
2021-04-22 03:32:47 Author: www.webroot.com(查看原文) 阅读量:205 收藏
Although cybercriminal activity throughout 2020 was as innovative as ever, some of the most noteworthy threat activity we saw came from the old familiar players, namely ransomware, business email compromise (BEC) and phishing. According to the 2021 Webroot BrightCloud® Threat Report, each of these threat types saw significant fluctuations as people all over the world shifted to working, studying, and doing everything else online. Here are some of the findings from the report.
Ransomware
One of the newer trends we saw in ransomware was that of data extortion. Believed to have been started by the Maze ransomware group, the data extortion trend involves not just encrypting business’ data and holding it for ransom, but in fact threatening to expose the compromised data if the victims refuses to pay. This new ransomware business model specifically targets sensitive data to increase the likelihood of payment.
Unfortunately, there’s little a targeted business can do in these situations. If they don’t pay up, their data might be disclosed publicly or otherwise misused. And, depending on what kind of data has been compromised, the consequences of exposure could include costly fines for violating privacy regulations like GDPR and California’s Consumer Privacy Act (CCPA). These fines can really add up, starting at $100 per customer per record lost and going up to flat percentages of revenue.
As if the ransom cost and regulatory fines aren’t enough, there’s also the cost of other ransomware fallout, such as downtime and time to recover. Universal Healthcare Services reportedly suffered three weeks of downtime after its September 2020 ransomware incident, resulting in a $67 million loss of revenue. Finally, there’s the question of the brand’s reputation and customer trust, which could be so irreparably damaged that the business might not survive.
Read more about the hidden costs of ransomware in our eBook.
As the data extortion trend took off, we also saw massive payouts to ransomware actors.
- The attackers who hit Foxconn demanded ~1804 Bitcoin ($34 million at the time) to prevent the data they’d stolen from being publicly exposed.
- Malicious actors infected Garmin’s systems with ransomware and required (and reportedly received) $10 million to destroy the stolen data.
- By September 2020, the average ransom payment peaked at $233,817.
“In most cases, ransomware isn’t the beginning of a compromise. It’s actually the end state, where the criminals cash in after an extended period. By the time you realize you’ve got ransomware on your network, the criminals may have been in there, watching, listening, and tampering with things for weeks or months without your knowledge. They might’ve even checked out your financials, so they know what kind of ransom to demand.”
– Kelvin Murray, Sr. Threat Research Analyst
Business email compromise (BEC)
BEC typically targets commercial, government, and nonprofit organizations by impersonating a senior colleague, IT team member, vendor, or trusted customer. In most scenarios, the malicious actor contacts the victim via email under the pretense of requesting money (especially via wire transfer or pre-paid gift card), provide credentials, or release sensitive data.
BEC relies pretty heavily on the inherent trust of employees in their management teams, fellow colleagues, and customers. But with so many invoices and payment requests that occur as part of the daily operations in any businesses, it can be quite easy for attackers to sneak a fake one in.
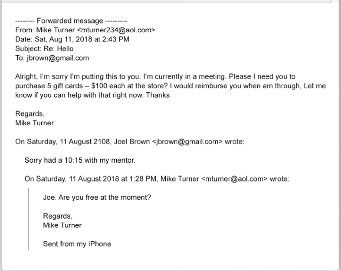
From the example above, you might not think much of the consequences of this type of attack. It’s important to keep in mind that it’s not always a matter of a few $50 or $100 gift cards; it could just as easily be a legitimate-looking vendor invoice for tens of thousands of dollars. BEC remains a very lucrative business; the Internet Crime Complaint Center (IC3) got 19,369 BEC complaints in 2020, resulting in adjusted losses of $1.8 billion!
“Like phishing prevention, successfully preventing BEC involves a combination of robust training for end users and appropriately designed and publicized business policies around how to handle financial or technical requests.” – Grayson Milbourne, Security Intelligence Director
Phishing
Phishing is still one of the most popular ways (if not the most popular) to get ransomware and other types of malware into a business’ network. Getting a victim to fall for a phishing attack is often the first step, which gives attackers a jumping off point to perform reconnaissance on the network, acquire any necessary credentials, interfere with protection measures and backup schedules, deploy malware payloads, and more — and then they get to decide what to do with any data they steal at their leisure.
COVID-19 definitely affected phishing in very visible ways. For example, the majority of phishing lures we spotted throughout the year pretended to offer information on the pandemic, COVID-19 tracking, protection measures and PPE, and more, often purporting to be from reputable sources like the CDC or WHO. There were also numerous malicious spam (malspam) emails claiming to provide details on stimulus checks and vaccines.
The rates of phishing attacks throughout 2020 largely coincided with the early months of the pandemic. Attacks increased 510% from January to February, with eBay and Apple the brands most often targeted (we believe these numbers were due to buyers increasingly looking online as product shortages and technology needs arose). Attack volume continued to grow into March, then dropped off as we moved into the summer months. A more modest spike occurred in the months leading up to the U.S. election, up 34% from September to October, and another 36% from October to November.
Here are a few of the other phishing stats that stand out.
- From March to July, during the initial lockdown phase in the U.S., phishing URLs targeting Netflix jumped 646%. Other popular streaming services saw similar spikes at corresponding times.
- By the end of 2020, 54% of phishing sites used HTTPS, indicating that checking for the lock icon in your browser’s address bar is no longer an adequate way to gauge if a website is legitimate or not.
Summary
Cybercriminals certainly didn’t sit 2020 out, but it’s not all gloom and doom. In fact, there were numerous cybersecurity achievements throughout the year that work to the benefit of businesses and individuals everywhere. Security researchers and analysts have been working hard to identify and neutralize new threats the moment they’re encountered. More businesses are adopting robust backup and disaster recovery plans to remain resilient in the face of downtime, planned or unplanned. Operating systems and web browsers are improving their built-in security to stop threats sooner in the attack cycle. Phishing simulations and security awareness training for employees continue to improve business security postures by major percentages (up to 72%, per the report). Nations and companies are working together to break down cybercriminal infrastructure. Even malware (for the moment) is trending gently downward. It’s clear from our findings that, with the right backup, training, and security layers working together to form a united defense against cyber threats, businesses and individuals can achieve true resilience, no matter what threatens.
Get the full story on these details and more in the 2021 Webroot BrightCloud® Threat Report.

About the Author
Justine Kurtz
Senior Copywriter
Justine Kurtz has crafted the voice of Webroot for nearly a decade. As senior copywriter, she partners with clients across the organization (and the globe) to communicate the value Webroot solutions bring to businesses, consumers, and technology partners alike.
如有侵权请联系:admin#unsafe.sh