2021-10-26 15:55:08 Author: blog.elcomsoft.com(查看原文) 阅读量:34 收藏
A lot of folks (and even some law enforcement experts) are looking for a one-click solution for mobile extractions and data decryption. Unfortunately, in today’s day and age there are no ‘silver bullet’ solutions. In the days of high-tech mobile devices and end-to-end encryption one must clearly understand the available options, and plan their actions accordingly. The time of ‘snake oil’ exploits is long gone. The modern world of mobile forensics is complex, and your actions will depend on a lot of factors. Today, we’re going to make your life a notch more complex by introducing a new iCloud authentication option you’ve never heard of before.
The complex world of cloud forensics
Being a mobile forensic specialist, you probably know of some manufacturers offering “magic solutions” that work straight out of the box, supporting unadvertised range of devices running a secret range of OS versions. In real life, those solutions only work in very specific conditions, on very specific devices, running very specific versions of the software. In order to use these and other tools efficiently, one must learn the theory, and one must constantly improve one’s level of knowledge from day to day. This is a factor of your success. I want to draw your attention at how important it is to understand the things happening under the hood, especially when performing cloud extractions where someone else has physical control over the data you’re attempting to access.
Today, I will introduce a very different methods for authenticating into iCloud when doing cloud extractions. But before I do this, let me briefly remind you of our achievements in iCloud extractions.
The iCloud extraction timeline
It’s been almost 10 years since we learned how to download iCloud backups; a lot of improvements has been made since then:
- May 2012: we were the first to download iCloud backups
- June 2014: we made it possible to access iCloud data without a password, using an authentication token
- August 2017: another first: we made it possible to access iCloud Keychain
- November 2018: we learned to download end-to-end encrypted data from iCloud including messages in iCloud and Health data
- October 2019: we can now download ScreenTime passcode and Voice memos
- You are here: we implemented passwordless device-based authentication for iCloud downloads
The benefits of iCloud firensics
I think there is no need to tell why iCloud acquisition is important in general. Even if you have an unlocked device compatible with low-level file system and keychain acquisition (and so Elcomsoft iOS Forensic Toolkit could do the job for you), you may not get the all the data theoretically available; more on that below. We have a good feeling that future iPhones will not have a Lightning port (latest Apple Watch already has diagnostics port removed, so even limited logical acquisition is not available anymore), while iCloud acquisition method should remain forever.
Why we developed trusted device authentication
REFERENCES:
![]()
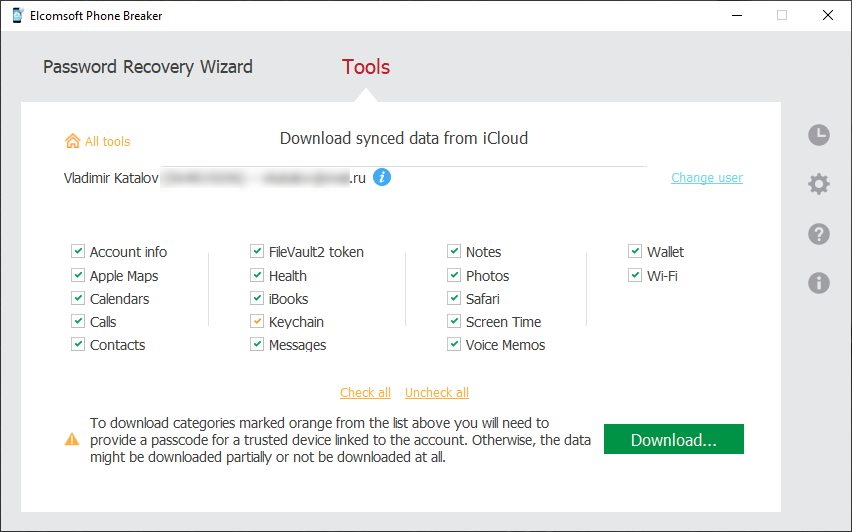
Elcomsoft Phone Breaker
Gain full access to information stored in FileVault 2 containers, iOS, Apple iCloud, Windows Phone and BlackBerry 10 devices! Download device backups from Apple iCloud, Microsoft OneDrive and BlackBerry 10 servers. Use Apple ID and password or extract binary authentication tokens from computers, hard drives and forensic disk images to download iCloud data without a password. Decrypt iOS backups with GPU-accelerated password recovery.
如有侵权请联系:admin#unsafe.sh