Last week was the 20th anniversary of the Open Web Application Security Project (OWASP), and in honor of that date, the organization issued its long-awaited update to its top 10 exploits. It has been in draft form for months and has been updated several times since 2003, and before its latest iteration, in 2017.
In the past two decades, OWASP has become a sprawling series of projects, tutorials, knowledge bases, and other tools that are incredibly useful for application developers, corporate security managers, and penetration testers. If you haven’t spent much time browsing its content, I’d encourage doing so, as it’s very worthwhile and a tremendous learning resource. It incorporates the work of hundreds of volunteers, spanning hundreds of local chapters who give their time and energy to help improve the quality of applications and stop potential cyberthreats. It now has more than 200 different projects that cover topics such as mobile security, various testing tools such as WebGoat, and honeypots.

Image credit: Hugo Costa
The top 10 list is one of the major milestones of how application security – and particularly, the security of web-based applications – has evolved over the past couple of decades. Exploits have gotten more complex, attackers have gotten more skilled at finding ways to leverage their way into our networks, and malware kits have become common so that anyone with a web browser can pretty much launch anything at anyone at any time. Sadly, against that landscape, “not much has changed in terms of the actual exploits over the years,” said Jeff Williams, one of the originators of OWASP’s list back in 2003. Many of the items on those early lists are still on that of 2021, just packaged somewhat differently.
Here is a graphic comparing OWASP’s 2017 and 2021 lists:
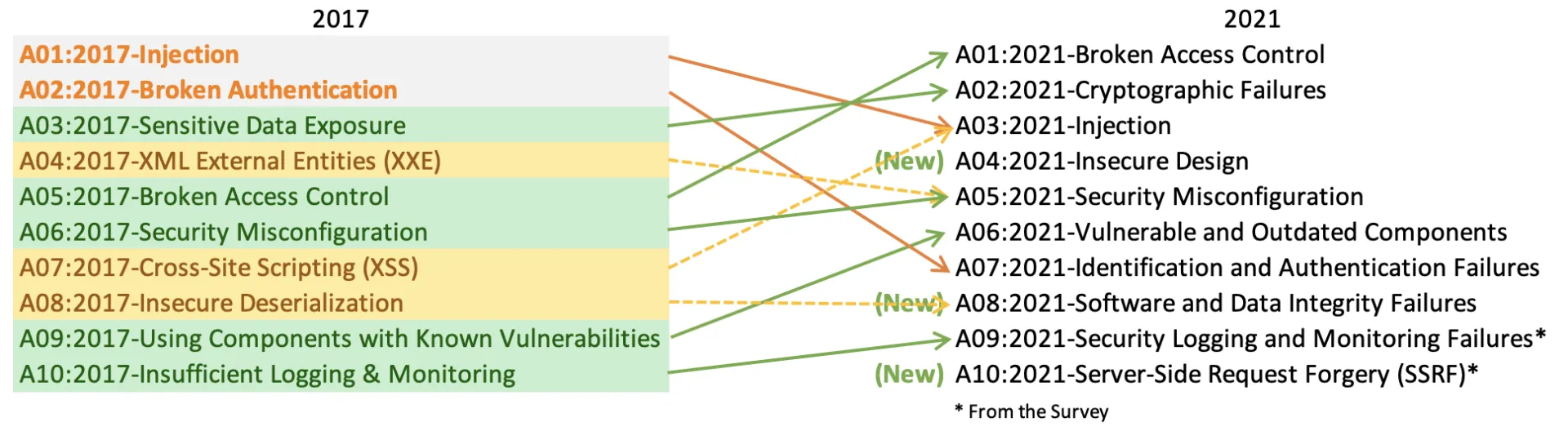
Image credit: OWASP
Threat data was collected from more than 500,000 applications and telemetry from several security vendor organizations and anonymous contributors. This made the top 10 collection cover a wider landscape, going from approximately 30 Common Weakness Enumeration (CWEs, or categories of vulnerabilities) in 2017 to almost 200 CWEs analyzed in this latest dataset.
The project team realized that they couldn’t use such a pared-down list of exploits because “it wasn’t helpful for awareness, training or baselines,” as they wrote on their website describing the new selection process. “We wanted to build risk categories of groups of related CWEs, focusing more on root causes and symptoms,” they wrote. If you examine the new top 10 list, you will see that each entry (except one, and I’ll get to that one in a moment) covers multiple vulnerabilities.
A closer look at the 2021 OWASP top 10 vulnerabilities
This year’s top list of vulnerabilities, in order from most to least important, are as follows:
- Broken access controls, when unauthorized users can gain access to administrator or other accounts to do further damage. This rose to the top spot this year because these vulnerabilities were found in more than 90% of the applications analyzed, which is far more than any of the other items on the list. “Every application gets attacked every month with a broken access control attack,” said Williams.
- Cryptographic failures, when private data is unprotected either in a storage container or transmitted without any encryption (or with easily cracked encryption) online. Better cryptographic methods and understanding the various algorithms are called for.
- Injection, where an attacker sends invalid or malicious data to a web app. Common abuses include SQL injections and Cross-Site Scripting (XSS) attacks, the latter being its own top 10 item on many earlier lists. These attacks were also found in more than 90% of applications analyzed.
- Insecure design, which is a completely new item and a new direction for the top 10. It was included to focus on threat modeling and security architectures and applications pre-planning, what some folks call “shifting left.” This item shows that the architectural design of an application plays a key role in how secure the software is when it goes into production. OWASP joins the National Institute of Standards and Technology and the Payment Card Institute, which both added threat modeling to their latest standards.
- Security misconfiguration. This category includes two 2017 top 10 categories, XML external entities and security misconfigurations, and was found in 90% of applications analyzed. The former is where attackers take advantage of sending malicious XML inputs. This happens when poorly written code doesn’t check for valid XML and malware can be uploaded to a web server or application. The latter covers other software coding configuration issues.
- Vulnerable and outdated components, which is an interesting top 10 item because it doesn’t include any known vulnerabilities yet is still found in many applications, such as depending on third-party code libraries that have their own exploits. This item also includes not checking for outdated components.
- Identification and authentication failures. This happens thanks to reused passwords or weak credentials, such as missing multi-factor authentication methods or sticking with default settings.
- Software and data integrity failures. This category includes software failures, such as the SolarWinds supply chain attack and other failures and include the 2017 category of insecure deserialization. As we build more complex applications, we must focus more care on the components and constantly vet their vulnerabilities.
- Security logging and monitoring failures, which covers how you obtain insights into how your applications operate and using run-time protection for your applications.
- Server-side request forgery (SSRF), also a new item for 2021. This one is an interesting choice, because it only includes one weakness but covers a wide range of circumstances that can create these attacks (without validating a URL, for example).
Key takeaways and recommended actions
OWASP members have three recommendations on how to improve the overall security of your applications:
- If you aren’t doing any threat modeling or penetration testing, now is the time to get more involved in using these tools and methods to help focus your security practices and understand your overall applications architecture.
- Figure out ways to automate your security processes to match the scale and reach of your applications infrastructure. One way to help guide your efforts is to test your security automation tools with the OWASP Benchmark Project to determine their effectiveness.
- Measure how long it takes you to fix vulnerabilities after you have discovered them. The industry average is many months, and this needs to be reduced to a matter of hours or days. It goes without saying that many threats could be minimized or thwarted entirely by a more prompt patching process.

