This post was written by Alexej Savcin and Michal Stanek.
When Jamil Qandah got a call from Avast tech support, he had no reason to think that it wasn’t really us calling. It wasn’t until the “tech support” stole his life savings of over $200,000 that he realized he’d become a victim of an increasingly popular form of online scam: technical support fraud.
Tech support fraud is a big business for criminals. You may not realize it, but these schemes are actually run like businesses, with sophisticated call centers and proven scripts that they use.
The losses from tech support fraud are huge. According to the FBI’s Internet Crime Complaint Center (IC3)’s 2020 Internet Crime Report, the FBI received 15,421 tech support fraud complaints from victims in 60 countries in 2020. The victims lost over $146 million, a 171% increase in losses from 2019.
Further reading: Cybercrime complaints are up, according to the FBI's latest report
Tech support fraud is a crime that disproportionately affects older people. According to the IC3 report, the majority of tech support fraud victims (66%) are over 60 years of age and experienced 84% of the total losses (over $116 million).
In order to help combat this issue, let’s take a look at some of the tricks that tech support fraudsters use to deceive people and steal their money.
What is tech support fraud?
Tech support fraud is an industry-wide issue where fraudsters use scare tactics to trick you into buying overpriced, unnecessary technical support services that supposedly fix problems with your computer, device, or software.
At best, the fraudsters are trying to get you to pay them to "fix" a nonexistent problem. At worst, they're trying to steal your personal or financial information. And if you allow them to remotely connect to your computer to perform this "fix," they will often install malware, remote desktop software, or other unwanted programs that can steal your information or damage your data or device.
As part of their work to “fix” these “problems,” they may ask you to open some files or run a scan on your computer and then tell you those files or the scan results show a problem. They will then try to convince you to pay for tech support services you don't need, to fix a problem that doesn’t exist. As part of the fraud, they often ask you to pay by wiring money, putting money on a gift card, prepaid card or cash reload card, or using a money transfer app because they know those types of payments can be hard to reverse. That means it’s harder for you to get your money back if you realize it’s a fraud.
Tech support fraud typically starts one of two ways: Either you receive a call on the phone from someone who claims to be with tech support saying they’re calling to help you or you end up on a web page that tech support fraudsters have set up. Let’s take a look at the tech support fraud websites.
To convince you that your computer has some kind of problem, fraudsters create web pages that imitate the look of well-known antivirus or firewall software that display fake messages with warnings and alerts. Once you’re on their malicious site, they try to block your browser to prevent you from leaving the website or closing the whole browser.
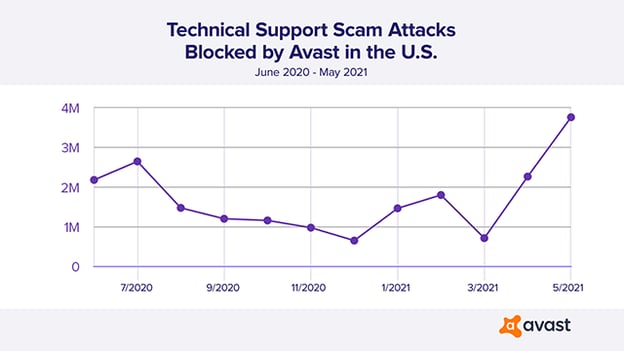
The graph below shows the number of tech support fraud attack attempts blocked in the U.S. by Avast from June 2020 through May 2021.
How tech support fraud is carried out
The first step in tech support fraud is to get potential victims on to sites that the fraudsters control. Once potential victims are on these sites, they use a variety of techniques to manipulate the computer and browser to make it seem like there’s a problem that needs to be fixed.
Malicious advertising (malvertising)
Advertising, which is a key part of the internet, can be exploited by tech support fraudsters in order to get potential victims onto their sites. Ad campaigns can be really complex and, like all systems, there are weak spots that cybercriminals can abuse. They can even sneak convincing malicious ads (malvertising) into ad networks in order to get a victim to click onto their sites. And while there are many types of online advertising, the one we’re focusing on works on the principle of real-time bidding.
Fraudsters abuse online advertising markets with ads which lure victims to their infrastructure, which consists of servers hosting websites that are under their control. The website can be a tech support fraud webpage or it could be a simple page that asks the user to allow push notifications: the fraudsters use this to set the stage for fraudulent ads later. It can also be an unwanted browser add-on which can access users’ data.

Push notifications

The process works as follows:
- The user visits a legitimate website that contains ads.
- The website requests a legitimate advertiser to show ads based on data gained from the user.
- The fraudster misrepresents themselves as a legitimate advertiser and pays a necessary amount to win a bidding contest for the ad campaign which is set to target the right group of users.
- The advertiser sends a response to the website with data for the fraudster’s ad to display.
- Based on the fraudster’s request, the website redirects users to their infrastructure: depending on the ad this can happen automatically or require the user to click on the ad. This way, the user eventually ends up on the tech support fraud page.
- Once the user is on the fraudster’s tech support fraud page, the page uses a variety of techniques to block the user’s browser to convince them there is a problem that needs fixing.
So that’s how internet tech support fraudsters get victims onto their page. Now, let’s talk about some of the techniques they use once a person is there.
The Evil Cursor technique
Tech support fraudsters sometimes use what is called The Evil Cursor Technique. This technique can be used to prevent users from closing a tab or browser window and works on every browser because it uses Cascading Style Sheets (CSS). CSS is a simple mechanism for adding style (e.g., fonts, colors, spacing) to web documents. In this case, though, attackers abuse it to try and keep you locked on their malicious page to make it seem like there’s an actual problem that you need them to “fix.”
Despite the fact that this trick is not new, our data shows that it is far from being obsolete and is actually quite popular.
How the Evil Cursor technique works
Evil Cursor works by abusing the cursor property on a web page. The cursor property is set to an image that is encoded in base64 with 128 by 128 pixels dimensions. The standard dimensions of the cursor is 32 by 32 pixels, so suddenly users have a large box that acts as a cursor. This simple replacement of the standard cursor with a much larger custom one, can make navigation very difficult.
Below, you can see an example of the malicious website’s HTML code, abusing the cursor property.

Source code of EvilCursor
If we decode this image from base64, we get a slightly different shape of the standard system cursor inside of a transparent box, as shown below.

Decoded image showing bogus cursor
The result is that the user sees just a “normal” cursor, which is in the corner of the decoded image. However, all clicks point to a different area. The final result is that closing pop-ups or browser tabs by mouse or touchpad is more difficult, if not impossible.
We can see this in action in the image below. The animated circles show you where the cursor actually is using a feature in Microsoft Windows that you can use to locate your cursor. In this image, you can see the cursor is actually hidden behind the message box while a fake cursor is shown on the “Ok” button. Since the actual cursor is not on the OK button, clicking the mouse button will not activate the OK button. This creates the illusion of unresponsiveness that the fraudsters exploit to convince the user there’s a problem.

Where you see your cursor vs. where it really is: A default Windows animation indicates the cursor’s real position via the circle, while the user sees the cursor over the “Ok” button, as scammers have altered the visual cursor position.
The 401 authentication loop technique
One of the first simple tricks that tech support fraud site creators used was abusing an authorization pop-up window which in some cases imitates the Microsoft Windows system design. They do this to trick the user into believing the message comes from Microsoft. Typically, this pop-up window contains some basic messages and telephone numbers to contact the tech support fraudsters and it cannot be simply closed. Below is an example of one of these fake messages.

How the 401 authentication loop technique works
Once again, the fraudsters use a specially constructed webpage to create the illusion of a problem. A login form is what website's visitors will use to login to a particular website to access content for logged-in users (such as a profile page). In many cases, the shown login will do nothing, as scam websites do not have any administration. The main purpose of the shown login form is to prevent interaction with the rest of the webpage.

Use of login form
The file download jamming technique
Another technique fraudsters use to make a website visitor think there’s a problem that needs to be fixed is jamming the browser with file downloads. This can cause the browser to be overloaded and unresponsive, making it seem like there’s a problem. Jamming the browser with multiple file downloads also consumes a huge amount of RAM memory, which slows down the victim’s computer and creates the impression of the computer being infected with malicious software. Uninformed users are scared by the sudden unfamiliar behavior of their computer and call the number fraudsters present on the landing page.
How the file download jamming technique works
Yet again, the fraudsters use the coding on the webpage they control to create behavior that makes it appear there’s a problem that needs to be “fixed.” Source code of the landing page contains a simple script that runs when the page is loaded, as is shown below.

This script triggers an infinite loop, which consists of two steps:
- Create a dummy file containing a randomly generated character
- Try to download the file in a new tab
The whole script is written in a very chaotic way in order to obfuscate the real purpose, which is most likely to confound security tools.
The keyboard shortcut lockout technique
The first thing that users may try to do when they see an unexpected flurry of pop-ups and alerts is, of course, close them all. We have already seen that some pop-ups can’t be easily closed, as they are open in an infinite loop. We’ve also seen how tech support fraud sites can manipulate the cursor so users cannot hit the close button. So what about keyboard shortcuts? Tech support fraudsters have accounted for this in many cases and lock out commonly used keyboard shortcuts such as ALT+F4, F5, F12, and the “Escape” key.
How the keyboard shortcut lockout technique works
Key codes are numeric values that correspond to physical keys on the keyboard, but do not necessarily correspond to a particular character. For example, the “A” key on the keyboard produces the same key code when pressed, even though its character code might be 65 (uppercase A) or 97 (lowercase a), depending on whether the “Shift” key is down at the same time.
In the sample below, we can see that the fraudsters web page uses code to remap the keycodes that correspond to commonly used keyboard shortcuts.

In fact, the fraudsters have remapped not only the keys but also the right mouse, as is shown below.

The net result of this technique is that when a visitor to the webpage tries to use the keyboard or mouse shortcuts to close the browser or navigate away from the page, those won’t work because they’ve been hijacked by the fraudsters.
The browser history manipulation technique
In addition to hijacking keyboard shortcuts, another trick that the fraudsters use is making sure that the “back” button is no longer an option for leaving their site.
How the browser history manipulation technique works
Fraudsters can make the current page come up as the “back” page when you click the button by manipulating your browser session history.

The fraudsters use the history API to manipulate your browser history, so whenever you click “back,” it just reloads the page you’re currently on. Looking at the code in the example above, you can see they do this by initially replacing the page you would be going to with the back button with the current page.
Here, the technique again makes it seem like the browser is frozen or otherwise malfunctioning.
The print spam technique
This technique is similar to file download jamming. In this case, the malicious web page uses an infinite loop to continuously send print commands to the browser, once again making it seem slow and unresponsive.
How the print spam technique works
The infinite loop is started by a short script that is executed when the page is loaded by the browser. During this loop a single function window.print() is called with an interval of 100ms. This function activates a printing dialog, which prevents the user from leaving the page, creating a browser lock similar to what we’ve seen before. Below is an example of the code that makes this happen.

This technique probably aims at outdated browsers such as Internet Explorer or older versions of Safari, because the newer browsers are able to leave the page even when the print dialog is active.
Attackers behind tech support fraud
Tech support fraud is a big, global business and Avast monitors several groups across the world.
We’ve divided the fraudsters into groups according to geography and similar attack patterns. These groupings can include multiple fraud groups that use the same tool, or use similar browser locking methods. The following table represents the unique hits for each group over Q1/2021.
|
Logical group
|
Unique hits over Q1/2021
|
|
GR1
|
137,730
|
|
GR2
|
220,557
|
|
GR3
|
1,992
|
|
GR4
|
10,824
|
|
GR5
|
709,615
|
|
GR6
|
70,448
|
|
GR7
|
97,487
|

GR1
|
Targeted regions
|
Locking techniques
|
- USA
- Canada
- Australia
- Japan
|
- Evil Cursor
- 401 authentication error
- File download jamming
|


Examples of landing pages:




GR2
|
Targeted regions
|
Locking techniques
|
- Japan
- USA
- Canada
- Australia
|
- Evil Cursor
- 401 authentication error
- File download jamming
|


Examples of landing pages:






GR3
|
Targeted regions
|
Locking techniques
|
- USA
- Canada
- Australia
- Japan
|
- Evil Cursor
- 401 authentication loop
- Print jamming
|

Examples of landing pages:



GR4
|
Targeted regions
|
Locking techniques
|
|
|
|

Examples of landing pages:

GR5
|
Targeted regions
|
Locking techniques
|
|
|
|

Examples of landing pages:

GR6
|
Targeted regions
|
Locking techniques
|
|
|
- Evil Cursor
- 401 authentication error
|

Examples of landing pages:

GR7
|
Targeted regions
|
Locking techniques
|
|
|
|

Examples of landing pages:

What to do if you’re on a tech support fraud page
Now that we’ve described several of the techniques attackers use, let’s focus on how you can spot these kinds of tech support fraud pages, realize you’re being targeted, and what to do in these situations.
Spotting technical support fraud
Technical support fraud pages can be spotted when you know what to look for. The crucial thing is to stay calm and to think about what just happened.
The first important thing to notice is the process of getting on the support web page. Did I actually search for a support page and get here directly from a search engine, or did the page pop up on it’s own? Official support pages don’t just appear to alert you that there is something wrong.
The biggest tip that you are looking at a fraudulent tech support attempt is often the web page alone. Isn’t it suspicious that the browser froze right on an official support page? And why would they want you to call them? If a security tool actually detected malicious activity, it would be blocked automatically without needing you to call a helpline.
Some fraud pages can be more sophisticated and look almost identical to the official support. However, the one thing that differentiates is the page URL. A complex domain rather than a simple one is a big tip. If the domain looks like mysupport.micr0s0ftzy56.com rather than support.microsoft.com that’s a tip that it’s probably not a legitimate site. In fact, the only way to be sure of the identity of a site you’re looking at is to check the name on the digital certificate, like in the image below.

And if the site doesn’t have a digital certificate? That's a huge warning, since all legitimate support sites today have digital certificates.
After that, you can identify fraudulent sites by answering these questions below. In situations which are not obvious, users should always keep in mind the golden rule about privacy on the internet: Never enter your credentials on a page that you did not browse to yourself, or that looks suspicious.

Unlocking the browser
If you find yourself stuck on a fraudulent page, what can you do next? Most importantly, remember, there is no real threat until you call the fraud number and let the fraudster access your computer via remote access tools.
As we explained earlier, attackers use many different methods to fool the victims into believing their browser is locked. However, it’s always just an illusion and for all the methods there is a counterstep. The most obvious one, yet the most effective, is to simply quit the browser. Sometimes, the fraudsters try to prevent users from doing so by switching the browser to full screen mode, so the Exit button is hidden from the plain sight. This can be reverted by a keyboard shortcut F11.
If even that fails, quitting the browser via the computer’s task list is a sure thing. To do so, on Microsoft Windows open the computer’s Task Manager with a keyboard shortcut “CTRL + SHIFT + ESC”, and on Apple Macs open the computer’s Force Quit Applications with a keyboard shortcut Option, Command, and Esc (Escape). Once the task list is up, find the browser task and click on the “End task” (Windows) or “Force Quit” (Mac) button.
If that doesn’t work, you can always restart the computer.
Conclusion
Tech support fraud is a big business and the people behind it use a number of techniques to try and convince you that you need their help. As we’ve seen, most of the techniques these websites use are aimed at making your browser and system seem broken.
But the truth is, your system is fine and you can get back to normal by getting off of the website.
The most important thing to remember is that legitimate support is support that you seek out, not that seeks you out. Whether it’s a phone call or a website, if someone or something is offering you support that you weren’t looking for, it’s almost certainly a fraud of some kind.
All you have to do is hang up the phone or navigate away from the site without engaging or giving them any information. That’s all it takes to protect yourself.
Additional information, explanations, and suggestions for protection regarding tech support fraud is available in the most recent tech support fraud PSA on the IC3 website.
Needless to say, we need to bring tech support fraud into the public awareness; it should be part of educational conversations about the internet, both in families and among friends. People need to talk about tech support fraud to their grandparents, parents, friends, and children. Users, if in doubt of whether they are being scammed, should always talk to family members and friends about the situation they are in, as an external person may realize a scam more easily than the affected person in the heat of the moment.


