2021-08-24 21:53:18 Author: blog.elcomsoft.com(查看原文) 阅读量:37 收藏
iMessage, Hangouts, Skype, Telegram, Signal, WhatsApp are familiar, while PalTalk, Pigin, Psi Jabber client, Gadu-Gadu, Gajim, Trillian, BigAnt or Brosix are relatively little known. The tools from the first group are not only more popular but infinitely more secure compared to the tools from the second group. In this publication we’ll review the authentication methods used by the various instant messengers, and attempt to extract a password to the user’s account.
Do instant messengers store passwords?
Many modern instant messengers gave up using passwords for authentication purposes, let alone store them on the user’s device. How does authentication work in that case, and what do they use instead?
WhatsApp does not use passwords. Instead, the user is authenticated and a new device authorized based on the user’s phone number. Notably, authorizing a new phone with WhatsApp de-authorizes the previously used one. This is exactly what happens when experts use forensic tools to access WhatsApp data, and there is currently no known workaround to prevent such behavior. Users can opt to use a PIN as a second authentication factor, yet such PIN codes are only verified on the server and are never stored (even in a hashed form) on the user’s device.
Telegram uses a somewhat similar authentication method. The original link is established based on the user’s phone number, but the user may optionally set up two-factor authentication with a password. Here, the password is the second authentication factor, while the initial authentication step is a single-use code delivered as an instant message to one of the already authenticated devices or as a text message to the user’s phone number. Quite obviously, the password is verified on the server, and never stored (even in a hashed form) on the user’s device. Unlike WhatsApp, Telegram allows multiple linked devices, so authorizing a new device does not de-authorize any previously used ones. Newly authenticated devices receive full access to the user’s past communication history (except private chats). In addition to the password protecting the user’s Telegram account, the Telegram app installed on a device can be also protected with a passcode. This is a separate setting unrelated to account protection.
In both cases, even if the password is used, it’s never stored on the device, not even as a hash. Therefore, extracting or brute-forcing a WhatsApp PIN or Telegram password is out of the question unless the user keeps them elsewhere (e.g. in iOS Keychain or Web browser).
Skype is a whole new animal. Once an independent instant messenger, Skype is now owned by Microsoft, who pushed Skype logins under the umbrella of Microsoft Account services. Windows 8 and Windows 10 users who sign in to their computers with a Microsoft Account (as opposed to using a standalone login and password) enjoy fully a automatic sign in experience when they launch Skype on their computer.
While Skype does use the login and password authentication, it does not store the password on the computer. However, Windows does – if you use the same Microsoft Account to log into Windows! This fact enables the following possibilities:
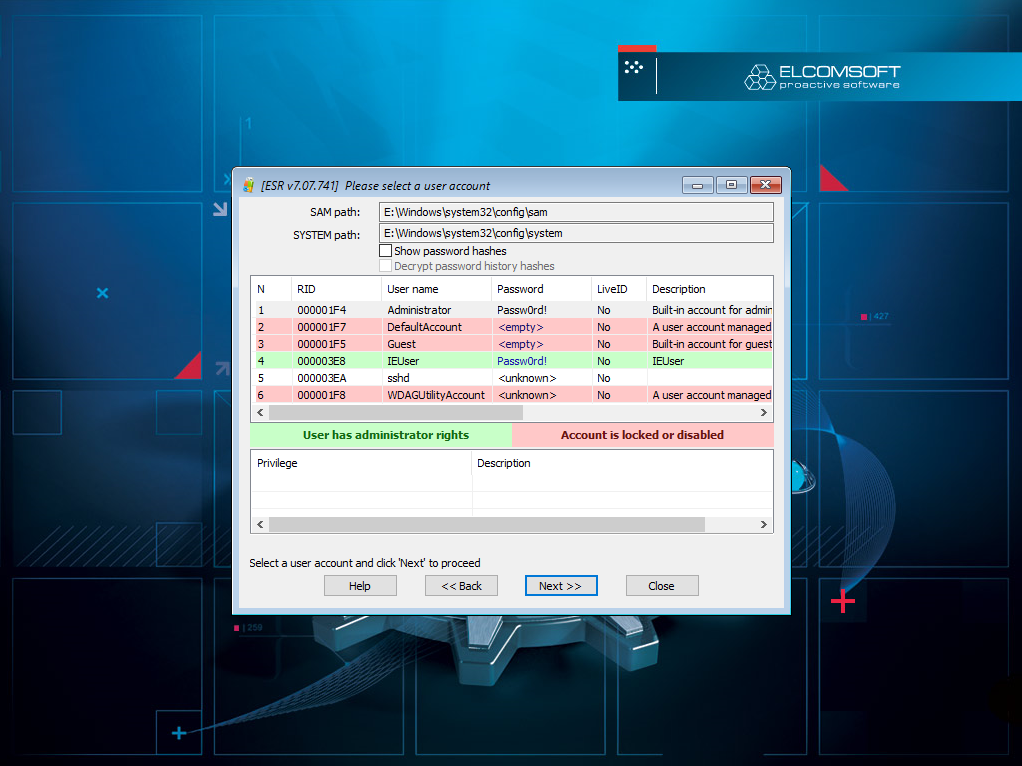
- Break Microsoft Account password, if one is used to sign into Windows. This approach won’t work if the user has a local Windows account (and not Microsoft Account). If, however, they do use Microsoft Account credentials to sign in to Windows, the password can be attacked with a high-speed, hardware-accelerated attack that runs on local hardware. Once recovered, the password can be used to access OneDrive data, Skype conversations, and even passwords stored in Microsoft Edge. More information in Analyzing Microsoft Timeline, OneDrive and Personal Vault Files | ElcomSoft blog.To run an attack on the user’s login credentials, one can use Elcomsoft System Recovery to extract password hashes, which can then be attacked with Distributed Password Recovery. The potential roadblocks may include BitLocker encryption and two-factor authentication, which may be requested by Microsoft when attempting to sign in from a new device even if the user never enabled two-factor authentication for their account.
- The password can be also extracted from iOS keychain with Elcomsoft Phone Breaker if the user has an iOS device. You’ll be looking for records containing one of Microsoft-owned domains such as hotmail.com, live.com, outlook.com, microsoft.com, office.com and a few others.
- The password can be also extracted from the user’s Google account with Elcomsoft Cloud Explorer. This only works if the user stored the password on their Android device or the Chrome browser. You will require the Google Account password to extract that data.
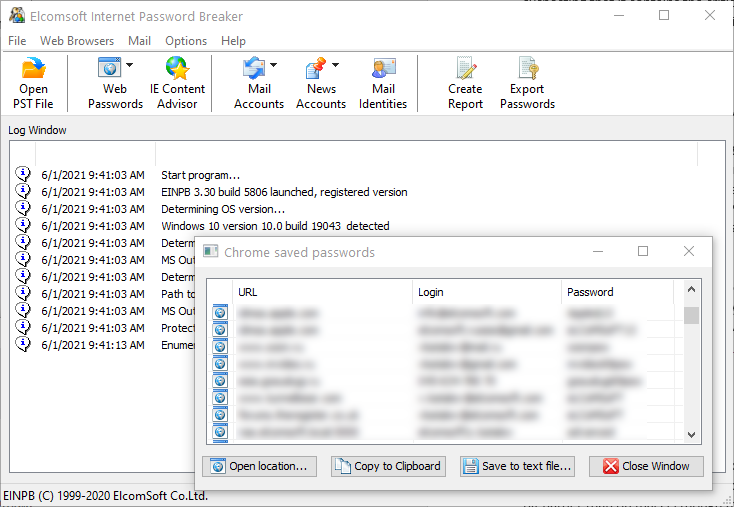
- If you have access to a live computer with authenticated user session, you may be able to extract said password from the local Web browser (e.g. Edge, Chrome, Firefox etc.) with Elcomsoft Internet Password Breaker.
- Last but not least, you may be able to transfer the user’s authenticated Skype session from their computer to a different PC, with full access to past conversation histories. The transfer can be performed using Advanced IM Password Recovery.
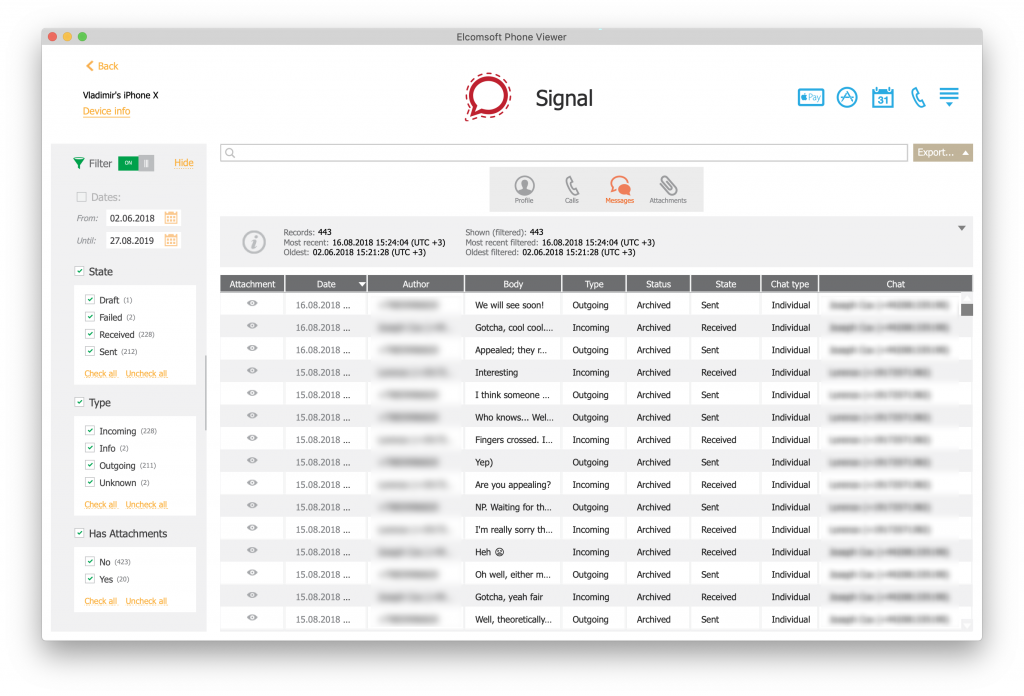
What about Signal? The PC version of this secure instant messenger does not use a password (and thus does not store it). In order to initialize a new instance of Signal, the user must perform an interactive pairing procedure using their smartphone and the previously authenticated Signal instance. The newly initialized Signal instance does not receive access to past conversations, making such pairing rather pointless from the forensic point of view. The only way to extract Signal conversations from an iPhone is via low-level extraction as shown in this article.
Instant password extraction
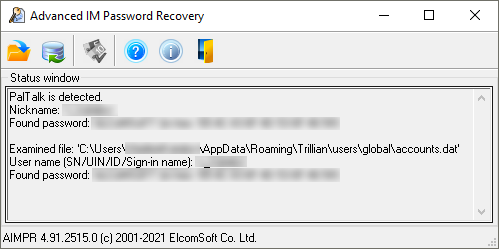
Most popular instant messengers are secure, and most of them are neither using nor storing passwords on the computer. However, a great number of communication tools do! The list goes on and on: ICQ and ICQLite, AOL Instant Messenger, AIM Triton, AIM Pro, Yahoo! Messenger, MSN Messenger, Windows Live Messenger, Google Talk, Trillian и Trillian Astra, Odigo, Jabber IM, Miranda, Tencent QQ, Ipswitch Instant Messenger, Psi Jabber client, QIP Infium, Gizmo Project, MySpace IM, Exodus, Gadu-Gadu, Mail.Ru Agent, Just Another Jabber Client, Pidgin and a lot more apps listed on this page either keep a copy of the original password on the computer, or store a password hash that can be transferred to another computer. We’ve also added PalTalk, Pigin, Psi Jabber client, Gadu-Gadu, Gajim, Trillian, BigAnt, and Brosix to the list of IMs we can extract passwords from.
For any app from this list, you can use Advanced IM Password Recovery to extract the login and password. If the password is not stored, you will be able to extract the stored authentication credentials (everything required to log in, including the password hash or authentication token), and transfer the “authenticated session” to another computer.
Additional information
If you are looking for more information about instant messengers, check out Forensic guide to iMessage, WhatsApp, Telegram, Signal and Skype data acquisition in our blog to learn about the extraction of IM data from iOS devices and cloud services.
REFERENCES:
![]()
Advanced IM Password Recovery
Retrieve the login and password information to various instant messengers in an instant. Advanced Instant Messengers Password Recovery instantly unlocks IM accounts and recovers forgotten passwords to many popular messengers. Advanced Instant Messengers Password Recovery supports over 70 popular instant messengers such as AOL, ICQ, MSN, and Yahoo!
Advanced IM Password Recovery official web page & downloads »
![]()
Elcomsoft Cloud eXplorer
Learn what Google knows about you! Download information directly from the Google Account with or without a password. Elcomsoft Cloud Explorer enables over-the-air acquisition for a wide range of Google services including Contacts, Hangouts Messages, Google Keep, Chrome browsing history, search history and page transitions, Calendars, images, location and a lot more.
![]()
Elcomsoft Distributed Password Recovery
Build high-performance clusters for breaking passwords faster. Elcomsoft Distributed Password Recovery offers zero-overhead scalability and supports GPU acceleration for faster recovery. Serving forensic experts and government agencies, data recovery services and corporations, Elcomsoft Distributed Password Recovery is here to break the most complex passwords and strong encryption keys within realistic timeframes.
Elcomsoft Distributed Password Recovery official web page & downloads »
![]()
Elcomsoft iOS Forensic Toolkit
Extract critical evidence from Apple iOS devices in real time. Gain access to phone secrets including passwords and encryption keys, and decrypt the file system image with or without the original passcode. Physical and logical acquisition options for all 64-bit devices running all versions of iOS.
Elcomsoft iOS Forensic Toolkit official web page & downloads »
![]()
Elcomsoft Internet Password Breaker
Elcomsoft Internet Password Breaker instantly reveals passwords to Web sites, identities, and mailboxes stored in a variety of applications. Supporting all popular Web browsers and all versions of Outlook Express, Microsoft Outlook, Windows Mail and Windows Live Mail, Elcomsoft Internet Password Breaker helps you retrieve the login and password information to a wide variety of resources.
Elcomsoft Internet Password Breaker official web page & downloads »
![]()
Elcomsoft Phone Breaker
Gain full access to information stored in FileVault 2 containers, iOS, Apple iCloud, Windows Phone and BlackBerry 10 devices! Download device backups from Apple iCloud, Microsoft OneDrive and BlackBerry 10 servers. Use Apple ID and password or extract binary authentication tokens from computers, hard drives and forensic disk images to download iCloud data without a password. Decrypt iOS backups with GPU-accelerated password recovery.
![]()
Elcomsoft System Recovery
Reset passwords to local Windows accounts and Microsoft Account and perform a wide range of administrative tasks. Assign administrative privileges to any user account, reset expired passwords or export password hashes for offline recovery, and create forensic disk images. Elcomsoft System Recovery is ready to boot thanks to the licensed Windows PE environment, allowing administrators to access locked computers.
![]()
Elcomsoft Explorer for WhatsApp
Elcomsoft Explorer for WhatsApp is a tool to download, decrypt and display WhatsApp communication histories. The tool automatically acquires WhatsApp databases from one or multiple sources, processes information and displays contacts, messages, call history and pictures sent and received. The built-in viewer offers convenient searching and filtering, and allows viewing multiple WhatsApp databases extracted from various sources.
Elcomsoft Explorer for WhatsApp official web page & downloads »
如有侵权请联系:admin#unsafe.sh