
2021-10-04 17:32:31 Author: infosecwriteups.com(查看原文) 阅读量:139 收藏

Hey amazing Hackers! its Raidh_Here
After many month, I decided to write writeups regarding my bounty from Google of worth $5000. So without wasting any time, lets begin the story!
After getting many duplicates and N/A from H1 & Bugcrowd, I decided to write about my journey and started searching for VDP programs. I got many bugs and reported to them but till then no reply . Finally, I decided to start hunt on google.
Started searching google subdomains using Google dorks. I know its piece of a shit but never mind. I found few domains and nothing work for me. So finally, I decided to test on google cloud.
While scrolling down in the google cloud market place I found an interesting application called Dialogflow

I started searching more about the application. Dialogflow is a natural language understanding platform used to design and integrate a conversational user interface into mobile apps, web applications, devices, bots, interactive voice response systems and related uses.
I started searching common bugs like xss,sqli,htmli.. etc.

But it didn’t work! :(
After doing a lot of search, I got an interesting Option

and started creating the phone gateway :)

It also has a delete option. I turned on my proxy and started intercepting the requests and I found a request like this .
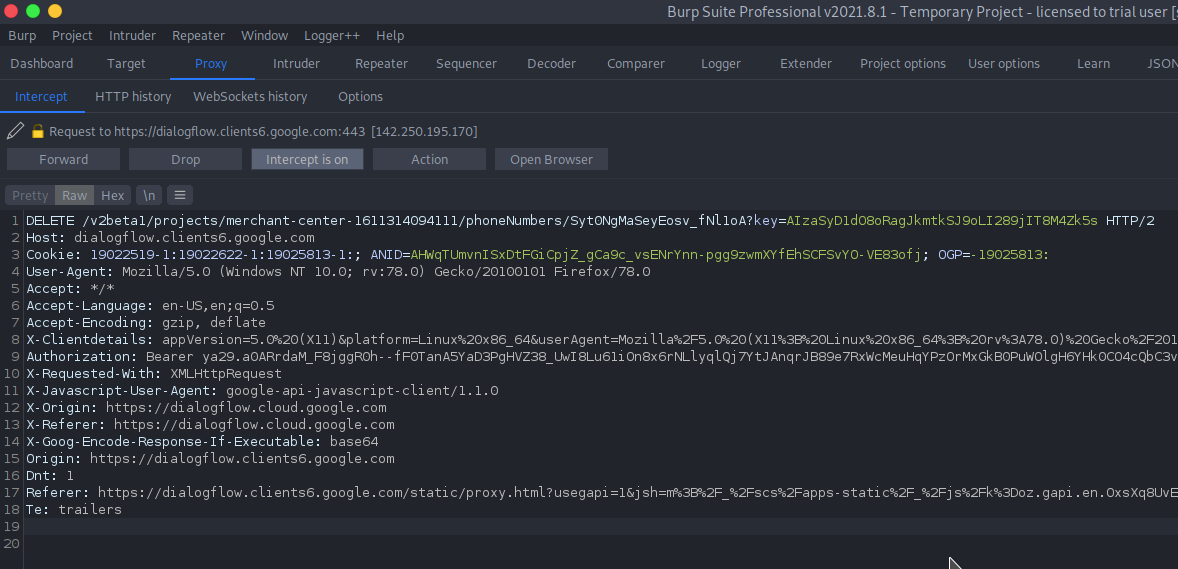
i send the request to burp intruder and added the points to some strings and created a-z character in the payload section. but it is very hard to get a hit. while checking the dialoglfow cx i saw the same Phone Gateway.


we can see there is a area code option to get specified phone numbers for that particular area.
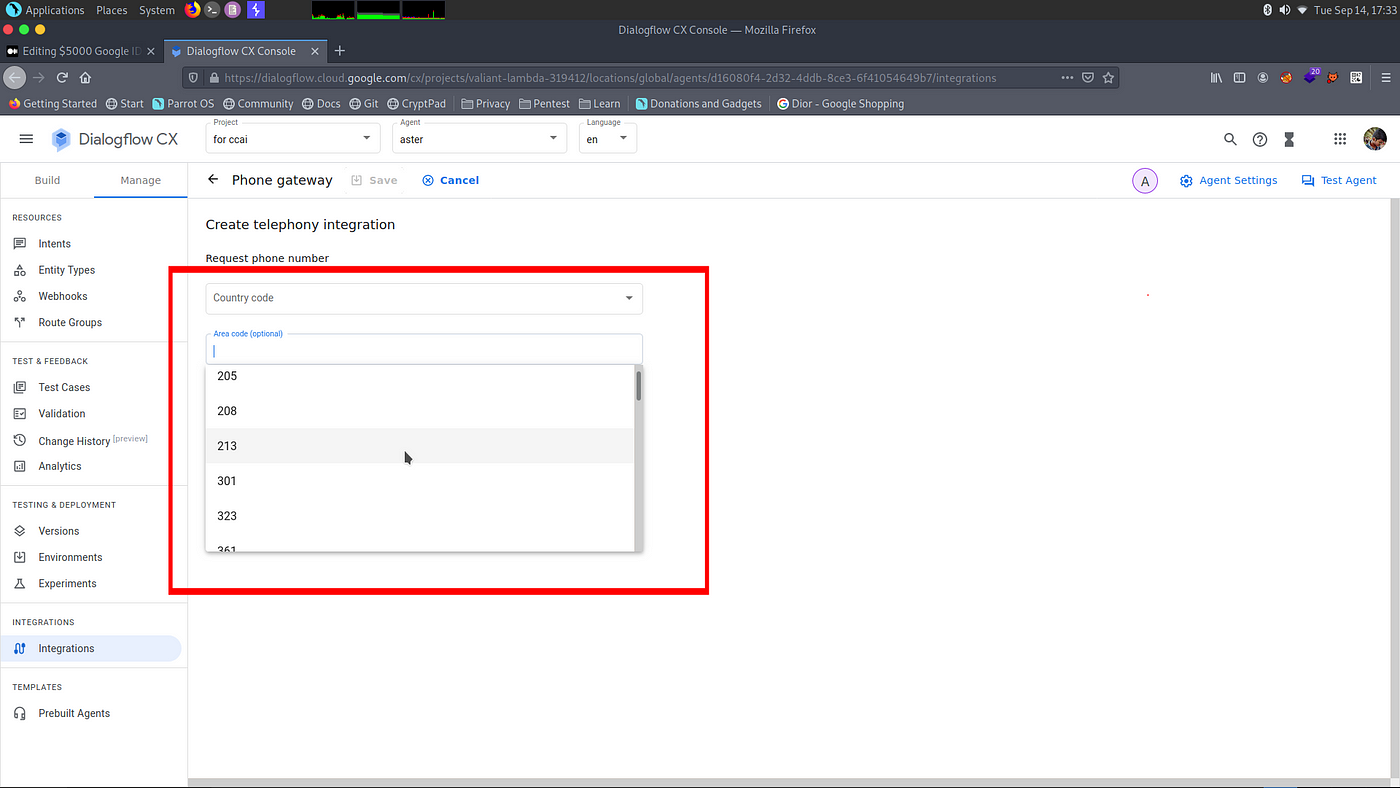
i selected the area code 205 so i got the active list of numbers belongs to 205. we can select all available area codes and able to fetch the all active random strings to create a word list.

I sent the request to burp repeater and replace the phoneNumbers/<randomstring> to the victims <randomstring> and submit the request.

BHOOOOOOOM!. The victim number got deleted and created a poc and reported to Google. But they closed the report as intended Behavior. Then, I was like ??!!

After explaining the attacking scenario and impact, they reopened and accepted the bug. Whooo hooo! and rewarded with $5000.
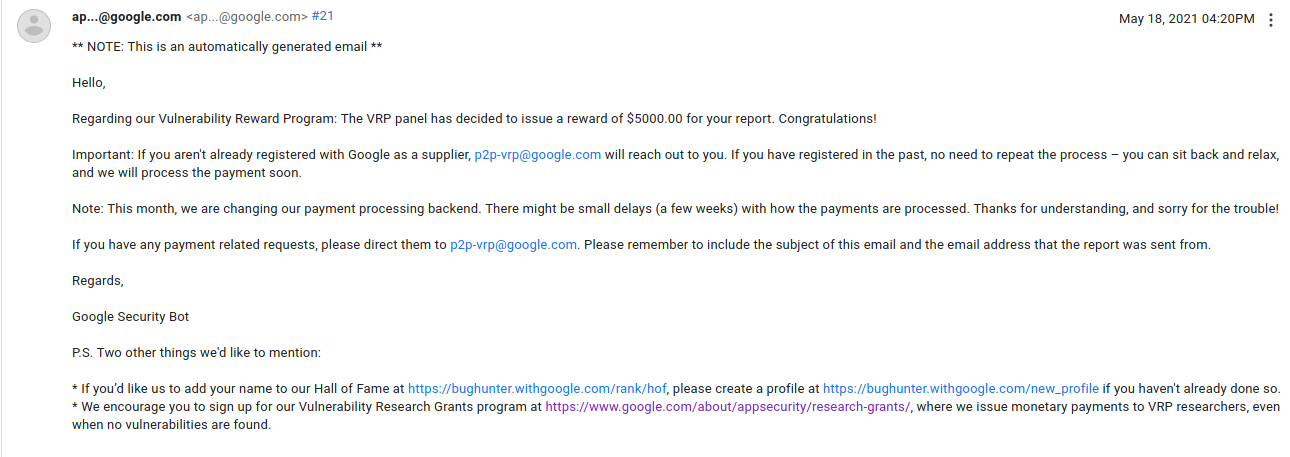
May 4, 2021 06:28AM — Reported
May 4, 2021 04:19PM — Status: Won’t Fix (Not Reproducible)
May 7, 2021 06:30PM — Status: Won’t Fix (Intended Behavior)
May 12, 2021 09:10AM — Status: Accepted (reopened)
May 18, 2021 04:20PM — Rewarded $5000 bounty
Aug 28, 2021 01:29AM — fixed.
如有侵权请联系:admin#unsafe.sh