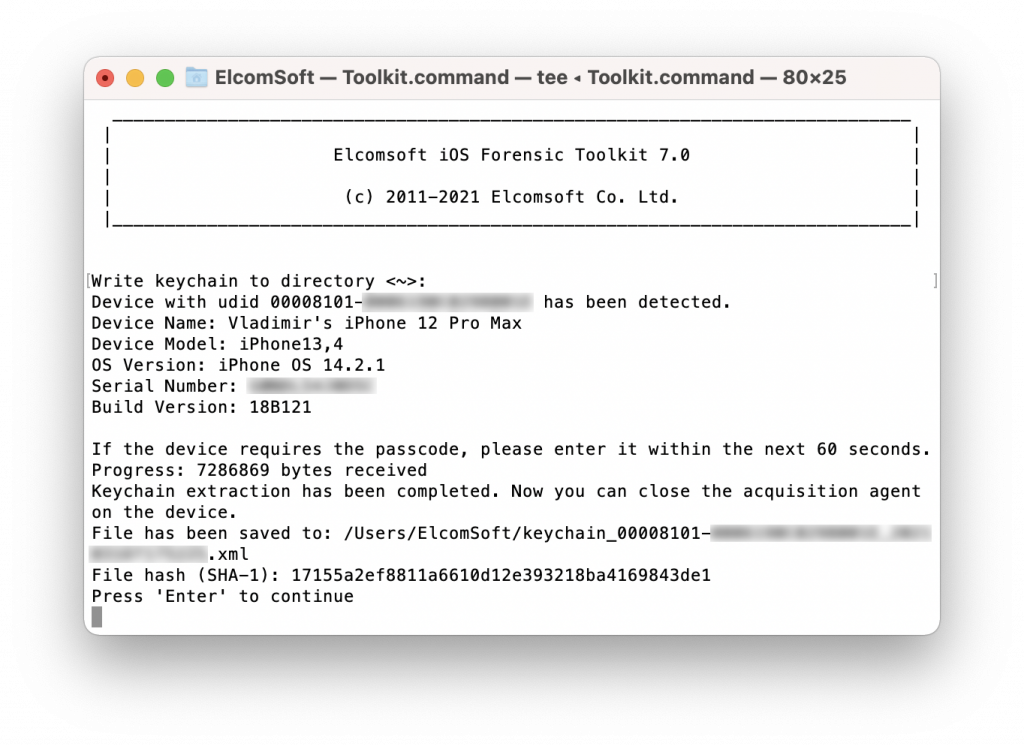
Enter “2” to decrypt the keychain. Note that starting with iOS 14, keychain extraction may require several attempts on A12 through A14 devices. The iPhone may spontaneously reboot. If this happens, disconnect the iPhone from the computer, unlock the iPhone with a passcode, and reconnect it to the computer, then launch the extraction agent again and retry the extraction. You may need 2-3 attempts. This is expected behavior; we are currently working on an improved solution. The reboots bear no negative consequences, and no user data will be modified.
Enter “3” to image the file system including the system partition, or enter “4” to image only the user partition. Normally, we recommend using the “4” option.
Enter “5” to uninstall the extraction agent and remove it from the iPhone. Alternatively, you may uninstalling the agent from the iPhone by removing it from the home screen.
Analyzing the results
iOS Forensic Toolkit produces the following files in the user’s home folder (macOS), or in %AppData%\Elcomsoft\Elcomsoft iOS Forensic Toolkit on Windows (you can define a different output folder in either system):
keychain_udid_timestamp.xml // the decrypted keychain udid_timestamp.tar // file system image info_udid_timestamp.xml // the extraction logs for file system and keychain
Now you can load the file system image into Elcomsoft Phone Viewer, or browse the keychain in Elcomsoft Phone Breaker.
REFERENCES:
![]()
Elcomsoft iOS Forensic Toolkit
Extract critical evidence from Apple iOS devices in real time. Gain access to phone secrets including passwords and encryption keys, and decrypt the file system image with or without the original passcode. Physical and logical acquisition options for all 64-bit devices running all versions of iOS.
Elcomsoft iOS Forensic Toolkit official web page & downloads »
如有侵权请联系:admin#unsafe.sh