2018-06-08 03:10:22 Author: medium.com(查看原文) 阅读量:317 收藏
This is a short explanation of how I took over a subdomain by doing recon at the right time and what I learned about the competition in bug bounty community.
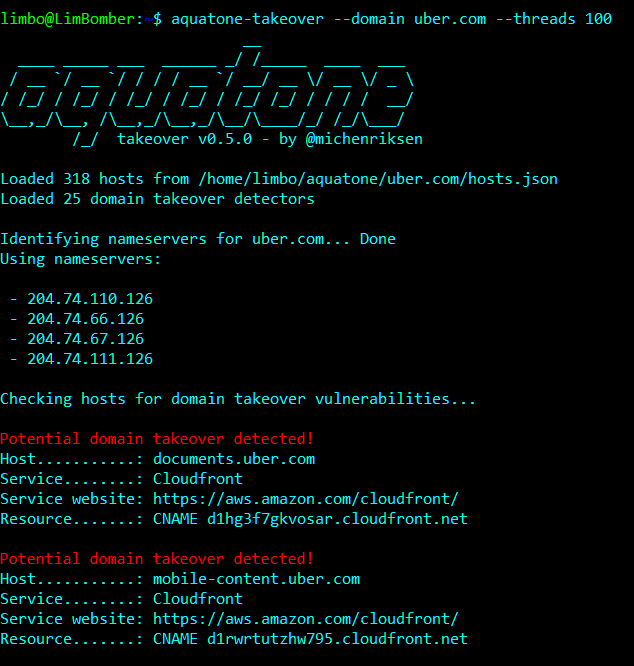
First things first, the tool I used to identify the vulnerable subdomain was Aquatone by Michael Henriksen . This tool is perfect for recon and every hacker should consider using it to scout a target. Luckily I encountered the vulnerable domain the first day I cloned the Aquatone repo but you might not be that lucky.
After running aquatone-takeover — domain {{target}}.com I saw a domain vulnerable to takeover on AWS Cloudfront. At first I wasn’t excited because most of the time you get a CNAME already in use error trying to claim a subdomain. However to my great surprise the company had forgotten to remove the CNAME and I was able to claim it.
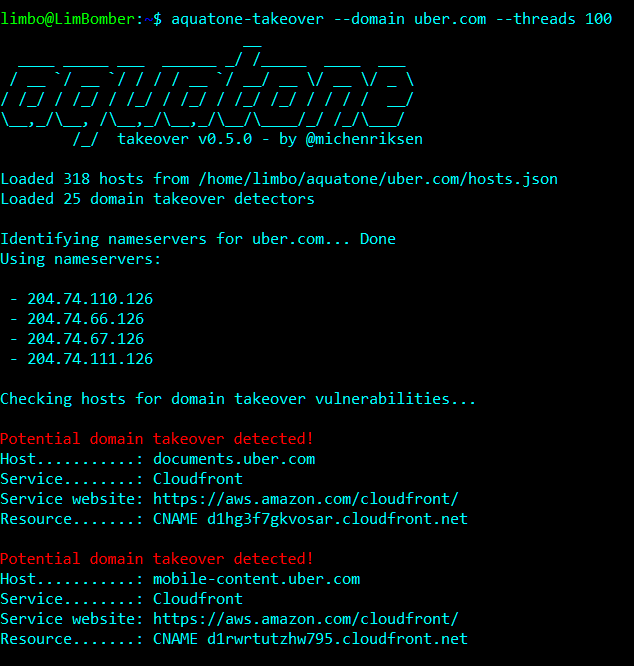
These ones are of course in use by Uber and impossible to claim. As a side note a fast way to check if the finding is fallacious is to navigate to the host using both http and https. If both of them return the same Error page you can probably takeover the domain and should log on to AWS.
If you are also able to claim a subdomain it is best practice to host your content in a path other than / to avoid damaging company’s reputation. I hosted a simple HTML file on my AWS bucket and pointed the domain to that.
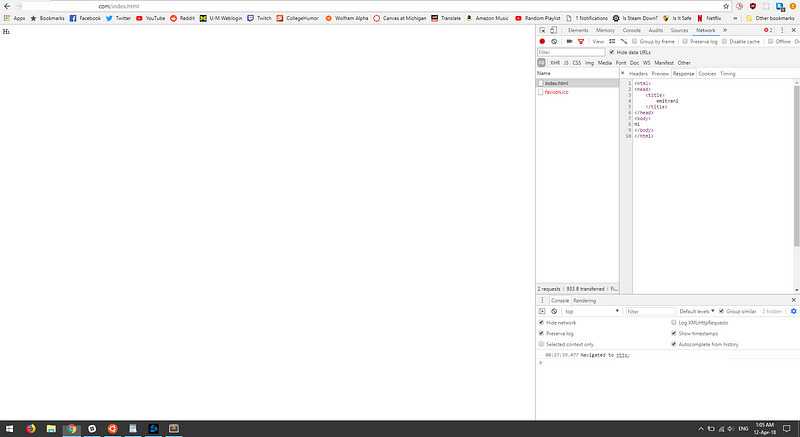
My report was quickly validated by HackerOne staff and fixed within 4 days. However the most interesting part about this was all the data I collected over the weekend while I held the domain.
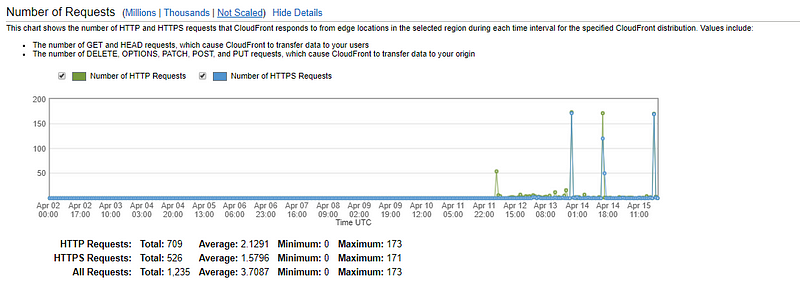
You can see around 1200 requests were sent to the subdomain over the weekend and by analyzing those I realized most of the traffic was hackers doing dirsearch or otherwise looking for vulnerabilities. At that moment I began to see how much competition exists in public bug bounty programs. I’m honestly lucky to be invited to private ones where competition seems a lot less intense.
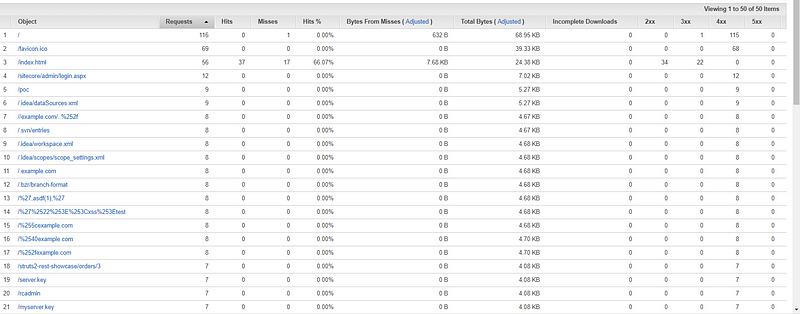
As you can see most people are doing basic recon on the target looking for reflected XSS, open redirect or exposed directories. You need to be extremely lucky to find that sort of low hanging fruit but it doesn’t hurt to try.
As far as this finding goes, I was awarded $4500 as this subdomain could be used to set valid cookies on the entire domain. I honestly don’t know how I got to beat Frans Rosén’s scripts but I’ll take it.
Timeline:
April 12, 2018: Report Submitted and triaged
April 16, 2018: Report Resolved
May 3,2018: $4500 Bounty awarded
如有侵权请联系:admin#unsafe.sh