Mitmproxy implemented with golang. Intercept HTTP & HTTPS requests and responses and modify them.
Features
- Intercept HTTP & HTTPS requests and responses and modify them on the fly
- SSL/TLS certificates for interception are generated on the fly
- Certificates logic compatible with mitmproxy, saved at
~/.mitmproxy. If you used mitmproxy before and installed certificates, then you can use this go-mitmproxy directly - Addon mechanism, you can add your functions easily, refer to addon/addon.go
- Performance advantages
- Golang's inherent performance advantages
- Forwarding and parsing HTTPS traffic in process memory without inter-process communication such as tcp port or unix socket
- Use LRU cache when generating certificates of different domain names to avoid double counting
- Support
Wiresharkto analyze traffic through the environment variableSSLKEYLOGFILE - Support streaming when uploading/downloading large files
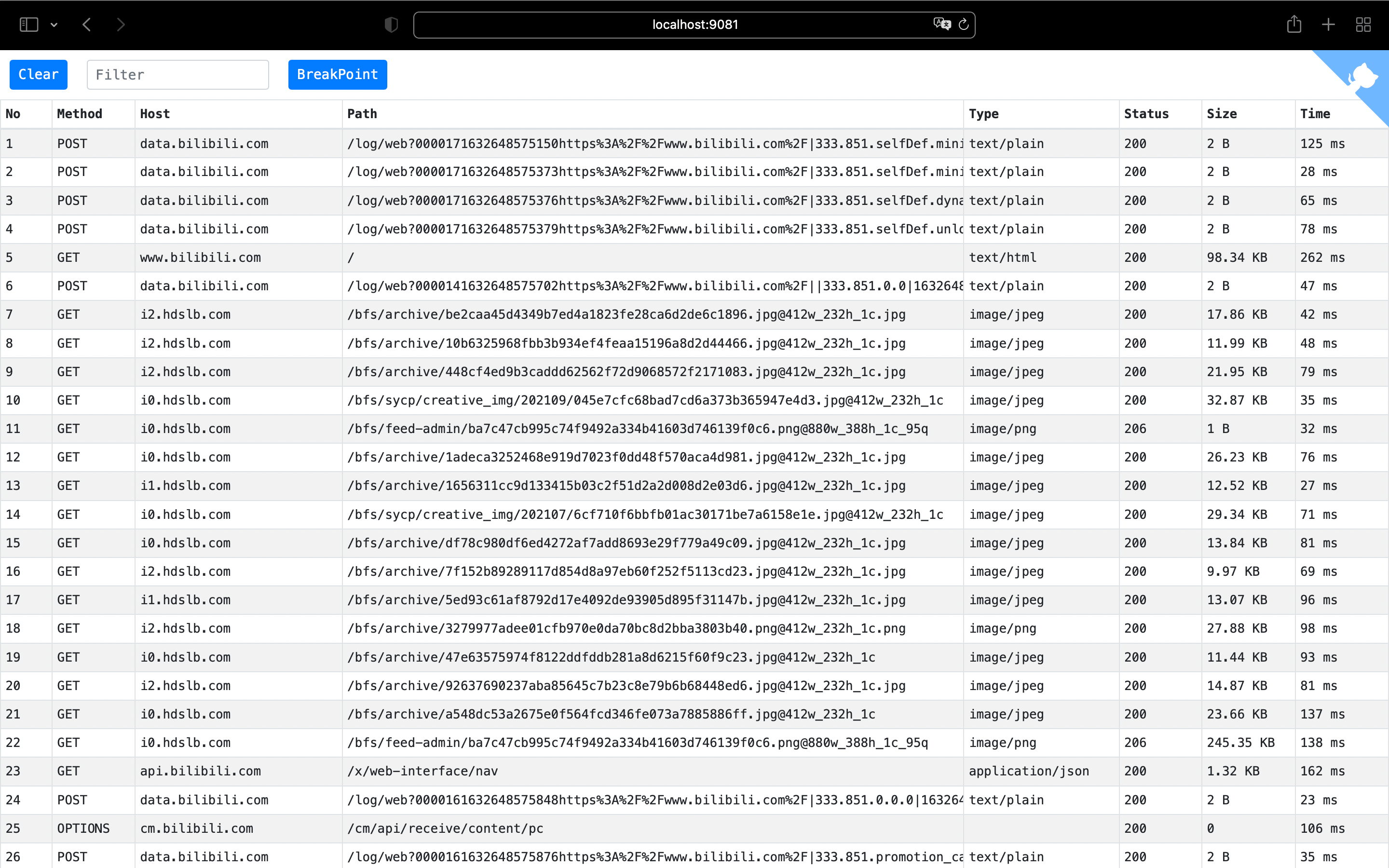
- Web interface
Install
GO111MODULE=on go get -u github.com/lqqyt2423/go-mitmproxy/cmd/go-mitmproxy
Usage
Startup
After startup, the HTTP proxy address defaults to port 9080, and the web interface defaults to port 9081.
After the first startup, the SSL/TLS certificate will be automatically generated at ~/.mitmproxy/mitmproxy-ca-cert.pem. You can refer to this link to install: About Certificates.
Help
Usage of go-mitmproxy:
-addr string
proxy listen addr (default ":9080")
-dump string
dump filename
-dump_level int
dump level: 0 - header, 1 - header + body
-version
show version
-web_addr string
web interface listen addr (default ":9081")
Usage as package
Refer to cmd/go-mitmproxy/main.go, you can add your own addon by call AddAddon method.
For more examples, please refer to examples
Web interface
TODO
- Support http2
- Support parse websocket