2021-10-26 15:56:33 Author: blog.elcomsoft.com(查看原文) 阅读量:103 收藏
To perform an iCloud extraction, a valid password is generally required, followed by solving the two-factor authentication challenge. If the user’s iPhone is everything that you have, the iCloud password may not be available. By using a trusted device, one can gain unrestricted access to everything that is stored in the user’s iCloud account. This article gives a comprehensive walkthrough on this alternative authentication method.
What device-based authentication is and how it’s different from token-based authentication
If, for the purpose of iCloud extraction, the user’s Apple ID and password are not available, you may be able to use an alternative method for authenticating into iCloud. Currently, Elcomsoft Phone Breaker supports two alternative authentication methods: token-based and device-based.
Token-based authentication employs binary authentication tokens extractable from the user’s computer (currently, macOS systems only) to access limited sets of synchronized data stored in iCloud. The use of authentication tokens allows bypassing two-factor authentication even if no access to the second authentication factor is available. However, authentication tokens are tied to the computer they are extracted from, which means you must run Elcomsoft Phone Breaker on the user’s computer to make use of the authentication token. Currently, iCloud tokens extracted from Windows systems cannot be used for iCloud extractions. Tokens are not only device-specific, they are also short-lived, and must be periodically refreshed.
Device-based authentication offers significantly more than token-based authentication. This method offers unrestricted access to everything stored in the user’s iCloud account. This includes cloud backups produced by all devices on the same Apple account, iCloud photos, synchronized data, as well as end-to-end encrypted data such as iCloud keychain, Health, Safari history, and much more.
Device-based authentication means that, in place of the login and password, you can authenticate to iCloud with the user’s trusted iOS device such as an iPhone or iPad that is signed in to their Apple ID at the time of extraction. The trusted device must be unlocked and compatible with a jailbreak or the included agent app.
Pre-requisites
Using the new device-based authentication method has several requirements. First, you’ll need access to the user’s iOS device such as an iPhone or iPad that is signed in to the user’s Apple ID at the time of extraction. The device must be unlocked (known or empty screen lock passcode), and it must remain online and connected during the extraction.
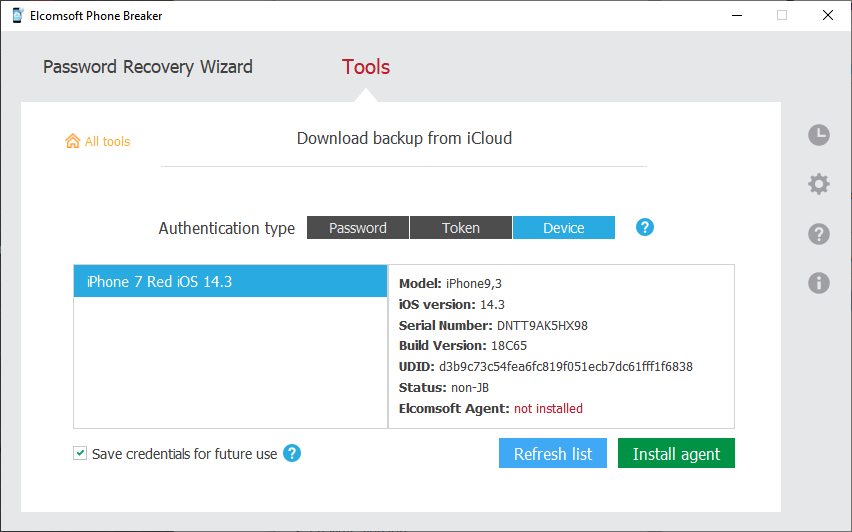
A jailbreak or agent app installation is required to perform device-based authentication. The agent app is included with Elcomsoft Phone Breaker and supports all 64-bit iOS devices running iOS 9.0 through 14.3. Sideloading the agent app requires a developer account with Apple if using Windows; macOS users may use a regular Apple ID to sideload the agent. The new agent app has the same compatibility requirements as the extraction agent used in iOS Forensic Toolkit.
Our solution has been tested on about a dozen devices from iPhone 5s to iPhone Xr, running iOS 9 to 14.8 (there is no jailbreak for iOS 15 today; there is no support for an extractor agent either). iPhone 11 and 12 devices are supported if they run a version of iOS supported by the agent app. At the same time, any data contributed from devices running iOS 15 (including cloud backups and synced data) will be successfully retrieved from the cloud even if the device that is used for authorization runs an older version of iOS.
We tested the solution with checkra1n, Electra and unc0ver jailbreaks.
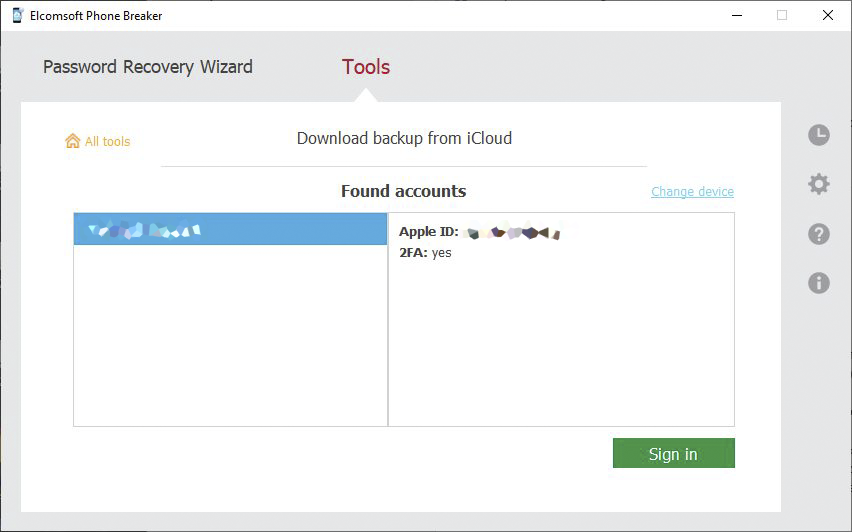
Trusted device authentication is exclusive to the Forensic edition, and is supported only for accounts with two-factor authentication. For accounts without 2FA, you can use a token from the keychain, which is also supported in EPB.
Using the new authentication method
To use a trusted device for iCloud extraction, follow these steps.
- Launch Elcomsoft Phone Breaker 10.0 or newer.
- Select Download from iCloud (backups, sync, drive)
- Observe the available authentication options: Password, Token, Device. Select “Device” to use the new method.
- Unlock and connect the trusted iOS device to the computer. Perform the required steps to establish trust between the device and the PC.
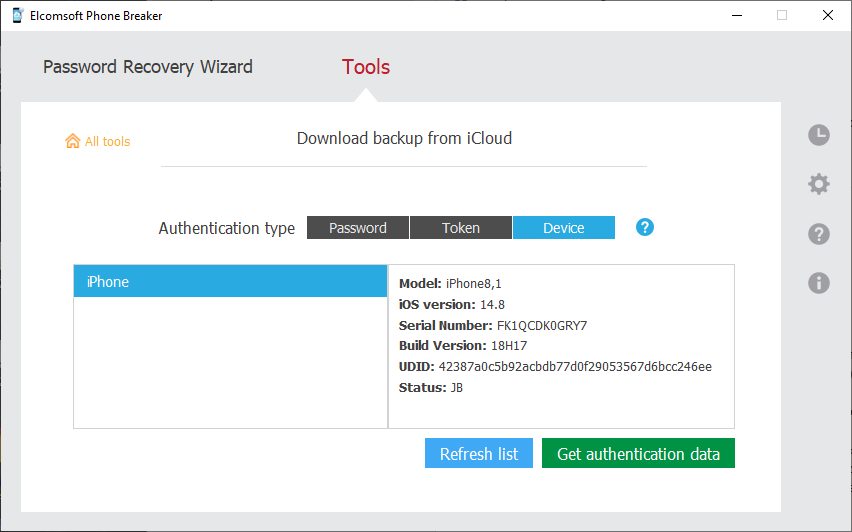
- You will now see the status of the device (jailbroken or not). If the device is jailbroken, proceed directly to extraction. The extraction agent will be installed transparently. If no jailbreak is installed, follow the steps to sideload and launch the extraction agent.
Sideloading the extraction agent
These steps are only required if the device has not been jailbroken. The agent app is included with Elcomsoft Phone Breaker and supports all 64-bit iOS devices running iOS 9.0 through 14.3.
- Sideload the extraction agent.
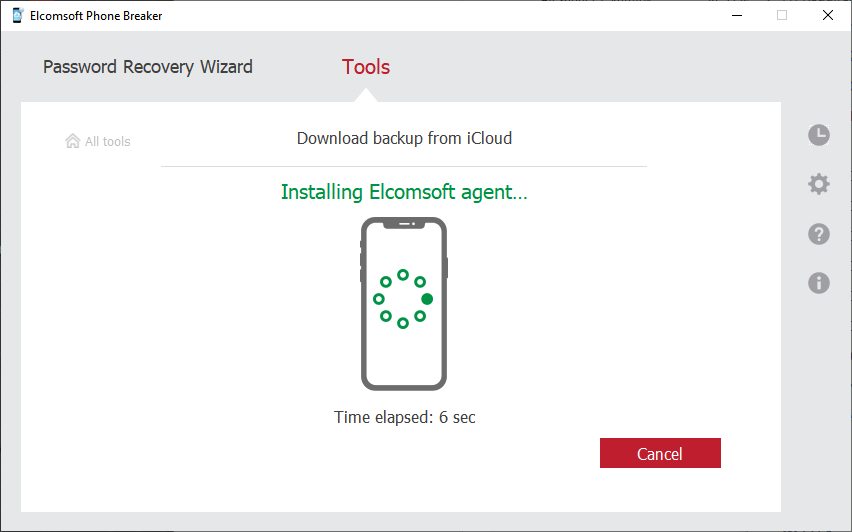

- Sideloading the agent app requires a developer account with Apple if using Windows; macOS users may use a regular Apple ID to sideload the agent.
- Manually launch the agent on the iOS device by touching its icon.
Extraction
The trusted device must be connected to the PC and kept online during the entire duration of the extraction. Once authenticated, you will see the list of available backups, synced data categories, or files from iCloud Drive.
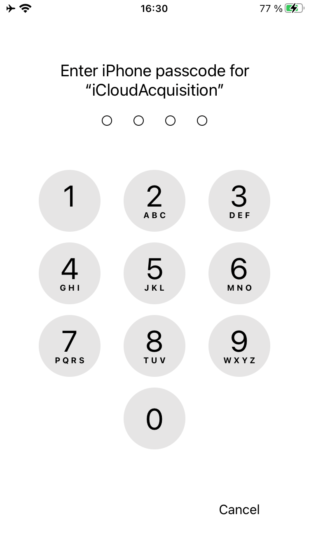
The extraction process using the new authentication method is similar to password-based authentication, with one exception: at some point, you will be prompted for a screen lock passcode on the device. Enter the screen lock passcode to enable access to certain records.
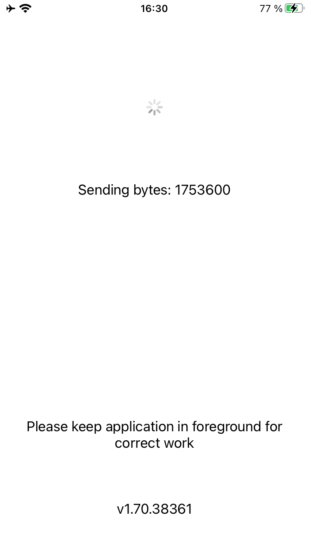
During the extraction, the device will display the following information:
Conclusion
The new authentication method offers the complete iCloud extraction, enabling experts to download iOS backups and synchronized data, including end-to-end encrypted categories. At this time, Elcomsoft Phone Breaker is the only third-party solution on the market allowing to access end-to-end encrypted data and iCloud backups saved by iPhone and iPad devices running any version of iOS. Pulling backups from the cloud is often the only means of accessing critical evidence that may no longer present on the iPhone itself.
Every year, Apple tightens security by placing more types of data under the end-to-end encrypted umbrella. Elcomsoft Phone Breaker is the only tool on the market that can recover many end-to-end encrypted categories including the user’s passwords from iCloud Keychain, iCloud Messages, Health, Screen Time, and Maps, and more.
REFERENCES:
![]()
Elcomsoft Phone Breaker
Gain full access to information stored in FileVault 2 containers, iOS, Apple iCloud, Windows Phone and BlackBerry 10 devices! Download device backups from Apple iCloud, Microsoft OneDrive and BlackBerry 10 servers. Use Apple ID and password or extract binary authentication tokens from computers, hard drives and forensic disk images to download iCloud data without a password. Decrypt iOS backups with GPU-accelerated password recovery.
如有侵权请联系:admin#unsafe.sh