2021-07-30 18:34:39 Author: infosecwriteups.com(查看原文) 阅读量:38 收藏
Hello everyone, today I will be talking about one of the critical bugs which I found in the Oracle Corporation. Now, let’s start with the recon process
Step 1 :
1)There are multiple tools by which you can get subdomains, a few of them are given below…
i) Findomain
ii) Subfinder
iii) knock.py
2) To get the live host from the subdomain list, we can use tools such as
i)httprobe
ii) httpx
Now I prefer to use findomain for getting my results quickly. So the command would look something like this….
Command : findomain -t oracle.com| httpx -title -status-code | tee oracle.txt
Step 2 :
You need to gather some more endpoints to find P1 bugs and for that, you can use Waybackurls and Gau.
Step 3 :
Now, I was looking for admin portals to get unauthenticated access and for that, I searched for some endpoints.
Endpoints :
i)dev.
ii)stag.
iii)admin.
iv)internal.
v)stag-dev.
vi)stag-admin.
vii)internal-dev.
viii)_dev.
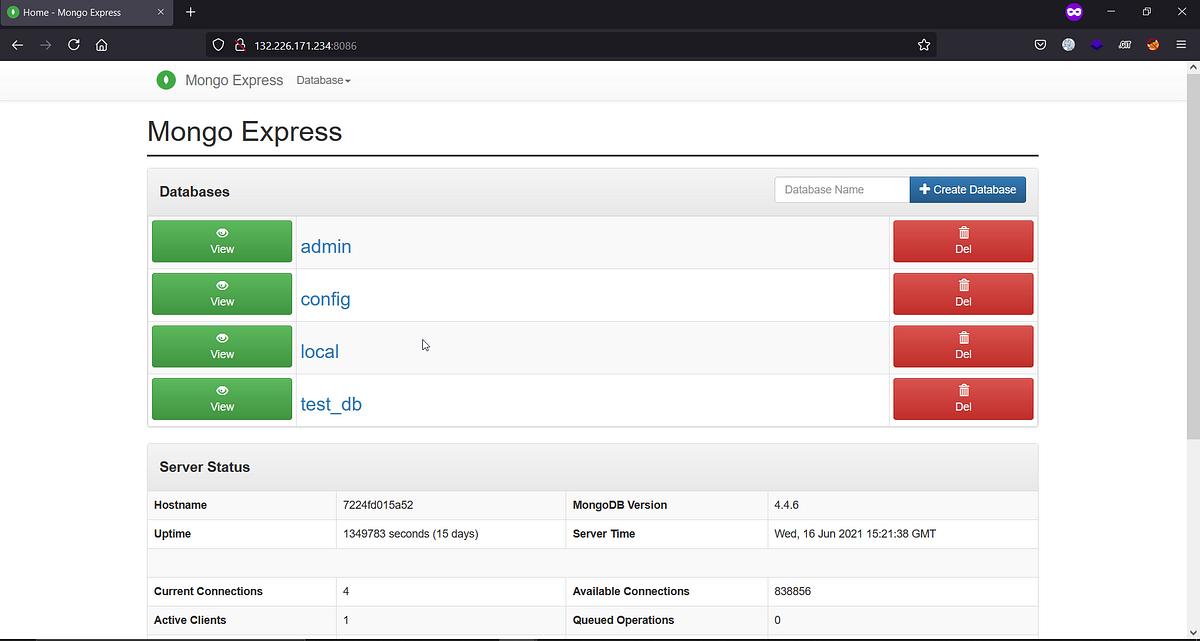
There are more endpoints that you can find out by opening the URLs one by one from waybackurls, gau, and then add the endpoints to your list. I got my endpoint which started with stag-dev. There were 2 links that opened the MongoDB database. I changed the DNS to IP to see what kind of changes can be seen over here and I found out that it was working on the 8086 port.
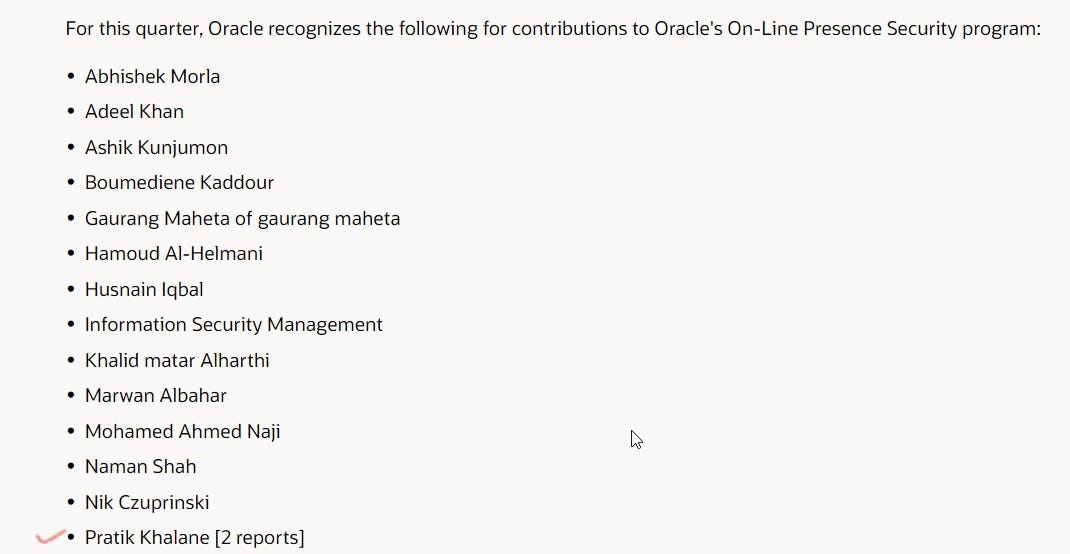
After reporting this issue to Oracle Corporation, I’m honored on their Hall of Fame page.
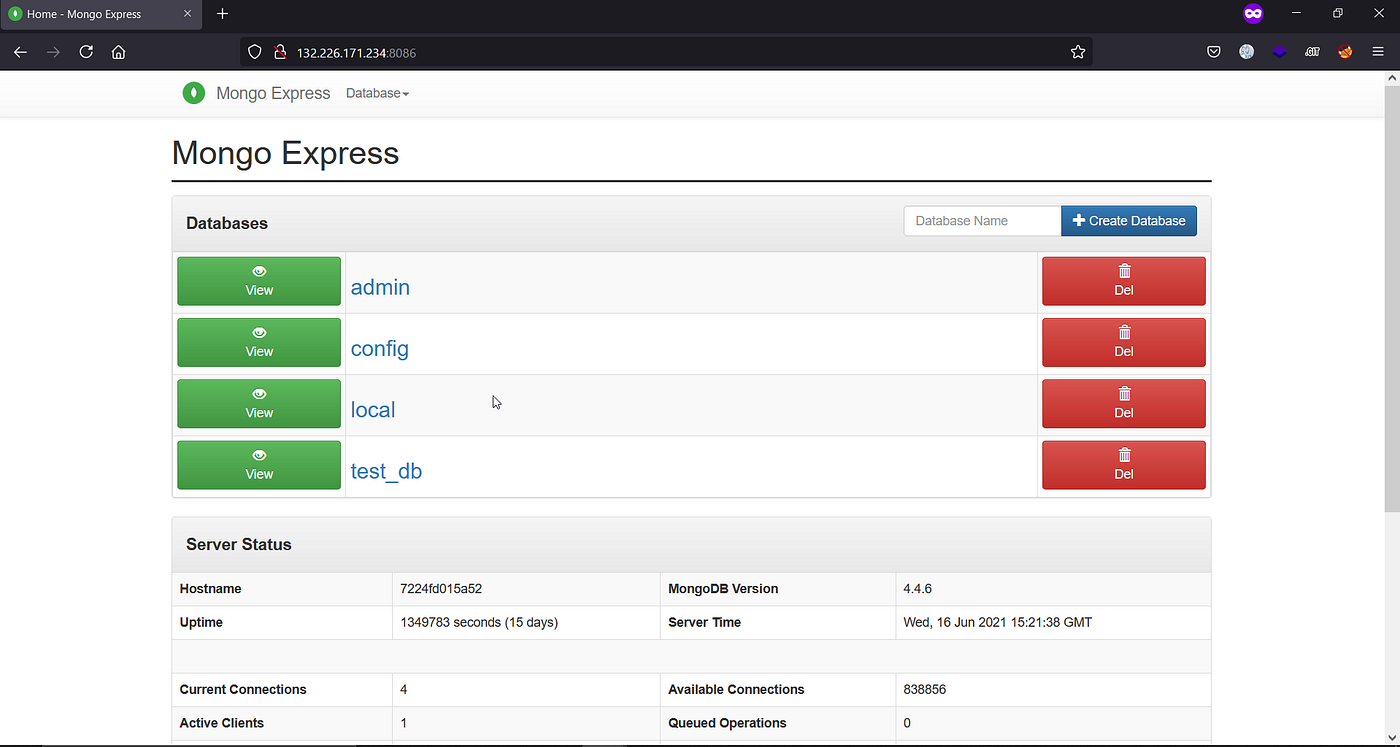
They removed the whole website and blocked all of the access to the MongoDB database.
Timeline
- Reported: June 15
- Mitigated: June 16
- Acknowledged in the hall of fame: July 21
Always try to find new endpoints using different tools and make a list of them.
Stay tuned for more writeups.
如有侵权请联系:admin#unsafe.sh