I was hunting a full month on a federal private program and comes up with plenty of account takeovers. I am going to share one of the findings.
The Scope of the target was a wildcard and unauthenticated testing only. So the first thing I did -> Recon.
I fired up sub-finder combined with httpx (https://github.com/projectdiscovery) and I came up with a huge number of sub-domains, one of the domains caught my eyes with 403 forbidden error.
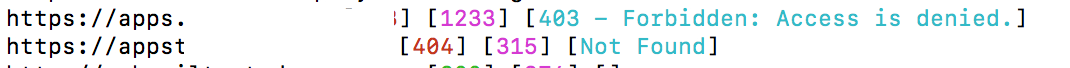
So instead of running ffuf, the first thing I run, a simple google search such as:
site:subdomainhere
It comes up with plenty of results
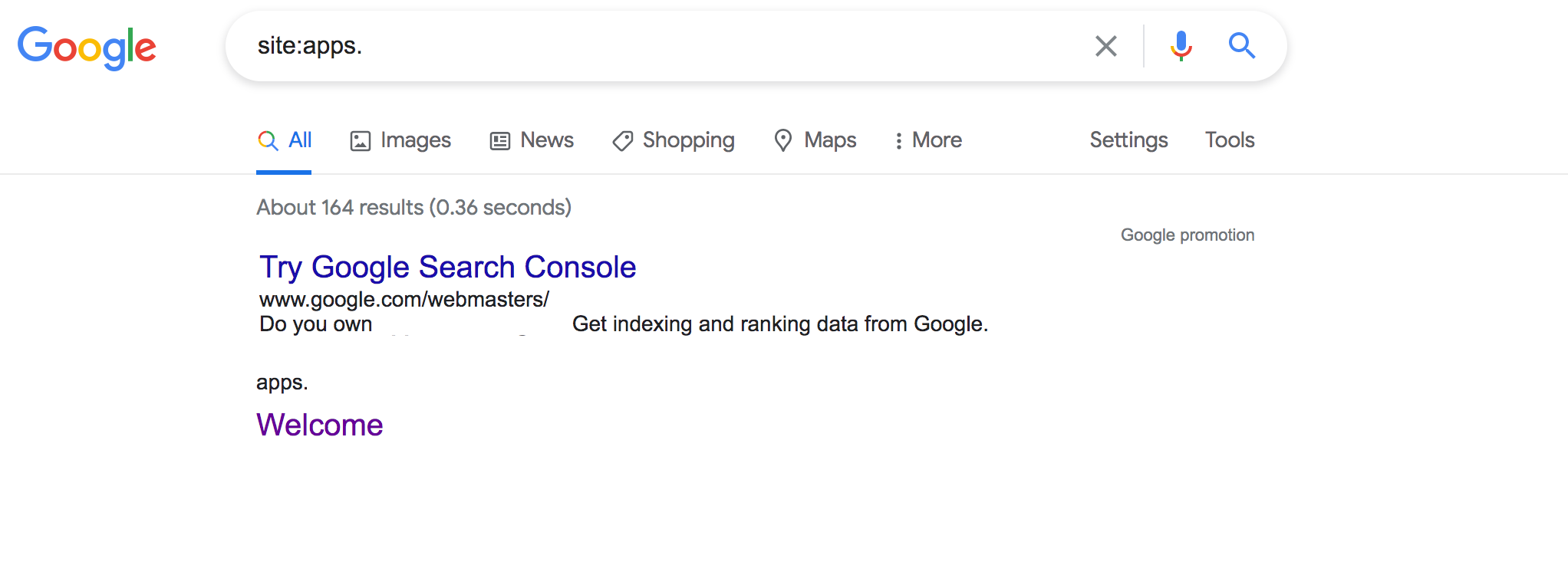
While this has been hosted with plenty of login pages, I decided to hunt on the very first result, it was an online invoice system. The application asks for some kinda D** Ids and Password for login.
I search about D** Ids in help articles, and I got to know, it's a 9 digit number assigned to all vendors at the time of licensing.
I did google searches but didn’t come up with this particular ID. I ended up looking at google images results in hope that licensing could have done over a paper and can have this id included.

Cool, I was correct, licensing was done over a paper and I got a couple of valid D** ID in the subject Part of letters, such as

Since I have this ID now, the first thing I did was brute-forcing for a password but ended up with nothing.
I started testing forget password flow, it asks for D** ID first for resetting the password. I found that the application is using two requests for resetting the password, one for querying the password for D** ID and another one sending a newly generated password to their email ID inside the request itself

So, this discloses not only their password but emails too. Using the newly generated password, I was able to login into their account.

stay curious.
