2021-12-25 00:0:49 Author: www.sentinelone.com(查看原文) 阅读量:30 收藏
The Good
We have a few nifty victories for law enforcement this week. First off, an individual that heralds from Massachusetts, Flavio Candido da Silva, recently pled guilty to aggravated identity theft and conspiracy to commit wire fraud in a Boston federal court. Da Silva is alleged to be part of a larger team responsible for the theft of identities and the manufacture and distribution of falsified documents. The case relates to charges laid back in May when nineteen individuals were charged with conspiracy to open fraudulent driver accounts at multiple rideshare and delivery companies.

In some cases, identifying information used to feed fake accounts was obtained directly from victims through social engineering. The actors would gain access to victims’ identification documents by posting as an alcohol delivery service or deliberately causing minor vehicle accidents. The fraudulent accounts were used to further spoof income documents for these newly-created fake workers. There is potentially a lengthy jail term tied to this one, which hopefully will serve as a deterrent to those thinking of engaging in cybercrime.
The week would not be complete without mention of Log4j. There have been some important updates around this threat from the wider community, including CISA’s Mitigating Log4Shell and Other Log4j-Related Vulnerabilities, which was updated on December 22nd. Their advisory serves as a launching point for various other Joint Cybersecurity and JCDC advisories. As always, the latest bleeding edge updates will be posted on the SentinelOne blog.
The Bad
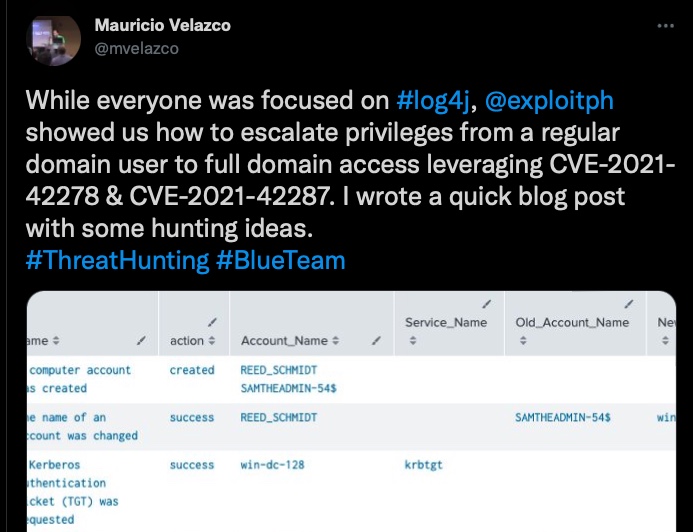
On top of the extra workload IT admins have been dealing with thanks to the ongoing log4j2 vulnerability, this week’s bad news is particularly unwelcome as it involves another “patch the thing we already patched” scenario from Microsoft. This week’s new fire hazard comes courtesy of two Active Directory domain controller bugs. The bugs were addressed last month, but it turns out they can still be exploited by attackers and allow the take over of Windows Domain Controllers.

The two flaws, which have a severity rating of 7.5, are tracked as CVE-2021-42278 and CVE-20210-42287. The new advisory comes in the wake of a publicly available exploit being published back on December 12th.
SAM Name impersonation (CVE-2021-42278) allows attackers to tamper with the SAM-Account-Name attribute used to log users into a system in the AD domain. Meanwhile, KDC Bamboozling (CVE-20210-42287) allows a potential attacker to impersonate a domain controller directly. According to Microsoft:
“Combining the two CVEs, an attacker with domain user credentials can leverage them for granting access as a domain admin user in a few simple steps.”
OK folks, you know the drill. Patch the patch, and ensure you have reliable endpoint protection in place.
The Ugly
As if things aren’t bad enough on the ransomware scene, it gets even uglier when actors find new ways to bypass or disable certain security tools. In that context, we shine a light on AvosLocker, which emerged in June 2021 as a new RaaS (Ransomware as a Service) operator.
In an effort to improve the success rate of encryption, AvosLocker decided to do what any good IT admin would do when encountering a problem on a device: boot it in Safe Mode!
According to researchers, in some cases AvosLocker was forcing victim machines to reboot in Safe Mode with networking, and installing the remote management tool AnyDesk. This allows the attackers to control the target machines remotely while security tools that don’t run in Safe Mode are inactive.
The attackers were also seen running a tool called PDQ Deploy to push customized batch scripts out to target devices to assist in disabling a number of endpoint security solutions before rebooting into Safe Mode. Once booted, the victim machines run the ransomware payload and files are encrypted.
Endpoint security tools affected by the technique, the researchers say, include:
- Windows Defender
- Carbon Black
- Bitdefender
- Trend Micro
- Kaspersky
- Symantec
- Cylance
AvosLocker does not succeed on devices protected by SentinelOne.
This serves as a good reminder that all these ransomware actors are constantly at work, even when not being highlighted in the news. For additional information on ransomware and potential solutions, start here.
如有侵权请联系:admin#unsafe.sh