看雪论坛作者ID:neilwu
一
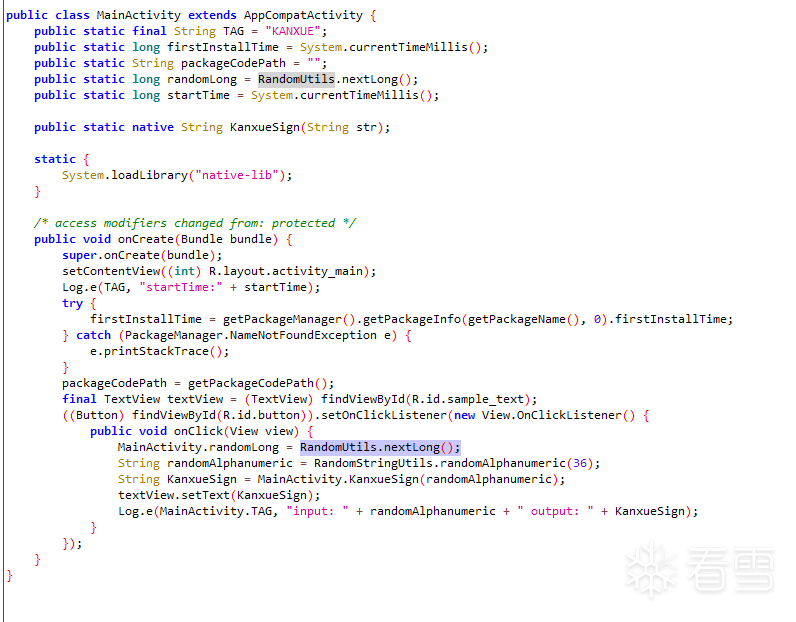
题目
二
逆向过程
1、java层
2021-11-30 14:29:23.634 17199-17199/? E/KANXUE:input: jPCAeDizNJqxh52TNFcabKlmX8KmxKws0NjFoutput: 9c4d974eef6e8cba9dd8b260d19704a2f91e54fac3a9a3039e961b960d5bfa420207014700be00a800be020700be011c011c0207010501c1009e00ca019000be016b0239014b008200ca01c10071007102b6009e00bd016b0147019000bd01b801b802c701dd029701a200d401a2019c00bd020600a501e2009302490072012d01e00071007202a202b1023a02a200c902000200020701a900be02a2008200ca00be011c0190ahrybxzva3vxa6aLbQeMak4Mb38Kbe==
2、native层
(1)JNI_ONLoad
public static native String KanxueSign(String str)对应sub_12AE4
(2)init_array
对datadiv_decode64400029844576484运行时解密。
.....xmmword_5CB20 0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF7d48b22b20 4b 61 6e 78 75 65 53 69 67 6e 20 65 72 72 6f 72 KanxueSign error7d48b22b30 21 00 00 00 00 00 00 00 4b 61 6e 78 75 65 53 69 !.......KanxueSi7d48b22b40 67 6e 00 00 00 00 00 00 00 00 00 00 00 00 00 00 gn..............stru_5CA60 0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF7d48b22a60 63 6f 6d 2f 6b 61 6e 78 75 65 2f 6f 6c 6c 76 6d com/kanxue/ollvm7d48b22a70 5f 6e 64 6b 2f 4d 61 69 6e 41 63 74 69 76 69 74 _ndk/MainActivit7d48b22a80 79 00 00 00 00 00 00 00 73 74 61 72 74 54 69 6d y.......startTim7d48b22a90 65 00 00 00 4a 00 00 00 00 00 00 00 00 00 00 00 e...J...........qword_5CA88 0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF7d48b22a88 73 74 61 72 74 54 69 6d 65 00 00 00 4a 00 00 00 startTime...J...7d48b22a98 00 00 00 00 00 00 00 00 66 69 72 73 74 49 6e 73 ........firstIns7d48b22aa8 74 61 6c 6c 54 69 6d 65 00 00 00 00 00 00 00 00 tallTime........7d48b22ab8 00 00 00 00 00 00 00 00 70 61 63 6b 61 67 65 43 ........packageC7d48b22ac8 6f 64 65 50 61 74 68 00 4c 6a 61 76 61 2f 6c 61 odePath.Ljava/la7d48b22ad8 6e 67 2f 53 74 72 69 6e 67 3b 00 00 00 00 00 00 ng/String;......7d48b22ae8 72 61 6e 64 6f 6d 4c 6f 6e 67 00 00 00 00 00 00 randomLong......7d48b22af8 25 30 38 6c 78 25 30 38 6c 78 00 00 25 30 32 78 %08lx%08lx..%02x7d48b22b08 00 00 00 00 25 30 34 78 00 00 00 00 00 00 00 00 ....%04x.............
(3)sub_12AE4
通过frida对函数进行分析,可以将output分为3部分进行处理:
output 9c4d974eef6e8cba9dd8b260d19704a2f91e54fac3a9a3039e961b960d5bfa420207014700be00a800be020700be011c011c0207010501c1009e00ca019000be016b0239014b008200ca01c10071007102b6009e00bd016b0147019000bd01b801b802c701dd029701a200d401a2019c00bd020600a501e2009302490072012d01e00071007202a202b1023a02a200c902000200020701a900be02a2008200ca00be011c0190ahrybxzva3vxa6aLbQeMak4Mb38Kbe==
第一部分:
9c4d974eef6e8cba9dd8b260d19704a2f91e54fac3a9a3039e961b960d5bfa42sub_1A9D0(v48, s, v11);sub_1B2DC(&v49, v27);sub_1D1E8sub_1AFC4(v48, v47);sub_17F9C(v30, v31, v29[0]);
public static long firstInstallTime = System.currentTimeMillis();firstInstallTime = getPackageManager().getPackageInfo(getPackageName(), 0).firstInstallTime;public static long startTime = System.currentTimeMillis();
7d50734e50 31 37 64 36 39 61 30 38 63 30 63 31 37 64 32 31 17d69a08c0c17d217d50734e60 61 32 34 32 30 35 00 00 00 00 00 00 00 00 00 00 a24205..........
7d50734b10 6d 6b 38 6a 65 3d 6c 64 3f 6c 3f 6d 6b 38 6e 6d mk8je=ld?l?mk8nm7d50734b20 3d 6e 68 6e 6c 69 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c =nhnli\\\\\\\\\\7d50734b30 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c \\\\\\\\\\\\\\\\7d50734b40 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c \\\\\\\\\\\\\\\\
addr_1B2DC onEnter args0 0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF7d50734d80 67 e6 09 6a 85 ae 67 bb 72 f3 6e 3c 3a f5 4f a5 g..j..g.r.n<:.O. // 疑似sha2567d50734d90 7f 52 0e 51 8c 68 05 9b ab d9 83 1f 19 cd e0 5b .R.Q.h.........[addr_1B2DC onEnter args1 0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF7d50734b10 6d 6b 38 6a 65 3d 6c 64 3f 6c 3f 6d 6b 38 6e 6d mk8je=ld?l?mk8nm7d50734b20 3d 6e 68 6e 6c 69 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c =nhnli\\\\\\\\\\7d50734b30 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c \\\\\\\\\\\\\\\\7d50734b40 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c \\\\\\\\\\\\\\\\addr_1B2DC onEnter args2 0x40
0x6a09e667, 0xbb67ae85, 0x3c6ef372, 0x737f4c85b0,0x510e527f, 0x9b05688c, 0x1f83d9ab, 0x737f4c8570
还原函数如下:
int *__fastcall sub_1D1E8(int *result, _DWORD *a2, __int64 a3){//函数过大,放附件了;}
__int64 __fastcall sub_26300(unsigned int a1, int a2, unsigned int a3, _DWORD *a4, unsigned int a5, int a6, int a7, _DWORD *a8, int a9){unsigned __int64 v9; // t2int v10; // w22int v11; // w5unsigned __int64 v12; // kr00_8int v13; // w8int v14; // w14int v15; // w15__int64 result; // x0int v17; // [xsp+14h] [xbp-3Ch]HIDWORD(v9) = a5;LODWORD(v9) = a5;v10 = ~((a6 ^ a7) & a5);v11 = (v9 >> 25) ^ (a5 << 21) ^ ((unsigned __int64)a5 >> 11);HIDWORD(v9) = a1;LODWORD(v9) = a1;v12 = (unsigned __int64)a1 << 10;v17 = ((a1 >> 2) | (a1 << 30)) ^ (v9 >> 13);v13 = *a8 + ~(a7 ^ v10) + (((a5 << 26) | ((unsigned __int64)a5 >> 6)) ^ v11) + a9;v14 = a2 | a1;v15 = a2 & a1;result = (a2 | a1) ^ a3;*a4 += v13;*a8 = ((v12 | HIDWORD(v12)) ^ v17) + v13 + (v15 | v14 & a3);return result;}
7d50734d80 67 e6 09 6a 85 ae 67 bb 72 f3 6e 3c 3a f5 4f a5 g..j..g.r.n<:.O.7d50734d90 7f 52 0e 51 8c 68 05 9b ab d9 83 1f 19 cd e0 5b .R.Q.h.........[7d50734b10 6d 6b 38 6a 65 3d 6c 64 3f 6c 3f 6d 6b 38 6e 6d mk8je=ld?l?mk8nm7d50734b20 3d 6e 68 6e 6c 69 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c =nhnli\\\\\\\\\\7d50734b30 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c \\\\\\\\\\\\\\\\7d50734b40 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c 5c \\\\\\\\\\\\\\\\经过函数sub_1D1E8((int *)result,key,0x1) 处理得到7d50734d80 87 2e 2b 58 48 6f fc 78 7c db f9 b2 8d b3 87 55 ..+XHo.x|......U7d50734d90 ce 0f 70 74 fc 59 39 3c 50 48 f5 f1 64 28 60 bd ..pt.Y9<PH..d(`.
7d50734de8 67 e6 09 6a 85 ae 67 bb 72 f3 6e 3c 3a f5 4f a5 g..j..g.r.n<:.O.7d50734df8 7f 52 0e 51 8c 68 05 9b ab d9 83 1f 19 cd e0 5b .R.Q.h.........[7d50734b10 07 01 52 00 0f 57 06 0e 55 06 55 07 01 52 04 07 ..R..W..U.U..R..7d50734b20 57 04 02 04 06 03 36 36 36 36 36 36 36 36 36 36 W.....66666666667d50734b30 36 36 36 36 36 36 36 36 36 36 36 36 36 36 36 36 66666666666666667d50734b40 36 36 36 36 36 36 36 36 36 36 36 36 36 36 36 36 6666666666666666经过函数sub_1D1E8((int *)result,key,0x1) 处理得到7d50734de8 f4 78 93 8b 63 04 c3 95 86 19 0c 03 0b c4 3c ab .x..c.........<.7d50734df8 7a ab c0 f7 39 bd 67 b5 8e 7a 1b ca 13 7e cb d5 z...9.g..z...~..
7d50734de8 f4 78 93 8b 63 04 c3 95 86 19 0c 03 0b c4 3c ab .x..c.........<.7d50734df8 7a ab c0 f7 39 bd 67 b5 8e 7a 1b ca 13 7e cb d5 z...9.g..z...~..7da963b000 2f 64 61 74 61 2f 61 70 70 2f 63 6f 6d 2e 6b 61 /data/app/com.ka7da963b010 6e 78 75 65 2e 6f 6c 6c 76 6d 5f 6e 64 6b 5f 31 nxue.ollvm_ndk_17da963b020 31 2d 55 41 47 54 47 4f 5f 30 5a 4c 35 52 53 33 1-UAGTGO_0ZL5RS37da963b030 66 6c 53 73 50 48 73 77 3d 3d 2f 62 61 73 65 2e flSsPHsw==/base.经过函数sub_1D1E8((int *)result,key,0x1) 处理得到7d50734de8 52 dc d8 f0 11 63 f2 5d 61 5b 0d 5b 97 fb bd 58 R....c.]a[.[...X7d50734df8 d8 e6 36 0c 44 6c 2f 87 e9 29 47 e0 bf 4f 55 b6 ..6.Dl/..)G..OU.
7d50734de8 52 dc d8 f0 11 63 f2 5d 61 5b 0d 5b 97 fb bd 58 R....c.]a[.[...X7d50734df8 d8 e6 36 0c 44 6c 2f 87 e9 29 47 e0 bf 4f 55 b6 ..6.Dl/..)G..OU.7d50734e08 61 70 6b 80 00 00 00 00 00 00 00 00 00 00 00 00 apk.............7d50734e18 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................7d50734e28 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................7d50734e38 00 00 00 00 00 00 00 00 00 00 00 00 00 00 04 18 ................经过函数sub_1D1E8((int *)result,key,0x1) 处理得到7d50734de8 fe 93 4b f7 f7 31 2d 96 cd 30 30 a7 be a3 b2 b3 ..K..1-..00.....7d50734df8 e2 78 21 59 b2 89 a7 0b f0 bf e9 4e 47 f9 9f c1 .x!Y.......NG...
7d50734de8 fe 93 4b f7 f7 31 2d 96 cd 30 30 a7 be a3 b2 b3 ..K..1-..00.....7d50734df8 e2 78 21 59 b2 89 a7 0b f0 bf e9 4e 47 f9 9f c1 .x!Y.......NG...转换7d50734da0 f7 4b 93 fe 96 2d 31 f7 a7 30 30 cd b3 b2 a3 be .K...-1..00.....7d50734db0 59 21 78 e2 0b a7 89 b2 4e e9 bf f0 c1 9f f9 47 Y!x.....N......G
7d50734d80 87 2e 2b 58 48 6f fc 78 7c db f9 b2 8d b3 87 55 ..+XHo.x|......U7d50734d90 ce 0f 70 74 fc 59 39 3c 50 48 f5 f1 64 28 60 bd ..pt.Y9<PH..d(`.7d50734da0 f7 4b 93 fe 96 2d 31 f7 a7 30 30 cd b3 b2 a3 be .K...-1..00.....7d50734db0 59 21 78 e2 0b a7 89 b2 4e e9 bf f0 c1 9f f9 47 Y!x.....N......G7d50734dc0 80 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................7d50734dd0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 03 00 ................经过函数sub_1D1E8((int *)result,key,0x1) 处理得到7d50734d80 4e 97 4d 9c ba 8c 6e ef 60 b2 d8 9d a2 04 97 d1 N.M...n.`.......7d50734d90 fa 54 1e f9 03 a3 a9 c3 96 1b 96 9e 42 fa 5b 0d .T..........B.[.
__int64 __fastcall sub_1B89C(_DWORD *a1, int *a2){__int64 v3; // x0unsigned int v4; // w0unsigned int v5; // w30unsigned int v6; // w20int v7; // w17__int64 result; // x0_DWORD *v9; // [xsp+10h] [xbp-A0h]_QWORD src[2]; // [xsp+50h] [xbp-60h] BYREF//v9 = sub_1B2DC(v3, src, 8LL);v9 = a1;*a2 = (*v9 >> 8) & 0xFF00 | HIBYTE(*v9) | (*v9 << 24) | (*v9 << 8) & 0xFF00FF;a2[1] = HIBYTE(v9[1]) | (v9[1] >> 8) & 0xFF00 | (v9[1] << 24) | (v9[1] << 8) & 0xFF0000;a2[2] = (v9[2] >> 8) & 0xFF00 | HIBYTE(v9[2]) | (v9[2] << 24) | (v9[2] << 8) & 0xFF0000;a2[3] = (v9[3] >> 8) & 0xFF00 | (v9[3] >> 24) | (v9[3] << 24) | (v9[3] << 8) & 0xFF0000;a2[4] = (v9[4] >> 8) & 0xFF00 | HIBYTE(v9[4]) | (v9[4] << 24) | (v9[4] << 8) & 0xFF00FF;a2[5] = (v9[5] >> 8) & 0xFF00 | HIBYTE(v9[5]) | (v9[5] << 24) | (v9[5] << 8) & 0xFF00FF;a2[6] = (v9[6] >> 8) & 0xFF00 | HIBYTE(v9[6]) | (v9[6] << 24) | (v9[6] << 8) & 0xFF0000;v4 = v9[7];v5 = v4 & 0xFF0000;v6 = HIBYTE(v4);v7 = v4 << 24;result = (v4 << 8) & 0xFF0000;a2[7] = (v5 >> 8) | v6 | v7 | result;return result;}
int cipher[8];_DWORD result1[] = {0x4e974d9c, 0xba8c6eef, 0x60b2d89d, 0xa20497d1, 0xfa541ef9, 0x03a3a9c3, 0x961b969e, 0x42fa5b0d};sub_1B89C(result1, cipher);
第二部分:
0207014700be00a800be020700be011c011c0207010501c1009e00ca019000be016b0239014b008200ca01c10071007102b6009e00bd016b0147019000bd01b801b802c701dd029701a200d401a2019c00bd020600a501e2009302490072012d01e00071007202a202b1023a02a200c902000200020701a900be02a2008200ca00be011c0190
算法分析
public static long randomLong = RandomUtils.nextLong();_DWORD dword_5C008[] = {0x16A, 0x151, 0xD7, 0x134, 0x196, 0x229, 0x67, 0xFA,0x269, 0x272, 0x226, 0x122, 0xEC, 0x2B5, 0x216, 0x214,0x179, 0x9F, 0x277, 0x194, 0xF4, 0x2AD, 0xA0, 0x210,0x26D, 0x1B9, 0x257, 0x2C9, 0xE9, 0xA1, 0x16C, 0x15F,0x99, 0x2E1, 0xBF, 0x1C6, 0xB4, 0x21D, 0xDE, 0x16D,0xC4, 0x8B, 0x25D, 0x108, 0x11B, 0x12C, 0x14A, 0xC3,0x195, 0x2C7, 0xCA, 0x207, 0x206, 0x1B8, 0x1A0, 0x12D,0xCE, 0x93, 0x2DF, 0x205, 0xAA, 0x28B, 0x9B, 0x1DF,0x288, 0x200, 0x86, 0x169, 0x211, 0x297, 0x2D6, 0x135,0x223, 0xA9, 0x208, 0x1A2, 0x23A, 0x294, 0x1AD, 0x1CA,0x1E2, 0x102, 0xA7, 0x19C, 0x2B1, 0x1D1, 0x249, 0x72,0xD4, 0x1DD, 0x173, 0xB5, 0x17A, 0xE1, 0xA5, 0x10B,0x2D9, 0x281, 0x12B, 0xBD, 0x111, 0xBE, 0x1A9, 0x105,0x147, 0x82, 0x1E0, 0x1A3, 0x156, 0x23E, 0x22A, 0x190,0x71, 0x9E, 0x16B, 0x1C1, 0x11C, 0x204, 0x2E2, 0x2A2,0xA8, 0x14B, 0x2B6, 0xC9, 0x239, 0x116, 0x2A7, 0xD1,0x273, 0x6C, 0x21C, 0xE2, 0xEB, 0x2D0, 0x1DB, 0x6B,0x232, 0xEF, 0x85, 0x13F, 0xF5, 0x9D, 0xF8, 0x267,0x1F2, 0x75, 0x246, 0x1D8, 0x13B, 0x2D7, 0x2AC, 0xD5,0x187, 0x29C, 0x176, 0x131, 0x28D, 0x91, 0xB6, 0x114,0x2D8, 0x275, 0x11A, 0x26C, 0x110, 0x2AA, 0x1C3, 0x19F,0x1A8, 0x279, 0x2DE, 0x15D, 0x2DB, 0x6A, 0x230, 0x68,0x178, 0x2BD, 0x217, 0x146, 0x186, 0x1E6, 0x1B1, 0x143,0x2E3, 0x2AF, 0x8E, 0x1D0, 0xAC, 0x1DE, 0x260, 0x81,0x193, 0x266, 0x231, 0x1D2, 0xBA, 0x240, 0x18E, 0x7E,0xC1, 0x1F1, 0x1FE, 0x2A3, 0x250, 0x13A, 0x24A, 0x64,0x29A, 0x24B, 0x2CA, 0x188, 0xFD, 0x103, 0x100, 0x1D9,0x9A, 0x1F3, 0x182, 0x7D, 0xDA, 0xDF, 0x11F, 0x27E,0x1B4, 0x215, 0x8F, 0x263, 0x192, 0x150, 0x17D, 0x2A4,0x154, 0x23B, 0x14F, 0x12F, 0x29F, 0x2BA, 0x237, 0x2BC,0x126, 0x1FD, 0x168, 0x2C5, 0x254, 0x2E0, 0x1C9, 0x201,0x172, 0x140, 0x138, 0xE0, 0xB1, 0xBB, 0x2DD, 0x19E,0x1E7, 0x160, 0x13E, 0x7A, 0x1CB, 0x28C, 0x7F, 0xF9,0x14E, 0x2B8, 0x101, 0x1EA, 0x1D7, 0x1F7, 0x276, 0x1C2,0x8A, 0x2CF, 0x238, 0xDC, 0x2AE, 0x94, 0x157, 0x175,0x21F, 0x2C2, 0xAB, 0x130, 0x104, 0xFB, 0x24D, 0x222,0x221, 0x18C, 0x1FA, 0x1FC, 0x1B5, 0x87, 0x2BE, 0x1AF,0x1B7, 0xC2, 0x22B, 0x10A, 0x19B, 0x121, 0x198, 0x148,0x1F6, 0x280, 0x132, 0x17B, 0x1BB, 0xCD, 0x20E, 0x2BB,0xB7, 0x1CC, 0x244, 0x2A6, 0x264, 0x1EF, 0x251, 0x76,0x171, 0x2DC, 0x236, 0x25F, 0x159, 0x1A4, 0x1F4, 0x118,0x17E, 0x106, 0x115, 0x262, 0x1A6, 0x185, 0x1F5, 0x29B,0x29E, 0x13D, 0x9C, 0x224, 0xC5, 0x219, 0x25C, 0x149,0x88, 0x137, 0x2A9, 0xB2, 0x139, 0x24E, 0x183, 0x235,0x1FB, 0x15B, 0xC7, 0x1C5, 0xD9, 0x26B, 0x7B, 0x1E4,0xF7, 0x2C6, 0x22F, 0x16F, 0x2D2, 0xFC, 0x177, 0x1CD,0x241, 0x2CE, 0x1BE, 0x1BC, 0x7C, 0x1E3, 0x258, 0x2B0,0xAE, 0x125, 0xA6, 0x2D1, 0x1B6, 0xCF, 0x278, 0x18D,0x155, 0x1AB, 0x1F8, 0x270, 0x1D5, 0x2C1, 0x1B0, 0x27F,0x74, 0x1AE, 0xE7, 0x2A5, 0xD0, 0x98, 0x141, 0x289,0x1F0, 0x1AA, 0x1BF, 0x2CD, 0x1C8, 0x2B7, 0x296, 0x299,0x6F, 0x17C, 0xD8, 0x77, 0x124, 0xE8, 0x18F, 0x26E,0x2BF, 0x1DC, 0x21A, 0x209, 0x20A, 0x18A, 0x274, 0x1AC,0x28A, 0x109, 0x1EE, 0x73, 0x2B3, 0x136, 0x234, 0x1DA,0x10D, 0x27A, 0x2D4, 0x22E, 0x2C4, 0x83, 0x261, 0x18B,0x20F, 0x167, 0x1E5, 0x1F9, 0x252, 0x1E8, 0x89, 0x25E,0x23C, 0x129, 0xB3, 0xBC, 0x284, 0x112, 0x11D, 0x22D,0x2D3, 0x15C, 0x10F, 0xD2, 0xF2, 0x15E, 0x298, 0x28E,0x2CC, 0xEA, 0x120, 0x145, 0xF3, 0x202, 0x197, 0x181,0x2C3, 0x170, 0x1A7, 0x78, 0xE6, 0xC0, 0xF1, 0x1FF,0x295, 0x213, 0xC8, 0x164, 0x22C, 0x10C, 0x1D4, 0xCB,0x165, 0x1EC, 0xCC, 0x282, 0x1BD, 0xB0, 0x24F, 0x80,0xA2, 0x29D, 0x2D5, 0x14D, 0xE4, 0x16E, 0x158, 0x152,0xC6, 0x6D, 0xD3, 0x212, 0x184, 0x153, 0x180, 0x66,0x228, 0x220, 0x259, 0x2AB, 0x70, 0x27D, 0x2B9, 0x291,0xED, 0xAF, 0x127, 0x255, 0x123, 0x90, 0x293, 0xF0,0x271, 0x247, 0x162, 0x27C, 0x203, 0x119, 0x218, 0xFE,0x1C0, 0x1C4, 0x163, 0x243, 0x14C, 0x1D6, 0x1E1, 0x65,0x12A, 0x2DA, 0x292, 0xF6, 0x11E, 0x20D, 0x25B, 0x144,0xE5, 0xA3, 0x8C, 0x283, 0x1CF, 0x96, 0x191, 0x2A0,0x225, 0x199, 0x242, 0x92, 0x107, 0x21E, 0x166, 0x8D,0x290, 0x24C, 0x285, 0x287, 0x113, 0x133, 0x13C, 0x10E,0x17F, 0x1EB, 0xE3, 0x233, 0x26F, 0x265, 0x26A, 0xD6,0x19D, 0x15A, 0xAD, 0x256, 0x1A1, 0x23F, 0x6E, 0x1A5,0x245, 0x2C8, 0x1ED, 0x20C, 0xDD, 0x2B4, 0x21B, 0x1C7,0xA4, 0x97, 0x1B3, 0x2CB, 0x174, 0x1B2, 0x27B, 0x189,0x20B, 0x23D, 0x142, 0x28F, 0xDB, 0x69, 0x79, 0x2B2,0x1CE, 0x12E, 0x2A8, 0x268, 0x95, 0x25A, 0x227, 0xB8,0x253, 0xEE, 0xB9, 0x19A, 0x1BA, 0x161, 0x1D3, 0x2C0,0x128, 0x2A1, 0xFF, 0x117, 0x1E9, 0x84, 0x286, 0x248};
for(int j=0;j<67;j++){printf("%04x ", dword_5C008[4 + v27[j]]);}
第三部分:
ahrybxzva3vxa6aLbQeMak4Mb38Kbe==算法分析
三
总结
看雪ID:neilwu
https://bbs.pediy.com/user-home-590753.htm
# 往期推荐
球分享
球点赞
球在看
点击“阅读原文”,了解更多!
文章来源: http://mp.weixin.qq.com/s?__biz=MjM5NTc2MDYxMw==&mid=2458412043&idx=1&sn=2dc05ccc842f0879728b2fcd89c20c25&chksm=b18f548186f8dd976bbefdbffc0b42282448a71d5f95724e2cd7b30dcf09299bdd7c679e2ad6#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh