This article will depict “How to discover SSID for WiFi Network” using several tools designed for Windows and Linux platforms. SSID discovery is applicable in Wi-fi hacking or penetration testing.
Table of Content
- inSSIDer
- Wireless NetView
- Microsoft Network Monitor
- NetSurveyor
- Kismet
- Airodump-ng
- Wash
- Wireshark
SSID acronym is used for Service Set Identifier also known as the network identification which is the name of the wireless network. This may be viewed by anybody with a wireless device within reach of your network. It could be set up to 32 characters long and are case-sensitive of your choice.

After the network manager has set up the SSID, the router or another Wi-Fi base station broadcasts it to the surrounding region. Then when a device scans the neighboring networks, its SSIDs are displayed—the user only has to pick the one and connect to the device.

In Wi-Fi Pentesting, we need to discover SSID, Security, Channels, and connected client for further exploitation. Through this post, I divulge some tool names that may help you to discover the following:
- Wi-Fi Network Name
- MAC Address
- Channel
- Wifi Mode
- Client
- Security
inSSIDer
inSSIDer analyzes the configuration of your WiFi including channel settings, security, signal strength, and the impact of neighboring WiFi networks. It is easy to install and use for enumeration neighboring WiFi networks.
Download it from here

After execution, it will list all SSIDs and select an SSID in which you are interested.

Wireless NetView
Wireless NetView is a small utility that runs in the background and monitors the activity of wireless networks around you. For each detected network, it displays the following information: SSID, Last Signal Quality, Average Signal Quality, Detection Counter, Authentication Algorithm, Cipher Algorithm, MAC Address, RSSI, Channel Frequency, Channel Number, and more.
Download it from here
This tool is very easy to use, unzip the folder and run the executable file which will start SSID scanning and will list neighbouring Wi-Fi networks.

Microsoft Network Monitor
Microsoft Network Monitor is a tool for viewing the contents of network packets that are being sent and received over a live network connection or from a previously captured data file. It provides filtering options for the complex analysis of network data.
Note: To use this tool you may need an external wi-fi adapter.
You can download it from here:

NetSurveyor
NetSurveyor is a diagnostic tool that falls under the category of WiFi Scanners or 802.11 Network Discovery Tools. The best known in this category is NetStumbler. A discovery tool reports the Service Set Identifier (SSID) for each wireless network it detects, along with the channel used by the access point (AP) servicing that network.
You can download it from here:

Kismet
Kismet is an 802.11 layer-2 wireless network and device detector, sniffer, wardriving tool, and WIDS (wireless intrusion detection) framework. Kismet works with Wi-Fi interfaces, Bluetooth interfaces, some SDR (software-defined radio) hardware like the RTLSDR, and other specialized capture hardware. Kismet works on Linux, OSX, and, to a degree, Windows 10 under the WSL framework.
Start the Kismet server, using the wireless interface as the capture source (-c wlan0mon)
Note: To use this tool you may need an external wi-fi adapter.

The service will be running at localhost on port 2501 which is accessible through web browser http://localhost:2501

Kismet will enumerate neighboring WiFi networks along with their MAC address and Encryption type.

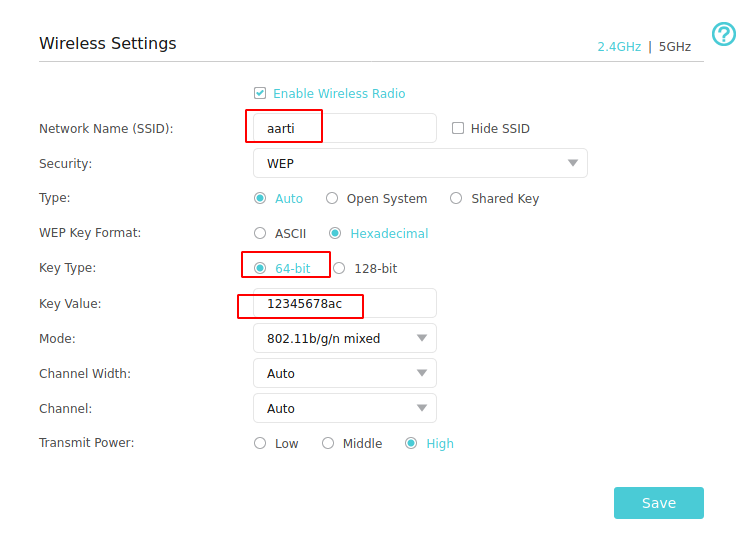
If you choose any Network ID it will depict the Wi-Fi configuration details. As you can see, we are interested in “SSID: AARTI” that has WEP encryptions 😱 (less secure and highly exploitable).

Airodump-ng
Airodump-ng is included in the aircrack-ng package and is used for packet capturing of raw 802.11 frames. It is ideal for collecting WEP IVs for use with aircrack-ng. If you have a GPS receiver connected to the computer, airodump-ng can log the coordinates of the discovered access points.
Note: To use this tool you may need an external wi-fi adapter.

The following command monitors all wireless networks, frequency hopping between all wireless channels.
airodump-ng wlan0mon

Wash
Wash is a tool for discovering WPS-enabled access points. It may either survey from a live interface or scan a list of pcap files. Wash is included in the Reaver package. It comes preinstalled in Kali Linux and you can execute the following command for SSID discovery.
wash -I wlan0mon
Note: To use this tool you may need an external wi-fi adapter.

Wireshark
Wireshark is the world’s foremost and widely-used network protocol analyzer. It lets you see what’s happening on your network at a microscopic level. It is also WAN/LAN Analyzer and Decryption support for many protocols, including IPsec, ISAKMP, Kerberos, SNMPv3, SSL/TLS, WEP, and WPA/WPA2
Note: To use this tool you may need an external wi-fi adapter for SSID discovery.

Start Wireshark and choose the interface for the Wi-Fi adapter and it will list all network ID available in the surroundings.

Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here