被人问到各种蜜罐的测评然后就想写一下各种开源蜜罐的测评报告,各种开源蜜罐地址可以在下面找到我也将按照里面的模板进行测评。
https://github.com/paralax/awesome-honeypots/blob/master/README_CN.md数据库蜜罐
MongoDB-HoneyProxy
MongoDB-HoneyProxy是为响应MongoDB Apocalypse而创建的
安装
我们看到代码可以发现这个蜜罐是起到代理mongodb的功能服务器启动mongodb后需要改变默认端口让蜜罐变成mongodb端口或者不用改变端口到时在docker映射出来。我在下面的命令映射出来端口为11111。
const net = require('net');
const ref = require('ref')
const fs = require('fs');
const bson = require('bson');
const parseArgs = require('minimist');
var args = parseArgs(process.argv);
/*process.on('uncaughtException', function (err) {
console.log("Client triggered an error.");
console.log(err.message);
})*/
if(args.h || args.help) {
console.log("Help:");
console.log("--address, -a: The ip of the dummy mongodb instance");
console.log(" Default: 127.0.0.1");
console.log("--port, -p: The port of the dummy mongodb instance");
console.log(" Default: 27016");
console.log("-l, --listen: The port to listen on");
console.log(" Default: 27017");
console.log("-o, --out: The file to output logs to");
console.log(" Default: proxy.log");
console.log("-h, --help: Displays this message and returns");
process.exit()
}
const EXTERNAL_PORT = args.listen || args.l || 27017;
const MONGODB_HOST = args.address || args.a || "127.0.0.1"
const MONGODB_PORT = args.port || args.p || 27016;
const LOG_FILE = args.out || args.o || "proxy.log";官方的dockerfile有问题改了一下
FROM ubuntu:18.04
RUN apt update -y
RUN apt install -y curl gcc g++ make mongodb
RUN curl -sL https://deb.nodesource.com/setup_8.x | bash -
RUN apt-get install -y nodejs
COPY . /opt/mongodb-honeyproxy
RUN cd /opt/mongodb-honeyproxy && npm install
#service mongodb start && cd /opt/mongodb-honeyproxy && node index.js -p 27017 -l 11111
#docker run -it -p 27017:11111 t运行
docker run -it -p 27017:11111 hon进入容器后运行下面的命令进行操作
启动服务
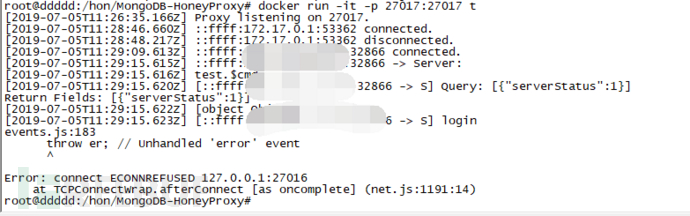
service mongodb start && cd /opt/mongodb-honeyproxy && node index.js -p 27017 -l 11111我为什么不直接entrypoint因为好像是mongodb和这个蜜罐原因导致不兼容只能这样玩不然会出现下面的情况使用nmap扫描的时候就会让蜜罐报错并退出
 运行成功在浏览器打开mongodb默认端口
运行成功在浏览器打开mongodb默认端口

前台显示攻击者访问的信息 
进入容器里面我们可以看到他生成了一个日志文件可以看到日志的组成是由源地址和访问的数据包。

注:后期修改文章重新测试的时候发现在浏览器打开的时候蜜罐会报错无解

总结
难易性★☆☆☆☆
可用性★★☆☆☆
展示性★☆☆☆☆
交互性★☆☆☆☆
这个蜜罐是用nodejs写的一个代理监控mongodb的蜜罐而且用起来有点不爽你要去兼容nodejs和蜜罐太麻烦了最后就是展示日志的时候捕捉的日志有点繁琐正常来说蜜罐只需捕捉攻击地址和攻击语句就行了。
Elastic honey
这个蜜罐四年都没有更新了当我使用docker-compose up的时候发现启动不了看了一下原来是配置文件设置了查询IP的接口这个接口已经失效了所以我就改了一个新的接口可以启动。

在下面json那段就是查询IP接口返回来的结果

在浏览器打开9200端口可以看出基本的交互性还是有的


当你要保存日志的时候一定要创建一个logs文件夹放置日志文件。从日志文件我们可以看出攻击者访问的路径参数攻击载荷头攻击地址。
总结
难易性★☆☆☆☆
可用性★★★★★
展示性★★★★☆
交互性★★☆☆☆
这个蜜罐安装很简单有着正常的ES的基本查询交互性还算可以。
mysql
这个项目是七年前的一个mysql监听蜜罐是基于windows的exe运行程序在现在看来作用很小这玩意就跳过了。
NoSQLpot
构建环境
FROM ubuntu:18.04
RUN apt update -y
RUN apt install -y git python-pip python-dev
RUN cd /opt && git clone https://github.com/torque59/nosqlpot.git
RUN cd /opt/nosqlpot && pip install -r requirements.txt这个蜜罐是用python写的模拟redis和couchdb的蜜罐。

redis测试


客户端对蜜罐进行连接 
服务端的日志信息可以看到攻击者输入了什么命令 
我们发现蜜罐和客户端之所以能够进行交互是因为写了回显规则。

couchdb演示

蜜罐记录的信息

发现客户端返回的结果与普通的couchdb没有什么区别

只不过当输入API命令的时候response就显得有点假了。

我们查看日志文件发现当用nmap扫描的时候会报错
root@08d68507730d:/opt/nosqlpot# tail -n 200 -f redis.log
Traceback (most recent call last):
File "/usr/local/lib/python2.7/dist-packages/twisted/python/log.py", line 103, in callWithLogger
return callWithContext({"system": lp}, func, *args, **kw)
File "/usr/local/lib/python2.7/dist-packages/twisted/python/log.py", line 86, in callWithContext
return context.call({ILogContext: newCtx}, func, *args, **kw)
File "/usr/local/lib/python2.7/dist-packages/twisted/python/context.py", line 122, in callWithContext
return self.currentContext().callWithContext(ctx, func, *args, **kw)
File "/usr/local/lib/python2.7/dist-packages/twisted/python/context.py", line 85, in callWithContext
return func(*args,**kw)
--- <exception caught here> ---
File "/usr/local/lib/python2.7/dist-packages/twisted/internet/posixbase.py", line 614, in _doReadOrWrite
why = selectable.doRead()
File "/usr/local/lib/python2.7/dist-packages/twisted/internet/tcp.py", line 243, in doRead
return self._dataReceived(data)
File "/usr/local/lib/python2.7/dist-packages/twisted/internet/tcp.py", line 249, in _dataReceived
rval = self.protocol.dataReceived(data)
File "/opt/nosqlpot/redispot/redisdeploy.py", line 37, in dataReceived
print "original data:"+str(rcvdata),
File "/usr/local/lib/python2.7/dist-packages/twisted/logger/_io.py", line 163, in write
string = string.decode(self._encoding)
exceptions.UnicodeDecodeError: 'ascii' codec can't decode byte 0x84 in position 15: ordinal not in range(128)
2019-07-12 03:33:15+0000 [-] End connection: 'ascii' codec can't decode byte 0x84 in position 15: ordinal not in range(128)
2019-07-12 03:33:15+0000 [-] New connection: 1 from 172.17.0.2
2019-07-12 03:33:15+0000 [RedisServer,17,172.17.0.2] Unhandled Error
Traceback (most recent call last):
File "/usr/local/lib/python2.7/dist-packages/twisted/python/log.py", line 103, in callWithLogger
return callWithContext({"system": lp}, func, *args, **kw)
File "/usr/local/lib/python2.7/dist-packages/twisted/python/log.py", line 86, in callWithContext
return context.call({ILogContext: newCtx}, func, *args, **kw)
File "/usr/local/lib/python2.7/dist-packages/twisted/python/context.py", line 122, in callWithContext
return self.currentContext().callWithContext(ctx, func, *args, **kw)
File "/usr/local/lib/python2.7/dist-packages/twisted/python/context.py", line 85, in callWithContext
return func(*args,**kw)
--- <exception caught here> ---
File "/usr/local/lib/python2.7/dist-packages/twisted/internet/posixbase.py", line 614, in _doReadOrWrite
why = selectable.doRead()
File "/usr/local/lib/python2.7/dist-packages/twisted/internet/tcp.py", line 243, in doRead
return self._dataReceived(data)
File "/usr/local/lib/python2.7/dist-packages/twisted/internet/tcp.py", line 249, in _dataReceived
rval = self.protocol.dataReceived(data)
File "/opt/nosqlpot/redispot/redisdeploy.py", line 37, in dataReceived
print "original data:"+str(rcvdata),
File "/usr/local/lib/python2.7/dist-packages/twisted/logger/_io.py", line 163, in write
string = string.decode(self._encoding)
exceptions.UnicodeDecodeError: 'ascii' codec can't decode byte 0x80 in position 26: ordinal not in range(128)总结
难易性★☆☆☆☆
可用性★★★★☆
展示性★☆☆☆☆
交互性★★★★☆
由于使用python写的模拟蜜罐基本安装依赖就非常容易和简单由上面可以知道这个蜜罐提供了两种功能一种是redis另外一种是couchdb在测试过程中发现他们的交互性还算可以基本可以返回常用的命令和API的信息。不过遗憾的是日志的处理一般般。
ESPot
一个用 NodeJS 编写的 Elasticsearch 蜜罐用于对 CVE-2014-3120 的利用。这个项目是五年前做出来的漏洞捕捉也是五年前的漏洞对于现在来说并没有什么用而且我尝试安装的时候被nodejs搞到崩溃安装不了所以这个项目就pass掉
Delilah
这款蜜罐是一个Elasticsearch蜜罐据文档所说他有分单机和节点监控程序是用python3启动的
FROM ubuntu:18.04
RUN apt update -y
RUN apt install -y git python-dev python-pip sqlite
RUN cd /opt && git clone https://github.com/SecurityTW/delilah.git
RUN pip install tornado requests如果直接启动如下面图一样提示错误原因就是你要在它的ini文件设置邮箱提醒。

不过让我觉得傻X的是当我设置了邮箱之后发现不能访问一直提示加载中服务器这边也没有接收到任何的提示。

这个是没有设置邮箱能够正常访问我们可以看出蜜罐跟正常的ES并没有什么区别交互性比较高

不过奇怪的是这个蜜罐的日志使用sqlite来存储的不过当我刷新页面的时候sqlite文件并没有添加日志内容大小还是一样我看了一下配置文件并没有设置sqlite的选项猜测问题出现在程序中问我问什么没有解决这个问题我只是做测评的不想去改错

还有就是节点监控那个程序并没有看毕竟单机已经这么不稳定了。。。
总结
难易性★☆☆☆☆
可用性★★☆☆☆
展示性★☆☆☆☆
交互性★★★★☆
mysql-honeypotd
低交互基于C语言的mysql蜜罐
构造环境
FROM ubuntu:18.04
RUN apt update -y
RUN apt install syslog-ng git gcc make libev-dev -y
RUN cd /opt && git clone https://github.com/sjinks/mysql-honeypotd.git
RUN cd /opt/mysql-honeypotd && make 
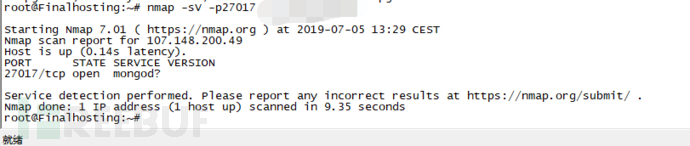
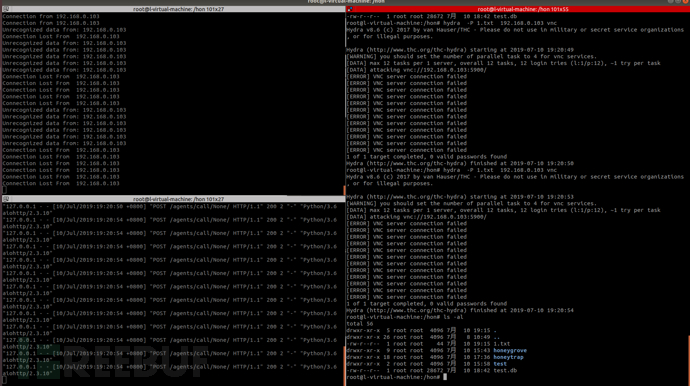
使用nmap看一下可以看到nmap识别的指纹是mysql5.7的

我们用hydra爆破一下mysql服务发现日志并没有记录攻击者爆破的账号和密码。
mysql-honeypotd[18]: New connection from MYIP:10109 [MYIP] to 172.17.0.2:3306
mysql-honeypotd[18]: New connection from MYIP:10110 [MYIP] to 172.17.0.2:3306
mysql-honeypotd[18]: Access denied for user '0' from MYIP:10109 to 172.17.0.2:3306 (using password: NO)
mysql-honeypotd[18]: New connection from MYIP:10108 [MYIP] to 172.17.0.2:3306
mysql-honeypotd[18]: Closing connection for MYIP:10109
mysql-honeypotd[18]: New connection from MYIP:10112 [MYIP] to 172.17.0.2:3306
mysql-honeypotd[18]: Connection timed out for MYIP:10110
mysql-honeypotd[18]: Closing connection for MYIP:10110
mysql-honeypotd[18]: Access denied for user '¨+°2' from MYIP:10108 to 172.17.0.2:3306 (using password: NO)
mysql-honeypotd[18]: New connection from MYIP:10113 [MYIP] to 172.17.0.2:3306
mysql-honeypotd[18]: Access denied for user 'root' from MYIP:10112 to 172.17.0.2:3306 (using password: YES)
mysql-honeypotd[18]: Closing connection for MYIP:10108
mysql-honeypotd[18]: New connection from MYIP:10114 [MYIP] to 172.17.0.2:3306
mysql-honeypotd[18]: Closing connection for MYIP:10113
mysql-honeypotd[18]: Closing connection for MYIP:10112
mysql-honeypotd[18]: New connection from MYIP:10115 [MYIP] to 172.17.0.2:3306
mysql-honeypotd[18]: Closing connection for MYIP:10114
mysql-honeypotd[18]: New connection from MYIP:10118 [MYIP] to 172.17.0.2:3306
mysql-honeypotd[18]: Closing connection for MYIP:10115
mysql-honeypotd[18]: New connection from MYIP:10116 [MYIP] to 172.17.0.2:3306
mysql-honeypotd[18]: Access denied for user '0' from MYIP:10118 to 172.17.0.2:3306 (using password: NO)
mysql-honeypotd[18]: New connection from MYIP:10117 [MYIP] to 172.17.0.2:3306
mysql-honeypotd[18]: Access denied for user '0' from MYIP:10116 to 172.17.0.2:3306 (using password: NO)
mysql-honeypotd[18]: Closing connection for MYIP:10118
mysql-honeypotd[18]: New connection from MYIP:10119 [MYIP] to 172.17.0.2:3306
mysql-honeypotd[18]: Access denied for user '0' from MYIP:10117 to 172.17.0.2:3306 (using password: NO)
mysql-honeypotd[18]: Closing connection for MYIP:10116
mysql-honeypotd[18]: New connection from MYIP:10120 [MYIP] to 172.17.0.2:3306
mysql-honeypotd[18]: Access denied for user '0' from MYIP:10119 to 172.17.0.2:3306 (using password: NO)
mysql-honeypotd[18]: Closing connection for MYIP:10117
mysql-honeypotd[18]: New connection from MYIP:10121 [MYIP] to 172.17.0.2:3306
mysql-honeypotd[18]: Access denied for user 'root' from MYIP:10120 to 172.17.0.2:3306 (using password: YES)
mysql-honeypotd[18]: Closing connection for MYIP:10119
mysql-honeypotd[18]: New connection from MYIP:10122 [MYIP] to 172.17.0.2:3306
mysql-honeypotd[18]: Access denied for user 'root' from MYIP:10121 to 172.17.0.2:3306 (using password: YES)
mysql-honeypotd[18]: Closing connection for MYIP:10120
mysql-honeypotd[18]: New connection from MYIP:10123 [MYIP] to 172.17.0.2:3306
mysql-honeypotd[18]: Access denied for user 'root' from MYIP:10122 to 172.17.0.2:3306 (using password: YES)
mysql-honeypotd[18]: Closing connection for MYIP:10121试一下用正确的账号密码登录看看交互性写到这里突然发现这个程序并没有密码的也就是说没有交互信息。。。。

总结
难易性★☆☆☆☆
可用性★★☆☆☆
展示性★☆☆☆☆
交互性★☆☆☆☆
Web 蜜罐
Glastopf
Google翻译一波
Glastopf是由Lukas Rist创建的Python Web应用程序蜜罐。一般的做法漏洞类型仿真而不是漏洞仿真。一旦模拟了漏洞类型Glastopf就可以处理相同类型的未知攻击。虽然实施可能更慢更复杂但我们仍然领先于攻击者直到他们提出新方法或发现我们实施中的新缺陷。模块化设计以添加新的日志记录功能或攻击类型处理程序。各种数据库功能已经到位。集中数据收集支持HPFeeds日志记录。流行的攻击类型仿真已经到位远程文件包含通过内置PHP沙箱本地文件包含提供来自虚拟文件系统的文件和通过POST请求的HTML注入。攻击者通常使用搜索引擎和特制的搜索请求来查找受害者。为了吸引它们Glastopf提供了这些关键词AKA“dork”并另外从请求中提取它们自动扩展其攻击面。结果蜜罐在尝试每次新的攻击时变得越来越有吸引力。我们将公开SQL注入模拟器为爬虫识别和智能傻瓜选择提供IP分析。
使用docker运行
docker run -it -p 80:80 colinhe/glastopf
打开80端口可以看到有个web系统有几个表单sqlmap跑一下跑不到漏洞

查看它的日志只有访问路径并没有具体payload捕捉到。
2019-07-07 09:05:32,830 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:32,847 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:32,874 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:32,892 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:32,912 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:32,930 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:32,948 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:32,974 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:32,992 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,020 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,039 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,056 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,079 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,116 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,143 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,160 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,186 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,206 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,229 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,248 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,269 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,289 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,310 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,331 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,347 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,375 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,393 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,411 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,441 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,459 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,497 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,516 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,533 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,552 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,572 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,592 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,618 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,635 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,656 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,674 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,692 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,718 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,739 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,758 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,778 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,797 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,814 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,832 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,857 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,879 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,901 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,919 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,939 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,956 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:33,983 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:34,009 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:34,028 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:34,055 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80
2019-07-07 09:05:34,081 (glastopf.glastopf) 192.168.0.101 requested POST /index on 1b34ad501b36:80蜜罐里面还有一个sqlite的存放日志信息和爬虫的关键字


因为我是用docker测试没有设置中继所以会报错

总结
难易性★★★★☆
可用性★★★☆☆
展示性★★★☆☆
交互性★★☆☆☆
这款蜜罐按照官方介绍也是挺厉害的设置google的关键字让攻击者可以搜索到不过官方说的注入模拟器是指可以成功注入吗非常奇怪
Snare
官方说这个蜜罐是这样下一代高交互 honEypot我们来看看效果
这个蜜罐是复制别人网站的源码程序原理跟钓鱼网站差不多
我们用dockerfile生成一下修改一下dockerfile的PAGE_URL

我们可以看到它生成的过程是复制网站的源码
Step 12/13 : RUN clone --target "http://$PAGE_URL"
---> Running in 6c0d00d5fa12
ERROR Property: Invalid value for "CSS Level 2.1" property: "\"}\"" [245:3: voice-family]
______ __ ______ _ ____________
/ ____// / / __ // | / / ____/ __ \
/ / / / / / / // |/ / __/ / /_/ /
/ /___ / /____ / /_/ // /| / /___/ _, _/
/_____//______//_____//_/ |_/_____/_/ |_|
Error logs will be stored in /opt/snare/clone.err
name: /index.html
name: /status_404
name: /style.css
name: /index.php
name: /categories.php
name: /artists.php
name: /disclaimer.php
name: /cart.php
name: /guestbook.php
name: /AJAX/index.php
name: /login.php
name: /userinfo.php
name: /privacy.php
name: /Mod_Rewrite_Shop/
name: /hpp/
name: /images/logo.gif
name: /Flash/add.swf
name: /search.php?test=query
name: /listproducts.php?cat=1
name: /listproducts.php?cat=2
name: /listproducts.php?cat=3
name: /listproducts.php?cat=4
name: /artists.php?artist=1
name: /artists.php?artist=2
name: /artists.php?artist=3
name: /images/remark.gif
name: /styles.css
name: /signup.php
name: /Details/network-attached-storage-dlink/1/
name: /Details/web-camera-a4tech/2/
name: /Details/color-printer/3/
name: /images/1.jpg
name: /images/2.jpg
name: /images/3.jpg
name: /?pp=12
name: /product.php?pic=1
name: /showimage.php?file=./pictures/1.jpg
name: /product.php?pic=2
name: /showimage.php?file=./pictures/2.jpg
name: /product.php?pic=3
name: /showimage.php?file=./pictures/3.jpg
name: /product.php?pic=4
name: /showimage.php?file=./pictures/4.jpg
name: /product.php?pic=5
name: /showimage.php?file=./pictures/5.jpg
name: /product.php?pic=7
name: /showimage.php?file=./pictures/7.jpg
name: /showimage.php?file=./pictures/1.jpg&size=160
name: /showimage.php?file=./pictures/2.jpg&size=160
name: /showimage.php?file=./pictures/3.jpg&size=160
name: /showimage.php?file=./pictures/4.jpg&size=160
name: /showimage.php?file=./pictures/5.jpg&size=160
name: /showimage.php?file=./pictures/7.jpg&size=160
name: /product.php?pic=6
name: /showimage.php?file=./pictures/6.jpg
name: /showimage.php?file=./pictures/6.jpg&size=160
name: /listproducts.php?artist=1
name: /listproducts.php?artist=3
name: /secured/newuser.php有些css没有复制过来
/opt/snare # cat clone.err
2019-07-08 03:08:49 ERROR:CSSUTILS:__handle: Property: Invalid value for "CSS Level 2.1" property: "\"}\"" [245:3: voice-family]
2019-07-08 03:09:10 ERROR:snare.cloner:get_body:
2019-07-08 03:09:24 ERROR:snare.cloner:get_body:
2019-07-08 03:09:54 ERROR:snare.cloner:get_body:
2019-07-08 03:10:15 ERROR:snare.cloner:get_body:导致看到下面这样

用sqlmap跑一下看看能不能捕捉到。
在内网跑也会出现连接超时神奇的蜜罐

不过还是可以捕捉到SQLMAP的攻击载荷的
2019-07-08 03:25:55 INFO:snare.server:handle_request: Request path: /userinfo.php
2019-07-08 03:25:55 INFO:snare.server:handle_request: POST data:
2019-07-08 03:25:55 INFO:snare.server:handle_request: - uname: 1 AND 5791=DBMS_PIPE.RECEIVE_MESSAGE(CHR(70)||CHR(106)||CHR(71)||CHR(84),5)-- uoGM
2019-07-08 03:25:55 INFO:snare.server:handle_request: - pass: 1
2019-07-08 03:25:55 INFO:aiohttp.access:log: 192.168.0.101 [08/Jul/2019:03:25:55 +0000] "POST /userinfo.php HTTP/1.1" 200 5073 "http://192.168.0.103/login.php" "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:67.0) Gecko/20100101 Firefox/67.0"
2019-07-08 03:25:55 INFO:snare.server:handle_request: Request path: /userinfo.php
2019-07-08 03:25:55 INFO:snare.server:handle_request: POST data:
2019-07-08 03:25:55 INFO:snare.server:handle_request: - uname: 1') AND 5791=DBMS_PIPE.RECEIVE_MESSAGE(CHR(70)||CHR(106)||CHR(71)||CHR(84),5) AND ('yVLf'='yVLf
2019-07-08 03:25:55 INFO:snare.server:handle_request: - pass: 1
2019-07-08 03:25:56 INFO:aiohttp.access:log: 192.168.0.101 [08/Jul/2019:03:25:55 +0000] "POST /userinfo.php HTTP/1.1" 200 5073 "http://192.168.0.103/login.php" "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:67.0) Gecko/20100101 Firefox/67.0"
2019-07-08 03:25:56 INFO:snare.server:handle_request: Request path: /userinfo.php
2019-07-08 03:25:56 INFO:snare.server:handle_request: POST data:
2019-07-08 03:25:56 INFO:snare.server:handle_request: - uname: 1' AND 5791=DBMS_PIPE.RECEIVE_MESSAGE(CHR(70)||CHR(106)||CHR(71)||CHR(84),5) AND 'joJv'='joJv
2019-07-08 03:25:56 INFO:snare.server:handle_request: - pass: 1
2019-07-08 03:25:57 INFO:aiohttp.access:log: 192.168.0.101 [08/Jul/2019:03:25:56 +0000] "POST /userinfo.php HTTP/1.1" 200 5073 "http://192.168.0.103/login.php" "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:67.0) Gecko/20100101 Firefox/67.0"
2019-07-08 03:25:57 INFO:snare.server:handle_request: Request path: /userinfo.php
2019-07-08 03:25:57 INFO:snare.server:handle_request: POST data:
2019-07-08 03:25:57 INFO:snare.server:handle_request: - uname: 1%' AND 5791=DBMS_PIPE.RECEIVE_MESSAGE(CHR(70)||CHR(106)||CHR(71)||CHR(84),5) AND '%'='
2019-07-08 03:25:57 INFO:snare.server:handle_request: - pass: 1
2019-07-08 03:26:03 INFO:aiohttp.access:log: 192.168.0.101 [08/Jul/2019:03:25:57 +0000] "POST /userinfo.php HTTP/1.1" 200 5073 "http://192.168.0.103/login.php" "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:67.0) Gecko/20100101 Firefox/67.0"
2019-07-08 03:26:03 INFO:snare.server:handle_request: Request path: /userinfo.php
2019-07-08 03:26:03 INFO:snare.server:handle_request: POST data:
2019-07-08 03:26:03 INFO:snare.server:handle_request: - uname: 1) ORDER BY 1-- Xxww
2019-07-08 03:26:03 INFO:snare.server:handle_request: - pass: 1
2019-07-08 03:26:04 INFO:aiohttp.access:log: 192.168.0.101 [08/Jul/2019:03:26:03 +0000] "POST /userinfo.php HTTP/1.1" 200 5073 "http://192.168.0.103/login.php" "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:67.0) Gecko/20100101 Firefox/67.0"
2019-07-08 03:26:04 INFO:snare.server:handle_request: Request path: /userinfo.php
2019-07-08 03:26:04 INFO:snare.server:handle_request: POST data:
2019-07-08 03:26:04 INFO:snare.server:handle_request: - uname: 1) UNION ALL SELECT NULL-- HsfF
2019-07-08 03:26:04 INFO:snare.server:handle_request: - pass: 1
2019-07-08 03:26:13 INFO:aiohttp.access:log: 192.168.0.101 [08/Jul/2019:03:26:04 +0000] "POST /userinfo.php HTTP/1.1" 200 5073 "http://192.168.0.103/login.php" "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:67.0) Gecko/20100101 Firefox/67.0"
2019-07-08 03:26:13 INFO:snare.server:handle_request: Request path: /userinfo.php
2019-07-08 03:26:13 INFO:snare.server:handle_request: POST data:
2019-07-08 03:26:13 INFO:snare.server:handle_request: - uname: 1) UNION ALL SELECT NULL,NULL-- paMe
2019-07-08 03:26:13 INFO:snare.server:handle_request: - pass: 1
2019-07-08 03:26:17 INFO:aiohttp.access:log: 192.168.0.101 [08/Jul/2019:03:26:13 +0000] "POST /userinfo.php HTTP/1.1" 200 5073 "http://192.168.0.103/login.php" "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:67.0) Gecko/20100101 Firefox/67.0"
2019-07-08 03:26:17 INFO:snare.server:handle_request: Request path: /userinfo.php
2019-07-08 03:26:17 INFO:snare.server:handle_request: POST data:
2019-07-08 03:26:17 INFO:snare.server:handle_request: - uname: 1) UNION ALL SELECT NULL,NULL,NULL-- NvGq
2019-07-08 03:26:17 INFO:snare.server:handle_request: - pass: 1
2019-07-08 03:26:20 INFO:aiohttp.access:log: 192.168.0.101 [08/Jul/2019:03:26:17 +0000] "POST /userinfo.php HTTP/1.1" 200 5073 "http://192.168.0.103/login.php" "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:67.0) Gecko/20100101 Firefox/67.0"
2019-07-08 03:26:20 INFO:snare.server:handle_request: Request path: /userinfo.php
2019-07-08 03:26:20 INFO:snare.server:handle_request: POST data:
2019-07-08 03:26:20 INFO:snare.server:handle_request: - uname: 1) UNION ALL SELECT NULL,NULL,NULL,NULL-- FgjB
2019-07-08 03:26:20 INFO:snare.server:handle_request: - pass: 1测试到最后直接504

这个蜜罐有个选项可以设置tanner。TANNER是一种远程数据分析和分类服务用于评估HTTP请求并组成SNARE事件服务的响应。
试试装上这个会不会504呢
在虚拟机运行下面的命令重新安装
snare

tanner

安装并运行

使用avws进去扫描测试启动tannerweb

打开地址可以看到snare蜜罐捕捉到的信息
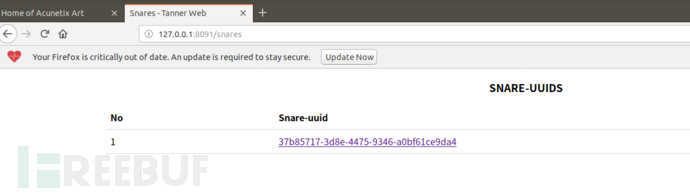
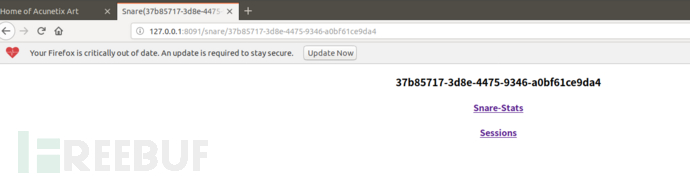
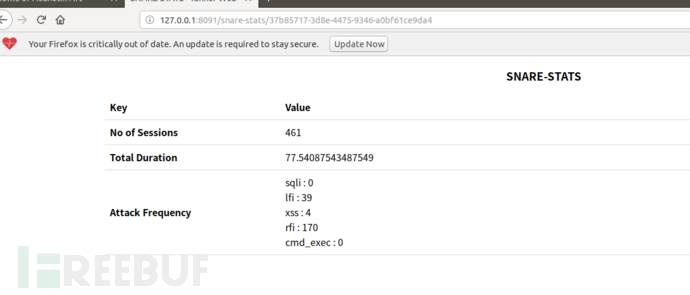
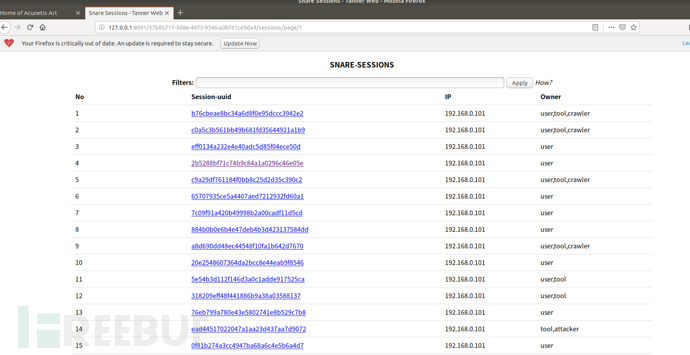

总结
难易性★★☆☆☆
可用性★★★★★
展示性★★★★★
交互性★★★★☆
官方说这个蜜罐是下一代高交互 honEypot不过我测试发现克隆一些网站的时候还是不能克隆程序会报错不过tanner用来处理信息就非常不错的清晰明了。
phpmyadmin_honeypot
一个简单有效的 phpMyAdmin 蜜罐只需要安装php+apache2不需要安装mysql使用安装脚本就可以打开

测试发现会在前端获取IP这样就有个问题了假如我修改了IP呢

我修改IP为114.114.114.114

使用正确的账号密码登录发现页面是这样。

总结
难易性★☆☆☆☆
可用性★★★★★
展示性★☆☆☆☆
交互性★★☆☆☆
这款蜜罐虽然交互性低不过也算不错就是IP那里让我感到无语=-=
Nodepot
这一款蜜罐不用于生产环境也就是半成品而且当我用docker build的时候无法构造成功这个蜜罐就跳过了


basic-auth-pot

直接运行bap.py在浏览器打开8080端口

使用BP拦截到数据包可以看到账号和密码加密是base64

程序运行之后当攻击者访问的时候会生成两个日志一个时访问网站(access)的日志一个是登录(bap)的日志

总结
难易性★☆☆☆☆
可用性★★★★★
展示性★★☆☆☆
交互性★★☆☆☆
这个蜜罐效果很不错可以捕捉到账号和密码也有访问的日志。
Shadow Daemon

安装shadowd

安装完成之后在浏览器打开127.0.0.18080里面设置可以设置为中文页面超酷炫的

现在在后台管理里面什么都没有你需要添加规则让连接器进行连接

选择被动模式也就是蜜罐模式然后输入一串key用来连接器连接的密码

官方文档是连接器就是一个模块在request之前检测或者捕捉数据。下面是连接器的配置方法我一开始看见文档第一个就是PHP用了一些不知道为什么不行干脆用django调用它的连接器。
注意不要用python3.6和3.7试了一下会报错的我最后用了2.7
目录结构

代码
#views.py
from django.shortcuts import render, HttpResponse
import MySQLdb
# Create your views here.
def sqli(request):
data = []
id = request.GET.get('id')
db = MySQLdb.connect(user='root', db='vul', passwd='123456', host='192.168.0.103')
cursor = db.cursor()
cursor.execute('SELECT * FROM apps_article ORDER BY ' + id)
names = cursor.fetchall()
for i in names:
title = i[1]
content = i[2]
db.close()
return HttpResponse(id)
#models.py
from django.db import models
# Create your models here.
class Article(models.Model):
title = models.CharField(max_length=50)
content = models.TextField()
#urls.py
from app.views import *
urlpatterns = [
url(r'^admin/', admin.site.urls),
url(r'sql/',sqli)
]
#shadowdconnector.py
#创建middleware文件夹里面必须有__init__.py
from shadowd.django_connector import InputDjango, OutputDjango, Connector
from django.utils import deprecation
class ShadowdConnectorMiddleware(deprecation.MiddlewareMixin):
def process_request(self, request):
input = InputDjango(request)
output = OutputDjango()
status = Connector().start(input, output)
if not status == True:
return status
#settings.py
添加中间件
MIDDLEWARE = [
'app.middleware.shadowdconnector.ShadowdConnectorMiddleware',
]连接器的配置需要在/etc/文件夹下新建shadowd文件夹将python配置文件复制到里面。配置文件profile和key参数是必须填的。
git clone https://github.com/zecure/shadowd_python.git
将里面的connectors.ini复制到/etc/shadowd/下
root@l-virtual-machine:/opt/shadowd_python/misc/examples# ls
connectors.ini
root@l-virtual-machine:/etc/shadowd# ls
connectors.ini
root@l-virtual-machine:/etc/shadowd# cat connectors.ini
[shadowd_python]
; Sets the profile id. Required.
profile=1
; Sets the key for the profile. Required.
key=123456
; Sets the address of the shadowd server.
; Default Value: 127.0.0.1
;host=
; Sets the port of the shadowd server.
; Default Value: 9115
;port=
; Sets the path to the SSL certificate and enables SSL.
;ssl=
; If activated threats are not removed. This can be used to test new rules without
; making the web application unusable. It can be also used to turn Shadow Daemon
; into a high-interaction web honeypot.
; Possible Values:
; 0
; 1
; Default Value: 0
;observe=
; If activated error messages are printed.
; Possible Values:
; 0
; 1
; Default Value: 0
debug=1
; Sets the log file, but it is only used if debug is enabled.
; Default Value: /var/log/shadowd.log
;log=
; If set the ignore list is used to ignore certain parameters and not send them to
; the shadowd server. It is good practise to not send passwords or other very
; sensitive information to the server.
;ignore=
; Sets the source for the client ip. It is a key of $_SERVER. If you are using a
; reverse proxy or something similar forward the real client ip and reference it
; here, e.g., HTTP_X_FORWARDED_FOR.
; Default Value:
; CGI: REMOTE_ADDR
; Django: REMOTE_ADDR
; Flask: REMOTE_ADDR
;client_ip=
; Sets the source for the caller. It is a key of $_SERVER. If you are using web
; application with a front controller or something like that change it to PHP_SELF.
; Default Value:
; CGI: SCRIPT_FILENAME
; Django: PATH_INFO
; Flask: PATH_INFO
;caller=
root@l-virtual-machine:/etc/shadowd#搞定完连接器和连接器的配置我们sqlmap跑一下


因为我是使用蜜罐模式所以sqlmap还是能跑到注入

总结
难易性★★★★☆
可用性★★★★★
展示性★★★★★
交互性★★★★★
这款蜜罐非常好用就是需要二次开发把连接器弄进程序里面有点麻烦。
Servletpot
这款蜜罐太旧了就不测试了

django-admin-honeypot
我按照文档将库插入到app里面修改路由结果显示如下

登录到真实的后台上面可以看到爆破的日志

总结
难易性★☆☆☆☆
可用性★★★★★
展示性★★★★★
交互性★★★★☆
这款蜜罐适合内网监测心怀鬼胎的内鬼(๑•̀ㅂ•́)و✧
honeyhttpd
HoneyHTTPD是一个基于Python的Web服务器蜜罐框架。它可以轻松设置虚假Web服务器并记录给它的请求。
我按照文档去安装和启动最后访问的时候会报错。所以这个蜜罐就跳过吧
HTTP


HTTPS

服务蜜罐
honeyntp
这个蜜罐的运行环境是python2.7。启动之后它会监听123UDP端口使用nmap扫描可以看到ntp蜜罐已经成功的
 不过交互性还是有点低它会给出错误提示
不过交互性还是有点低它会给出错误提示
 日志记录有问题记录不到日志
日志记录有问题记录不到日志

总结
难易性★☆☆☆☆
可用性★★☆☆☆
展示性★☆☆☆☆
交互性★★☆☆☆
honeypot-camera
官方说观察相机蜜罐概念验证然后我真的不懂这玩意的有什么用=-=。当你刷新一次之后它会自动刷新时间并且在后台生成camera.JPG。


HoneyPy
低交互蜜罐具有更多中等交互蜜罐的能力
构造环境
FROM ubuntu:18.04
RUN apt update -y
RUN apt install -y vim net-tools git python-dev python python-pip
RUN cd /opt && git clone https://github.com/foospidy/HoneyPy.git && cd HoneyPy && pip install -r requirements.txt官方文档里面有运行操作启动完成之后蜜罐会启动下面的端口
root@9fc129372dea:/opt/HoneyPy# python Honey.py
Your service configuration suggests that you want to run on at least one low port!
To enable port redirection run the following ipt-kit (https://github.com/foospidy/ipt-kit) commands as root:
___
/\ /\___ _ __ ___ _ _ / _ \_ _
/ /_/ / _ \| '_ \ / _ \ | | |/ /_)/ | | |
/ __ / (_) | | | | __/ |_| / ___/| |_| |
\/ /_/ \___/|_| |_|\___|\__, \/ \__, |
|___/ |___/
[HoneyPy Copyright (c) 2013-2017. foospidy]
HoneyPy Console. For help type 'help'.
HoneyPy> start
8 service(s) started!
HoneyPy> 
root@0c7d27bfdec5:/opt/HoneyPy# nmap -sV -p10007-10010 127.0.0.1
Starting Nmap 7.60 ( https://nmap.org ) at 2019-07-10 03:16 UTC
Nmap scan report for localhost (127.0.0.1)
Host is up (0.000063s latency).
PORT STATE SERVICE VERSION
10007/tcp open echo
10008/tcp open octopus?
10009/tcp open swdtp-sv?
10010/tcp open rxapi?
3 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port10008-TCP:V=7.60%I=7%D=7/10%Time=5D255897%P=x86_64-pc-linux-gnu%r(N
SF:ULL,34,"Prototype\x20unit\x200001\x20is\x20ready\x20to\x20accept\x20pro
SF:gramming\r\n")%r(GenericLines,34,"Prototype\x20unit\x200001\x20is\x20re
SF:ady\x20to\x20accept\x20programming\r\n")%r(GetRequest,34,"Prototype\x20
SF:unit\x200001\x20is\x20ready\x20to\x20accept\x20programming\r\n")%r(HTTP
SF:Options,34,"Prototype\x20unit\x200001\x20is\x20ready\x20to\x20accept\x2
SF:0programming\r\n")%r(RTSPRequest,34,"Prototype\x20unit\x200001\x20is\x2
SF:0ready\x20to\x20accept\x20programming\r\n")%r(RPCCheck,34,"Prototype\x2
SF:0unit\x200001\x20is\x20ready\x20to\x20accept\x20programming\r\n")%r(DNS
SF:VersionBindReq,34,"Prototype\x20unit\x200001\x20is\x20ready\x20to\x20ac
SF:cept\x20programming\r\n")%r(DNSStatusRequest,34,"Prototype\x20unit\x200
SF:001\x20is\x20ready\x20to\x20accept\x20programming\r\n")%r(Help,34,"Prot
SF:otype\x20unit\x200001\x20is\x20ready\x20to\x20accept\x20programming\r\n
SF:")%r(SSLSessionReq,34,"Prototype\x20unit\x200001\x20is\x20ready\x20to\x
SF:20accept\x20programming\r\n")%r(TLSSessionReq,34,"Prototype\x20unit\x20
SF:0001\x20is\x20ready\x20to\x20accept\x20programming\r\n")%r(Kerberos,34,
SF:"Prototype\x20unit\x200001\x20is\x20ready\x20to\x20accept\x20programmin
SF:g\r\n")%r(SMBProgNeg,34,"Prototype\x20unit\x200001\x20is\x20ready\x20to
SF:\x20accept\x20programming\r\n")%r(X11Probe,34,"Prototype\x20unit\x20000
SF:1\x20is\x20ready\x20to\x20accept\x20programming\r\n")%r(FourOhFourReque
SF:st,34,"Prototype\x20unit\x200001\x20is\x20ready\x20to\x20accept\x20prog
SF:ramming\r\n")%r(LPDString,34,"Prototype\x20unit\x200001\x20is\x20ready\
SF:x20to\x20accept\x20programming\r\n")%r(LDAPSearchReq,34,"Prototype\x20u
SF:nit\x200001\x20is\x20ready\x20to\x20accept\x20programming\r\n")%r(LDAPB
SF:indReq,34,"Prototype\x20unit\x200001\x20is\x20ready\x20to\x20accept\x20
SF:programming\r\n")%r(SIPOptions,34,"Prototype\x20unit\x200001\x20is\x20r
SF:eady\x20to\x20accept\x20programming\r\n")%r(LANDesk-RC,34,"Prototype\x2
SF:0unit\x200001\x20is\x20ready\x20to\x20accept\x20programming\r\n")%r(Ter
SF:minalServer,34,"Prototype\x20unit\x200001\x20is\x20ready\x20to\x20accep
SF:t\x20programming\r\n")%r(NCP,34,"Prototype\x20unit\x200001\x20is\x20rea
SF:dy\x20to\x20accept\x20programming\r\n");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port10009-TCP:V=7.60%I=7%D=7/10%Time=5D25589D%P=x86_64-pc-linux-gnu%r(N
SF:ULL,1B,"Debian\x20GNU/Linux\x207\r\nLogin:\x20")%r(GenericLines,47,"Deb
SF:ian\x20GNU/Linux\x207\r\nLogin:\x20\xff\xfb\x01password:\x20\xff\xfc\x0
SF:1\r\n\r\ninvalid\x20login\r\npassword:")%r(GetRequest,47,"Debian\x20GNU
SF:/Linux\x207\r\nLogin:\x20\xff\xfb\x01password:\x20\xff\xfc\x01\r\n\r\ni
SF:nvalid\x20login\r\npassword:")%r(HTTPOptions,47,"Debian\x20GNU/Linux\x2
SF:07\r\nLogin:\x20\xff\xfb\x01password:\x20\xff\xfc\x01\r\n\r\ninvalid\x2
SF:0login\r\npassword:")%r(RTSPRequest,47,"Debian\x20GNU/Linux\x207\r\nLog
SF:in:\x20\xff\xfb\x01password:\x20\xff\xfc\x01\r\n\r\ninvalid\x20login\r\
SF:npassword:")%r(RPCCheck,1B,"Debian\x20GNU/Linux\x207\r\nLogin:\x20")%r(
SF:DNSVersionBindReq,1B,"Debian\x20GNU/Linux\x207\r\nLogin:\x20")%r(DNSSta
SF:tusRequest,1B,"Debian\x20GNU/Linux\x207\r\nLogin:\x20")%r(Help,28,"Debi
SF:an\x20GNU/Linux\x207\r\nLogin:\x20\xff\xfb\x01password:\x20")%r(SSLSess
SF:ionReq,1B,"Debian\x20GNU/Linux\x207\r\nLogin:\x20")%r(TLSSessionReq,28,
SF:"Debian\x20GNU/Linux\x207\r\nLogin:\x20\xff\xfb\x01password:\x20")%r(Ke
SF:rberos,1B,"Debian\x20GNU/Linux\x207\r\nLogin:\x20")%r(SMBProgNeg,1B,"De
SF:bian\x20GNU/Linux\x207\r\nLogin:\x20")%r(X11Probe,1B,"Debian\x20GNU/Lin
SF:ux\x207\r\nLogin:\x20")%r(FourOhFourRequest,47,"Debian\x20GNU/Linux\x20
SF:7\r\nLogin:\x20\xff\xfb\x01password:\x20\xff\xfc\x01\r\n\r\ninvalid\x20
SF:login\r\npassword:")%r(LPDString,1B,"Debian\x20GNU/Linux\x207\r\nLogin:
SF:\x20")%r(LDAPSearchReq,1B,"Debian\x20GNU/Linux\x207\r\nLogin:\x20")%r(L
SF:DAPBindReq,1B,"Debian\x20GNU/Linux\x207\r\nLogin:\x20")%r(SIPOptions,15
SF:E,"Debian\x20GNU/Linux\x207\r\nLogin:\x20\xff\xfb\x01password:\x20\xff\
SF:xfc\x01\r\n\r\ninvalid\x20login\r\npassword:\xff\xfc\x01\r\n\r\ninvalid
SF:\x20login\r\npassword:\xff\xfc\x01\r\n\r\ninvalid\x20login\r\npassword:
SF:\xff\xfc\x01\r\n\r\ninvalid\x20login\r\npassword:\xff\xfc\x01\r\n\r\nin
SF:valid\x20login\r\npassword:\xff\xfc\x01\r\n\r\ninvalid\x20login\r\npass
SF:word:\xff\xfc\x01\r\n\r\ninvalid\x20login\r\npassword:\xff\xfc\x01\r\n\
SF:r\ninvalid\x20login\r\npassword:\xff\xfc\x01\r\n\r\ninvalid\x20login\r\
SF:npassword:\xff\xfc\x01\r\n\r\ninvalid\x20login\r\npassword:");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port10010-TCP:V=7.60%I=7%D=7/10%Time=5D25589D%P=x86_64-pc-linux-gnu%r(N
SF:ULL,2C,"Welcome\x20to\x20Microsoft\x20Telnet\x20Service\n\nlogin:\x20")
SF:%r(GenericLines,36,"Welcome\x20to\x20Microsoft\x20Telnet\x20Service\n\n
SF:login:\x20password:\x20")%r(GetRequest,36,"Welcome\x20to\x20Microsoft\x
SF:20Telnet\x20Service\n\nlogin:\x20password:\x20")%r(HTTPOptions,36,"Welc
SF:ome\x20to\x20Microsoft\x20Telnet\x20Service\n\nlogin:\x20password:\x20"
SF:)%r(RTSPRequest,36,"Welcome\x20to\x20Microsoft\x20Telnet\x20Service\n\n
SF:login:\x20password:\x20")%r(RPCCheck,36,"Welcome\x20to\x20Microsoft\x20
SF:Telnet\x20Service\n\nlogin:\x20password:\x20")%r(DNSVersionBindReq,36,"
SF:Welcome\x20to\x20Microsoft\x20Telnet\x20Service\n\nlogin:\x20password:\
SF:x20")%r(DNSStatusRequest,36,"Welcome\x20to\x20Microsoft\x20Telnet\x20Se
SF:rvice\n\nlogin:\x20password:\x20")%r(Help,36,"Welcome\x20to\x20Microsof
SF:t\x20Telnet\x20Service\n\nlogin:\x20password:\x20")%r(SSLSessionReq,36,
SF:"Welcome\x20to\x20Microsoft\x20Telnet\x20Service\n\nlogin:\x20password:
SF:\x20")%r(TLSSessionReq,36,"Welcome\x20to\x20Microsoft\x20Telnet\x20Serv
SF:ice\n\nlogin:\x20password:\x20")%r(Kerberos,36,"Welcome\x20to\x20Micros
SF:oft\x20Telnet\x20Service\n\nlogin:\x20password:\x20")%r(SMBProgNeg,36,"
SF:Welcome\x20to\x20Microsoft\x20Telnet\x20Service\n\nlogin:\x20password:\
SF:x20")%r(X11Probe,36,"Welcome\x20to\x20Microsoft\x20Telnet\x20Service\n\
SF:nlogin:\x20password:\x20")%r(FourOhFourRequest,36,"Welcome\x20to\x20Mic
SF:rosoft\x20Telnet\x20Service\n\nlogin:\x20password:\x20")%r(LPDString,36
SF:,"Welcome\x20to\x20Microsoft\x20Telnet\x20Service\n\nlogin:\x20password
SF::\x20")%r(LDAPSearchReq,36,"Welcome\x20to\x20Microsoft\x20Telnet\x20Ser
SF:vice\n\nlogin:\x20password:\x20")%r(LDAPBindReq,36,"Welcome\x20to\x20Mi
SF:crosoft\x20Telnet\x20Service\n\nlogin:\x20password:\x20")%r(SIPOptions,
SF:36,"Welcome\x20to\x20Microsoft\x20Telnet\x20Service\n\nlogin:\x20passwo
SF:rd:\x20")%r(LANDesk-RC,36,"Welcome\x20to\x20Microsoft\x20Telnet\x20Serv
SF:ice\n\nlogin:\x20password:\x20")%r(TerminalServer,36,"Welcome\x20to\x20
SF:Microsoft\x20Telnet\x20Service\n\nlogin:\x20password:\x20")%r(NCP,36,"W
SF:elcome\x20to\x20Microsoft\x20Telnet\x20Service\n\nlogin:\x20password:\x
SF:20");
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 147.98 secondstelnet10007端口
2019-07-10 03:23:33,559301,+0000 [plugins.Echo.Echo.pluginFactory] 18d6b97a-a2c2-11e9-a744-0242ac110002 TCP CONNECT 127.0.0.1 10007 Echo 127.0.0.1 42958
2019-07-10 03:23:39,566261,+0000 [Echo,16,127.0.0.1] 18d6b97a-a2c2-11e9-a744-0242ac110002 TCP RX 127.0.0.1 10007 Echo 127.0.0.1 42958 0d0a0d0a
2019-07-10 03:23:39,566549,+0000 [Echo,16,127.0.0.1] 18d6b97a-a2c2-11e9-a744-0242ac110002 TCP TX 127.0.0.1 10007 Echo 127.0.0.1 42958 0d0a0d0a
2019-07-10 03:23:44,572409,+0000 [plugins.Echo.Echo.pluginFactory] 1f6733c8-a2c2-11e9-a744-0242ac110002 TCP CONNECT 127.0.0.1 10007 Echo 127.0.0.1 42960
2019-07-10 03:23:44,573143,+0000 [Echo,17,127.0.0.1] 1f6733c8-a2c2-11e9-a744-0242ac110002 TCP RX 127.0.0.1 10007 Echo 127.0.0.1 42960 474554202f20485454502f312e300d0a0d0a
2019-07-10 03:23:44,573309,+0000 [Echo,17,127.0.0.1] 1f6733c8-a2c2-11e9-a744-0242ac110002 TCP TX 127.0.0.1 10007 Echo 127.0.0.1 42960 474554202f20485454502f312e300d0a0d0a
2019-07-10 03:23:49,578632,+0000 [plugins.Echo.Echo.pluginFactory] 226315f6-a2c2-11e9-a744-0242ac110002 TCP CONNECT 127.0.0.1 10007 Echo 127.0.0.1 42962
2019-07-10 03:23:49,579462,+0000 [Echo,18,127.0.0.1] 226315f6-a2c2-11e9-a744-0242ac110002 TCP RX 127.0.0.1 10007 Echo 127.0.0.1 42962 4f5054494f4e53202f20485454502f312e300d0a0d0a
2019-07-10 03:23:49,579578,+0000 [Echo,18,127.0.0.1] 226315f6-a2c2-11e9-a744-0242ac110002 TCP TX 127.0.0.1 10007 Echo 127.0.0.1 42962 4f5054494f4e53202f20485454502f312e300d0a0d0a
2019-07-10 03:23:54,584078,+0000 [plugins.Echo.Echo.pluginFactory] 255edbf0-a2c2-11e9-a744-0242ac110002 TCP CONNECT 127.0.0.1 10007 Echo 127.0.0.1 42964
2019-07-10 03:23:54,584756,+0000 [Echo,19,127.0.0.1] 255edbf0-a2c2-11e9-a744-0242ac110002 TCP RX 127.0.0.1 10007 Echo 127.0.0.1 42964 4f5054494f4e53202f20525453502f312e300d0a0d0a
2019-07-10 03:23:54,584890,+0000 [Echo,19,127.0.0.1] 255edbf0-a2c2-11e9-a744-0242ac110002 TCP TX 127.0.0.1 10007 Echo 127.0.0.1 42964 4f5054494f4e53202f20525453502f312e300d0a0d0a
2019-07-10 03:23:59,590095,+0000 [plugins.Echo.Echo.pluginFactory] 285ab75c-a2c2-11e9-a744-0242ac110002 TCP CONNECT 127.0.0.1 10007 Echo 127.0.0.1 42966
2019-07-10 03:23:59,590867,+0000 [Echo,20,127.0.0.1] 285ab75c-a2c2-11e9-a744-0242ac110002 TCP RX 127.0.0.1 10007 Echo 127.0.0.1 42966 8000002872fe1d130000000000000002000186a00001977c0000000000000000000000000000000000000000
2019-07-10 03:23:59,591000,+0000 [Echo,20,127.0.0.1] 285ab75c-a2c2-11e9-a744-0242ac110002 TCP TX 127.0.0.1 10007 Echo 127.0.0.1 42966 8000002872fe1d130000000000000002000186a00001977c0000000000000000000000000000000000000000
2019-07-10 03:24:04,595562,+0000 [plugins.Echo.Echo.pluginFactory] 2b567d7e-a2c2-11e9-a744-0242ac110002 TCP CONNECT 127.0.0.1 10007 Echo 127.0.0.1 42968
2019-07-10 03:24:04,596226,+0000 [Echo,21,127.0.0.1] 2b567d7e-a2c2-11e9-a744-0242ac110002 TCP RX 127.0.0.1 10007 Echo 127.0.0.1 42968 001e0006010000010000000000000776657273696f6e0462696e640000100003
2019-07-10 03:24:04,596393,+0000 [Echo,21,127.0.0.1] 2b567d7e-a2c2-11e9-a744-0242ac110002 TCP TX 127.0.0.1 10007 Echo 127.0.0.1 42968 001e0006010000010000000000000776657273696f6e0462696e640000100003
2019-07-10 03:24:09,601097,+0000 [plugins.Echo.Echo.pluginFactory] 2e524652-a2c2-11e9-a744-0242ac110002 TCP CONNECT 127.0.0.1 10007 Echo 127.0.0.1 42970
2019-07-10 03:24:09,601812,+0000 [Echo,22,127.0.0.1] 2e524652-a2c2-11e9-a744-0242ac110002 TCP RX 127.0.0.1 10007 Echo 127.0.0.1 42970 000c000010000000000000000000
2019-07-10 03:24:09,601911,+0000 [Echo,22,127.0.0.1] 2e524652-a2c2-11e9-a744-0242ac110002 TCP TX 127.0.0.1 10007 Echo 127.0.0.1 42970 000c000010000000000000000000
2019-07-10 03:24:14,607146,+0000 [plugins.Echo.Echo.pluginFactory] 314e238a-a2c2-11e9-a744-0242ac110002 TCP CONNECT 127.0.0.1 10007 Echo 127.0.0.1 42972
2019-07-10 03:24:14,607735,+0000 [Echo,23,127.0.0.1] 314e238a-a2c2-11e9-a744-0242ac110002 TCP RX 127.0.0.1 10007 Echo 127.0.0.1 42972 48454c500d0a
2019-07-10 03:24:14,607862,+0000 [Echo,23,127.0.0.1] 314e238a-a2c2-11e9-a744-0242ac110002 TCP TX 127.0.0.1 10007 Echo 127.0.0.1 42972 48454c500d0a蜜罐服务插件可以自我定制服务
root@0c7d27bfdec5:/opt/HoneyPy/etc# cat services.cfg
# HoneyPy Copyright (C) 2013-2017 foospidy
# services.default.profile
# Important: service names must not contain spaces.
# Important: use port redirecting for services that listen on ports below 1024 (see https://github.com/foospidy/ipt-kit).
[Echo]
plugin = Echo
low_port = tcp:7
port = tcp:10007
description = Echo back data received via tcp.
enabled = Yes
[Echo.udp]
plugin = Echo_udp
low_port = udp:7
port = udp:10007
description = Echo back data received via udp.
enabled = Yes
[MOTD]
plugin = MOTD
low_port = tcp:8
port = tcp:10008
description = Send a message via tcp and close connection.
enabled = Yes
[MOTD.udp]
plugin = MOTD_udp
low_port = udp:8
port = udp:10008
description = Send a message via udp.
enabled = Yes
[Telnet]
plugin = TelnetUnix
low_port = tcp:23
port = tcp:10009
description = Emulate Debian telnet login via tcp.
enabled = Yes
[Telnet.Windows]
plugin = TelnetWindows
low_port = tcp:24
port = tcp:10010
description = Emulate Windows telnet login via tcp.
enabled = Yes
[Random]
plugin = Random
low_port = tcp:2048
port = tcp:2048
description = Send random data via tcp.
enabled = Yes
[HashCountRandom]
plugin = HashCountRandom
low_port = tcp:4096
port = tcp:4096
description = Send random data prefixed with a hash of a counter via tcp.
enabled = Yes
[Elasticsearch]
plugin = Elasticsearch
low_port = tcp:9200
port = tcp:9200
description = Send basic elasticsearch like replies
enabled = No日志放在log文件夹下面这是nmap扫描的日志
root@9fc129372dea:/opt/HoneyPy# cat log/honeypy.log
2019-07-14 04:59:30,066628,+0000 [-] Log opened.
2019-07-14 04:59:30,069222,+0000 [-] HoneyPy (0.7.0) Started
2019-07-14 04:59:30,099161,+0000 [-] pluginFactory starting on 10007
2019-07-14 04:59:30,099425,+0000 [-] Starting factory <plugins.Echo.Echo.pluginFactory instance at 0x7f87ee126fc8>
2019-07-14 04:59:30,102159,+0000 [-] pluginMain starting on 10007
2019-07-14 04:59:30,102297,+0000 [-] Starting protocol <plugins.Echo_udp.Echo.pluginMain instance at 0x7f87ed82d680>
2019-07-14 04:59:30,103776,+0000 [-] pluginFactory starting on 10008
2019-07-14 04:59:30,103883,+0000 [-] Starting factory <plugins.MOTD.MOTD.pluginFactory instance at 0x7f87ed8385f0>
2019-07-14 04:59:30,105335,+0000 [-] pluginMain starting on 10008
2019-07-14 04:59:30,105435,+0000 [-] Starting protocol <plugins.MOTD_udp.MOTD.pluginMain instance at 0x7f87ed838a70>
2019-07-14 04:59:30,117802,+0000 [-] pluginFactory starting on 10009
2019-07-14 04:59:30,117985,+0000 [-] Starting factory <plugins.TelnetUnix.TelnetUnix.pluginFactory instance at 0x7f87ed842200>
2019-07-14 04:59:30,119658,+0000 [-] pluginFactory starting on 10010
2019-07-14 04:59:30,119755,+0000 [-] Starting factory <plugins.TelnetWindows.TelnetWindows.pluginFactory instance at 0x7f87ed4ff3b0>
2019-07-14 04:59:30,121256,+0000 [-] pluginFactory starting on 2048
2019-07-14 04:59:30,121354,+0000 [-] Starting factory <plugins.Random.Random.pluginFactory instance at 0x7f87ed4ff830>
2019-07-14 04:59:30,125075,+0000 [-] pluginFactory starting on 4096
2019-07-14 04:59:30,125214,+0000 [-] Starting factory <plugins.HashCountRandom.HashCountRandom.pluginFactory instance at 0x7f87ed4ffbd8>
2019-07-14 04:59:30,126780,+0000 [-] (TCP Port 10007 Closed)
2019-07-14 04:59:30,126951,+0000 [-] Stopping factory <plugins.Echo.Echo.pluginFactory instance at 0x7f87ee126fc8>
2019-07-14 04:59:30,127055,+0000 [-] (UDP Port 10007 Closed)
2019-07-14 04:59:30,127160,+0000 [-] Stopping protocol <plugins.Echo_udp.Echo.pluginMain instance at 0x7f87ed82d680>
2019-07-14 04:59:30,127287,+0000 [-] (TCP Port 10008 Closed)
2019-07-14 04:59:30,127397,+0000 [-] Stopping factory <plugins.MOTD.MOTD.pluginFactory instance at 0x7f87ed8385f0>
2019-07-14 04:59:30,127539,+0000 [-] (UDP Port 10008 Closed)
2019-07-14 04:59:30,127671,+0000 [-] Stopping protocol <plugins.MOTD_udp.MOTD.pluginMain instance at 0x7f87ed838a70>
2019-07-14 04:59:30,127782,+0000 [-] (TCP Port 10009 Closed)
2019-07-14 04:59:30,127905,+0000 [-] Stopping factory <plugins.TelnetUnix.TelnetUnix.pluginFactory instance at 0x7f87ed842200>
2019-07-14 04:59:30,127998,+0000 [-] (TCP Port 10010 Closed)
2019-07-14 04:59:30,128101,+0000 [-] Stopping factory <plugins.TelnetWindows.TelnetWindows.pluginFactory instance at 0x7f87ed4ff3b0>
2019-07-14 04:59:30,128191,+0000 [-] (TCP Port 2048 Closed)
2019-07-14 04:59:30,128304,+0000 [-] Stopping factory <plugins.Random.Random.pluginFactory instance at 0x7f87ed4ff830>
2019-07-14 04:59:30,128393,+0000 [-] (TCP Port 4096 Closed)
2019-07-14 04:59:30,128589,+0000 [-] Stopping factory <plugins.HashCountRandom.HashCountRandom.pluginFactory instance at 0x7f87ed4ffbd8>
2019-07-14 04:59:32,383961,+0000 [-] pluginFactory starting on 10007
2019-07-14 04:59:32,384180,+0000 [-] Starting factory <plugins.Echo.Echo.pluginFactory instance at 0x7f87ee126fc8>
2019-07-14 04:59:32,384356,+0000 [-] pluginMain starting on 10007
2019-07-14 04:59:32,384448,+0000 [-] Starting protocol <plugins.Echo_udp.Echo.pluginMain instance at 0x7f87ed82d680>
2019-07-14 04:59:32,384633,+0000 [-] pluginFactory starting on 10008
2019-07-14 04:59:32,384714,+0000 [-] Starting factory <plugins.MOTD.MOTD.pluginFactory instance at 0x7f87ed8385f0>
2019-07-14 04:59:32,384900,+0000 [-] pluginMain starting on 10008
2019-07-14 04:59:32,384989,+0000 [-] Starting protocol <plugins.MOTD_udp.MOTD.pluginMain instance at 0x7f87ed838a70>
2019-07-14 04:59:32,385153,+0000 [-] pluginFactory starting on 10009
2019-07-14 04:59:32,385245,+0000 [-] Starting factory <plugins.TelnetUnix.TelnetUnix.pluginFactory instance at 0x7f87ed842200>
2019-07-14 04:59:32,385392,+0000 [-] pluginFactory starting on 10010
2019-07-14 04:59:32,385497,+0000 [-] Starting factory <plugins.TelnetWindows.TelnetWindows.pluginFactory instance at 0x7f87ed4ff3b0>
2019-07-14 04:59:32,385639,+0000 [-] pluginFactory starting on 2048
2019-07-14 04:59:32,385714,+0000 [-] Starting factory <plugins.Random.Random.pluginFactory instance at 0x7f87ed4ff830>
2019-07-14 04:59:32,385910,+0000 [-] pluginFactory starting on 4096
2019-07-14 04:59:32,385990,+0000 [-] Starting factory <plugins.HashCountRandom.HashCountRandom.pluginFactory instance at 0x7f87ed4ffbd8>
2019-07-14 04:59:58,569027,+0000 [plugins.MOTD.MOTD.pluginFactory] (TCP Port 10008 Closed)
2019-07-14 04:59:58,569414,+0000 [plugins.MOTD.MOTD.pluginFactory] Stopping factory <plugins.MOTD.MOTD.pluginFactory instance at 0x7f87ed8385f0>
2019-07-14 04:59:58,569535,+0000 [plugins.Echo.Echo.pluginFactory] (TCP Port 10007 Closed)
2019-07-14 04:59:58,569647,+0000 [plugins.Echo.Echo.pluginFactory] Stopping factory <plugins.Echo.Echo.pluginFactory instance at 0x7f87ee126fc8>
2019-07-14 04:59:58,569754,+0000 [plugins.HashCountRandom.HashCountRandom.pluginFactory] (TCP Port 4096 Closed)
2019-07-14 04:59:58,569908,+0000 [plugins.HashCountRandom.HashCountRandom.pluginFactory] Stopping factory <plugins.HashCountRandom.HashCountRandom.pluginFactory instance at 0x7f87ed4ffbd8>
2019-07-14 04:59:58,570039,+0000 [plugins.TelnetWindows.TelnetWindows.pluginFactory] (TCP Port 10010 Closed)
2019-07-14 04:59:58,570147,+0000 [plugins.TelnetWindows.TelnetWindows.pluginFactory] Stopping factory <plugins.TelnetWindows.TelnetWindows.pluginFactory instance at 0x7f87ed4ff3b0>
2019-07-14 04:59:58,570266,+0000 [pluginMain (UDP)] (UDP Port 10007 Closed)
2019-07-14 04:59:58,570377,+0000 [pluginMain (UDP)] Stopping protocol <plugins.Echo_udp.Echo.pluginMain instance at 0x7f87ed82d680>
2019-07-14 04:59:58,570495,+0000 [pluginMain (UDP)] (UDP Port 10008 Closed)
2019-07-14 04:59:58,570581,+0000 [pluginMain (UDP)] Stopping protocol <plugins.MOTD_udp.MOTD.pluginMain instance at 0x7f87ed838a70>
2019-07-14 04:59:58,570693,+0000 [plugins.TelnetUnix.TelnetUnix.pluginFactory] (TCP Port 10009 Closed)
2019-07-14 04:59:58,570796,+0000 [plugins.TelnetUnix.TelnetUnix.pluginFactory] Stopping factory <plugins.TelnetUnix.TelnetUnix.pluginFactory instance at 0x7f87ed842200>
2019-07-14 04:59:58,570924,+0000 [plugins.Random.Random.pluginFactory] (TCP Port 2048 Closed)
2019-07-14 04:59:58,571056,+0000 [plugins.Random.Random.pluginFactory] Stopping factory <plugins.Random.Random.pluginFactory instance at 0x7f87ed4ff830>
2019-07-14 04:59:58,571153,+0000 [-] Main loop terminated.
2019-07-14 05:02:53,822740,+0000 [-] Log opened.
2019-07-14 05:02:53,825524,+0000 [-] HoneyPy (0.7.0) Started
2019-07-14 05:02:53,848438,+0000 [-] pluginFactory starting on 10007
2019-07-14 05:02:53,848664,+0000 [-] Starting factory <plugins.Echo.Echo.pluginFactory instance at 0x7f603d4371b8>
2019-07-14 05:02:53,849832,+0000 [-] pluginMain starting on 10007
2019-07-14 05:02:53,849936,+0000 [-] Starting protocol <plugins.Echo_udp.Echo.pluginMain instance at 0x7f603cb37638>
2019-07-14 05:02:53,851162,+0000 [-] pluginFactory starting on 10008
2019-07-14 05:02:53,851259,+0000 [-] Starting factory <plugins.MOTD.MOTD.pluginFactory instance at 0x7f603cb42488>
2019-07-14 05:02:53,852188,+0000 [-] pluginMain starting on 10008
2019-07-14 05:02:53,852285,+0000 [-] Starting protocol <plugins.MOTD_udp.MOTD.pluginMain instance at 0x7f603cb42878>
2019-07-14 05:02:53,862373,+0000 [-] pluginFactory starting on 10009
2019-07-14 05:02:53,862539,+0000 [-] Starting factory <plugins.TelnetUnix.TelnetUnix.pluginFactory instance at 0x7f603cb46e60>
2019-07-14 05:02:53,863885,+0000 [-] pluginFactory starting on 10010
2019-07-14 05:02:53,864024,+0000 [-] Starting factory <plugins.TelnetWindows.TelnetWindows.pluginFactory instance at 0x7f603c807f38>
2019-07-14 05:02:53,865143,+0000 [-] pluginFactory starting on 2048
2019-07-14 05:02:53,865272,+0000 [-] Starting factory <plugins.Random.Random.pluginFactory instance at 0x7f603c80c368>
2019-07-14 05:02:53,866443,+0000 [-] pluginFactory starting on 4096
2019-07-14 05:02:53,866534,+0000 [-] Starting factory <plugins.HashCountRandom.HashCountRandom.pluginFactory instance at 0x7f603c80c680>
2019-07-14 05:03:02,456409,+0000 [plugins.TelnetUnix.TelnetUnix.pluginFactory] a83b2652-a5f4-11e9-80ad-0242ac110002 TCP CONNECT 172.17.0.2 10009 Telnet 172.17.0.3 35880
2019-07-14 05:03:08,465192,+0000 [TelnetUnix,0,172.17.0.3] a83b2652-a5f4-11e9-80ad-0242ac110002 TCP RX 172.17.0.2 10009 Telnet 172.17.0.3 35880 0d0a0d0a
2019-07-14 05:03:08,465512,+0000 [TelnetUnix,0,172.17.0.3] a83b2652-a5f4-11e9-80ad-0242ac110002 TCP TX 172.17.0.2 10009 Telnet 172.17.0.3 35880 0d0a696e76616c6964206c6f67696e0d0a70617373776f72643a
2019-07-14 05:03:13,471376,+0000 [plugins.TelnetUnix.TelnetUnix.pluginFactory] aecbe7fe-a5f4-11e9-80ad-0242ac110002 TCP CONNECT 172.17.0.2 10009 Telnet 172.17.0.3 35912
2019-07-14 05:03:13,471632,+0000 [TelnetUnix,1,172.17.0.3] aecbe7fe-a5f4-11e9-80ad-0242ac110002 TCP RX 172.17.0.2 10009 Telnet 172.17.0.3 35912 474554202f20485454502f312e300d0a0d0a
2019-07-14 05:03:13,471797,+0000 [TelnetUnix,1,172.17.0.3] aecbe7fe-a5f4-11e9-80ad-0242ac110002 TCP TX 172.17.0.2 10009 Telnet 172.17.0.3 35912 0d0a696e76616c6964206c6f67696e0d0a70617373776f72643a
2019-07-14 05:03:18,476130,+0000 [plugins.TelnetUnix.TelnetUnix.pluginFactory] b1c79232-a5f4-11e9-80ad-0242ac110002 TCP CONNECT 172.17.0.2 10009 Telnet 172.17.0.3 35920
2019-07-14 05:03:18,476437,+0000 [TelnetUnix,2,172.17.0.3] b1c79232-a5f4-11e9-80ad-0242ac110002 TCP RX 172.17.0.2 10009 Telnet 172.17.0.3 35920 4f5054494f4e53202f20485454502f312e300d0a0d0a
2019-07-14 05:03:18,476645,+0000 [TelnetUnix,2,172.17.0.3] b1c79232-a5f4-11e9-80ad-0242ac110002 TCP TX 172.17.0.2 10009 Telnet 172.17.0.3 35920 0d0a696e76616c6964206c6f67696e0d0a70617373776f72643a
2019-07-14 05:03:23,481540,+0000 [plugins.TelnetUnix.TelnetUnix.pluginFactory] b4c35660-a5f4-11e9-80ad-0242ac110002 TCP CONNECT 172.17.0.2 10009 Telnet 172.17.0.3 35924
2019-07-14 05:03:23,481770,+0000 [TelnetUnix,3,172.17.0.3] b4c35660-a5f4-11e9-80ad-0242ac110002 TCP RX 172.17.0.2 10009 Telnet 172.17.0.3 35924 4f5054494f4e53202f20525453502f312e300d0a0d0a
2019-07-14 05:03:23,481930,+0000 [TelnetUnix,3,172.17.0.3] b4c35660-a5f4-11e9-80ad-0242ac110002 TCP TX 172.17.0.2 10009 Telnet 172.17.0.3 35924 0d0a696e76616c6964206c6f67696e0d0a70617373776f72643a
2019-07-14 05:03:28,487332,+0000 [plugins.TelnetUnix.TelnetUnix.pluginFactory] b7bf27c2-a5f4-11e9-80ad-0242ac110002 TCP CONNECT 172.17.0.2 10009 Telnet 172.17.0.3 35956
2019-07-14 05:03:28,487918,+0000 [TelnetUnix,4,172.17.0.3] b7bf27c2-a5f4-11e9-80ad-0242ac110002 TCP RX 172.17.0.2 10009 Telnet 172.17.0.3 35956 8000002872fe1d130000000000000002000186a00001977c0000000000000000000000000000000000000000
2019-07-14 05:03:33,487986,+0000 [plugins.TelnetUnix.TelnetUnix.pluginFactory] baba32c8-a5f4-11e9-80ad-0242ac110002 TCP CONNECT 172.17.0.2 10009 Telnet 172.17.0.3 35966
2019-07-14 05:03:33,488274,+0000 [TelnetUnix,5,172.17.0.3] baba32c8-a5f4-11e9-80ad-0242ac110002 TCP RX 172.17.0.2 10009 Telnet 172.17.0.3 35966 001e0006010000010000000000000776657273696f6e0462696e640000100003
2019-07-14 05:03:38,489205,+0000 [plugins.TelnetUnix.TelnetUnix.pluginFactory] bdb553a4-a5f4-11e9-80ad-0242ac110002 TCP CONNECT 172.17.0.2 10009 Telnet 172.17.0.3 35998
2019-07-14 05:03:38,489502,+0000 [TelnetUnix,6,172.17.0.3] bdb553a4-a5f4-11e9-80ad-0242ac110002 TCP RX 172.17.0.2 10009 Telnet 172.17.0.3 35998 000c000010000000000000000000
2019-07-14 05:03:43,490199,+0000 [plugins.TelnetUnix.TelnetUnix.pluginFactory] c0b06a12-a5f4-11e9-80ad-0242ac110002 TCP CONNECT 172.17.0.2 10009 Telnet 172.17.0.3 36004
2019-07-14 05:03:43,490858,+0000 [TelnetUnix,7,172.17.0.3] c0b06a12-a5f4-11e9-80ad-0242ac110002 TCP RX 172.17.0.2 10009 Telnet 172.17.0.3 36004 48454c500d0a
2019-07-14 05:03:50,998239,+0000 [plugins.TelnetUnix.TelnetUnix.pluginFactory] c52a0c38-a5f4-11e9-80ad-0242ac110002 TCP CONNECT 172.17.0.2 10009 Telnet 172.17.0.3 36016
2019-07-14 05:03:50,998716,+0000 [TelnetUnix,8,172.17.0.3] c52a0c38-a5f4-11e9-80ad-0242ac110002 TCP RX 172.17.0.2 10009 Telnet 172.17.0.3 36016 16030000530100004f03003f47d7f7ba2ceeeab2607ef300fd827bb9d596c8779be6c4db3c3ddb6fef106e00002800160013000a006600050004006500640063006200610060001500120009001400110008000600030100
2019-07-14 05:03:55,997604,+0000 [plugins.TelnetUnix.TelnetUnix.pluginFactory] c824e4c6-a5f4-11e9-80ad-0242ac110002 TCP CONNECT 172.17.0.2 10009 Telnet 172.17.0.3 36056
2019-07-14 05:03:55,997937,+0000 [TelnetUnix,9,172.17.0.3] c824e4c6-a5f4-11e9-80ad-0242ac110002 TCP RX 172.17.0.2 10009 Telnet 172.17.0.3 36056 1603000069010000650303551ca7e472616e646f6d3172616e646f6d3272616e646f6d3372616e646f6d3400000c002f000a00130039000400ff01000030000d002c002a000100030002060106030602020102030202030103030302040104030402010101030102050105030502
2019-07-14 05:04:01,002114,+0000 [plugins.TelnetUnix.TelnetUnix.pluginFactory] cb208388-a5f4-11e9-80ad-0242ac110002 TCP CONNECT 172.17.0.2 10009 Telnet 172.17.0.3 36060
2019-07-14 05:04:01,002541,+0000 [TelnetUnix,10,172.17.0.3] cb208388-a5f4-11e9-80ad-0242ac110002 TCP RX 172.17.0.2 10009 Telnet 172.17.0.3 36060 000000716a816e30816ba103020105a20302010aa4815e305ca00703050050800010a2041b024e4da3173015a003020100a10e300c1b066b72627467741b024e4da511180f31393730303130313030303030305aa70602041f1eb9d9a8173015020112020111020110020117020101020103020102
2019-07-14 05:04:06,008433,+0000 [plugins.TelnetUnix.TelnetUnix.pluginFactory] ce1c6a66-a5f4-11e9-80ad-0242ac110002 TCP CONNECT 172.17.0.2 10009 Telnet 172.17.0.3 36064
2019-07-14 05:04:06,009582,+0000 [TelnetUnix,11,172.17.0.3] ce1c6a66-a5f4-11e9-80ad-0242ac110002 TCP RX 172.17.0.2 10009 Telnet 172.17.0.3 36064 000000a4ff534d4272000000000801400000000000000000000000000000400600000100008100025043204e4554574f524b2050524f4752414d20312e3000024d4943524f534f4654204e4554574f524b5320312e303300024d4943524f534f4654204e4554574f524b5320332e3000024c414e4d414e312e3000024c4d312e3258303032000253616d626100024e54204c414e4d414e20312e3000024e54204c4d20302e313200
2019-07-14 05:04:11,009928,+0000 [plugins.TelnetUnix.TelnetUnix.pluginFactory] d1179664-a5f4-11e9-80ad-0242ac110002 TCP CONNECT 172.17.0.2 10009 Telnet 172.17.0.3 36098
2019-07-14 05:04:11,010772,+0000 [TelnetUnix,12,172.17.0.3] d1179664-a5f4-11e9-80ad-0242ac110002 TCP RX 172.17.0.2 10009 Telnet 172.17.0.3 36098 6c000b000000000000000000
2019-07-14 05:04:16,015482,+0000 [plugins.TelnetUnix.TelnetUnix.pluginFactory] d4135fec-a5f4-11e9-80ad-0242ac110002 TCP CONNECT 172.17.0.2 10009 Telnet 172.17.0.3 36102
2019-07-14 05:04:16,016509,+0000 [TelnetUnix,13,172.17.0.3] d4135fec-a5f4-11e9-80ad-0242ac110002 TCP RX 172.17.0.2 10009 Telnet 172.17.0.3 36102 474554202f6e696365253230706f7274732532432f5472692536456974792e74787425326562616b20485454502f312e300d0a0d0a
2019-07-14 05:04:16,016808,+0000 [TelnetUnix,13,172.17.0.3] d4135fec-a5f4-11e9-80ad-0242ac110002 TCP TX 172.17.0.2 10009 Telnet 172.17.0.3 36102 0d0a696e76616c6964206c6f67696e0d0a70617373776f72643a
2019-07-14 05:04:21,018296,+0000 [plugins.TelnetUnix.TelnetUnix.pluginFactory] d70ebdc2-a5f4-11e9-80ad-0242ac110002 TCP CONNECT 172.17.0.2 10009 Telnet 172.17.0.3 36136
2019-07-14 05:04:21,019209,+0000 [TelnetUnix,14,172.17.0.3] d70ebdc2-a5f4-11e9-80ad-0242ac110002 TCP RX 172.17.0.2 10009 Telnet 172.17.0.3 36136 0164656661756c740a
2019-07-14 05:04:26,024199,+0000 [plugins.TelnetUnix.TelnetUnix.pluginFactory] da0a9636-a5f4-11e9-80ad-0242ac110002 TCP CONNECT 172.17.0.2 10009 Telnet 172.17.0.3 36140
2019-07-14 05:04:26,025164,+0000 [TelnetUnix,15,172.17.0.3] da0a9636-a5f4-11e9-80ad-0242ac110002 TCP RX 172.17.0.2 10009 Telnet 172.17.0.3 36140 30840000002d02010763840000002404000a01000a0100020100020164010100870b6f626a656374436c617373308400000000
2019-07-14 05:04:34,549887,+0000 [-] Received SIGINT, shutting down.
2019-07-14 05:04:34,550553,+0000 [plugins.Random.Random.pluginFactory] (TCP Port 2048 Closed)
2019-07-14 05:04:34,550779,+0000 [plugins.Random.Random.pluginFactory] Stopping factory <plugins.Random.Random.pluginFactory instance at 0x7f603c80c368>
2019-07-14 05:04:34,550950,+0000 [pluginMain (UDP)] (UDP Port 10008 Closed)
2019-07-14 05:04:34,551073,+0000 [pluginMain (UDP)] Stopping protocol <plugins.MOTD_udp.MOTD.pluginMain instance at 0x7f603cb42878>
2019-07-14 05:04:34,551260,+0000 [plugins.HashCountRandom.HashCountRandom.pluginFactory] (TCP Port 4096 Closed)
2019-07-14 05:04:34,551382,+0000 [plugins.HashCountRandom.HashCountRandom.pluginFactory] Stopping factory <plugins.HashCountRandom.HashCountRandom.pluginFactory instance at 0x7f603c80c680>
2019-07-14 05:04:34,551518,+0000 [plugins.MOTD.MOTD.pluginFactory] (TCP Port 10008 Closed)
2019-07-14 05:04:34,551625,+0000 [plugins.MOTD.MOTD.pluginFactory] Stopping factory <plugins.MOTD.MOTD.pluginFactory instance at 0x7f603cb42488>
2019-07-14 05:04:34,551776,+0000 [plugins.Echo.Echo.pluginFactory] (TCP Port 10007 Closed)
2019-07-14 05:04:34,551905,+0000 [plugins.Echo.Echo.pluginFactory] Stopping factory <plugins.Echo.Echo.pluginFactory instance at 0x7f603d4371b8>
2019-07-14 05:04:34,552005,+0000 [pluginMain (UDP)] (UDP Port 10007 Closed)
2019-07-14 05:04:34,552090,+0000 [pluginMain (UDP)] Stopping protocol <plugins.Echo_udp.Echo.pluginMain instance at 0x7f603cb37638>
2019-07-14 05:04:34,552200,+0000 [plugins.TelnetWindows.TelnetWindows.pluginFactory] (TCP Port 10010 Closed)
2019-07-14 05:04:34,552304,+0000 [plugins.TelnetWindows.TelnetWindows.pluginFactory] Stopping factory <plugins.TelnetWindows.TelnetWindows.pluginFactory instance at 0x7f603c807f38>
2019-07-14 05:04:34,552434,+0000 [plugins.TelnetUnix.TelnetUnix.pluginFactory] (TCP Port 10009 Closed)
2019-07-14 05:04:34,552721,+0000 [plugins.TelnetUnix.TelnetUnix.pluginFactory] Stopping factory <plugins.TelnetUnix.TelnetUnix.pluginFactory instance at 0x7f603cb46e60>
2019-07-14 05:04:34,553037,+0000 [-] Main loop terminated.总结
难易性★☆☆☆☆
可用性★★★★☆
展示性★☆☆☆☆
交互性★★★☆☆
RDPy
RDPY是Microsoft RDP远程桌面协议协议客户端和服务器端的纯Python实现。RDPY是在事件驱动的网络引擎Twisted上构建的。RDPY支持标准RDP安全层基于SSL的RDP和NLA身份验证通过ntlmv2身份验证协议。
RDPY提供以下RDP和VNC二进制文件
RDP Man In Middle代理记录会话
RDP蜜罐
RDP截图
RDP客户端
VNC客户端
VNC截图
RSS播放器
这个蜜罐是代理蜜罐下面图的104是win2008的IP是基于代理真实的windows服务器的蜜罐。

当攻击者访问蜜罐的3389的端口后就会记录视频画面和键盘。我们可以通过rssplayer重现视频和敲击键盘命令


hon这个脚本重现攻击画面的过程。

不过有点遗憾的是使用hydra爆破的时候会报错这如果做蜜罐的话会产生大量的rss文件很麻烦这玩意我觉得比较适合内网钓鱼

总结
难易性★☆☆☆☆
可用性★★★★★
展示性★★★★★
交互性★★★★★
Honeyprint
这个蜜罐的功能是模仿打印机的功能。启动之后使用nmap扫描没反应

telnet 9100会报错的

我找了一款打印机渗透软件https://github.com/RUB-NDS/PRET.git效果如下它会超时连接失败也就是交互性很低

没有日志记录只是将日志显示在终端上面。
总结
难易性★☆☆☆☆
可用性★★☆☆☆
展示性★☆☆☆☆
交互性★☆☆☆☆
Tom’s Honeypot
低交互 Python 蜜罐
需要修改监听的IP为0.0.0.0

查看程序代码可以看到它开放了以下的端口

启动以下程序使用hydra爆破rdp协议只能捕捉到账号名没有密码。

使用hydra爆破mssql协议出现了一串编码

程序运行之后会在目录下生成日志文件
root@l-virtual-machine:/hon/toms_honeypot# tail -f -n 50 toms_honeypot.log
020002000000020000000000000000000000000000000000000000000000000000000000000000726f6f740000000000000000000000000000000000000000000000000000044644530000000000000000000000000000000000000000000000000000000330303030303061300000000000000000000000000000000000201881b82c080301060a090101000000000000000000737175656c646120312e30000000000000000000000000000000000000000b0000000000000000000000000000000000000000000000000000000000000000034644530000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000040200004d5344424c49420000000706000000000d11000000000000000000000000000000000000000000000000
2019-07-14 13:46:45.9990: TCPData on port 1433 from: 127.0.0.1 (40546/TCP):
020002000000020000000000000000000000000000000000000000000000000000000000000000726f6f7400000000000000000000000000000000000000000000000000000448554a46474a0000000000000000000000000000000000000000000000000630303030303061300000000000000000000000000000000000201881b82c080301060a090101000000000000000000737175656c646120312e30000000000000000000000000000000000000000b00000000000000000000000000000000000000000000000000000000000000000648554a46474a0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000040200004d5344424c49420000000706000000000d11000000000000000000000000000000000000000000000000
2019-07-14 13:46:46.2218: TCPData on port 1433 from: 127.0.0.1 (40548/TCP):
020002000000020000000000000000000000000000000000000000000000000000000000000000726f6f740000000000000000000000000000000000000000000000000000044647000000000000000000000000000000000000000000000000000000000230303030303061300000000000000000000000000000000000201881b82c080301060a090101000000000000000000737175656c646120312e30000000000000000000000000000000000000000b0000000000000000000000000000000000000000000000000000000000000000024647000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000040200004d5344424c49420000000706000000000d11000000000000000000000000000000000000000000000000
2019-07-14 13:46:46.4451: TCPData on port 1433 from: 127.0.0.1 (40550/TCP):
020002000000020000000000000000000000000000000000000000000000000000000000000000726f6f740000000000000000000000000000000000000000000000000000043a77710000000000000000000000000000000000000000000000000000000330303030303061300000000000000000000000000000000000201881b82c080301060a090101000000000000000000737175656c646120312e30000000000000000000000000000000000000000b0000000000000000000000000000000000000000000000000000000000000000033a77710000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000040200004d5344424c49420000000706000000000d11000000000000000000000000000000000000000000000000
2019-07-14 13:46:46.6677: TCPData on port 1433 from: 127.0.0.1 (40552/TCP):
020002000000020000000000000000000000000000000000000000000000000000000000000000726f6f740000000000000000000000000000000000000000000000000000040000000000000000000000000000000000000000000000000000000000000030303030303061300000000000000000000000000000000000201881b82c080301060a090101000000000000000000737175656c646120312e30000000000000000000000000000000000000000b0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000040200004d5344424c49420000000706000000000d11000000000000000000000000000000000000000000000000总结
难易性★☆☆☆☆
可用性★★☆☆☆
展示性★☆☆☆☆
交互性★☆☆☆☆
Honeyport
honeyport本质上是蜜罐的简单版本。虽然蜜罐旨在模拟攻击者使用的应用程序或协议但所有honeyport查找都是来自外部方的连接之后执行特定操作通常将其列入黑名单。虽然互联网上的主机通过自动攻击定期进行端口扫描和连接但通常只有目标攻击者会连接到更多不寻常的端口以确定在其上运行的服务。通常情况下你会想要击退这些有针对性的攻击者。
Bash脚本是一个相当简单的Linux Bash honeyport脚本它使用Ncat监听给定端口然后阻止任何连接它的人的IP。它可以使用Linux的内部IPtables防火墙阻止攻击者或者如果您使用该服务它可以将IP添加到您的Dome9动态防火墙黑名单中最多可供5台服务器免费使用。Dome9解决方案的好处是任何在一个系统上列入黑名单的IP都会自动立即列入所有启用Dome9的服务器的黑名单。该脚本还具有白名单因此您可以阻止某些IP被阻止。此外我选择Ncat而不是Netcat因为它更具可扩展性可以让你用Honeyport做更多有趣的事情。在这种情况下当有人连接脚本时将执行’response.sh’。
Python脚本具有与Bash脚本相同的功能但支持Mac OS X上的IPFWLinux上的iptables和Windows上的Windows防火墙。它还允许您定义要在每个用户连接上运行的自定义脚本并将客户端的IP作为参数传递给脚本。脚本的输出在被列入黑名单之前返回给已连接的用户。
修改监听的端口并运行脚本

使用nmap进行扫描

使用ssh进行连接连接失败

里面还有一个honeystats的脚本是用来处理日志效果如下

总结
难易性★☆☆☆☆
可用性★★★☆☆
展示性★★★★☆
交互性★☆☆☆☆
Honeygrove
Honeygrove是一个基于Python的模块化蜜罐它基于Broker和Twisted Framework构建。
Honeygrove目前需要Python 3.5+并在Ubuntu 16.4Debian 9.1和ArchLinux上进行了测试。但是它应该适用于提供兼容的Python发行版的其他发行版。如果Broker不可用蜜罐本身可以在没有它的情况下使用。目前没有Broker就无法与管理控制台或监控堆栈进行通信。
按照文档安装启动之后会发现开放了以下的端口。接下来我会用nmap和hydra测试各个端口的情况。

21FTP

22,SSH

23,TELNET

25SMTP
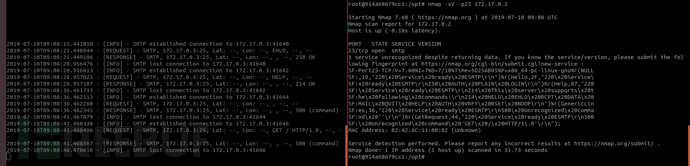

80HTTP。测试一下之后会报错的不会捕捉到密码

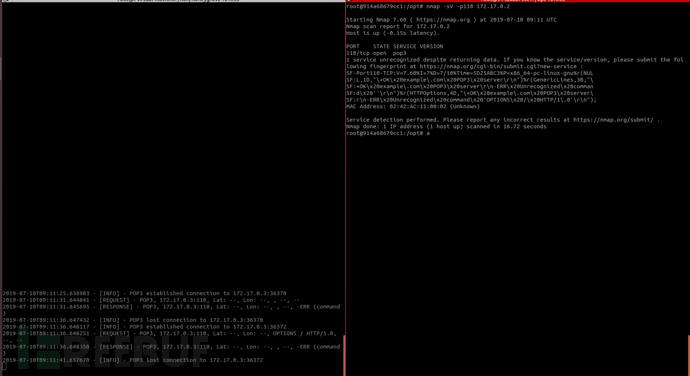
110POP3

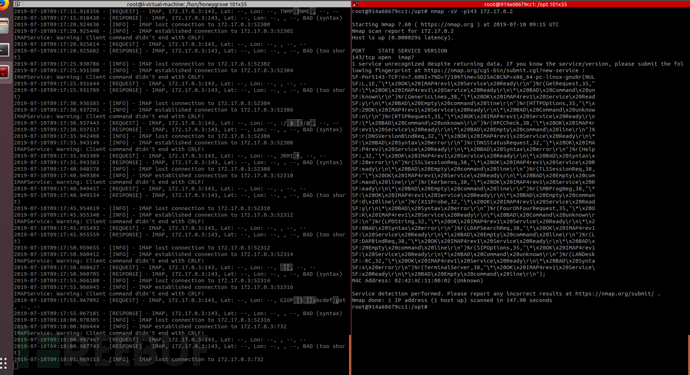
143IMAP

587smtps
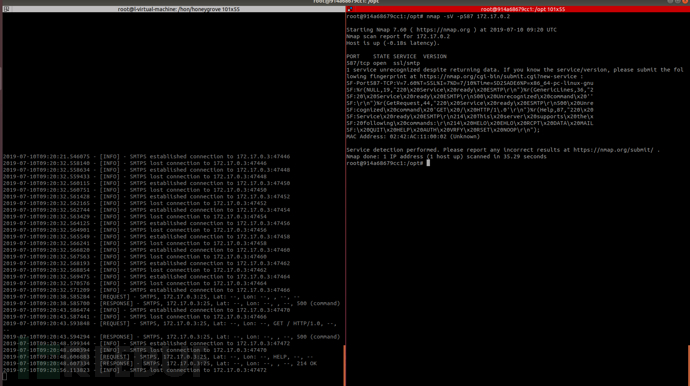

993IMAPS
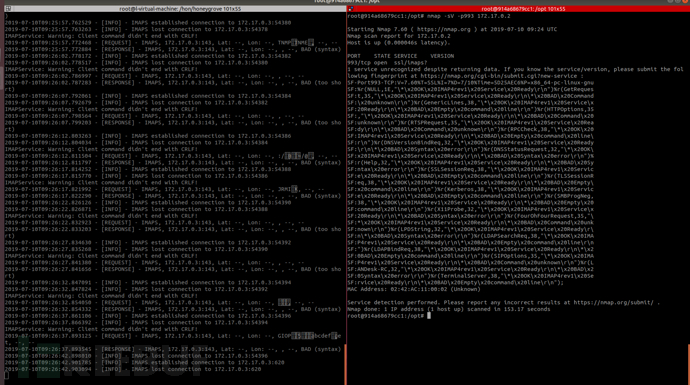

995POP3S


日志位置

总结
难易性★☆☆☆☆
可用性★★★★☆
展示性★★★★★
交互性★☆☆☆☆
honeytrap

直接用docker运行
docker run -p 8022:8022 honeytrap/honeytrap:latest我们进入容器之后查看它的配置文件可以看到模拟的ssh8022端口的密码为root后来测试不是root是旁边的password很奇怪。。正常来说8022对应root8023对应password

使用ssh连接进去输入password左边是监听到攻击者输入的命令字符右边是攻击者输入的命令字符。可以看出交互性不高

还有5900开放telnet服务telnet进去随便输入密码就可以进入终端界面然后蜜罐就会开始记录攻击者的操作命令

总结
难易性★☆☆☆☆
可用性★★★★★
展示性★★★★★
交互性★★★☆☆
DemonHunter
DemnonHunter是一个分布式低交互蜜罐具有Agent / Master设计。
代理是不同协议的蜜罐master是接收攻击信息并向蜜罐管理员显示的地方。
通过使用DemonHunter您可以从各种协议处理程序中进行选择例如您可以在Apachev2.4.18或Nginx1.10.0之间进行选择。处理程序是假的您不需要在服务器上安装任何额外的东西。
每个代理都能够拥有多个协议。每个主人都可以拥有无限制的代理人数。
蜜罐的架构

直接可以用pip安装这个蜜罐
pip install demonhunter查看蜜罐的命令

这个蜜罐提供了三个服务VNChttptelnet默认是http
--hp-protocol TEXT vnc|http|telnet **default:httpHTTP
运行http服务我按照命令设置http的路径http就是404不能找到路径。它的http有两种启动一种是apache一种是nginx我都试过了都是显示404


测试telnet可以看到可以捕捉到账号和密码只是不能做交互

vnc就直接提示连接失败账号和密码都没有

日志文件
总结
难易性★☆☆☆☆
可用性★★☆☆☆
展示性★★☆☆☆
交互性★☆☆☆☆
其他蜜罐
DSHP

按照文档输入邮件账号的信息,当你被人扫描或者攻击的时候,会收到邮件报警。


总结
难易性★☆☆☆☆
可用性★★★★☆
展示性★★★★☆
交互性★☆☆☆☆
OpenCanary
直接使用pip安装opencanary
首先你要先运行这个蜜罐,需要把默认的配置文件复制过来。我们看到下面的配置文件,里面提供了很多的虚假服务,如果你有需要那种服务的话,你只需在下面将false修改为true即可。
root@l-virtual-machine:/hon# opencanaryd --copyconfig
[*] A sample config file is ready (/root/.opencanary.conf)
[*] Edit your configuration, then launch with "opencanaryd --start"
root@l-virtual-machine:/hon# opencanaryd --start
** We hope you enjoy using OpenCanary. For more open source Canary goodness, head over to canarytokens.org. **
[-] Failed to open opencanary.conf for reading ([Errno 2] No such file or directory: 'opencanary.conf')
[-] Using config file: /root/.opencanary.conf
{"dst_host": "", "dst_port": -1, "local_time": "2019-07-10 13:08:55.101798", "logdata": {"msg": {"logdata": "Added service from class CanaryFTP in opencanary.modules.ftp to fake"}}, "logtype": 1001, "node_id": "opencanary-1", "src_host": "", "src_port": -1}
{"dst_host": "", "dst_port": -1, "local_time": "2019-07-10 13:08:55.102043", "logdata": {"msg": "Canary running!!!"}, "logtype": 1001, "node_id": "opencanary-1", "src_host": "", "src_port": -1}
root@l-virtual-machine:/hon# cat /root/.opencanary.conf
{
"device.node_id": "opencanary-1",
"git.enabled": false,
"git.port" : 9418,
"ftp.enabled": true,
"ftp.port": 21,
"ftp.banner": "FTP server ready",
"http.banner": "Apache/2.2.22 (Ubuntu)",
"http.enabled": false,
"http.port": 80,
"http.skin": "nasLogin",
"http.skin.list": [
{
"desc": "Plain HTML Login",
"name": "basicLogin"
},
{
"desc": "Synology NAS Login",
"name": "nasLogin"
}
],
"httpproxy.enabled" : false,
"httpproxy.port": 8080,
"httpproxy.skin": "squid",
"httproxy.skin.list": [
{
"desc": "Squid",
"name": "squid"
},
{
"desc": "Microsoft ISA Server Web Proxy",
"name": "ms-isa"
}
],
"logger": {
"class": "PyLogger",
"kwargs": {
"formatters": {
"plain": {
"format": "%(message)s"
}
},
"handlers": {
"console": {
"class": "logging.StreamHandler",
"stream": "ext://sys.stdout"
},
"file": {
"class": "logging.FileHandler",
"filename": "/var/tmp/opencanary.log"
}
}
}
},
"portscan.enabled": false,
"portscan.logfile":"/var/log/kern.log",
"portscan.synrate": 5,
"portscan.nmaposrate": 5,
"portscan.lorate": 3,
"smb.auditfile": "/var/log/samba-audit.log",
"smb.enabled": false,
"mysql.enabled": false,
"mysql.port": 3306,
"mysql.banner": "5.5.43-0ubuntu0.14.04.1",
"ssh.enabled": false,
"ssh.port": 22,
"ssh.version": "SSH-2.0-OpenSSH_5.1p1 Debian-4",
"redis.enabled": false,
"redis.port": 6379,
"rdp.enabled": false,
"rdp.port": 3389,
"sip.enabled": false,
"sip.port": 5060,
"snmp.enabled": false,
"snmp.port": 161,
"ntp.enabled": false,
"ntp.port": "123",
"tftp.enabled": false,
"tftp.port": 69,
"tcpbanner.maxnum":10,
"tcpbanner.enabled": false,
"tcpbanner_1.enabled": false,
"tcpbanner_1.port": 8001,
"tcpbanner_1.datareceivedbanner": "",
"tcpbanner_1.initbanner": "",
"tcpbanner_1.alertstring.enabled": false,
"tcpbanner_1.alertstring": "",
"tcpbanner_1.keep_alive.enabled": false,
"tcpbanner_1.keep_alive_secret": "",
"tcpbanner_1.keep_alive_probes": 11,
"tcpbanner_1.keep_alive_interval":300,
"tcpbanner_1.keep_alive_idle": 300,
"telnet.enabled": false,
"telnet.port": "23",
"telnet.banner": "",
"telnet.honeycreds": [
{
"username": "admin",
"password": "$pbkdf2-sha512$19000$bG1NaY3xvjdGyBlj7N37Xw$dGrmBqqWa1okTCpN3QEmeo9j5DuV2u1EuVFD8Di0GxNiM64To5O/Y66f7UASvnQr8.LCzqTm6awC8Kj/aGKvwA"
},
{
"username": "admin",
"password": "admin1"
}
],
"mssql.enabled": false,
"mssql.version": "2012",
"mssql.port":1433,
"vnc.enabled": false,
"vnc.port":5000
}这个蜜罐的默认配置文件只开放了ftp端口,那我就只测试ftp端口,使用hydra爆破FTP服务,在左边就可以看到捕捉到的FTP被爆破的信息。

总结
难易性★☆☆☆☆
可用性★★★★★
展示性★★★★☆
交互性★★☆☆☆
UDPot Honeypot
这个脚本背后的想法是提供一个DNS蜜罐,它将所有请求记录到SQLite数据库并具有可配置的交互级别。
它可以配置为仅解析许多DNS请求,看起来像攻击者的开放解析器,之后它充当了一个下沉洞。
对于来自源IP的每个请求,只有一个自定义数量的请求在作为下沉孔工作之前才真正解决(发回DNS回复); 在可配置的超时之后,它可以重新启动循环。
按照文档安装之后完python依赖库,运行之后,使用nmap,程序会报错。

使用nslookup测试这个dns蜜罐

它的日志使用sqlite存储的,可以看到解析的记录

总结
难易性★☆☆☆☆
可用性★★★★★
展示性★★★★★
交互性★★★★☆
Artillery
开源蓝队工具,旨在通过多种办法保护 Linux 和 Windows 操作系统。
根据文档安装之后,查看它的配置文件
#############################################################################################
#
# This is the Artillery configuration file. Change these variables and flags to change how
# this behaves.
#
# Artillery written by: Dave Kennedy (ReL1K)
# Website: https://www.binarydefense.com
# Email: info [at] binarydefense.com
# Download: git clone https://github.com/binarydefense/artillery artillery/
# Install: python setup.py
#
#############################################################################################
#
# DETERMINE IF YOU WANT TO MONITOR OR NOT
MONITOR="ON"
#
# THESE ARE THE FOLDERS TO MONITOR, TO ADD MORE, JUST DO "/root","/var/", etc.
MONITOR_FOLDERS="/var/www","/etc/"
#
# BASED ON SECONDS, 2 = 2 seconds.
MONITOR_FREQUENCY="60"
#
# PORT 22 CHECK
SSH_DEFAULT_PORT_CHECK="ON"
#
# EXCLUDE CERTAIN DIRECTORIES OR FILES. USE FOR EXAMPLE: /etc/passwd,/etc/hosts.allow
EXCLUDE=""
#
# DO YOU WANT TO AUTOMATICALLY BAN ON THE HONEYPOT
HONEYPOT_BAN="OFF"
#
# WHITELIST IP ADDRESSES, SPECIFY BY COMMAS ON WHAT IP ADDRESSES YOU WANT TO WHITELIST
WHITELIST_IP="127.0.0.1,localhost"
#
# PORTS TO SPAWN HONEYPOT FOR
TCPPORTS="22,1433,8080,21,5060,5061,5900,25,53,110,1723,1337,10000,5800,44443,16993"
UDPPORTS="123,53,5060,5061,3478"
#
# SHOULD THE HONEYPOT AUTOMATICALLY ADD ACCEPT RULES TO THE ARTILLERY CHAIN FOR ANY PORTS ITS LISTENING ON
HONEYPOT_AUTOACCEPT="ON"
#
# SHOULD EMAIL ALERTS BE SENT
EMAIL_ALERTS="OFF"
#
# CURRENT SUPPORT IS FOR SMTP, ENTER YOUR USERNAME AND PASSWORD HERE. LEAVE BLANK FOR OPEN RELAY
SMTP_USERNAME=""
#
# ENTER THE SMTP PASSWORD HERE. LEAVE BLANK FOR OPEN RELAY
SMTP_PASSWORD=""
#
# THIS IS WHO TO SEND THE ALERTS TO - EMAILS WILL BE SENT FROM ARTILLERY TO THIS ADDRESS
ALERT_USER_EMAIL="[email protected]"
#
# FOR SMTP ONLY HERE, THIS IS THE MAILTO
SMTP_FROM="Artillery_Incident"
#
# SMTP ADDRESS FOR SENDING EMAILS, DEFAULT IS GMAIL
SMTP_ADDRESS="smtp.gmail.com"
#
# SMTP PORT FOR SENDING EMAILS DEFAULT IS GMAIL WITH TTLS
SMTP_PORT="587"
#
# THIS WILL SEND EMAILS OUT DURING A CERTAIN FREQUENCY. IF THIS IS SET TO OFF, ALERTS
# WILL BE SENT AUTOMATICALLY AS THEY HAPPEN (CAN LEAD TO A LOT OF SPAM)
EMAIL_TIMER="ON"
#
# HOW OFTEN DO YOU WANT TO SEND EMAIL ALERTS (DEFAULT 10 MINUTES)
EMAIL_FREQUENCY="600"
#
# DO YOU WANT TO MONITOR SSH BRUTE FORCE ATTEMPTS
SSH_BRUTE_MONITOR="ON"
#
# HOW MANY ATTEMPTS BEFORE YOU BAN
SSH_BRUTE_ATTEMPTS="4"
#
# DO YOU WANT TO MONITOR FTP BRUTE FORCE ATTEMPTS
FTP_BRUTE_MONITOR="OFF"
#
# HOW MANY ATTEMPTS BEFORE YOU BAN
FTP_BRUTE_ATTEMPTS="4"
#
# DO YOU WANT TO DO AUTOMATIC UPDATES. TYPE ON OR OFF
AUTO_UPDATE="OFF"
#
# ANTI DOS WILL CONFIGURE MACHINE TO THROTTLE CONNECTIONS, TURN THIS OFF IF YOU DO NOT WANT TO USE
ANTI_DOS="OFF"
#
# THESE ARE THE PORTS THAT WILL PROVIDE ANTI-DOS PROTECTION
ANTI_DOS_PORTS="80,443"
#
# THIS WILL THROTTLE HOW MANY CONNECTIONS PER MINUTE ARE ALLOWED HOWEVER THE BURST WILL ENFORCE THIS
ANTI_DOS_THROTTLE_CONNECTIONS="50"
#
# THIS WILL ONLY ALLOW A CERTAIN BURST PER MINUTE THEN WILL ENFORCE AND NOT ALLOW ANYMORE TO CONNECT
ANTI_DOS_LIMIT_BURST="200"
#
# THIS IS THE PATH FOR THE APACHE LOG FILES INCLUDING ERROR AND ACCESS
ACCESS_LOG="/var/log/apache2/access.log"
ERROR_LOG="/var/log/apache2/error.log"
#
# THIS ALLOWS YOU TO SPECIFY AN IP ADDRESS. LEAVE THIS BLANK TO BIND TO ALL INTERFACES. EXAMPLE BIND_IP="192.168.1.154"
BIND_INTERFACE=""
#
# THIS TURNS ON THE THREAT INTELLIGENCE FEED, THIS WILL CALL TO https://www.binarydefense.com/banlist.txt IN ORDER TO FIND
# ALREADY KNOWN MALICIOUS WEBSITES. WILL PULL EVERY 24 HOURS
THREAT_INTELLIGENCE_FEED="ON"
#
# CONFIGURE THIS TO BE WHATEVER THREAT FEED YOU WANT BY DEFAULT IT WILL USE BINARY DEFENSE
# NOTE YOU CAN SPECIFY MULTIPLE THREAT FEEDS BY DOING #http://urlthreatfeed1,http://urlthreadfeed2
THREAT_FEED="https://www.binarydefense.com/banlist.txt"
#
# A THREAT SERVER IS A SERVER THAT WILL COPY THE BANLIST.TXT TO A PUBLIC HTTP LOCATION TO BE PULLED BY
# OTHER ARTILLERY SERVER. THIS IS USED IF YOU DO NOT WANT TO USE THE STANDARD BINARY DEFENSE ONE.
#
# THIS WILL DETECT IF A THREAT SERVER IS NEEDED, AS IN IT WILL COPY TO /var/www/ FOR YOU AUTOMATICALLY
THREAT_SERVER="OFF"
#
# PUBLIC LOCATION TO PULL VIA HTTP ON THE THREAT SERVER. NOTE THAT THREAT SERVER MUST BE SET TO ON
THREAT_LOCATION="/var/www/"
#
# THIS CHECKS TO SEE WHAT PERMISSIONS ARE RUNNING AS ROOT IN A WEB SERVER DIRECTORY
ROOT_CHECK="ON"
#
# Specify SYSLOG TYPE to be local, file or remote. LOCAL will pipe to syslog, REMOTE will pipe to remote SYSLOG, and file will send to alerts.log in local artillery directory
SYSLOG_TYPE="LOCAL"
#
# LOG MESSAGES (IMPORTANT: Everything except the %s are optional. e.g. a minimal message would be "%s %s %s" which would be
# the time, the ipaddress, and the port number
LOG_MESSAGE_ALERT="%s [!] Artillery has detected an attack from IP address: %s for a connection on a honeypot port: %s"
LOG_MESSAGE_BAN="%s [!] Artillery has blocked (and blacklisted) the IP Address: %s for connecting to a honeypot restricted port: %s"
#
# IF YOU SPECIFY SYSLOG TYPE TO REMOTE, SPECIFY A REMOTE SYSLOG SERVER TO SEND ALERTS TO
SYSLOG_REMOTE_HOST="192.168.0.1"
#
# IF YOU SPECIFY SYSLOG TYPE OF REMOTE, SEPCIFY A REMOTE SYSLOG PORT TO SEND ALERTS TO
SYSLOG_REMOTE_PORT="514"
#
# TURN ON CONSOLE LOGGING
CONSOLE_LOGGING="ON"
#
# RECYCLE LOGS AFTER A CERTAIN AMOUNT OF TIME - THIS WILL WIPE ALL IP ADDRESSES AND START FROM SCRATCH AFTER A CERTAIN INTERVAL
RECYCLE_IPS="OFF"
#
# RECYCLE INTERVAL AFTER A CERTAIN AMOUNT OF MINUTES IT WILL OVERWRITE THE LOG WITH A BLANK ONE AND ELIMINATE THE IPS - DEFAULT IS 7 DAYS
ARTILLERY_REFRESH="604800"
#
# PULL ADDITIONAL SOURCE FEEDS FOR BANNED IP LISTS FROM MULTIPLE OTHER SOURCES OTHER THAN ARTILLERY
SOURCE_FEEDS="ON"使用nmap测试,跟配置文件开放的端口一模一样,左边的是攻击日志。

这个蜜罐有一个HONEYPOT_BAN选项,当我选择ON选项的时候,我爆破SSH端口如左边终端下面,只是出现了一个,右边会提示连接失败。

当我选择OFF的时候,爆破FTP服务,不受任何阻碍。

这个蜜罐还提供邮件报警功能

开启DOS防御

总结
难易性★☆☆☆☆
可用性★★★★★
展示性★★★★★
交互性★★★★☆
Heralding
目前支持以下协议:ftp,telnet,ssh,http,https,pop3,pop3s,imap,imaps,smtp,vnc,postgresql和socks5。
按照文档按照和启动,如下所示
root@8ec2f3a760b8:/opt# heralding
2019-07-11 04:24:33,676 (root) Initializing Heralding version 1.0.5
2019-07-11 04:24:33,677 (root) Using default config file: "/usr/local/lib/python3.6/dist-packages/heralding/heralding.yml", if you want to customize values please copy this file to the current working directory
2019-07-11 04:24:33,698 (heralding.reporting.file_logger) File logger: Using log_auth.csv to log authentication attempts in CSV format.
2019-07-11 04:24:33,698 (heralding.reporting.file_logger) File logger: Using log_session.csv to log unified session data in CSV format.
2019-07-11 04:24:33,698 (heralding.reporting.file_logger) File logger: Using log_session.json to log complete session data in JSON format.
2019-07-11 04:24:33,700 (heralding.honeypot) Started smtp capability listening on port 25
2019-07-11 04:24:33,701 (heralding.honeypot) Started Pop3 capability listening on port 110
2019-07-11 04:24:33,703 (heralding.honeypot) Started Pop3S capability listening on port 995
2019-07-11 04:24:33,704 (heralding.honeypot) Started Socks5 capability listening on port 1080
2019-07-11 04:24:33,704 (heralding.honeypot) Started Vnc capability listening on port 5900
2019-07-11 04:24:33,705 (heralding.honeypot) Started Http capability listening on port 80
2019-07-11 04:24:33,752 (heralding.honeypot) Started SSH capability listening on port 22
2019-07-11 04:24:33,752 (heralding.honeypot) Started PostgreSQL capability listening on port 5432
2019-07-11 04:24:33,753 (heralding.honeypot) Started ftp capability listening on port 21
2019-07-11 04:24:33,753 (heralding.honeypot) Started MySQL capability listening on port 3306
2019-07-11 04:24:33,754 (heralding.honeypot) Started Imap capability listening on port 143
2019-07-11 04:24:33,755 (heralding.honeypot) Started Imaps capability listening on port 993
2019-07-11 04:24:33,755 (heralding.honeypot) Started Telnet capability listening on port 23
2019-07-11 04:24:33,756 (heralding.honeypot) Started https capability listening on port 443
2019-07-11 04:24:33,757 (root) Privileges dropped, running as nobody/nogroup.使用nmap扫描端口
root@78ffad956ab3:/# nmap -sV 172.17.0.2
Starting Nmap 7.60 ( https://nmap.org ) at 2019-07-11 04:38 UTC
Nmap scan report for 172.17.0.2
Host is up (0.000014s latency).
Not shown: 986 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
23/tcp open telnet Pocket CMD telnetd
25/tcp open smtp
80/tcp open http BaseHTTPServer 0.6 (Python 3.6.8)
110/tcp open pop3?
143/tcp open imap?
443/tcp open ssl/http BaseHTTPServer 0.6 (Python 3.6.8)
993/tcp open ssl/imaps?
995/tcp open ssl/pop3s?
1080/tcp open socks5 (Username/password authentication required)
3306/tcp open mysql MySQL 5.7.16
5432/tcp open postgresql?
5900/tcp open vnc VNC (protocol 3.7)最后会生成会话(SESSION)和验证(AUTH)的日志
root@8ec2f3a760b8:/opt# ls
heralding.log imaps.pem log_session.csv pop3s.pem
https.pem log_auth.csv log_session.json ssh.key
root@8ec2f3a760b8:/opt# cat log_session.json
{"timestamp": "2019-07-11 04:40:10.492332", "duration": 5, "session_id": "1cac1590-5d1e-421a-90de-d442e15386b2", "source_ip": "172.17.0.3", "source_port": 60018, "destination_ip": "172.17.0.2", "destination_port": 5432, "protocol": "postgresql", "num_auth_attempts": 0, "auth_attempts": [], "session_ended": true, "auxiliary_data": {}}
{"timestamp": "2019-07-11 04:40:10.492858", "duration": 5, "session_id": "dd05a3fb-e017-48da-b537-206b33ab9720", "source_ip": "172.17.0.3", "source_port": 50546, "destination_ip": "172.17.0.2", "destination_port": 143, "protocol": "imap", "num_auth_attempts": 0, "auth_attempts": [], "session_ended": true, "auxiliary_data": {}}
{"timestamp": "2019-07-11 04:40:11.518492", "duration": 5, "session_id": "4fe78f92-5e6e-4b12-b7f3-2f0fc4207f24", "source_ip": "172.17.0.3", "source_port": 48390, "destination_ip": "172.17.0.2", "destination_port": 995, "protocol": "pop3s", "num_auth_attempts": 0, "auth_attempts": [], "session_ended": true, "auxiliary_data": {}}
{"timestamp": "2019-07-11 04:40:11.523369", "duration": 5, "session_id": "c4efcc0c-17bc-4783-8511-66165f9bdaa1", "source_ip": "172.17.0.3", "source_port": 37698, "destination_ip": "172.17.0.2", "destination_port": 993, "protocol": "imaps", "num_auth_attempts": 0, "auth_attempts": [], "session_ended": true, "auxiliary_data": {}}
{"timestamp": "2019-07-11 04:40:15.498686", "duration": 5, "session_id": "d7da8eb6-47a0-4c7a-bac4-3aed2252c58d", "source_ip": "172.17.0.3", "source_port": 60030, "destination_ip": "172.17.0.2", "destination_port": 5432, "protocol": "postgresql", "num_auth_attempts": 0, "auth_attempts": [], "session_ended": true, "auxiliary_data": {}}
{"timestamp": "2019-07-11 04:40:15.498887", "duration": 5, "session_id": "9d84b148-cfe4-48f1-ac6e-31212d22ef3b", "source_ip": "172.17.0.3", "source_port": 50558, "destination_ip": "172.17.0.2", "destination_port": 143, "protocol": "imap", "num_auth_attempts": 0, "auth_attempts": [], "session_ended": true, "auxiliary_data": {}}
{"timestamp": "2019-07-11 04:40:15.498521", "duration": 5, "session_id": "0d6a5729-96c8-4347-8d56-eb42ece64501", "source_ip": "172.17.0.3", "source_port": 51784, "destination_ip": "172.17.0.2", "destination_port": 110, "protocol": "pop3", "num_auth_attempts": 0, "auth_attempts": [], "session_ended": true, "auxiliary_data": {}}
{"timestamp": "2019-07-11 04:40:16.520882", "duration": 5, "session_id": "d221bfd6-01d7-41d8-8d76-acb727bff885", "source_ip": "172.17.0.3", "source_port": 48400, "destination_ip": "172.17.0.2", "destination_port": 995, "protocol": "pop3s", "num_auth_attempts": 0, "auth_attempts": [], "session_ended": true, "auxiliary_data": {}}
{"timestamp": "2019-07-11 04:40:16.524779", "duration": 5, "session_id": "95284fbe-029c-4244-bf3b-3cd91cc60ae3", "source_ip": "172.17.0.3", "source_port": 37708, "destination_ip": "172.17.0.2", "destination_port": 993, "protocol": "imaps", "num_auth_attempts": 0, "auth_attempts": [], "session_ended": true, "auxiliary_data": {}}
{"timestamp": "2019-07-11 04:40:20.502401", "duration": 5, "session_id": "7a5edf3f-5091-42a5-a856-36703d17236b", "source_ip": "172.17.0.3", "source_port": 60038, "destination_ip": "172.17.0.2", "destination_port": 5432, "protocol": "postgresql", "num_auth_attempts": 0, "auth_attempts": [], "session_ended": true, "auxiliary_data": {}}
{"timestamp": "2019-07-11 04:40:21.525372", "duration": 5, "session_id": "cfba09da-c7c4-4b15-82bb-0546569b2e3e", "source_ip": "172.17.0.3", "source_port": 48406, "destination_ip": "172.17.0.2", "destination_port": 995, "protocol": "pop3s", "num_auth_attempts": 0, "auth_attempts": [], "session_ended": true, "auxiliary_data": {}}
{"timestamp": "2019-07-11 04:40:21.527828", "duration": 5, "session_id": "606a71b6-5c61-4b3e-b80d-bb22f09ce864", "source_ip": "172.17.0.3", "source_port": 37714, "destination_ip": "172.17.0.2", "destination_port": 993, "protocol": "imaps", "num_auth_attempts": 0, "auth_attempts": [], "session_ended": true, "auxiliary_data": {}}
{"timestamp": "2019-07-11 04:40:25.504112", "duration": 5, "session_id": "cf9f5f35-f805-40ee-adee-fc18c801231c", "source_ip": "172.17.0.3", "source_port": 60044, "destination_ip": "172.17.0.2", "destination_port": 5432, "protocol": "postgresql", "num_auth_attempts": 0, "auth_attempts": [], "session_ended": true, "auxiliary_data": {}}
{"timestamp": "2019-07-11 04:40:26.528136", "duration": 4, "session_id": "351c6ff8-efed-4e5c-a41a-c466802151df", "source_ip": "172.17.0.3", "source_port": 48412, "destination_ip": "172.17.0.2", "destination_port": 995, "protocol": "pop3s", "num_auth_attempts": 0, "auth_attempts": [], "session_ended": true, "auxiliary_data": {}}
{"timestamp": "2019-07-11 04:40:30.509884", "duration": 5, "session_id": "84bebcaa-f9ff-4d37-b6a0-4b996d557598", "source_ip": "172.17.0.3", "source_port": 60048, "destination_ip": "172.17.0.2", "destination_port": 5432, "protocol": "postgresql", "num_auth_attempts": 0, "auth_attempts": [], "session_ended": true, "auxiliary_data": {}}
{"timestamp": "2019-07-11 04:40:35.513509", "duration": 5, "session_id": "1b5a1916-e18e-42f2-8bb0-894d1d30c2d2", "source_ip": "172.17.0.3", "source_port": 60050, "destination_ip": "172.17.0.2", "destination_port": 5432, "protocol": "postgresql", "num_auth_attempts": 0, "auth_attempts": [], "session_ended": true, "auxiliary_data": {}}
{"timestamp": "2019-07-11 04:40:40.569427", "duration": 0, "session_id": "e367a9f2-b1f2-47f4-a2ea-b2b6899cf74f", "source_ip": "172.17.0.3", "source_port": 53594, "destination_ip": "172.17.0.2", "destination_port": 443, "protocol": "https", "num_auth_attempts": 0, "auth_attempts": [], "session_ended": true, "auxiliary_data": {}}
{"timestamp": "2019-07-11 04:40:40.570958", "duration": 0, "session_id": "a9d0572a-94f5-4cf8-9e03-b43279f4227b", "source_ip": "172.17.0.3", "source_port": 53596, "destination_ip": "172.17.0.2", "destination_port": 443, "protocol": "https", "num_auth_attempts": 0, "auth_attempts": [], "session_ended": true, "auxiliary_data": {}}
{"timestamp": "2019-07-11 04:40:40.564608", "duration": 0, "session_id": "6357260d-2f73-401c-b9e8-f98b8392fdac", "source_ip": "172.17.0.3", "source_port": 47540, "destination_ip": "172.17.0.2", "destination_port": 80, "protocol": "http", "num_auth_attempts": 0, "auth_attempts": [], "session_ended": true, "auxiliary_data": {}}
{"timestamp": "2019-07-11 04:40:40.565180", "duration": 0, "session_id": "9cd29fad-9735-4125-bf6b-aa728419a5bb", "source_ip": "172.17.0.3", "source_port": 47542, "destination_ip": "172.17.0.2", "destination_port": 80, "protocol": "http", "num_auth_attempts": 0, "auth_attempts": [], "session_ended": true, "auxiliary_data": {}}
{"timestamp": "2019-07-11 04:40:40.567050", "duration": 0, "session_id": "df815c4a-0b46-405b-b04b-1f71a5fdea07", "source_ip": "172.17.0.3", "source_port": 47546, "destination_ip": "172.17.0.2", "destination_port": 80, "protocol": "http", "num_auth_attempts": 0, "auth_attempts": [], "session_ended": true, "auxiliary_data": {}}
{"timestamp": "2019-07-11 04:40:40.572885", "duration": 0, "session_id": "1ff4e7d2-f0d3-4682-ba3a-540e414ae9fa", "source_ip": "172.17.0.3", "source_port": 53602, "destination_ip": "172.17.0.2", "destination_port": 443, "protocol": "https", "num_auth_attempts": 0, "auth_attempts": [], "session_ended": true, "auxiliary_data": {}}
{"timestamp": "2019-07-11 04:40:40.584135", "duration": 0, "session_id": "ffcb13b7-16b1-4a9c-80a4-ba0d04f5988b", "source_ip": "172.17.0.3", "source_port": 53606, "destination_ip": "172.17.0.2", "destination_port": 443, "protocol": "https", "num_auth_attempts": 0, "auth_attempts": [], "session_ended": true, "auxiliary_data": {}}
{"timestamp": "2019-07-11 04:40:40.582159", "duration": 0, "session_id": "3fbaf728-6c55-4c18-9c59-c8e879d0c670", "source_ip": "172.17.0.3", "source_port": 47550, "destination_ip": "172.17.0.2", "destination_port": 80, "protocol": "http", "num_auth_attempts": 0, "auth_attempts": [], "session_ended": true, "auxiliary_data": {}}
{"timestamp": "2019-07-11 04:40:40.633480", "duration": 0, "session_id": "fde8b86b-afe1-4f2f-9692-d7fe8b6637d9", "source_ip": "172.17.0.3", "source_port": 47552, "destination_ip": "172.17.0.2", "destination_port": 80, "protocol": "http", "num_auth_attempts": 0, "auth_attempts": [], "session_ended": true, "auxiliary_data": {}}
{"timestamp": "2019-07-11 04:40:47.589571", "duration": 0, "session_id": "e78a0cf6-867d-427c-a25d-4c3f8357cc34", "source_ip": "172.17.0.3", "source_port": 53612, "destination_ip": "172.17.0.2", "destination_port": 443, "protocol": "https", "num_auth_attempts": 0, "auth_attempts": [], "session_ended": true, "auxiliary_data": {}}
{"timestamp": "2019-07-11 04:40:54.598317", "duration": 1, "session_id": "ef89fb5a-d758-4765-bc84-81004b887d36", "source_ip": "172.17.0.3", "source_port": 722, "destination_ip": "172.17.0.2", "destination_port": 143, "protocol": "imap", "num_auth_attempts": 0, "auth_attempts": [], "session_ended": true, "auxiliary_data": {}}
{"timestamp": "2019-07-11 04:40:54.597370", "duration": 1, "session_id": "5301dfdb-6d9d-4c9b-b58b-a075fdb6073c", "source_ip": "172.17.0.3", "source_port": 605, "destination_ip": "172.17.0.2", "destination_port": 110, "protocol": "pop3", "num_auth_attempts": 0, "auth_attempts": [], "session_ended": true, "auxiliary_data": {}}
{"timestamp": "2019-07-11 04:40:54.598889", "duration": 1, "session_id": "20912b15-c096-445e-a7bf-2631a3b4db2e", "source_ip": "172.17.0.3", "source_port": 528, "destination_ip": "172.17.0.2", "destination_port": 5432, "protocol": "postgresql", "num_auth_attempts": 0, "auth_attempts": [], "session_ended": true, "auxiliary_data": {}}
root@8ec2f3a760b8:/opt# cat log_auth.csv
timestamp,auth_id,session_id,source_ip,source_port,destination_ip,destination_port,protocol,username,password
2019-07-11 04:38:20.397103,3a7a6307-ae33-4cd4-8ae0-1a7dede1f21c,e383b4d3-4dc1-42e5-8a53-d17b8ee91f08,172.17.0.3,53366,172.17.0.2,23,telnet,,
2019-07-11 04:45:42.611927,cd7603a3-6531-4162-9463-9446292c1a09,da84bb50-1312-4c7e-b9f8-0c9a204b23ff,172.17.0.3,44376,172.17.0.2,22,ssh,root,f
2019-07-11 04:45:42.612567,511ff040-dd6e-4770-8776-24b52efed8be,da84bb50-1312-4c7e-b9f8-0c9a204b23ff,172.17.0.3,44376,172.17.0.2,22,ssh,root,gfsa
2019-07-11 04:45:42.621929,9b1ff5ea-1729-438f-b9f7-61a7c8e8f45e,02b23467-adc4-4084-9946-ac6131b61823,172.17.0.3,44372,172.17.0.2,22,ssh,root,gdsa
2019-07-11 04:45:42.622303,77757bf4-3e82-47c5-a8d5-357c2b44e32e,dfe5f088-cddf-4642-b810-aaa0f37aea1f,172.17.0.3,44370,172.17.0.2,22,ssh,root,f
2019-07-11 04:45:42.622625,7b0ffc10-3def-42f4-a89d-fa3a7ab3e796,4220f9ef-3a3b-43fc-8b7a-4303cf31530a,172.17.0.3,44378,172.17.0.2,22,ssh,root,sa
2019-07-11 04:45:42.623199,45949bff-7787-4ff5-b2fc-c8215bd47a2c,da84bb50-1312-4c7e-b9f8-0c9a204b23ff,172.17.0.3,44376,172.17.0.2,22,ssh,root,f
2019-07-11 04:45:42.624343,36bd0293-1866-48b4-8e3b-7f8161ed624b,84e907ba-ba60-4e73-a787-0890c203a932,172.17.0.3,44382,172.17.0.2,22,ssh,root,f
2019-07-11 04:45:42.629085,078a591f-36cd-4cc8-a1c3-25c5a6072a83,d029fbdf-1609-4f47-bfb5-066683810968,172.17.0.3,44368,172.17.0.2,22,ssh,root,sa
2019-07-11 04:45:42.629509,32e2d95b-f68e-48df-99ca-12fe7b037f27,aaaf2ed9-4de3-4992-b384-091b275b9286,172.17.0.3,44374,172.17.0.2,22,ssh,root,fsa
2019-07-11 04:45:42.636537,502e85ea-bddf-410c-96a8-2ef83ad20f57,2c9a7b33-46c8-4993-bb86-37308395d480,172.17.0.3,44384,172.17.0.2,22,ssh,root,saf
2019-07-11 04:45:42.637216,b071aef7-0328-40ae-ad98-59516d6ae4ca,7bd4c809-5840-4b42-966e-f89c14b30c18,172.17.0.3,44364,172.17.0.2,22,ssh,root,asdsad
2019-07-11 04:45:42.637905,682b980e-98fa-482e-b75a-4f21d9188b1c,02b23467-adc4-4084-9946-ac6131b61823,172.17.0.3,44372,172.17.0.2,22,ssh,root,
2019-07-11 04:45:42.638511,11f18002-d494-4678-bb0e-6164d0970ca4,dfe5f088-cddf-4642-b810-aaa0f37aea1f,172.17.0.3,44370,172.17.0.2,22,ssh,root,asd
2019-07-11 04:45:42.639108,1eee2a51-5d87-4be3-af4c-9b5bdf1cb16a,d029fbdf-1609-4f47-bfb5-066683810968,172.17.0.3,44368,172.17.0.2,22,ssh,root,asg
2019-07-11 04:45:42.639766,19d87eff-b069-428e-8aa3-0f5701798ea3,789bb53d-701e-4d3c-be99-5a06af8fc9e8,172.17.0.3,44366,172.17.0.2,22,ssh,root,sad
2019-07-11 04:45:42.645056,c535b4d8-e9b0-4e04-911c-8ec7fa7fef03,83674ba2-e320-4992-ac13-d6b9185a75a8,172.17.0.3,44390,172.17.0.2,22,ssh,root,f
2019-07-11 04:45:42.645762,aa4f1390-7c25-4c7b-bdb1-b6f1dce9975d,42685061-fb2e-4d60-a266-a8af2e8fb388,172.17.0.3,44392,172.17.0.2,22,ssh,root,saf
2019-07-11 04:45:42.646597,fd123b12-e778-406a-9635-96b53cee04e5,e87fc3a0-eb60-4bf4-b4d9-055e9d78fd3c,172.17.0.3,44394,172.17.0.2,22,ssh,root,sa总结
难易性★☆☆☆☆
可用性★★★★★
展示性★★★★★
交互性★★★★☆
vnclowpot
低交互VNC蜜罐。侦听端口并记录对静态VNC Auth质询的响应。
查看vnslowpot的用法
root@f99b6302c92a:~/go/bin# ./vnclowpot -h
Usage: ./vnclowpot [options]
Listens for VNC connections, performs the initial handshake either using only
VNC Authentication or offering all auth types (except VNC auth and no auth),
and logs the auth request to stdout. Other logs (errors, etc.) go to stderr.
Options:
-j Print lines suitable for John The Ripper cracking
-l address
Listen address (default "0.0.0.0:5900")
root@f99b6302c92a:~/go/bin#在目录下面有一个test文件夹,使用go编译它之后,就可以用它对密码进行测试。其中第二张图出现这样只因为我用了-j参数,显示出可以进行爆破的彩虹表。不过我有困惑,因为里面还有一个crack的目录下面有个cracker程序,用来破解VNC的密码(彩虹表暴力破解形式),蜜罐是不能直接捕捉明文吗?程序并没有日志保存,只是将信息显示在终端上面。
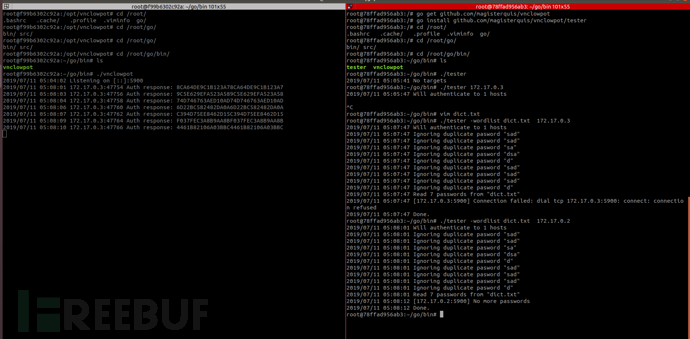

Cowrie
Cowrie是一种中等交互式SSH和Telnet蜜罐,用于记录暴力攻击和攻击者执行的shell交互。
直接运行docker
docker run -p 2222:2222 cowrie/cowrie可以看到右边,随便什么密码都可以成功

使用任意密码进行登录SSH,可以打开某些命令,比如ifconfig,wget。

总结
难易性★☆☆☆☆
可用性★★★★★
展示性★★★★★
交互性★★★★☆
sshlowpot
低交互式ssh蜜罐。接受给定端口上的SSH连接(默认为2222),记录身份验证尝试并告知连接客户端身份验证失败。
运行
docker run -it -p 22:22 wushangleon/sshlowpot
使用hydra进行爆破SSH服务
root@87d3315ba415:/# hydra -l root -P 1.txt 172.17.0.2 ssh
Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2019-07-11 10:00:05
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 18 login tries (l:1/p:18), ~2 tries per task
[DATA] attacking ssh://172.17.0.2:22/
1 of 1 target completed, 0 valid passwords found
Hydra (http://www.thc.org/thc-hydra) finished at 2019-07-11 10:00:06
root@87d3315ba415:/#下面是蜜罐的被爆破的信息
root@cc543bc53951:~/go/bin# ./sshlowpot -a 0.0.0.0:22 -v
2019/07/11 09:59:59.603766 Read SSH key file slp_id_rsa
2019/07/11 09:59:59.604714 Listening on [::]:22
2019/07/11 10:00:05.186104 Address:172.17.0.3:59392 Connect
2019/07/11 10:00:05.225228 Address:172.17.0.3:59392 Disconnect
2019/07/11 10:00:05.445462 Address:172.17.0.3:59394 Connect
2019/07/11 10:00:05.446802 Address:172.17.0.3:59396 Connect
2019/07/11 10:00:05.449805 Address:172.17.0.3:59402 Connect
2019/07/11 10:00:05.451391 Address:172.17.0.3:59408 Connect
2019/07/11 10:00:05.452154 Address:172.17.0.3:59410 Connect
2019/07/11 10:00:05.452812 Address:172.17.0.3:59412 Connect
2019/07/11 10:00:05.453448 Address:172.17.0.3:59398 Connect
2019/07/11 10:00:05.454033 Address:172.17.0.3:59400 Connect
2019/07/11 10:00:05.454677 Address:172.17.0.3:59414 Connect
2019/07/11 10:00:05.455539 Address:172.17.0.3:59404 Connect
2019/07/11 10:00:05.456412 Address:172.17.0.3:59416 Connect
2019/07/11 10:00:05.457362 Address:172.17.0.3:59406 Connect
2019/07/11 10:00:05.458826 Address:172.17.0.3:59418 Connect
2019/07/11 10:00:05.460202 Address:172.17.0.3:59420 Connect
2019/07/11 10:00:05.713906 Address:172.17.0.3:59424 Connect
2019/07/11 10:00:05.867014 Address:172.17.0.3:59422 Connect
2019/07/11 10:00:06.045416 Address:172.17.0.3:59406 Target:cc543bc53951 Version:"SSH-2.0-libssh_0.7.0" User:"root" Password:"sad"
2019/07/11 10:00:06.050529 Address:172.17.0.3:59402 Target:cc543bc53951 Version:"SSH-2.0-libssh_0.7.0" User:"root" Password:"asd"
2019/07/11 10:00:06.051971 Address:172.17.0.3:59400 Target:cc543bc53951 Version:"SSH-2.0-libssh_0.7.0" User:"root" Password:"dsa"
2019/07/11 10:00:06.052534 Address:172.17.0.3:59396 Target:cc543bc53951 Version:"SSH-2.0-libssh_0.7.0" User:"root" Password:"dsa"
2019/07/11 10:00:06.053016 Address:172.17.0.3:59394 Target:cc543bc53951 Version:"SSH-2.0-libssh_0.7.0" User:"root" Password:"asdsad"
2019/07/11 10:00:06.053601 Address:172.17.0.3:59406 Target:cc543bc53951 Version:"SSH-2.0-libssh_0.7.0" User:"root" Password:"sad"
2019/07/11 10:00:06.056040 Address:172.17.0.3:59420 Target:cc543bc53951 Version:"SSH-2.0-libssh_0.7.0" User:"root" Password:"sad"
2019/07/11 10:00:06.056544 Address:172.17.0.3:59398 Target:cc543bc53951 Version:"SSH-2.0-libssh_0.7.0" User:"root" Password:"dsa"
2019/07/11 10:00:06.056619 Address:172.17.0.3:59418 Target:cc543bc53951 Version:"SSH-2.0-libssh_0.7.0" User:"root" Password:"d"
2019/07/11 10:00:06.056656 Address:172.17.0.3:59404 Target:cc543bc53951 Version:"SSH-2.0-libssh_0.7.0" User:"root" Password:"d"
2019/07/11 10:00:06.056692 Address:172.17.0.3:59410 Target:cc543bc53951 Version:"SSH-2.0-libssh_0.7.0" User:"root" Password:"d"
2019/07/11 10:00:06.056721 Address:172.17.0.3:59416 Target:cc543bc53951 Version:"SSH-2.0-libssh_0.7.0" User:"root" Password:"sa"
2019/07/11 10:00:06.056756 Address:172.17.0.3:59412 Target:cc543bc53951 Version:"SSH-2.0-libssh_0.7.0" User:"root" Password:"asdsa"
2019/07/11 10:00:06.060613 Address:172.17.0.3:59396 Disconnect
2019/07/11 10:00:06.061656 Address:172.17.0.3:59394 Target:cc543bc53951 Version:"SSH-2.0-libssh_0.7.0" User:"root" Password:""
2019/07/11 10:00:06.062176 Address:172.17.0.3:59400 Disconnect
2019/07/11 10:00:06.063223 Address:172.17.0.3:59406 Disconnect
2019/07/11 10:00:06.064331 Address:172.17.0.3:59410 Disconnect
2019/07/11 10:00:06.065333 Address:172.17.0.3:59418 Disconnect
2019/07/11 10:00:06.066322 Address:172.17.0.3:59412 Disconnect
2019/07/11 10:00:06.067237 Address:172.17.0.3:59404 Disconnect
2019/07/11 10:00:06.068132 Address:172.17.0.3:59416 Disconnect
2019/07/11 10:00:06.068948 Address:172.17.0.3:59402 Disconnect
2019/07/11 10:00:06.070013 Address:172.17.0.3:59394 Disconnect
2019/07/11 10:00:06.071375 Address:172.17.0.3:59398 Disconnect
2019/07/11 10:00:06.072772 Address:172.17.0.3:59420 Disconnect
2019/07/11 10:00:06.073652 Address:172.17.0.3:59408 Target:cc543bc53951 Version:"SSH-2.0-libssh_0.7.0" User:"root" Password:"dsa"
2019/07/11 10:00:06.074914 Address:172.17.0.3:59408 Disconnect
2019/07/11 10:00:06.076697 Address:172.17.0.3:59414 Target:cc543bc53951 Version:"SSH-2.0-libssh_0.7.0" User:"root" Password:"sa"
2019/07/11 10:00:06.077693 Address:172.17.0.3:59414 Disconnect
2019/07/11 10:00:06.078440 Address:172.17.0.3:59422 Target:cc543bc53951 Version:"SSH-2.0-libssh_0.7.0" User:"root" Password:"sad"
2019/07/11 10:00:06.079349 Address:172.17.0.3:59422 Disconnect
2019/07/11 10:00:06.080845 Address:172.17.0.3:59424 Target:cc543bc53951 Version:"SSH-2.0-libssh_0.7.0" User:"root" Password:"sad"
2019/07/11 10:00:06.081781 Address:172.17.0.3:59424 Disconnect总结
难易性★☆☆☆☆
可用性★★★★★
展示性★★☆☆☆
交互性★☆☆☆☆
sshhipot
高交互性ssh蜜罐
运行
docker run -it wushangleon/sshhipot
查看蜜罐的命令
root@cc543bc53951:~/go/bin# ./sshhipot -h
Usage: ./sshhipot [options]
Options:
-A Allow clients to connect without authentication
-B Don't log connections with no authentication attempts (banners).
-H hostname
Keyboard-Interactive challenge hostname (default "localhost")
-ck key
RSA key to use as a client, which will be created if it does not exist (default "id_rsa")
-cs address
Real server address (default "192.168.0.2:22")
-cu username
Upstream username (default "root")
-d directory
Per-connection log directory (default "conns")
-k key
SSH RSA key, which will be created if it does not exist (default "shp_id_rsa")
-l address
Listen address (default ":2222")
-p password
Allowed password (default "hunter2")
-pf file
Password file with one password per line
-pp probability
Accept any password with this probability (default 0.05)
-sf fingerprint
Real server host key fingerprint
-v version
Server version to present to clients (default "SSH-2.0-OpenSSH_7.2")这个蜜罐的高交互是因为它使用了代理模式,也就是说攻击者攻击蜜罐的时候,蜜罐就会连接真实机,以达到代理捕捉数据的功能。不过由于ssh的配置有问题,导致连接不上,我这边就没有仔细去搞,我估计是证书要配置好就行
172.17.0.2 真实的机器
172.17.0.3 攻击机
172.17.0.4 蜜罐

捕捉到账号和密码信息

总结
难易性★☆☆☆☆
可用性★★★★★
展示性★★☆☆☆
交互性★★★★★
hornet
Hornet旨在成为支持多个虚拟主机的中型交互SSH Honeypot。每个虚拟主机都是独立配置的,并获得自己的沙盒文件系统。Hornet允许跨主机进行交互,这意味着攻击者可以从另一个主机登录(使用ssh命令)。Hornet实例必须包含默认主机,该主机用作启动板以登录其他主机。通过简单的配置更改,可以将任何已配置的主机设置为默认值。
在较高的层次上,Hornet可以根据下图进行可视化工作:
+-------------+
| VirtualHost |
+----------------> | |
| | One |
| +------+------+
| ^
| |
| |
v v
+--------+----+ +------+------+
| Default | | VirtualHost |
Attacker+--------> | | <---------> | |
| VirtualHost | | One |
+--------+----+ +------+------+
^ ^
| |
| |
| v
| +------+------+
| | VirtualHost |
+----------------> | |
| One |
+-------------+运行
docker run -it wushangleon/hornet

被爆破的日志
2019-07-11 11:41:52,491 [INFO] (hornet.core.handler) Connection from ('172.17.0.3', 43812), <socket fileno=9 sock=172.17.0.4:2222 peer=172.17.0.3:43812>
2019-07-11 11:41:52,493 [INFO] (hornet.core.handler) Connection from ('172.17.0.3', 43814), <socket fileno=11 sock=172.17.0.4:2222 peer=172.17.0.3:43814>
2019-07-11 11:41:52,495 [INFO] (hornet.core.handler) Connection from ('172.17.0.3', 43816), <socket fileno=12 sock=172.17.0.4:2222 peer=172.17.0.3:43816>
2019-07-11 11:41:52,497 [INFO] (hornet.core.handler) Connection from ('172.17.0.3', 43818), <socket fileno=17 sock=172.17.0.4:2222 peer=172.17.0.3:43818>
2019-07-11 11:41:52,499 [INFO] (hornet.core.handler) Connection from ('172.17.0.3', 43820), <socket fileno=18 sock=172.17.0.4:2222 peer=172.17.0.3:43820>
2019-07-11 11:41:52,502 [INFO] (hornet.core.handler) Connection from ('172.17.0.3', 43822), <socket fileno=19 sock=172.17.0.4:2222 peer=172.17.0.3:43822>
2019-07-11 11:41:52,506 [INFO] (hornet.core.handler) Connection from ('172.17.0.3', 43824), <socket fileno=20 sock=172.17.0.4:2222 peer=172.17.0.3:43824>
2019-07-11 11:41:52,508 [INFO] (hornet.core.handler) Connection from ('172.17.0.3', 43826), <socket fileno=21 sock=172.17.0.4:2222 peer=172.17.0.3:43826>
2019-07-11 11:41:52,510 [INFO] (hornet.core.handler) Connection from ('172.17.0.3', 43828), <socket fileno=22 sock=172.17.0.4:2222 peer=172.17.0.3:43828>
2019-07-11 11:41:52,512 [INFO] (hornet.core.handler) Connection from ('172.17.0.3', 43830), <socket fileno=23 sock=172.17.0.4:2222 peer=172.17.0.3:43830>
2019-07-11 11:41:52,514 [INFO] (hornet.core.handler) Connection from ('172.17.0.3', 43832), <socket fileno=24 sock=172.17.0.4:2222 peer=172.17.0.3:43832>
2019-07-11 11:41:52,516 [INFO] (hornet.core.handler) Connection from ('172.17.0.3', 43834), <socket fileno=25 sock=172.17.0.4:2222 peer=172.17.0.3:43834>
2019-07-11 11:41:52,518 [DEBUG] (hornet.core.session) Started watching <Session last_activity=1562845312, id=12f61a99-d760-41a7-9cfd-b554d63ef68b, client_address=('172.17.0.3', 43812)>
2019-07-11 11:41:52,519 [DEBUG] (hornet.core.session) Started watching <Session last_activity=1562845312, id=337bb1a6-4314-418d-acc7-b853d74b9600, client_address=('172.17.0.3', 43814)>
2019-07-11 11:41:52,519 [DEBUG] (hornet.core.session) Started watching <Session last_activity=1562845312, id=bee66617-3395-4047-b5a7-858d4e1a8738, client_address=('172.17.0.3', 43816)>
2019-07-11 11:41:52,519 [DEBUG] (hornet.core.session) Started watching <Session last_activity=1562845312, id=1d80d10a-8107-4a00-a93b-a99056d17eb5, client_address=('172.17.0.3', 43818)>
2019-07-11 11:41:52,520 [DEBUG] (hornet.core.session) Started watching <Session last_activity=1562845312, id=5c1a01b0-0cce-4735-9564-5dd979232608, client_address=('172.17.0.3', 43820)>
2019-07-11 11:41:52,520 [DEBUG] (hornet.core.session) Started watching <Session last_activity=1562845312, id=70f1f4d7-5e3b-49ee-b022-c3602135704a, client_address=('172.17.0.3', 43822)>
2019-07-11 11:41:52,521 [DEBUG] (hornet.core.session) Started watching <Session last_activity=1562845312, id=865108ae-576c-4d66-a89c-0cd4eb7649ba, client_address=('172.17.0.3', 43824)>
2019-07-11 11:41:52,521 [DEBUG] (hornet.core.session) Started watching <Session last_activity=1562845312, id=fdfc4c86-4a73-4ae4-ac30-b8002a090b63, client_address=('172.17.0.3', 43826)>
2019-07-11 11:41:52,522 [DEBUG] (hornet.core.session) Started watching <Session last_activity=1562845312, id=51b35866-d58a-4688-a5b6-7571991146fd, client_address=('172.17.0.3', 43828)>
2019-07-11 11:41:52,522 [DEBUG] (hornet.core.session) Started watching <Session last_activity=1562845312, id=b2bdb0ae-62ba-4fd7-a878-73b793ab30bc, client_address=('172.17.0.3', 43830)>
2019-07-11 11:41:52,522 [DEBUG] (hornet.core.session) Started watching <Session last_activity=1562845312, id=1d6dfc7d-9a50-4076-9ad8-31b48165c7ac, client_address=('172.17.0.3', 43832)>
2019-07-11 11:41:52,523 [DEBUG] (hornet.core.session) Started watching <Session last_activity=1562845312, id=a6e71195-2744-4dd4-a106-39ff8550a12c, client_address=('172.17.0.3', 43834)>
2019-07-11 11:41:52,528 [INFO] (root) Login attempt: root@test02 - 3124
2019-07-11 11:41:52,528 [INFO] (root) Login attempt: root@test02 - 12
2019-07-11 11:41:52,531 [INFO] (root) Login attempt: root@test02 - 12
2019-07-11 11:41:52,533 [INFO] (root) Login attempt: root@test02 - 312
2019-07-11 11:41:52,536 [INFO] (root) Login attempt: root@test02 - 312
2019-07-11 11:41:52,539 [INFO] (root) Login attempt: root@test02 - 54
2019-07-11 11:41:52,541 [INFO] (root) Login attempt: root@test02 - 3654
2019-07-11 11:41:52,545 [INFO] (root) Login attempt: root@test02 - 12
2019-07-11 11:41:52,545 [INFO] (root) Login attempt: root@test02 - 342
2019-07-11 11:41:52,545 [INFO] (root) Login attempt: root@test02 - 2346
2019-07-11 11:41:52,546 [INFO] (root) Login attempt: root@test02 - 5
2019-07-11 11:41:52,548 [INFO] (root) Login attempt: root@test02 - sa
2019-07-11 11:41:52,551 [INFO] (root) Login attempt: root@test02 - dsa
2019-07-11 11:41:52,553 [INFO] (root) Login attempt: root@test02 - d
2019-07-11 11:41:52,554 [ERROR] (root) SSH Session db859529-4408-4745-9bda-a68ee95b8e92 ended unexpectedly
2019-07-11 11:41:52,554 [ERROR] (root) SSH Session d2bf3e6d-2330-45bd-a7bc-59027f7552bb ended unexpectedly
2019-07-11 11:41:52,555 [INFO] (root) Login attempt: root@test02 - 3
2019-07-11 11:41:52,556 [INFO] (root) Login attempt: root@test02 - 312
2019-07-11 11:41:52,557 [INFO] (root) Login attempt: root@test02 - 21
2019-07-11 11:41:52,557 [INFO] (root) Login attempt: root@test02 - 4312
2019-07-11 11:41:52,562 [INFO] (root) Login attempt: root@test02 - sadsad
2019-07-11 11:41:52,564 [ERROR] (root) SSH Session 4e55aa0e-107a-4d9c-9e62-9708e3798fff ended unexpectedly
2019-07-11 11:41:52,569 [INFO] (root) Login attempt: root@test02 - dfs
2019-07-11 11:41:52,571 [INFO] (root) Login attempt: root@test02 - g
2019-07-11 11:41:52,574 [ERROR] (root) SSH Session 12f61a99-d760-41a7-9cfd-b554d63ef68b ended unexpectedly
2019-07-11 11:41:52,575 [ERROR] (root) SSH Session 337bb1a6-4314-418d-acc7-b853d74b9600 ended unexpectedly
2019-07-11 11:41:52,585 [INFO] (root) Login attempt: root@test02 - asg
2019-07-11 11:41:52,587 [INFO] (root) Login attempt: root@test02 - 132
2019-07-11 11:41:52,590 [INFO] (root) Login attempt: root@test02 - 54
2019-07-11 11:41:52,591 [ERROR] (root) SSH Session 51b35866-d58a-4688-a5b6-7571991146fd ended unexpectedly
2019-07-11 11:41:52,591 [ERROR] (root) SSH Session b2bdb0ae-62ba-4fd7-a878-73b793ab30bc ended unexpectedly
2019-07-11 11:41:52,592 [ERROR] (root) SSH Session 1d6dfc7d-9a50-4076-9ad8-31b48165c7ac ended unexpectedly
2019-07-11 11:41:52,594 [INFO] (root) Login attempt: root@test02 - 7
2019-07-11 11:41:52,624 [ERROR] (root) SSH Session a6e71195-2744-4dd4-a106-39ff8550a12c ended unexpectedly沙盒文件系统配置
root@50998dee9776:/opt/vfs# ls
config.json vhosts
root@50998dee9776:/opt/vfs# cat config.json
{
"port": 2222,
"host": "0.0.0.0",
"key_file": "test_server.key",
"network": {
"network_ip": "172.17.0.0/24",
"dns_server": "114.114.114.114",
"gateway": "172.17.0.1"
},
"database": "mysql+mysqldb://[email protected]/hornet",
"virtual_hosts": [
{
"hostname": "test01",
"valid_logins": {
"admin": "admin123",
"root": "toor",
"testuser": "passtest"
},
"env": {
"BROWSER": "firefox",
"EDITOR": "gedit",
"SHELL": "/bin/bash",
"PAGER": "less"
},
"ip_address":"172.17.0.100"
}
]
}因为这个蜜罐是中交互的,我想到应该可以设置密码的,蜜罐的IP是172.17.0.2,所以一开始我设置100,ssh密码错误,后来设置为2,还是错误。这就很无解了,那就过了。

总结
难易性★☆☆☆☆
可用性★★★★★
展示性★★☆☆☆
交互性★★★☆☆
ssh-honeypot
伪造 SSHD,记录 IP 地址、用户名与密码
查看蜜罐的命令
root@bf7944a990c4:/ssh-honeypot# bin/ssh-honeypot -h
ssh-honeypot 0.1.0 by Daniel Roberson
usage: bin/ssh-honeypot [-?h -p <port> -a <address> -b <index> -l <file> -r <file> -f <file> -u <user>]
-?/-h -- this help menu
-p <port> -- listen port
-a <address> -- IP address to bind to
-l <file> -- log file
-s -- toggle syslog usage. Default: off
-r <file> -- specify RSA key to use
-f <file> -- specify location to PID file
-b -- list available banners
-b <string> -- specify banner string (max 255 characters)
-i <index> -- specify banner index
-u <user> -- user to setuid() to after bind()
-j <file> -- path to JSON logfile
-J <address> -- server to send JSON logs
-P <port> -- port to send JSON logs使用hydra暴力破解SSH服务,可以捕捉到账号和密码

查看格式普通的日志
root@bf7944a990c4:/ssh-honeypot# cat /opt/log
[Thu Jul 11 12:15:49 2019] ssh-honeypot 0.1.0 by Daniel Roberson started on port 22. PID 360
[Thu Jul 11 12:15:52 2019] Session: SSH-2.0-libssh_0.7.0|SSH-2.0-OpenSSH_5.9p1 Debian-5ubuntu1.4|[email protected]|aes256-ctr|aes256-ctr|hmac-sha2-256|hmac-sha2-256
[Thu Jul 11 12:15:52 2019] Session: SSH-2.0-libssh_0.7.0|SSH-2.0-OpenSSH_5.9p1 Debian-5ubuntu1.4|[email protected]|aes256-ctr|aes256-ctr|hmac-sha2-256|hmac-sha2-256
[Thu Jul 11 12:15:52 2019] Session: SSH-2.0-libssh_0.7.0|SSH-2.0-OpenSSH_5.9p1 Debian-5ubuntu1.4|[email protected]|aes256-ctr|aes256-ctr|hmac-sha2-256|hmac-sha2-256
[Thu Jul 11 12:15:52 2019] 172.17.0.3 root sa
[Thu Jul 11 12:15:52 2019] 172.17.0.3 root 12
[Thu Jul 11 12:15:52 2019] Session: SSH-2.0-libssh_0.7.0|SSH-2.0-OpenSSH_5.9p1 Debian-5ubuntu1.4|[email protected]|aes256-ctr|aes256-ctr|hmac-sha2-256|hmac-sha2-256
[Thu Jul 11 12:15:52 2019] 172.17.0.3 root dsa
[Thu Jul 11 12:15:52 2019] 172.17.0.3 root sadsad
[Thu Jul 11 12:15:52 2019] 172.17.0.3 root 2346
[Thu Jul 11 12:15:52 2019] 172.17.0.3 root 342
[Thu Jul 11 12:15:52 2019] 172.17.0.3 root 5
[Thu Jul 11 12:15:52 2019] 172.17.0.3 root 4312
[Thu Jul 11 12:15:52 2019] 172.17.0.3 root 21
[Thu Jul 11 12:15:52 2019] 172.17.0.3 root 312
[Thu Jul 11 12:15:52 2019] 172.17.0.3 root 3
[Thu Jul 11 12:15:52 2019] 172.17.0.3 root 12
[Thu Jul 11 12:15:52 2019] Session: SSH-2.0-libssh_0.7.0|SSH-2.0-OpenSSH_5.9p1 Debian-5ubuntu1.4|[email protected]|aes256-ctr|aes256-ctr|hmac-sha2-256|hmac-sha2-256
[Thu Jul 11 12:15:52 2019] 172.17.0.3 root 312
[Thu Jul 11 12:15:52 2019] Session: SSH-2.0-libssh_0.7.0|SSH-2.0-OpenSSH_5.9p1 Debian-5ubuntu1.4|[email protected]|aes256-ctr|aes256-ctr|hmac-sha2-256|hmac-sha2-256
[Thu Jul 11 12:15:52 2019] Session: SSH-2.0-libssh_0.7.0|SSH-2.0-OpenSSH_5.9p1 Debian-5ubuntu1.4|[email protected]|aes256-ctr|aes256-ctr|hmac-sha2-256|hmac-sha2-256
[Thu Jul 11 12:15:52 2019] Session: SSH-2.0-libssh_0.7.0|SSH-2.0-OpenSSH_5.9p1 Debian-5ubuntu1.4|[email protected]|aes256-ctr|aes256-ctr|hmac-sha2-256|hmac-sha2-256
[Thu Jul 11 12:15:52 2019] Session: SSH-2.0-libssh_0.7.0|SSH-2.0-OpenSSH_5.9p1 Debian-5ubuntu1.4|[email protected]|aes256-ctr|aes256-ctr|hmac-sha2-256|hmac-sha2-256
[Thu Jul 11 12:15:52 2019] Session: SSH-2.0-libssh_0.7.0|SSH-2.0-OpenSSH_5.9p1 Debian-5ubuntu1.4|[email protected]|aes256-ctr|aes256-ctr|hmac-sha2-256|hmac-sha2-256
[Thu Jul 11 12:15:52 2019] Session: SSH-2.0-libssh_0.7.0|SSH-2.0-OpenSSH_5.9p1 Debian-5ubuntu1.4|[email protected]|aes256-ctr|aes256-ctr|hmac-sha2-256|hmac-sha2-256
[Thu Jul 11 12:15:52 2019] Session: SSH-2.0-libssh_0.7.0|SSH-2.0-OpenSSH_5.9p1 Debian-5ubuntu1.4|[email protected]|aes256-ctr|aes256-ctr|hmac-sha2-256|hmac-sha2-256
[Thu Jul 11 12:15:52 2019] Session: SSH-2.0-libssh_0.7.0|SSH-2.0-OpenSSH_5.9p1 Debian-5ubuntu1.4|[email protected]|aes256-ctr|aes256-ctr|hmac-sha2-256|hmac-sha2-256
[Thu Jul 11 12:15:52 2019] Session: SSH-2.0-libssh_0.7.0|SSH-2.0-OpenSSH_5.9p1 Debian-5ubuntu1.4|[email protected]|aes256-ctr|aes256-ctr|hmac-sha2-256|hmac-sha2-256
[Thu Jul 11 12:15:52 2019] 172.17.0.3 root 3124
[Thu Jul 11 12:15:52 2019] 172.17.0.3 root 12
[Thu Jul 11 12:15:52 2019] 172.17.0.3 root dfs
[Thu Jul 11 12:15:52 2019] 172.17.0.3 root 54
[Thu Jul 11 12:15:52 2019] 172.17.0.3 root g
[Thu Jul 11 12:15:52 2019] 172.17.0.3 root 312
[Thu Jul 11 12:15:52 2019] 172.17.0.3 root d
[Thu Jul 11 12:15:52 2019] 172.17.0.3 root asg
[Thu Jul 11 12:15:52 2019] 172.17.0.3 root 7
[Thu Jul 11 12:15:52 2019] Session: SSH-2.0-libssh_0.7.0|SSH-2.0-OpenSSH_5.9p1 Debian-5ubuntu1.4|[email protected]|aes256-ctr|aes256-ctr|hmac-sha2-256|hmac-sha2-256
[Thu Jul 11 12:15:52 2019] 172.17.0.3 root 3654
[Thu Jul 11 12:15:53 2019] Session: SSH-2.0-libssh_0.7.0|SSH-2.0-OpenSSH_5.9p1 Debian-5ubuntu1.4|[email protected]|aes256-ctr|aes256-ctr|hmac-sha2-256|hmac-sha2-256
[Thu Jul 11 12:15:53 2019] Session: SSH-2.0-libssh_0.7.0|SSH-2.0-OpenSSH_5.9p1 Debian-5ubuntu1.4|[email protected]|aes256-ctr|aes256-ctr|hmac-sha2-256|hmac-sha2-256
[Thu Jul 11 12:15:53 2019] 172.17.0.3 root 54
[Thu Jul 11 12:15:53 2019] 172.17.0.3 root 132查看JSON日志
root@bf7944a990c4:/ssh-honeypot# cat /opt/json
{ "event": "ssh-honeypot-session", "time": 1562847452, "host": "bf7944a990c4", "client": "172.17.0.3", "client_banner": "SSH-2.0-libssh_0.7.0", "server_banner": "SSH-2.0-OpenSSH_5.9p1 Debian-5ubuntu1.4", "kex_algo": "[email protected]", "cipher_in": "aes256-ctr", "cipher_out": "aes256-ctr", "hmac_in": "hmac-sha2-256", "hmac_out": "hmac-sha2-256" }
{ "event": "ssh-honeypot-session", "time": 1562847452, "host": "bf7944a990c4", "client": "172.17.0.3", "client_banner": "SSH-2.0-libssh_0.7.0", "server_banner": "SSH-2.0-OpenSSH_5.9p1 Debian-5ubuntu1.4", "kex_algo": "[email protected]", "cipher_in": "aes256-ctr", "cipher_out": "aes256-ctr", "hmac_in": "hmac-sha2-256", "hmac_out": "hmac-sha2-256" }
{ "event": "ssh-honeypot-session", "time": 1562847452, "host": "bf7944a990c4", "client": "172.17.0.3", "client_banner": "SSH-2.0-libssh_0.7.0", "server_banner": "SSH-2.0-OpenSSH_5.9p1 Debian-5ubuntu1.4", "kex_algo": "[email protected]", "cipher_in": "aes256-ctr", "cipher_out": "aes256-ctr", "hmac_in": "hmac-sha2-256", "hmac_out": "hmac-sha2-256" }
{ "event": "ssh-honeypot-auth", "time": 1562847452, "host": "bf7944a990c4", "client": "172.17.0.3", "user": "root", "pass": "sa" }
{ "event": "ssh-honeypot-auth", "time": 1562847452, "host": "bf7944a990c4", "client": "172.17.0.3", "user": "root", "pass": "12" }
{ "event": "ssh-honeypot-auth", "time": 1562847452, "host": "bf7944a990c4", "client": "172.17.0.3", "user": "root", "pass": "12" }
{ "event": "ssh-honeypot-auth", "time": 1562847452, "host": "bf7944a990c4", "client": "172.17.0.3", "user": "root", "pass": "5" }
{ "event": "ssh-honeypot-auth", "time": 1562847452, "host": "bf7944a990c4", "client": "172.17.0.3", "user": "root", "pass": "2346" }
{ "event": "ssh-honeypot-auth", "time": 1562847452, "host": "bf7944a990c4", "client": "172.17.0.3", "user": "root", "pass": "342" }
{ "event": "ssh-honeypot-auth", "time": 1562847452, "host": "bf7944a990c4", "client": "172.17.0.3", "user": "root", "pass": "12" }
{ "event": "ssh-honeypot-auth", "time": 1562847452, "host": "bf7944a990c4", "client": "172.17.0.3", "user": "root", "pass": "4312" }
{ "event": "ssh-honeypot-auth", "time": 1562847452, "host": "bf7944a990c4", "client": "172.17.0.3", "user": "root", "pass": "21" }
{ "event": "ssh-honeypot-session", "time": 1562847452, "host": "bf7944a990c4", "client": "172.17.0.3", "client_banner": "SSH-2.0-libssh_0.7.0", "server_banner": "SSH-2.0-OpenSSH_5.9p1 Debian-5ubuntu1.4", "kex_algo": "[email protected]", "cipher_in": "aes256-ctr", "cipher_out": "aes256-ctr", "hmac_in": "hmac-sha2-256", "hmac_out": "hmac-sha2-256" }
{ "event": "ssh-honeypot-auth", "time": 1562847452, "host": "bf7944a990c4", "client": "172.17.0.3", "user": "root", "pass": "312" }
{ "event": "ssh-honeypot-auth", "time": 1562847452, "host": "bf7944a990c4", "client": "172.17.0.3", "user": "root", "pass": "3" }
{ "event": "ssh-honeypot-auth", "time": 1562847452, "host": "bf7944a990c4", "client": "172.17.0.3", "user": "root", "pass": "sadsad" }
{ "event": "ssh-honeypot-session", "time": 1562847452, "host": "bf7944a990c4", "client": "172.17.0.3", "client_banner": "SSH-2.0-libssh_0.7.0", "server_banner": "SSH-2.0-OpenSSH_5.9p1 Debian-5ubuntu1.4", "kex_algo": "[email protected]", "cipher_in": "aes256-ctr", "cipher_out": "aes256-ctr", "hmac_in": "hmac-sha2-256", "hmac_out": "hmac-sha2-256" }
{ "event": "ssh-honeypot-session", "time": 1562847452, "host": "bf7944a990c4", "client": "172.17.0.3", "client_banner": "SSH-2.0-libssh_0.7.0", "server_banner": "SSH-2.0-OpenSSH_5.9p1 Debian-5ubuntu1.4", "kex_algo": "[email protected]", "cipher_in": "aes256-ctr", "cipher_out": "aes256-ctr", "hmac_in": "hmac-sha2-256", "hmac_out": "hmac-sha2-256" }
{ "event": "ssh-honeypot-session", "time": 1562847452, "host": "bf7944a990c4", "client": "172.17.0.3", "client_banner": "SSH-2.0-libssh_0.7.0", "server_banner": "SSH-2.0-OpenSSH_5.9p1 Debian-5ubuntu1.4", "kex_algo": "[email protected]", "cipher_in": "aes256-ctr", "cipher_out": "aes256-ctr", "hmac_in": "hmac-sha2-256", "hmac_out": "hmac-sha2-256" }
{ "event": "ssh-honeypot-session", "time": 1562847452, "host": "bf7944a990c4", "client": "172.17.0.3", "client_banner": "SSH-2.0-libssh_0.7.0", "server_banner": "SSH-2.0-OpenSSH_5.9p1 Debian-5ubuntu1.4", "kex_algo": "[email protected]", "cipher_in": "aes256-ctr", "cipher_out": "aes256-ctr", "hmac_in": "hmac-sha2-256", "hmac_out": "hmac-sha2-256" }
{ "event": "ssh-honeypot-session", "time": 1562847452, "host": "bf7944a990c4", "client": "172.17.0.3", "client_banner": "SSH-2.0-libssh_0.7.0", "server_banner": "SSH-2.0-OpenSSH_5.9p1 Debian-5ubuntu1.4", "kex_algo": "[email protected]", "cipher_in": "aes256-ctr", "cipher_out": "aes256-ctr", "hmac_in": "hmac-sha2-256", "hmac_out": "hmac-sha2-256" }
{ "event": "ssh-honeypot-session", "time": 1562847452, "host": "bf7944a990c4", "client": "172.17.0.3", "client_banner": "SSH-2.0-libssh_0.7.0", "server_banner": "SSH-2.0-OpenSSH_5.9p1 Debian-5ubuntu1.4", "kex_algo": "[email protected]", "cipher_in": "aes256-ctr", "cipher_out": "aes256-ctr", "hmac_in": "hmac-sha2-256", "hmac_out": "hmac-sha2-256" }总结
难易性★☆☆☆☆
可用性★★★★★
展示性★★★★☆
交互性★★☆☆☆
ssh-honeypotd
C 编写的低交互 SSH 蜜罐
下面是编译过程
root@1a9927d64975:/ssh-honeypotd# make
cc -c -o main.o main.c
main.c:7:10: fatal error: libssh/server.h: No such file or directory
#include <libssh/server.h>
^~~~~~~~~~~~~~~~~
compilation terminated.
<builtin>: recipe for target 'main.o' failed
make: *** [main.o] Error 1
root@1a9927d64975:/ssh-honeypotd# apt install -y libssh-dev
root@1a9927d64975:/ssh-honeypotd# make
cc -c -o main.o main.c
cc -c -o globals.o globals.c
cc -c -o cmdline.o cmdline.c
cc -c -o pidfile.o pidfile.c
cc -c -o daemon.o daemon.c
cc -c -o worker.o worker.c
cc main.o globals.o cmdline.o pidfile.o daemon.o worker.o -lssh -lssh_threads -pthread -o ssh-honeypotd
root@1a9927d64975:/ssh-honeypotd# ls
LICENSE daemon.c main.c ssh_host_dsa_key.pub.dist worker.c
Makefile daemon.h main.o ssh_host_ecdsa_key.dist worker.h
README.md daemon.o pidfile.c ssh_host_ecdsa_key.pub.dist worker.o
cmdline.c debian pidfile.h ssh_host_ed25519_key.dist
cmdline.h globals.c pidfile.o ssh_host_ed25519_key.pub.dist
cmdline.o globals.h ssh-honeypotd ssh_host_rsa_key.dist
coverity_model.c globals.o ssh_host_dsa_key.dist ssh_host_rsa_key.pub.dist
root@1a9927d64975:/ssh-honeypotd# ./ssh-honeypotd
Error creating PID file /run/ssh-honeypotd/ssh-honeypotd.pid
root@1a9927d64975:/ssh-honeypotd# ./ssh-honeypotd -h
Usage: ssh-honeypotd [options]...
Low-interaction SSH honeypot
Mandatory arguments to long options are mandatory for short options too.
-k, --host-key FILE the file containing the private host key (RSA, DSA, ECDSA, ED25519)
-b, --address ADDRESS the IP address to bind to (default: 0.0.0.0)
-p, --port PORT the port to bind to (default: 22)
-P, --pid FILE the PID file
(default: /run/ssh-honeypotd/ssh-honeypotd.pid)
-n, --name NAME the name of the daemon for syslog
(default: ssh-honeypotd)
-u, --user USER drop privileges and switch to this USER
(default: daemon or nobody)
-g, --group GROUP drop privileges and switch to this GROUP
(default: daemon or nogroup)
-f, --foreground do not daemonize
-h, --help display this help and exit
-v, --version output version information and exit
-k option must be specified at least once.
Please note:
- ECDSA keys are supported if ssh-honeypotd is compiled against libssh 0.6.4+
- ED25519 keys are supported if ssh-honeypotd is compiled against libssh 0.7.0+
ssh-honeypotd was compiled against libssh 0.7.0
libssh used: 0.7.0/openssl/zlib
Please report bugs here: <https://github.com/sjinks/ssh-honeypotd/issues>生成证书
root@1a9927d64975:/ssh-honeypotd# ./ssh-honeypotd -P 1.pid
Error listening to socket: ECDSA, DSA, or RSA host key file must be set
root@1a9927d64975:/ssh-honeypotd# ssh-keygen -t rsa -f ./ssh-honeypot.rsa
Generating public/private rsa key pair.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in ./ssh-honeypot.rsa.
Your public key has been saved in ./ssh-honeypot.rsa.pub.
The key fingerprint is:
SHA256:6nJD3S/ir2rb/v3T/Bu7UR5HLe+u9BQwtrwRmBA5tQo root@1a9927d64975
The key's randomart image is:
+---[RSA 2048]----+
| o+. |
| o. + .|
| E .+ =. o|
| . . o =+ |
| .So + o+|
| ... . oo=|
| .. . ..=+|
| ..+.. .....+*|
| ++*==o...o*B|
+----[SHA256]-----+
root@1a9927d64975:/ssh-honeypotd# ./ssh-honeypotd -P 1.pid
Error listening to socket: ECDSA, DSA, or RSA host key file must be set
root@1a9927d64975:/ssh-honeypotd# ./ssh-honeypotd -P 1.pid -k ./ssh-honeypot.rsa
root@1a9927d64975:/ssh-honeypotd# netstat -ant
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
root@1a9927d64975:/ssh-honeypotd#前台终端显示密码
root@1a9927d64975:/ssh-honeypotd# ./ssh-honeypotd -P 1.pid -k ./ssh-honeypot.rsa -f -n ssh
ssh[131]: Failed password for root from 172.17.0.3 port 46050 ssh2 (target: 172.17.0.2:22, password: 312)
ssh[131]: Failed password for root from 172.17.0.3 port 46050 ssh2 (target: 172.17.0.2:22, password: 12)
ssh[131]: Failed password for root from 172.17.0.3 port 46030 ssh2 (target: 172.17.0.2:22, password: sadsad)
ssh[131]: Failed password for root from 172.17.0.3 port 46060 ssh2 (target: 172.17.0.2:22, password: 132)
ssh[131]: Failed password for root from 172.17.0.3 port 46050 ssh2 (target: 172.17.0.2:22, password: 2346)ssh[131]: Failed password for root from 172.17.0.3 port 46030 ssh2 (target: 172.17.0.2:22, password: 5)
ssh[131]: Failed password for root from 172.17.0.3 port 46030 ssh2 (target: 172.17.0.2:22, password: 12)ssh[131]: Failed password for root from 172.17.0.3 port 46050 ssh2 (target: 172.17.0.2:22, password: 4312)
ssh[131]: Failed password for root from 172.17.0.3 port 46050 ssh2 (target: 172.17.0.2:22, password: 312)ssh[131]: Failed password for root from 172.17.0.3 port 46030 ssh2 (target: 172.17.0.2:22, password: 21)
ssh[131]: Failed password for root from 172.17.0.3 port 46030 ssh2 (target: 172.17.0.2:22, password: 3)
ssh[131]: Failed password for root from 172.17.0.3 port 46060 ssh2 (target: 172.17.0.2:22, password: 342)
ssh[131]: Failed password for root from 172.17.0.3 port 46052 ssh2 (target: 172.17.0.2:22, password: 54)
ssh[131]: Failed password for root from 172.17.0.3 port 46056 ssh2 (target: 172.17.0.2:22, password: 7)
ssh[131]: Failed password for root from 172.17.0.3 port 46034 ssh2 (target: 172.17.0.2:22, password: dsa)
ssh[131]: Failed password for root from 172.17.0.3 port 46048 ssh2 (target: 172.17.0.2:22, password: 312)
ssh[131]: Failed password for root from 172.17.0.3 port 46038 ssh2 (target: 172.17.0.2:22, password: asg)
ssh[131]: Failed password for root from 172.17.0.3 port 46032 ssh2 (target: 172.17.0.2:22, password: sa)
ssh[131]: Failed password for root from 172.17.0.3 port 46054 ssh2 (target: 172.17.0.2:22, password: 3654)
ssh[131]: Failed password for root from 172.17.0.3 port 46036 ssh2 (target: 172.17.0.2:22, password: d)
ssh[131]: Failed password for root from 172.17.0.3 port 46040 ssh2 (target: 172.17.0.2:22, password: dfs)
ssh[131]: Failed password for root from 172.17.0.3 port 46058 ssh2 (target: 172.17.0.2:22, password: 54)
ssh[131]: Failed password for root from 172.17.0.3 port 46044 ssh2 (target: 172.17.0.2:22, password: 3124)
ssh[131]: Failed password for root from 172.17.0.3 port 46042 ssh2 (target: 172.17.0.2:22, password: g)
ssh[131]: Failed password for root from 172.17.0.3 port 46046 ssh2 (target: 172.17.0.2:22, password: 12)查看日志
root@1a9927d64975:/ssh-honeypotd# cat /var/log/auth.log
Jul 11 12:37:19 1a9927d64975 ssh[943]: Failed password for root from 172.17.0.3 port 46096 ssh2 (target: 172.17.0.2:22, password: 312)
Jul 11 12:37:19 1a9927d64975 ssh[943]: Failed password for root from 172.17.0.3 port 46096 ssh2 (target: 172.17.0.2:22, password: 12)
Jul 11 12:37:19 1a9927d64975 ssh[943]: Failed password for root from 172.17.0.3 port 46076 ssh2 (target: 172.17.0.2:22, password: sadsad)
Jul 11 12:37:19 1a9927d64975 ssh[943]: Failed password for root from 172.17.0.3 port 46102 ssh2 (target: 172.17.0.2:22, password: 7)
Jul 11 12:37:19 1a9927d64975 ssh[943]: Failed password for root from 172.17.0.3 port 46076 ssh2 (target: 172.17.0.2:22, password: 5)
Jul 11 12:37:19 1a9927d64975 ssh[943]: Failed password for root from 172.17.0.3 port 46076 ssh2 (target: 172.17.0.2:22, password: 12)
Jul 11 12:37:19 1a9927d64975 ssh[943]: Failed password for root from 172.17.0.3 port 46096 ssh2 (target: 172.17.0.2:22, password: 2346)
Jul 11 12:37:19 1a9927d64975 ssh[943]: Failed password for root from 172.17.0.3 port 46076 ssh2 (target: 172.17.0.2:22, password: 4312)
Jul 11 12:37:19 1a9927d64975 ssh[943]: Failed password for root from 172.17.0.3 port 46096 ssh2 (target: 172.17.0.2:22, password: 21)
Jul 11 12:37:19 1a9927d64975 ssh[943]: Failed password for root from 172.17.0.3 port 46076 ssh2 (target: 172.17.0.2:22, password: 312)
Jul 11 12:37:19 1a9927d64975 ssh[943]: Failed password for root from 172.17.0.3 port 46096 ssh2 (target: 172.17.0.2:22, password: 3)
Jul 11 12:37:19 1a9927d64975 ssh[943]: Failed password for root from 172.17.0.3 port 46102 ssh2 (target: 172.17.0.2:22, password: 342)
Jul 11 12:37:19 1a9927d64975 ssh[943]: Failed password for root from 172.17.0.3 port 46082 ssh2 (target: 172.17.0.2:22, password: d)
Jul 11 12:37:19 1a9927d64975 ssh[943]: Failed password for root from 172.17.0.3 port 46088 ssh2 (target: 172.17.0.2:22, password: g)
Jul 11 12:37:19 1a9927d64975 ssh[943]: Failed password for root from 172.17.0.3 port 46090 ssh2 (target: 172.17.0.2:22, password: 3124)
Jul 11 12:37:19 1a9927d64975 ssh[943]: Failed password for root from 172.17.0.3 port 46098 ssh2 (target: 172.17.0.2:22, password: 54)
Jul 11 12:37:19 1a9927d64975 ssh[943]: Failed password for root from 172.17.0.3 port 46092 ssh2 (target: 172.17.0.2:22, password: 12)
Jul 11 12:37:19 1a9927d64975 ssh[943]: Failed password for root from 172.17.0.3 port 46094 ssh2 (target: 172.17.0.2:22, password: 312)
Jul 11 12:37:19 1a9927d64975 ssh[943]: Failed password for root from 172.17.0.3 port 46080 ssh2 (target: 172.17.0.2:22, password: dsa)
Jul 11 12:37:19 1a9927d64975 ssh[943]: Failed password for root from 172.17.0.3 port 46078 ssh2 (target: 172.17.0.2:22, password: sa)
Jul 11 12:37:19 1a9927d64975 ssh[943]: Failed password for root from 172.17.0.3 port 46086 ssh2 (target: 172.17.0.2:22, password: dfs)
Jul 11 12:37:19 1a9927d64975 ssh[943]: Failed password for root from 172.17.0.3 port 46100 ssh2 (target: 172.17.0.2:22, password: 3654)
Jul 11 12:37:19 1a9927d64975 ssh[943]: Failed password for root from 172.17.0.3 port 46084 ssh2 (target: 172.17.0.2:22, password: asg)
Jul 11 12:37:19 1a9927d64975 ssh[943]: Failed password for root from 172.17.0.3 port 46104 ssh2 (target: 172.17.0.2:22, password: 132)
Jul 11 12:37:19 1a9927d64975 ssh[943]: Failed password for root from 172.17.0.3 port 46106 ssh2 (target: 172.17.0.2:22, password: 54)总结
难易性★☆☆☆☆
可用性★★★★☆
展示性★★★★☆
交互性★★☆☆☆
sshesame
一个假的SSH服务器,允许每个人进入并记录他们的活动
运行
docker run -it wushangleon/sshesame
查看命令
root@d2fca17b9209:~/go/bin# ./sshesame -h
Usage of ./sshesame:
-host_key string
a file containing a private key to use
-json_logging
enable logging in JSON
-listen_address string
the local address to listen on (default "localhost")
-port uint
the port number to listen on (default 2022)
-server_version string
The version identification of the server (RFC 4253 section 4.2 requires that this string start with "SSH-2.0-") (default "SSH-2.0-sshesame")使用hydra爆破,左边显示了暴力破解的信息,不过这玩意并没有日志记录功能。

总结
难易性★☆☆☆☆
可用性★★★☆☆
展示性★☆☆☆☆
交互性★★☆☆☆
sshsyrup
特征
SSH自定义帐户和密码,也允许任何登录
假壳。记录shell会话并上传到asciinema.org(或者,如果您愿意,可以以UML兼容格式登录)
虚拟文件系统,用于浏览和欺骗入侵者
SFTP / SCP支持上传/下载文件
记录客户端密钥指纹
以JSON格式登录以便于解析
将活动推送到ElasticSearch进行分析和存储
当客户端尝试创建端口重定向时记录本地和远程主机
结构允许轻松扩展命令集
运行
docker run -it mkishere/sshsyrup直接ssh连接到172.17.0.2蜜罐上面,只有一些命令可以得到交互,其他命令都是没有的。左边记录了输入的命令字符

总结
难易性★☆☆☆☆
可用性★★★☆☆
展示性★☆☆☆☆
交互性★★☆☆☆
PS:在文章中有一些蜜罐并没有说到,比如是wordpress,工控等,由于功能比较单一,时间久远和麻烦,就没有去写出来。还有后面那些蜜罐,我是在docker内部网络(172.17.0.0)测试的,如果到时需要映射在外网,需要自己设置。最后,求各位大佬关注小弟一波~~~
*本文原创作者:陌度,本文属FreeBuf原创奖励计划,未经许可禁止转载
如有侵权请联系:admin#unsafe.sh