In the intricate tapestry of the digital world, threads of information interweave, forming connections, enabling interactions, and crafting narratives. Amidst this, a silent protector—SSL/TLS—ensures that the stories told are safeguarded, secure, and sincere. This comprehensive guide unravels the layers of SSL/TLS encryption, demystifying its core and shedding light on its crucial role in the realm of web security.
In this guide, we don't merely present information; we invite you on a journey—a voyage of discovery, understanding, and appreciation of one of the digital world's most pivotal players. Strap in and prepare to navigate the secure waves of the web with SSL/TLS as your guiding star. Let’s begin!
Definition of SSL/TLS
When diving into the digital landscape, one can't help but encounter terms like SSL and TLS. These aren't just random acronyms; they're foundational pillars ensuring the web remains a safe space for data exchange. Let's decode them.
SSL stands for Secure Socket Layer. Originating in the '90s, this protocol was a revolutionary leap in ensuring data between two systems—like your computer and a website server—remains confidential. By encrypting the data packets, it ensured that any eavesdropper would only see gibberish, not the actual information being transferred.
TLS, or Transport Layer Security, is like the upgraded sibling of SSL. Born from the need to address certain vulnerabilities and to enhance overall security, TLS took over the reins. While many use SSL and TLS interchangeably today, it's TLS that's the current standard. Over the years, it’s seen iterations and improvements, always keeping a step ahead of cyber miscreants.
Within the sphere of secure data exchanges, SSL and TLS are often uttered in the same breath, and while they share common goals, their evolutionary journey and the nuances that separate them are pivotal. As the digital terrain morphed, so did the protocols designed to protect it. Let’s put these two side by side, delving into their unique attributes and the evolutionary strides they've taken.
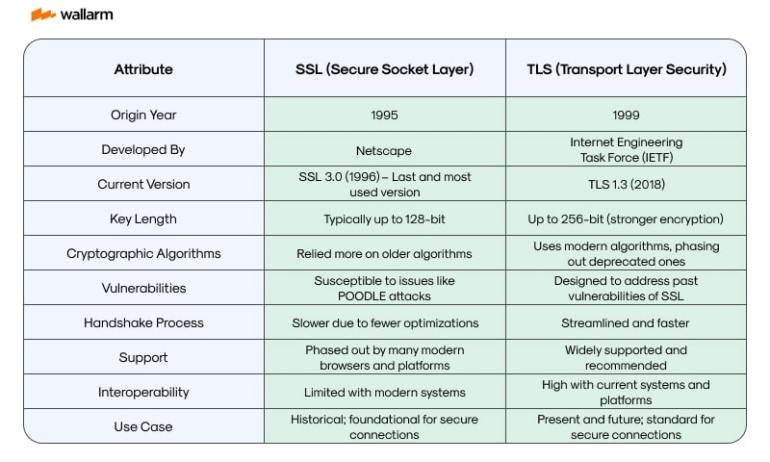
Comparison Table: SSL vs. TLS

In essence, while SSL laid the groundwork for a safer internet, TLS refined and fortified it, responding dynamically to the escalating demands of cybersecurity. These two, when viewed in tandem, chronicle the digital world's commitment to evolving and strengthening its bulwarks against cyber threats.
Historically, SSL was the brainchild of Netscape, a company synonymous with the early days of the web. They rolled out SSL in 1995, setting the first stones of a secure internet. But as technology and threats evolved, so did the need for something more robust. Enter TLS in 1999, courtesy of the Internet Engineering Task Force (IETF). It wasn't just a new name but a more fortified protocol, aiming to shield every byte of data crossing the digital highway.
In simple terms, if we likened data transfer to sending a letter, without SSL or TLS, it would be like sending your personal letter in a clear envelope. Anyone could peek and know your secrets. With SSL/TLS, that letter is in a tamper-evident envelope, ensuring prying eyes stay away.
Wrapping up this foundational chapter, remember these twin terms aren't mere jargon. They're silent guardians of your online transactions, conversations, and data exchanges, working tirelessly behind the scenes to ensure the web remains a trusted space for all.
Why SSL/TLS Matters
In today's digital epoch, a single misstep can cascade into a privacy catastrophe. So, why do SSL and TLS matter so much? Let's dive deep and break it down, also employing some handy comparison tables to elucidate the differences and their unique significance.
Protecting Data Transmission
Think of the countless times you’ve typed in personal details, credit card information, or even just browsed a website. That data doesn't just magically hop from your device to its intended server. It travels, often through multiple nodes. Without encryption, this data would be like an open book, readable by anyone with a little tech know-how.
SSL/TLS Role: These protocols wrap your data in a cocoon of encryption. So, even if someone intercepts it, decoding the information is a Herculean task.
Comparison Table: Data Transmission With and Without SSL/TLS
| Aspect | With SSL/TLS | Without SSL/TLS |
|---|---|---|
| Data Visibility | Encrypted, looks like random characters | Plain text, easily readable |
| Interception Risk | Low due to encryption | High, open to eavesdropping |
| Trustworthiness | High, especially with recognizable padlock icon | Low, often flagged as "Not Secure" |
Trust and Website Credibility
In the web world, trust is a currency. Users need assurance that their data won't fall into the wrong hands. Beyond just data protection, SSL/TLS play a psychological role.
SSL/TLS Role: Websites with SSL/TLS often display a padlock icon, sometimes even boasting the word "Secure" or the organization's name in the URL bar. These visual indicators bolster website credibility, making users more comfortable interacting or transacting.
Comparison Table: User Perception With and Without SSL/TLS
| Aspect | With SSL/TLS | Without SSL/TLS |
|---|---|---|
| User Confidence | High, due to visible trust indicators | Low, apprehensive about data theft |
| Bounce Rate | Lower, users more likely to stay | Higher, users more likely to leave |
| Transaction Completion | More likely, due to perceived security | Less likely, fear of data compromise |
Concluding this chapter, SSL/TLS aren’t just tools; they're trust badges, defenders of data, and silent promoters of website credibility. In the vast expanse of the internet, where cyber threats loom large, these encryption protocols stand as the vigilant sentinels, ensuring user trust and website integrity remain uncompromised.
How SSL/TLS Works ?
Behind every padlock icon in your browser's address bar lies a symphony of cryptographic processes and digital handshakes, ensuring that your connection remains private and integral. To truly appreciate the workings of SSL and TLS, let’s dissect their operations step-by-step, weaving through the intricate dance of keys, certificates, and algorithms.
Establishing the Connection: The Handshake
- a. Client Hello: The client, which is typically your browser, reaches out to a server, indicating a desire to establish a secure connection. It presents the SSL/TLS versions and cipher suites it supports.
- b. Server Hello: The server picks the highest version of the protocol that both it and the client support, and then chooses a cipher suite. It responds with this information and its digital certificate.
- c. Verification: The client verifies the authenticity of the server’s certificate against a list of trusted certificate authorities (CAs). If the certificate isn’t recognized or is expired, you might get a warning in your browser.
- d. Key Exchange: Using the server's public key (from its certificate), the client generates a pre-master secret, encrypts it, and sends it to the server. Both client and server then compute the session-specific master secret.
- e. Confirmation: Both parties exchange messages to confirm that future messages will be encrypted, and the handshake is completed.
Data Transfer: The Encryption Dance
- a. Symmetric Encryption: With the master secret established during the handshake, both parties now employ symmetric encryption, which means they both use the same key to encrypt and decrypt data.
- b. Data Packeting: Information to be sent is broken down into manageable chunks or packets. Each packet is then encrypted.
- c. Data Transmission: The encrypted packets travel safely across the internet, protected from prying eyes.
- d. Data Reception and Decryption: Once the packets reach their destination, they’re decrypted using the shared secret key, and then reassembled to their original format.
Session Termination: Wrapping Up
- a. Initiation: Either party can signal that they want to end the session.
- b. Key Discard: The session keys are discarded. If the client and server want to communicate again, they’ll have to establish a new session key.
- c. Closure: The secure session is terminated, and the parties can revert to an insecure session or disconnect entirely.
To paint a vivid picture, imagine two diplomats wanting to discuss sensitive matters in a room full of eavesdroppers. They first confirm each other's identity (the handshake), then use a special language only they know (encryption) to converse, and finally, once their discussion is over, they vow to forget that special language (session termination) until their next confidential talk.
SSL/TLS, in essence, choreographs this elaborate dance every time you see that padlock icon, ensuring that your data moves gracefully, securely, and imperceptibly across the vast ballroom of the internet.
Types of SSL/TLS Certificates
The vast, intricate web of online platforms demands varying levels of validation and trust. Not all sites require, or even qualify for, the same kind of SSL/TLS certificate. It's akin to the varying forms of identification - from a basic ID card to a full-fledged passport. Let’s explore the three primary SSL/TLS certificate types: Domain Validated (DV), Organization Validated (OV), and Extended Validation (EV).
Domain Validated (DV)
This is the basic level of SSL/TLS certification. Its primary function? To validate that the domain is owned or controlled by the entity requesting the certificate.
- Issuance Time: Swift, often within minutes to hours.
- Validation Process: A simple check to confirm domain ownership, typically via email or DNS.
- Visibility: Displays a padlock symbol in most browsers.
- Use Cases: Ideal for blogs, personal pages, or any site where heavy transactional or personal data isn't processed.
- Example: A personal blog where the writer shares daily musings.
Organization Validated (OV)
A step up from DV, the OV certificate delves deeper, validating not only the domain ownership but also certain details of the organization.
- Issuance Time: Takes longer than DV, usually a few days.
- Validation Process: Involves rigorous checks, confirming domain ownership and validating organizational information like name, city, and country.
- Visibility: Displays a padlock symbol and may show organizational details when clicked or hovered over in some browsers.
- Use Cases: Ideal for businesses and e-commerce sites where users need additional assurance before making transactions.
- Example: An online boutique selling handmade crafts.
Extended Validation (EV)
The pinnacle of SSL/TLS certifications, EV demands a comprehensive vetting process but offers the highest level of trust.
- Issuance Time: Extended period, can take weeks.
- Validation Process: A deep dive into the requesting entity. This includes verifying the organization’s existence, its operational status, physical location, domain ownership, and legal identity.
- Visibility: Distinctive visual indicators like a green address bar, padlock, and the organization’s name prominently displayed.
- Use Cases: Best suited for high-profile websites, banking institutions, and large-scale e-commerce platforms.
- Example: A major bank's online portal.
Comparison Table: DV vs. OV vs. EV

Differentiating between these certificates is crucial for both website owners and users. The right certification ensures that visitors can trust a site with their data. It’s a mutual handshake of assurance and security: the website assures the visitor it’s genuine and safe, and in return, the visitor trusts the website with their data or transactions. Always opting for the highest level isn't the key; choosing what’s apt for the website’s purpose and audience is what matters.
Common Misconceptions about SSL/TLS
The world of SSL/TLS, though critically foundational to internet security, is often clouded with myths and misconceptions. As with many things technical, the more complex a subject, the greater the chance for misunderstandings. This chapter aims to debunk some of these prevailing myths surrounding SSL/TLS.
A. SSL vs. TLS – Differences and Evolution
The progression from SSL to TLS isn't just a mere rebranding or a switch of acronyms; it signifies an evolutionary step in secure communications. Let’s dissect some misconceptions related to their differences and evolution.
"SSL and TLS are entirely different protocols."
- Reality: TLS is the successor of SSL and was developed based on the last version of SSL (SSL 3.0). Thus, they share many similarities but have distinct differences, especially in terms of security enhancements.
"If it’s TLS, it can’t be SSL, and vice versa."
- Reality: When people mention "SSL certificates" today, they're often referring broadly to the certs used in both SSL and TLS protocols. It's become a generic term, much like how some might say "Xerox" when they mean "photocopy".
Example: Think of SSL as a well-loved but aging classic car, and TLS as the newer, upgraded version. They both operate on the same foundational principles, but the latter comes with enhanced safety features and better performance.
B. Myths about Encryption Strength
The world of encryption isn't immune to myths, either. Strength and security are often misunderstood.
"128-bit encryption is half as strong as 256-bit encryption."
- Reality: Encryption strength doesn’t scale linearly. 256-bit isn't just "twice as strong" as 128-bit. In fact, 256-bit encryption offers a level of security that's astronomically higher.
"More bits always mean better security."
- Reality: While higher bit lengths generally provide more robust encryption, they can also require more processing power. There's a balance to be struck between encryption strength and performance.
Example: Consider locks. A basic padlock might have fewer tumblers inside than a high-security lock, making it easier to pick. But just because one high-security lock has 10 tumblers and another has 20 doesn't mean the latter is twice as secure. It might be many times more secure, or the difference might be negligible, depending on other factors.
Comparison Table: SSL vs. TLS Misconceptions
| Misconception | SSL | TLS |
|---|---|---|
| Originated as a response to the other's flaws | Developed first, had vulnerabilities | Evolved to address SSL's vulnerabilities |
| Encryption Algorithms | Relied on older algorithms | Incorporates newer, safer algorithms |
| Widely in use today | Phased out, rarely in use | Currently the standard |
| General perception in public vernacular | Often used as a catch-all term for secure certificates | More accurate but less commonly used in casual discussions |
By dispelling these misconceptions, we get a clearer, more accurate picture of SSL/TLS and encryption's nuanced world. Knowledge not only illuminates but also empowers users and administrators to make informed decisions about cybersecurity.
Implementing SSL/TLS: Basic Steps
Implementing SSL/TLS isn't just about bolstering security; it's about fostering trust with every visitor that crosses the digital threshold of a website. A green padlock or an organization’s name displayed in the browser isn't just an icon or text; it's a symbol of assurance. Let's dive into the fundamental steps of this implementation.
Choosing a Certificate Authority
The Certificate Authority is the trusted entity that issues digital certificates. The reputation of a CA plays a pivotal role, as browsers and systems come pre-loaded with trusted CAs.
- Research: Begin by assessing the reputation, reviews, and reliability of CAs.
- Budgeting: CAs offer a range of prices based on the type of certificate and validation level.
- Needs Analysis: Determine whether you need DV, OV, or EV. Does the CA cater to these requirements?
Certificate Installation
Once you've chosen a CA and procured the SSL/TLS certificate, it's time to set it up on your server.
- Download Certificate: Post-validation, the CA will provide a link to download the certificate, often in .crt or .pem format.
- Install on Server: The exact steps can vary depending on the server type. Here's a basic example for an Apache server:
<code class="language-bash">Copy code Backup your configurations cp /etc/httpd/conf/httpd.conf /etc/httpd/conf/httpd.conf.backup Open server configuration file nano /etc/httpd/conf/httpd.conf Add or modify the following lines: SSLEngine on SSLCertificateFile "/path/to/your_domain.crt" SSLCertificateKeyFile "/path/to/your_private.key" SSLCertificateChainFile "/path/to/CA.crt" Save the file and exit. Restart Apache to apply changes service httpd restart</code>
Testing and Validation
Post-installation, it's crucial to ensure that everything runs smoothly.
- Browser Testing: Simply visit your website, prefixed with https://. Look for the padlock symbol and click on it to view certificate details.
- SSL Test Tools: There are online tools like SSL Labs' SSL Server Test that can provide a comprehensive review of your configuration.
- Code Test: Sometimes, even after SSL/TLS implementation, content can be loaded insecurely (often termed 'mixed content'). Here's a JavaScript snippet that can be used to check for insecure content:
<code class="language-javascript">Copy code
if (window.location.protocol !== "https:") {
alert("Warning: Some content isn't loaded securely!");
}</code>
With the certificate successfully in place, not only does the site benefit from encryption, but visitors also gain a tangible sense of trust. The digital handshake is complete, and the conversation, guarded by the stalwart protocols of SSL/TLS, can commence with confidence.
The Future of SSL/TLS
SSL/TLS, like any technology serving as the bedrock of modern web infrastructure, isn't static. As cyber threats evolve, so does the need for robust encryption and secure communication mechanisms. As we glance toward the horizon, what might the future of SSL/TLS look like?
Expected Updates
While predicting the precise trajectory of tech innovation is a challenge, there are some evident directions in which SSL/TLS might be headed:
- Quantum-Resistant Algorithms: Quantum computing poses potential threats to current cryptographic standards. Preparing SSL/TLS for a post-quantum world will be essential.
- Improved Performance: As websites become more intricate and data-driven, minimizing the latency introduced by encryption processes will be pivotal. Expect further refinement of TLS handshakes and session resumptions.
- Wider Adoption of TLS 1.3: Given its enhanced security and performance features, the adoption rate of TLS 1.3 will likely surge. Older, less secure versions may get deprecated.
Importance in an Evolving Web Landscape
In an era where data breaches make headlines, and privacy concerns loom large, SSL/TLS's role is more crucial than ever. The web is not just about sharing information; it's about establishing trust, safeguarding user data, and ensuring seamless, secure transactions. As Internet of Things (IoT) devices proliferate and 5G networks enhance connectivity speeds, the data transferred will skyrocket. Here, SSL/TLS will serve as the watchful guardian, ensuring that the enormous data flow remains uncompromised.
Top 5 Improvements Required and Their Business Value
| Improvement | Business Value |
|---|---|
| Quantum-Resistant Encryption | Prepares businesses for future-proof security, ensuring longevity and data integrity. |
| Enhanced Mobile Device Support | Facilitates secure transactions on mobile, capturing a growing segment of web users. |
| Integration with IoT Security Standards | Safeguards data as IoT adoption surges, ensuring secure device-to-device communication. |
| Zero-Knowledge Proof Integration | Enables businesses to validate transactions without accessing the content, bolstering privacy. |
| AI-Driven Adaptive Encryption | Uses AI to optimize encryption based on data type and sensitivity, enhancing efficiency. |
The future of SSL/TLS is not just about refinement but also about adaptation. It's about recognizing emerging challenges and evolving to meet them head-on. As the next chapter of the digital age unfolds, SSL/TLS will undoubtedly play a defining role in sculpting a secure, trustworthy web ecosystem.
Conclusion: The Stalwart Sentinel of the Digital Age
As our journey through the complexities and marvels of SSL/TLS draws to an end, we're left standing at the crossroads of reflection and action. We've traversed the depths of its history, pierced through common misconceptions, and glimpsed into the promise of tomorrow. What remains, beyond the facts and technicalities, is a profound realization: SSL/TLS is more than just a protocol. It's the silent guardian, the unseen sentinel, ensuring that in the vast digital expanse, trust and security are never compromised.
Reiteration of SSL/TLS Significance
The digital realm can be likened to a vast, interconnected web of conversations, transactions, and interactions. Every click, every login, every purchase carries with it data—data that tells a story, holds value, and demands protection. SSL/TLS stands as the guardian of these stories. It wraps them in layers of encryption, ensuring they reach their destination intact, untouched, unviolated. In a world increasingly marred by data breaches and cyber threats, SSL/TLS is the beacon of trust, telling visitors, "Here, you are safe."
But beyond the technical, lies a deeper, more human truth. The real essence of SSL/TLS isn't in bits, bytes, or cryptographic algorithms. It's in the trust it fosters, the confidence it instills, and the digital relationships it nurtures. It's about enabling a mother to shop online for her child without fear, a student to submit their thesis without anxiety, or an entrepreneur to craft their digital empire with confidence.
Encourage Adoption and Regular Updates
If SSL/TLS is the unsung hero, then its adoption and regular updates are the songs of praise it rightfully deserves. Ignoring SSL/TLS or relegating it to the annals of 'techy stuff best left to IT' is akin to building a fortress but leaving the gates wide open. Inaction or complacency isn't just a technical oversight; it's a disservice to every user, every visitor, every individual who entrusts their data to the digital realm.
For businesses, adopting SSL/TLS isn't just a tick in a compliance box; it's a commitment—a vow to prioritize customer trust above all. And in that trust lies immense business value. A secure website doesn't just protect data; it invites more visitors, fosters loyalty, and amplifies brand reputation.
But the journey doesn't end with mere adoption. The digital landscape is ever-evolving, and with it, the challenges. Regular updates ensure that this formidable guardian remains equipped with the latest armor and weaponry, always prepared to thwart emerging threats.
In Closing
Let this exploration serve as more than just enlightenment. Let it be a clarion call—a call to action. In embracing SSL/TLS, we don't just adopt a protocol; we champion a cause. The cause of a secure, trusted, and resilient digital world. A world where data flows like poetry, guarded by the watchful eyes of SSL/TLS, ensuring every verse, every word, every letter remains sacred and inviolate.
May we step forward with renewed vigor, carrying the torch of digital security high, ensuring that the legacy of SSL/TLS doesn't just endure but thrives, illuminating the path for generations to come.
如有侵权请联系:admin#unsafe.sh