Vendor: Lenovo
Vendor URL: https://www.lenovo.com/
Versions affected: 1.1.20.2
Systems Affected: Windows
Author: [email protected]
Advisory URL: https://support.lenovo.com/us/en/product_security/LEN-75210
CVE Identifier: CVE-2021-3922, CVE-2021-3969
Risk: AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H/E:P/RL:U/RC:R CVSSv3.1: 7.1Summary
The ImController service comes installed on certain Lenovo devices, for example NCC found the service installed on a ThinkPad workstation. The service runs as the SYSTEM user and periodically executes child processes which perform system configuration and maintenance tasks.
Impact
Elevation of privilege. An attacker can elevate their privileges to that of the SYSTEM user from a user that is able to write files to the filesystem.
Details
A vulnerability exists in the way in which the ImControllerService handles the execution of highly privileged child processes which allows an unprivileged attacker with local access to the system to elevate their privileges.
The vulnerable component periodically starts child processes to perform tasks. Each child process immediately opens a named pipe server to which any user on the system can connect. The parent process establishes a connection to the child’s server as soon as possible in order to send XML serialised commands over the named pipe. The child does not validate the source of the connection and parses the XML serialized commands. One of the commands that the parent process can send instructs the child to load a ‘plugin’ from an arbitrary location on the filesystem. The child process validates the digital signature of the plugin DLL file before loading the file into its address space and yielding execution to it.
Successful exploitation of two vulnerabilities required to get the child to load a payload of the attacker’s choosing.
The first vulnerability is a race condition between an attacker and the parent process connecting to the child process’ named pipe. An attacker using high performance filesystem synchronization routines can reliably win the race with the parent process to connect to the named pipe. During testing NCC Group’s proof of concept code never failed to connect to the named pipe before the parent service could do so. Because the child process does not validate the source of the connection it will begin accepting commands from the attacker after the race condition has been exploited.
The following picture displays an instance of the named pipe server in the child process. The pipe is accessible for the EVERYONE group on the system for write access and is always named ‘pipe_’ followed by a random GUID.

The second vulnerability is a time-of-check to time-of-use (TOCTOU) vulnerability. When the child process is sent the command to load a plugin it first validates if the plugin is signed by Lenovo. The vulnerability exists because the child process releases all open handles to the file once the validation has succeeded and before the file is loaded. In order to increase the reliability of this attack, the attacker can use opportunistic locking (OpLocks) on a file that is accessed by the child process between the validation and the load operation. This file access is a by-product of the ImControllerService plugin loading process and is also fully under the attacker’s control. Once the OpLock is placed, the attacker can stall the loading process and replace the now validated plugin with a DLL file of the attacker’s choosing. Once the lock is released the child process loads the DLL, leading to escalation of privilege.
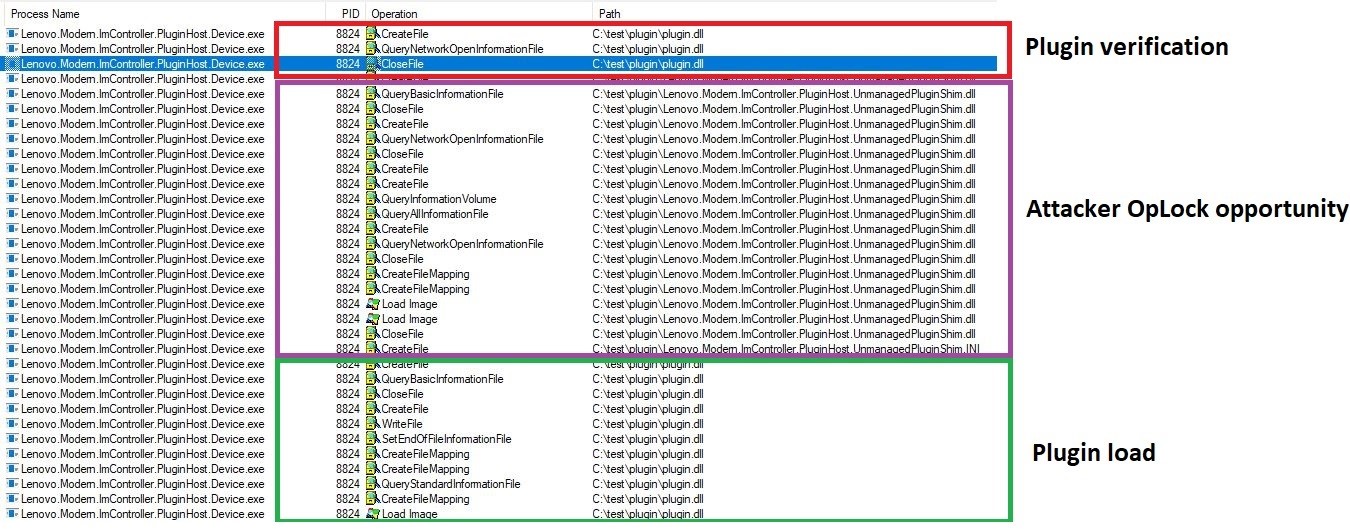
The following screenshot displays the relevant events in the exploitation chain. The events in the red box show the final steps in the verification process and all handles to the DLL being released making the plugin file writable again for the attacker. The events in the purple box show the dependency file being accessed that the attacker can use to stall the load operation using OpLocks. The final box displays events related to the load operation.

The screenshot below shows NCC Group’s proof of concept exploit working against a test installation of the ImControllerService, the steps taken during the exploit and dialog presented by the attacker controlled DLL launched loaded by the child process.

Recommendation
Update the IMController component of Lenovo System Interface Foundation to version 1.1.20.3.
Vendor Communication
Issue reported to Lenovo PSIRT: 29/10/2021
Lenovo confirms the issue: 02/11/2021
Lenovo releases patch: 17/11/2021
Lenovo releases advisory: 14/12/2021
NCC Group releases advisory: 15/12/2021Thanks to
Aaron Haymore, [email protected]
The professional, cordial and responsive security team of Lenovo, who received this report and were able to reproduce, and fix, the issue very quickly.
About NCC Group
NCC Group is a global expert in cybersecurity and risk mitigation, working with businesses to protect their brand, value and reputation against the ever-evolving threat landscape. With our knowledge, experience and global footprint, we are best placed to help businesses identify, assess, mitigate & respond to the risks they face. We are passionate about making the Internet safer and revolutionizing the way in which organizations think about cybersecurity.
Published date: 15-12-2021
Written by: Rick Veldhoven
Published