Our mobile acquisition tools, Elcomsoft iOS Forensic Toolkit and Elcomsoft Phone Breaker, support a number of different extraction options. While many of our readers know the differences between logical and physical acquisition in general better than most, there are some things in our software making the logical/physical dilemma somewhat different. In this article, we laid out the differences between the extraction methods as implemented in our tools.
Logical acquisition
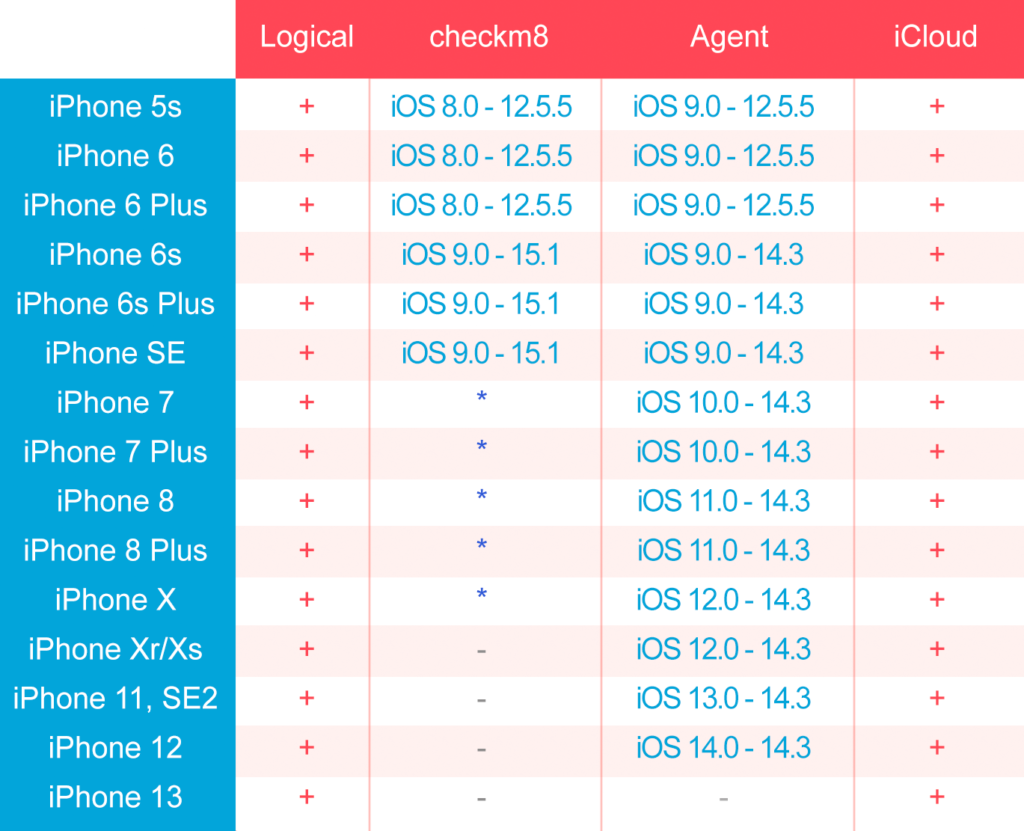
Today, “logical” acquisition becomes “extended logical” or “advanced logical”, as it not only extracts the well-known iTunes-style backup, but also media files (via the afc protocol), which includes photos, videos, music, and downloads, along with their metadata. All that works even if the backup if password protected. In addition, this method helps extract crash and diagnostic logs, which are difficult to parse, yet can really help to build the device usage timeline. Finally, this method can also extract the shared files. While most applications keep their data in their respective sandboxes, some apps allow external access, including even some password managers. Logical is the most universal, compatible, and easy to use acquisition method, but it returns a limited set of data.
Direct checkm8 extraction
This acquisition technique is theoretically available for all models based on the A5 through A11 SoC. The reality is different. The exploit itself is relatively easy to use, but that’s only part of the work. The next stage (extracting the data) is significantly more difficult. If implemented properly, this method is forensically sound and extracts everything down to the last bit, including the keychain. However, there are implementation issues for the A11 models (the iPhone 8/X and some iPads) running iOS 14 and 15: it looks like there is no way to obtain the data until the passcode is removed. Removing the passcode is generally not recommended as it has a lot of negative consequences, not saying that it is not always possible.
Acquisition agent
Elcomsoft’s acquisition agent returns the full set of data (just like with checkm8), but in itself is limited to the systems for which a kernel exploit is available. At this time, we have a full and reliable implementation for iOS 9 through 14.3, and support for some newer version is in the works (up to iOS 14.5.1 at least). Note that this method is not fully forensically sound, but very close to it. Also, it is absolutely safe to the device; the worst you can get is a reboot.
iCloud extraction
After many years, this method is still underestimated, probably due to the legal issues that vary across jurisdictions. Its main benefit is the fact that you do not even need the device itself. On the other hand, you need the user’s iCloud credentials (and a passcode of one of the trusted devices in order to get “end to end encrypted” data). While this method will not grant access to most system databases and application data, but you can get a lot of other data – and from several devices, not just one. Sometimes the historical data is also available, the one that is already deleted from the iPhone with no chance to recover.
Compatibility issues
Currently, only two methods are 100% compatible with all iPhone models and iOS versions: logical and iCloud. The other two (checkm8 and agent) have a large number of compatibility issues with both the hardware and iOS versions.
The above is the current compatibility status of all methods supported by our software; we will of course keep working on all of them, closing the remaining gaps – see below.
Future work
As you can see, our checkm8 implementation does not cover the iPhone 7, iPhone 8 and iPhone X yet. Support for the iPhone 7 is on the way; its SEP is different from the one we already know how to work with, and we need more time to create reliable code for it, keeping it forensically sound. The iPhone 8/X is a bigger headache, especially with iOS 14 and above; not sure if BFU extraction will be ever possible for the last version, but we are doing our best to at least make an extraction of the data partition without the need to remove the passcode.
Agent acquisition also needs improvements. We strive to improve it with every release, doing our best to make it as reliable as theoretically possible, and this is complex: you know, all the exploits we use have their own problems, and success rate (to get root access) depends on many factors. Our main target here is extending iOS version support beyond iOS 14.3, and we have a feeling that 14.4, 14.4.1, 14.4.2, 14.5 and 14.5.1 support will be achieved soon. We usually do not make forward-looking statements, but the work on new versions (up to 15.0.1) is also in progress.
To tell you the truth, iCloud acquisition is also in the works: we are expanding the range of iCloud categories to download (although we already support the wide range, some are still left out). Also, iOS 15 brings some surprises; the encryption basically remains the same, but the data format changed in some categories. And of course, we are making the whole process faster and more reliable.
Conclusion
We are proud to offer one of the most advanced and iOS acquisition solutions on the market. The latest build of Elcomsoft iOS Forensic Toolkit now delivers true forensically sound extraction of select iOS devices, offering repeatable, verifiable results after subsequent extractions. Elcomsoft Phone Breaker delivers best-in-class iCloud extraction, being the only tool on the market to access end-to-end encrypted data.
如有侵权请联系:admin#unsafe.sh