While unpatched installations of Magento 2 contain many vulnerabilities, I’m going to focus my attention on Magento 1 for this article. This is because Magento 2 provides regularly updated patches for many of the most common vulnerabilities targeting the platform. While Magento 1 also contains patches for many known vulnerabilities, those patches are not currently maintained.
Magento 1 reached its end-of-support on June 30, 2020. When Magento 2 was released, the focus was to improve security, include speed improvements, support the latest PHP installations, include SEO optimizations and provide a more user-friendly interface.
Despite this, Magento 1 continues to hold the lead in the number of installations between the two versions:

Image credit: https://www.similartech.com/compare/magento-1-vs-magento-2
It is understandable that developers and management teams are worried about migrating to the new platform. Magento can be heavily customized, and much of that code is developed specifically for each site. Migrating to a new platform or version can cost a great deal of time and money since a large percentage of those customizations cannot be easily ported to a newer version. This ability to heavily customize the code is also what leads to many of the critical vulnerabilities we frequently encounter. When your site has been compromised this can lead to thousands of dollars in repairs, and even more costly damage to your company’s reputation.
What if your site has become infected with a credit card swiper as can be seen in this Sucuri SiteCheck scan?
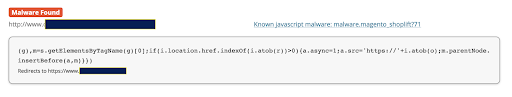
An injected credit card skimmer identified by our external monitoring
If so, your customers will hesitate purchasing from your site in the future, and they will let others know as well. In the case of common SEO spam, your site will display unwanted ads or redirect to other sites when visitors click your links in Google search results or other search engines.
One important note here is that many cases of credit card swipers are hidden well enough that a cursory scan is unable to identify them. The only way you will know that your site is infected is by receiving reports of suspicious credit card activity from your customers.
Prevalence of Malware
A Google search for ‘Magento 1 vulnerabilities‘ quickly uncovers an alarming number of articles detailing critical vulnerabilities and backdoors. Let’s consider these findings: According to an October 2020 report by independent cybersecurity company Foregenix, 93% of Magento 1 websites and 55% of Magento 2 sites are at a High/Critical Risk level:

From page 9 of the report above, we find the following data for card-harvesting malware distribution:
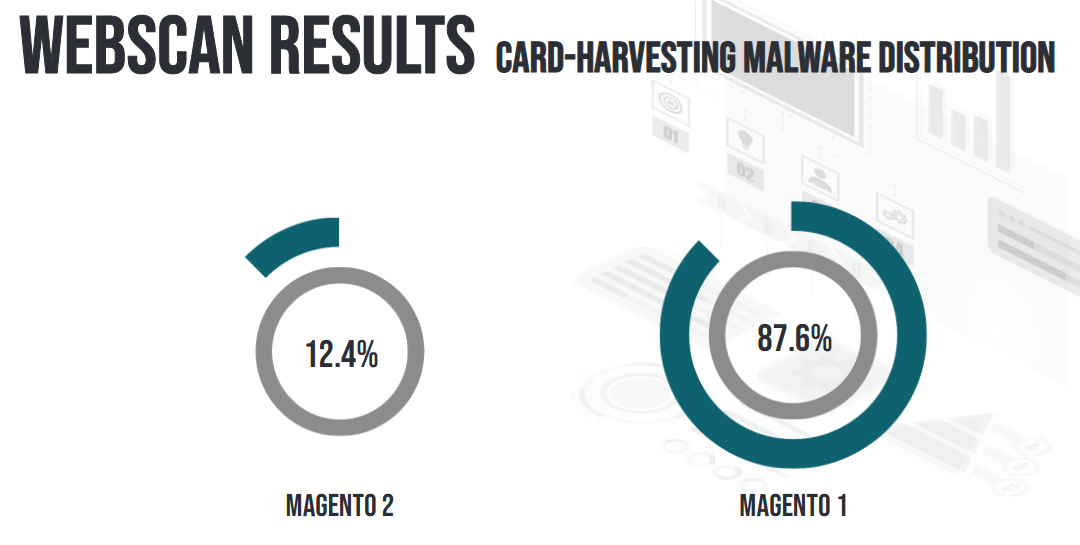
Magento 1 – 87.6% of known infected sites are using Magento 1
Magento 2 – 12.4% of known infected sites are using Magento 2
A large percentage of the attacks we see with Magento sites are credentials stealers and credit card skimmers, as we have covered in past blog posts:
- Examining Unique Magneto Backdoors
- Stylish Magneto Card Stealer Loads Without Script Tags
- Magneto Php Injection Loads Javascript Skimmer
Keeping Your Website Safe and Secure, Step by Step
Follow these seven steps to secure your Magento website as best as possible:
- Install all of the available security patches for your Magento installation. A great tool for checking your site for missing patches can be found at MageReport
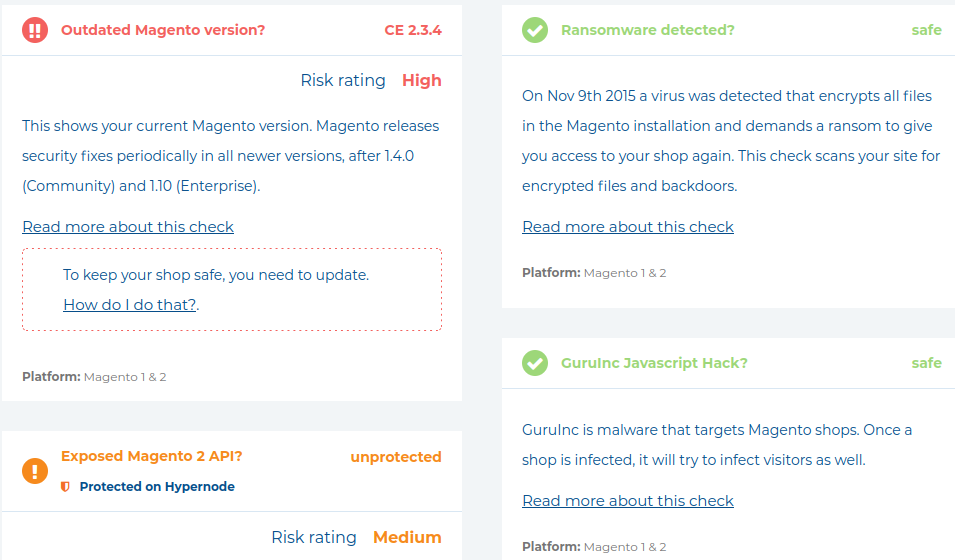
Once you have identified the patches you are missing, head over to the Magento Security Centre to download them. - Implement and follow the principle of least privilege. By limiting the number of administrator level accounts on your server and website, and ensuring that every user only has sufficient access to carry out their functions, you have greatly limited the number of points an attacker could use to infect your site. Compromised administrator accounts are one of the most common ways attackers gain access to servers and sites. You can find a detailed guide explaining this in our blog post, “What is the Principle of Least Privilege?”.
- Reduce the number of extensions or modules that your site uses. We often see sites that have a large number of plugins that are disabled, redundant or are simply not utilized at all. Since attackers are always looking for new ways to infect sites, they are also looking for security vulnerabilities in plugins. We find that unused or redundant plugins regularly go without being updated by the website administrators. When they are not utilized, those plugins are often forgotten and pose a risk. Since Magento is often used on VPS/private servers, you can take some additional steps in these environments to further secure your server.
- Regularly check for, and update, server-level patches on your server’s operating system installation. The method of obtaining these patches will depend on the operating system in use on your server. Be sure to check the documentation for details on your server’s operating system.
- Restrict access to services that are running on your server by implementing IP allow and block lists. For example, In most cases there is no need for your SQL or SSH ports to be accessible to everyone outside of your server.
- Use alternate ports and bind those ports to ‘localhost’ or ‘0.0.0.0’. By configuring MySQL to use port 3310, for example, and binding the service to localhost or 0.0.0.0, attackers would first need to guess the port that service is running on and then gain access to the server via SSH or some other method before they could gain access to the SQL server.
- Even if you have already restricted SSH to specific IPs, implement SSH key authentication. With key authentication, the connecting client would need to possess the private key before the server would authorize the user for logging in.Implementing these features is specific to the operating system your server is running, and those steps should be referenced in the available documentation for your server installation.
Securing the Magento Admin Panel
It is extremely important that the admin URL be changed since attackers will attempt to access the default path.
The admin URL can be configured in the admin panel by navigating to:
System -> Configuration -> Admin ->Admin Base URL
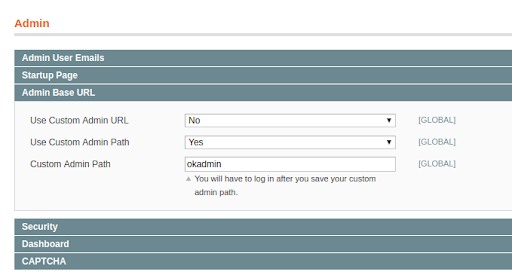
This is where we change the admin panel login URL
This is also accessible in the following configuration file:
./app/etc/local.xml
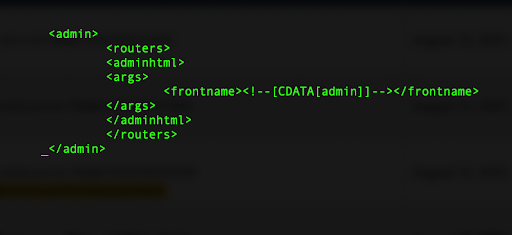
An example of the admin configuration section of a Magento config file
Forcing HTTPS Encryption
If an SSL certificate has been installed on your website, force HTTPS. This will ensure that your admin credentials are encrypted before they are sent to the server. To enable this option, login into the Magento admin panel and navigate to:
System -> Configuration -> General -> Web
From there, enable the “Use Secure URLs in Admin” option. Hopefully you have also enabled the option for “Use Secure URLs in Frontend” since your customers will be making purchases on your site.
Restricting Admin Access
Restricting access to the admin panel by IP address is an effective way to keep out attackers. By doing so, only authorized clients can navigate to the admin URL. This can be done by enabling the option in the site’s .htaccess file (for Apache). For example:
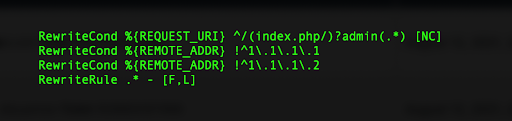
If your site is hosted on Nginx, you would need to configure that in the site’s configuration file:
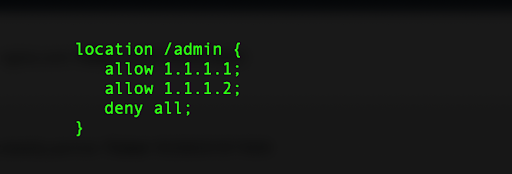
Note: If you have changed the admin panel path, you will need to update line 1 in the above examples to match that path. You will also need to update the allowed IPs in your configuration if your public IP changes.
Secure the Downloader
The Magento Connect downloader is a common attack point. You might consider changing the Connect Manager URL. You can also limit access to the /downloader directory by implementing IP restrictions on that path. How you do this is dependent on the version of Apache or Nginx your server is using.
The Sucuri Firewall service can also restrict access without needing to implement any of the server-side IP restrictions mentioned above and this can make managing those restrictions far easier.
Wrapping Up
With the continuous discovery of new vulnerabilities and malware, keeping your site protected can become overwhelming. This is why we offer our monitoring and firewall services. Our monitoring dashboard will regularly check your site against our world renowned malware signatures, and the firewall will filter all traffic to your website using those same signatures to stop attacks before they ever reach the server.
You can sign up to our protection and monitoring services here.
